Nginx配置4 Https网站设置
1 检查是否支持ssl模块
[root@nginx-node01 1.16.0]# ./nginx -V 2>&1 | sed 's/ /
/g' |grep ssl
--with-http_ssl_module
如果nginx没有http_ssl_module支持,则需要在编译时加入ssl支持,具体参考:Shell编译安装nginx
2 配置Server
将公私钥、CA证书生成中制作好的nginx-node01.crt证书文件和nginx私钥文件放入ssl目录
# HTTPS server
#增加HTTP强制跳转功能
server{
listen 80;
server_name www.kov.com;
return 301 https://$server_name$request_uri;
}
server {
listen 443 ssl;
server_name www.kov.com;
ssl_certificate ssl/nginx-node01.crt;
ssl_certificate_key ssl/nginx-node01.key;
ssl_session_cache shared:SSL:1m;
ssl_session_timeout 5m;
ssl_ciphers HIGH:!aNULL:!MD5;
ssl_prefer_server_ciphers on;
location / {
root html;
index index.html index.htm;
}
}
3 客户端设置域名
[root@ca CA]# echo 192.168.56.104 www.kov.com >> /etc/hosts
[root@ca CA]# cat /etc/hosts
##
# Host Database
#
# localhost is used to configure the loopback interface
# when the system is booting. Do not change this entry.
##
127.0.0.1 localhost
255.255.255.255 broadcasthost
::1 localhost
fe80::1%lo0 localhost
......
192.168.56.104 www.kov.com
4 客户端curl测试
客户端添加证书前
[root@ca CA]# curl https://www.kov.com
curl: (60) Peer's Certificate issuer is not recognized.
More details here: http://curl.haxx.se/docs/sslcerts.html
curl performs SSL certificate verification by default, using a "bundle"
of Certificate Authority (CA) public keys (CA certs). If the default
bundle file isn't adequate, you can specify an alternate file
using the --cacert option.
If this HTTPS server uses a certificate signed by a CA represented in
the bundle, the certificate verification probably failed due to a
problem with the certificate (it might be expired, or the name might
not match the domain name in the URL).
If you'd like to turn off curl's verification of the certificate, use
the -k (or --insecure) option.
客户端添加证书后
[root@ca CA]# curl --cacert cacert.pem https://www.kov.com
<!DOCTYPE html>
<html>
<head>
<title>Welcome to www.kov.com!</title>
</head>
<body>
<h1>Welcome to nginx ssl!</h1>
<p><em>Thank you for using nginx.</em></p>
</body>
</html>
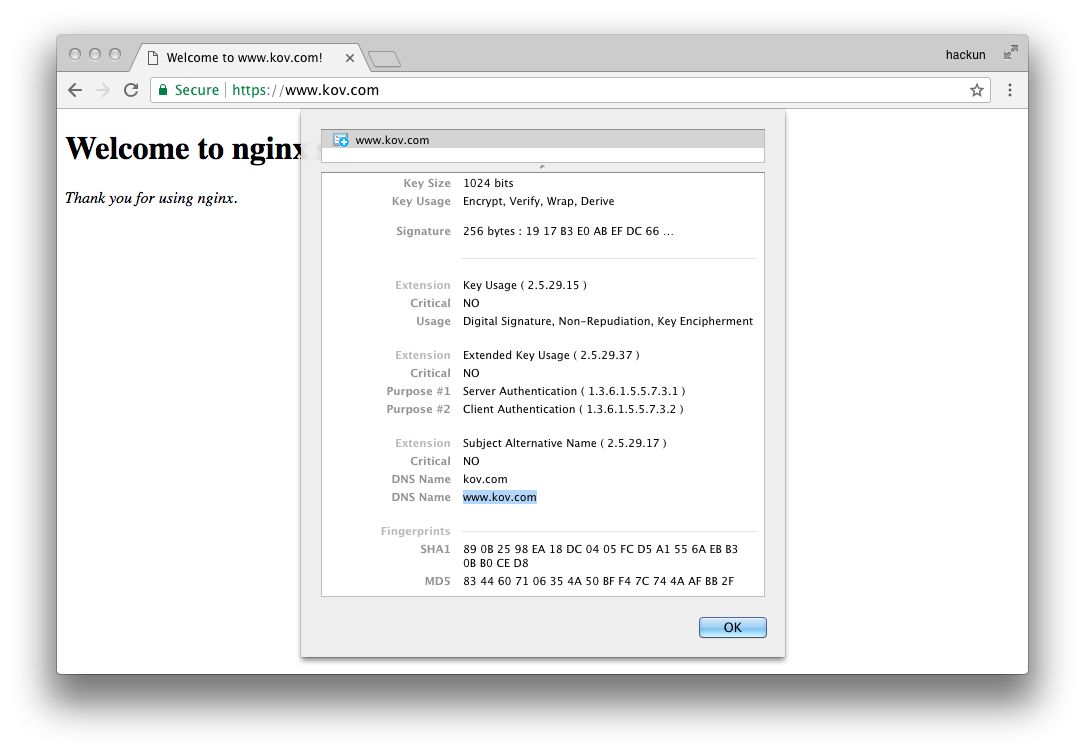
5 客户端浏览器验证
1. NET::ERR_CERT_AUTHORITY_INVALID错误
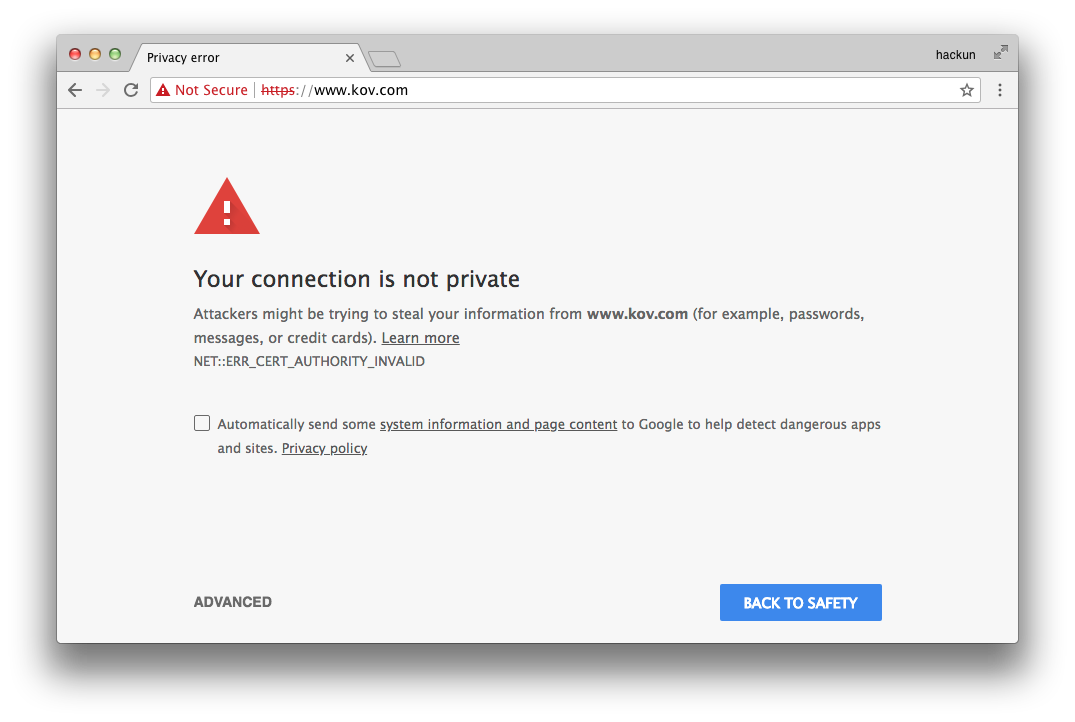
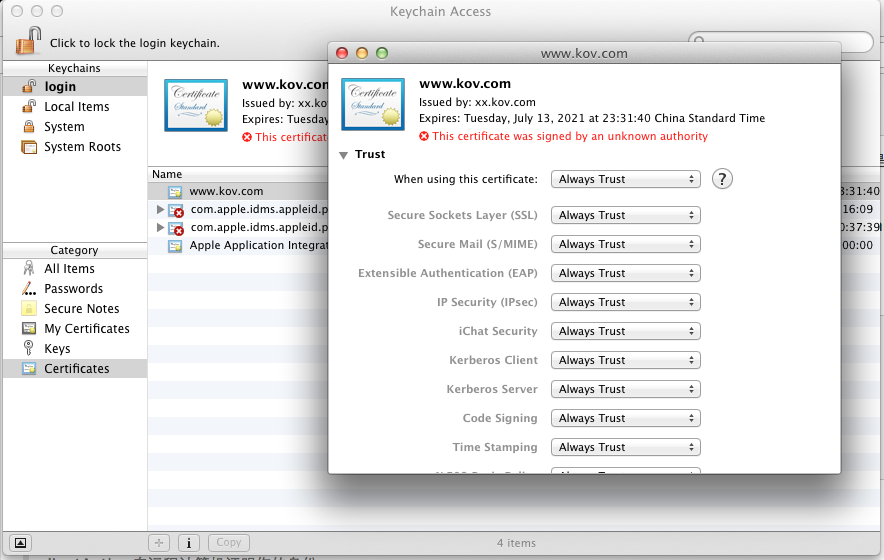
解决方法:在keychain中将证书改为信任(下图)
2. NET::ERR_CERT_COMMON_NAME_INVALID错误
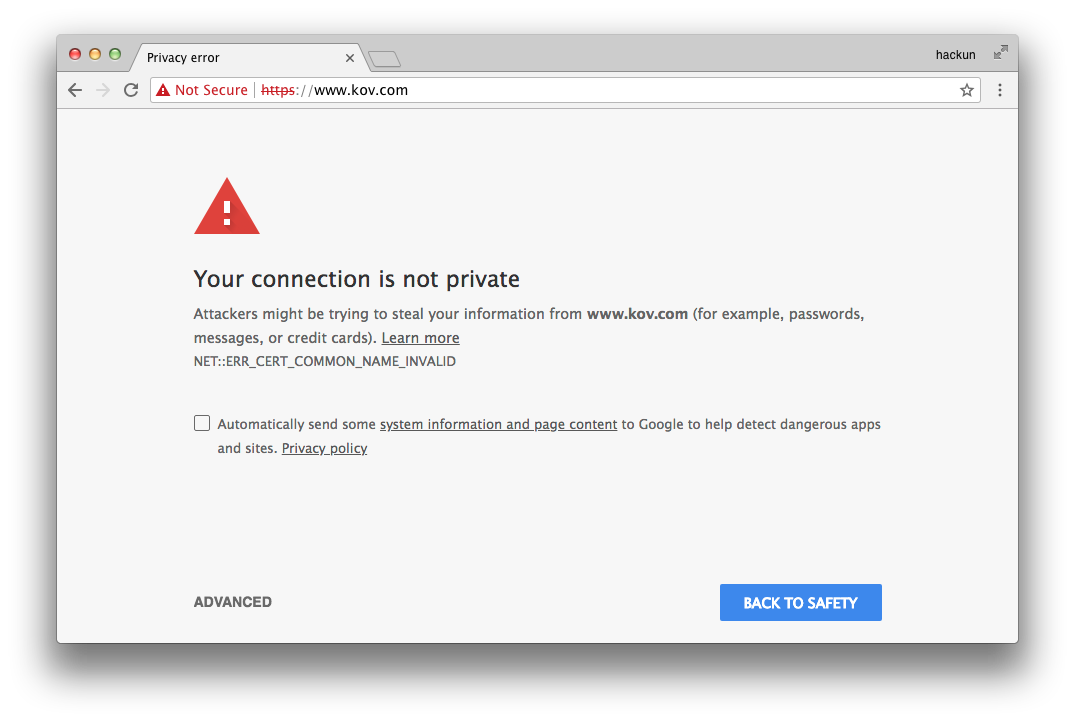
解决方法:参考《公私钥、证书生成》CA签署证书中补充,重新CA签署多域名证书后,重新在keychain中将证书改为信任。