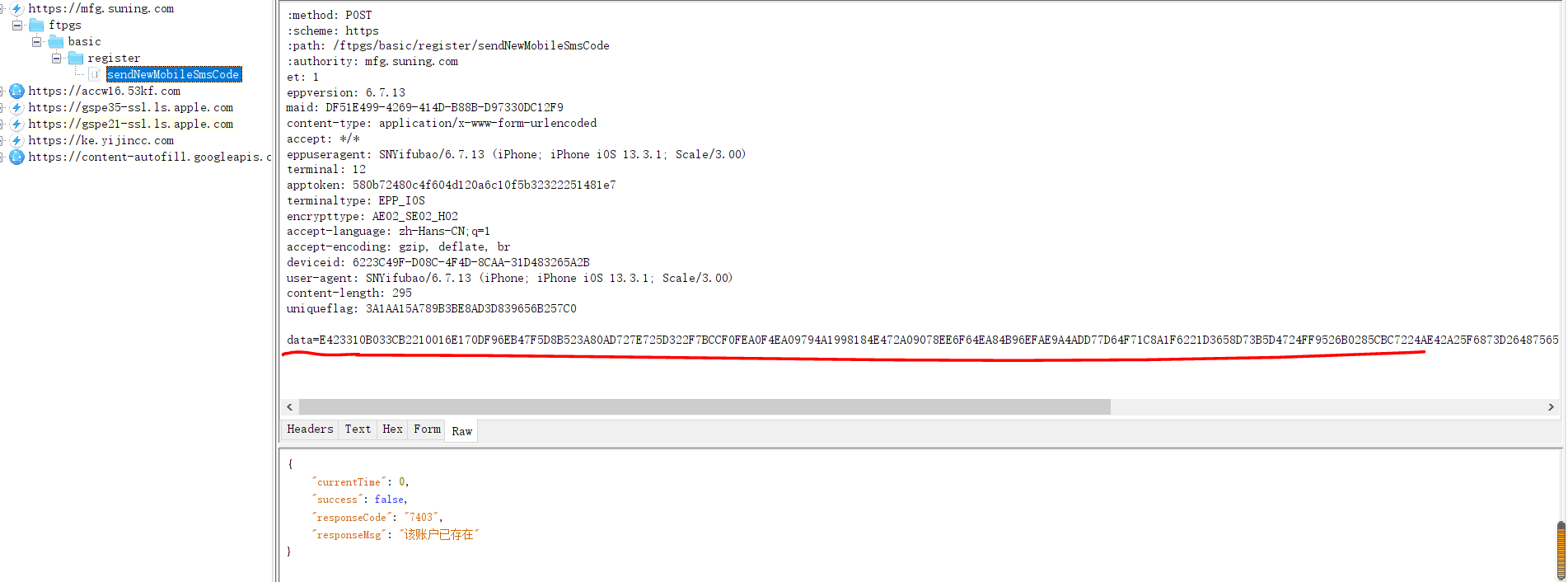
一、用工具抓包
二、分析apk是否加壳
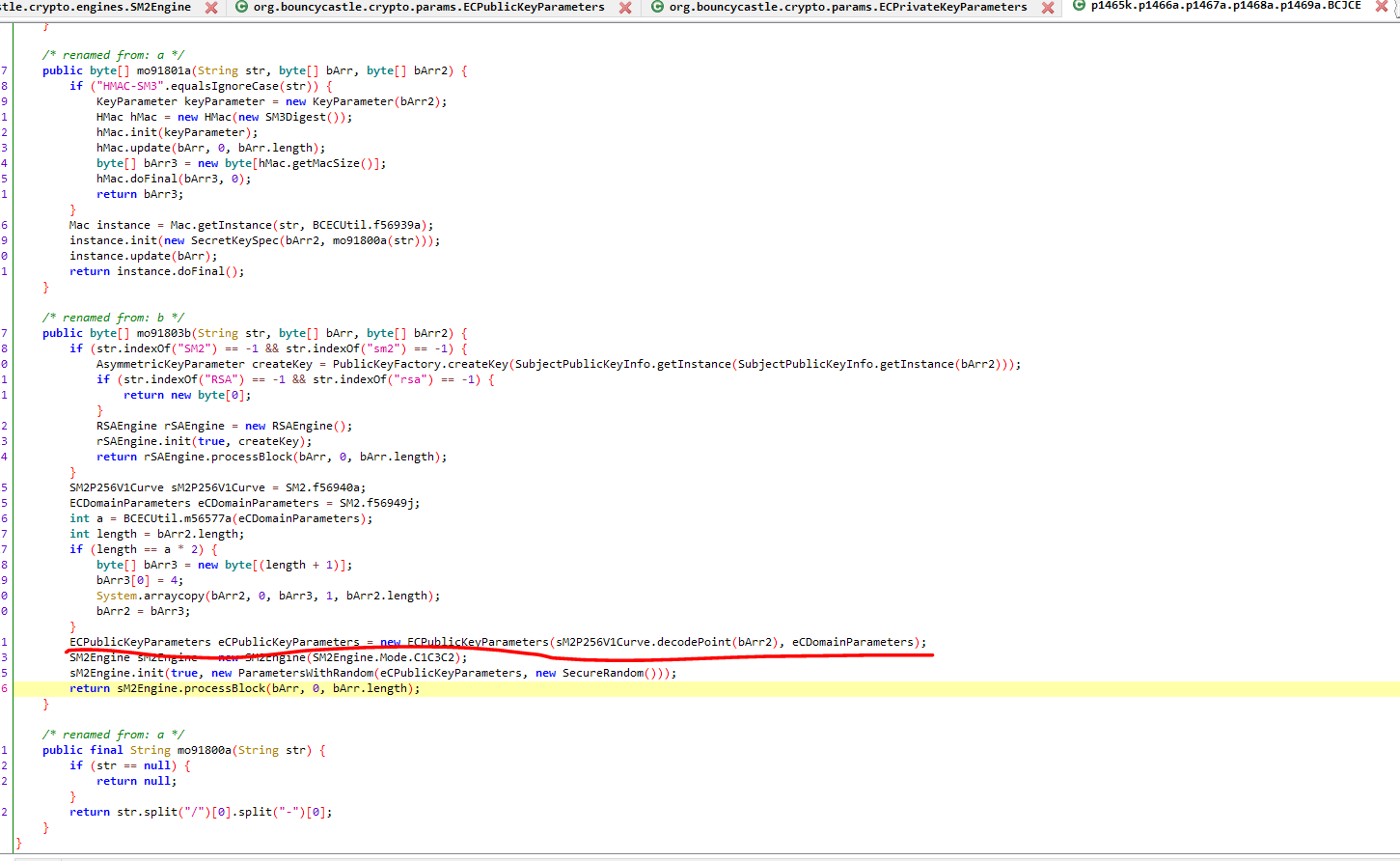
没有加壳,直接用jadx打开分析
查找data=参数
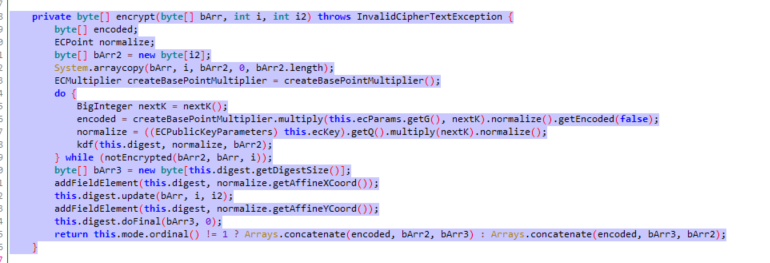
文件:su_ning_jin_rong.js
Java.perform(function () {
var encrypt1 = Java.use("org.bouncycastle.crypto.engines.SM2Engine");
console.log(encrypt1);
encrypt1.encrypt.overload('[B', 'int', 'int').implementation = function (args1,args2,args3) {
console.log("args1-1", args1,args2,args3);
//JS输出内容为[object Object] 转换成数组,然后转换成字节
console.log(JSON.stringify(args1),args2,args3)
var args = this.encrypt(args1,args2,args3);
console.log("args-1", args);
return args
}
});
三、用Frida HOOK 登录入参数
# -*- coding: utf-8 -*-
import logging
import frida
import sys
logging.basicConfig(level=logging.DEBUG)
def on_message(message, data):
print(message)
with open('su_ning_jin_rong.js', 'r', encoding='utf-8') as f:
sta = ''.join(f.readlines())
rdev = frida.get_remote_device()
processes = rdev.enumerate_processes() # 安卓手机中的所有进程
print(processes)
# android.content.Intent android.content.Context android.view.ViewGroup java.lang.String, java.util.List [Ljava.lang.String;(String[]), javax.net.ssl.SSLSession SSLSession
session = rdev.attach("com.suning.mobile.epa")
print(session)
script = session.create_script(sta)
script.on("message", on_message)
script.load()
sys.stdin.read()
四、用Frida HOOK SM2 公钥
Java.perform(function () {
var encrypt1 = Java.use("k.a.a.a.a.a");
console.log(encrypt1);
encrypt1.b.overload('java.lang.String', '[B', '[B').implementation = function (args1,args2,args3) {
console.log("args1-1", args1, args2, args3);
//JS输出内容为[object Object] 转换成数组,然后转换成字节
// console.log(JSON.stringify(args1),args2,args3)
console.log(args1)
console.log(JSON.stringify(args2))
console.log(JSON.stringify(args3))
var args = this.b(args1,args2,args3);
console.log("args-1:", args);
return args
}
});
import logging
import frida
import sys
logging.basicConfig(level=logging.DEBUG)
def on_message(message, data):
print(message)
with open('su_ning_jin_rong_key.js', 'r', encoding='utf-8') as f:
sta = ''.join(f.readlines())
rdev = frida.get_remote_device()
processes = rdev.enumerate_processes() # 安卓手机中的所有进程
print(processes)
# android.content.Intent android.content.Context android.view.ViewGroup java.lang.String, java.util.List [Ljava.lang.String;(String[]), javax.net.ssl.SSLSession SSLSession
session = rdev.attach("com.suning.mobile.epa")
print(session)
script = session.create_script(sta)
script.on("message", on_message)
script.load()
sys.stdin.read()
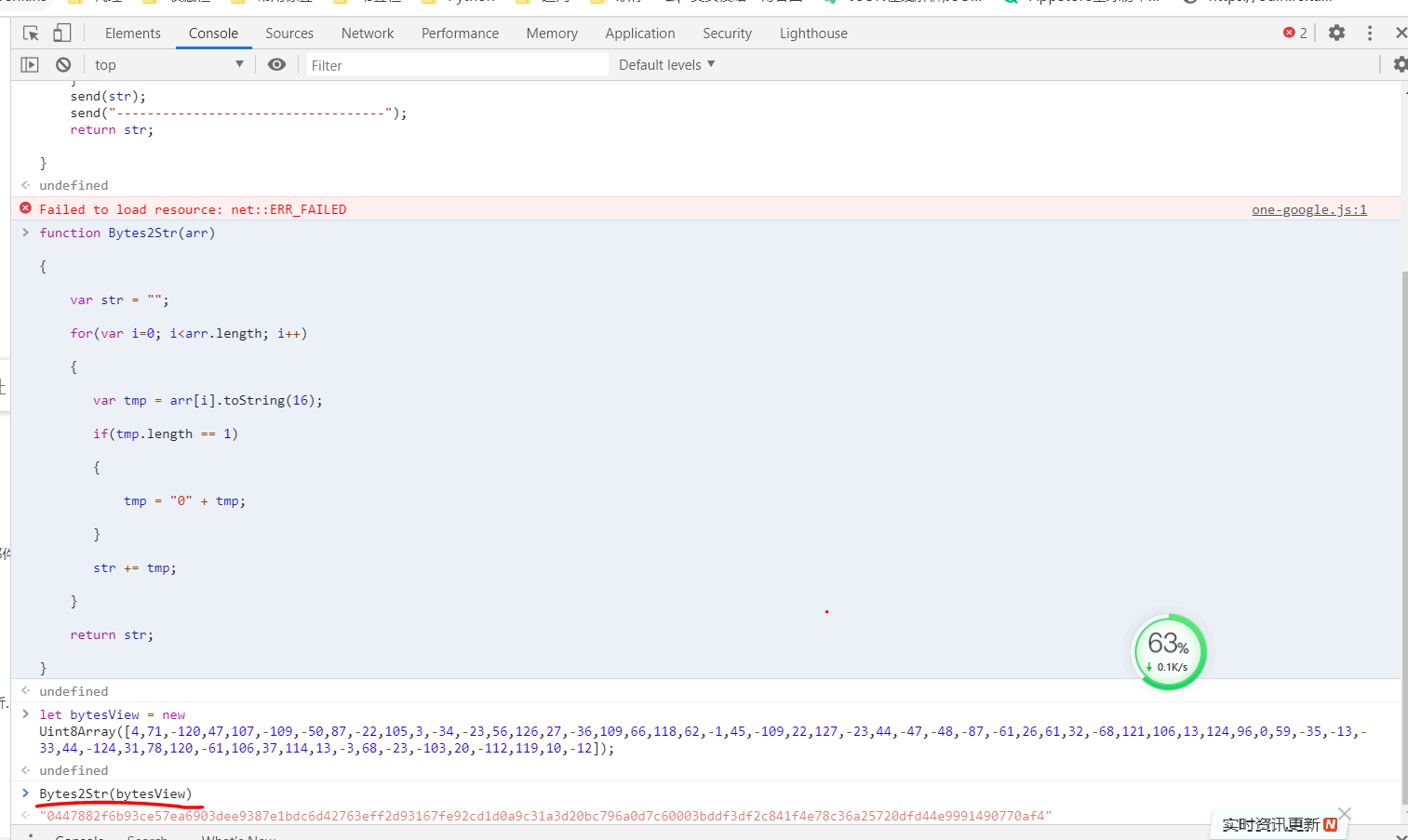
五、安装gmssl
pip install gmssl
import binascii
import json
from gmssl import sm2
public_key = '47882F6B93CE57EA6903DEE9387E1BDC6D42763EFF2D93167FE92CD1D0A9C31A3D20BC796A0D7C60003BDDF3DF2C841F4E78C36A25720DFD44E9991490770AF4'
sm2_crypt = sm2.CryptSM2(public_key=public_key, private_key='')
data = json.dumps({"mobileNo": "13899999999", "sceneId": "FTIS-M-001"}, separators=(',', ':')).encode()
enc_data = sm2_crypt.encrypt(data)
result = binascii.b2a_hex(enc_data).upper().decode()
print(result)
a=[123,34,109,111,98,105,108,101,78,111,34,58,34,49,51,57,49,56,50,51,56,51,52,52,34,44,34,115,99,101,110,101,73,100,34,58,34,70,84,73,83,45,77,45,48,48,49,34,125]
print(bytes(a))
六、获取公钥public_key
JS文件:su_ning_jin_rong_key.js
Java.perform(function () {
var encrypt1 = Java.use("k.a.a.a.a.a");
console.log(encrypt1);
encrypt1.b.overload('java.lang.String', '[B', '[B').implementation = function (args1,args2,args3) {
console.log("args1-1", args1, args2, args3);
//JS输出内容为[object Object] 转换成数组,然后转换成字节
// console.log(JSON.stringify(args1),args2,args3)
console.log(args1)
console.log(JSON.stringify(args2))
console.log(JSON.stringify(args3))
var args = this.b(args1,args2,args3);
console.log("args-1:", args);
return args
}
});
七、HOOK 公钥public_key
import logging
import frida
import sys
logging.basicConfig(level=logging.DEBUG)
def on_message(message, data):
print(message)
with open('su_ning_jin_rong_key.js', 'r', encoding='utf-8') as f:
sta = ''.join(f.readlines())
rdev = frida.get_remote_device()
processes = rdev.enumerate_processes() # 安卓手机中的所有进程
print(processes)
# android.content.Intent android.content.Context android.view.ViewGroup java.lang.String, java.util.List [Ljava.lang.String;(String[]), javax.net.ssl.SSLSession SSLSession
session = rdev.attach("com.suning.mobile.epa")
print(session)
script = session.create_script(sta)
script.on("message", on_message)
script.load()
sys.stdin.read()
八、加密