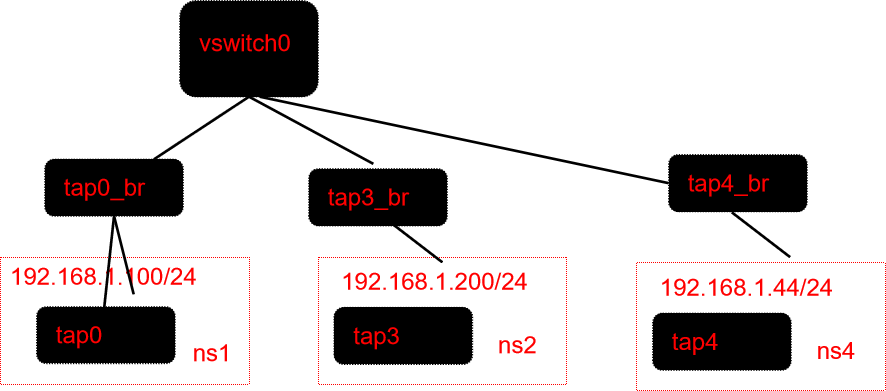
1、ovs-vsctl set port tap0_br tag=100
[root@kunpeng82 devuser]# ovs-vsctl list port tap0_br
_uuid : f8b41259-a1b3-4226-bd25-afb7c0dfe9e1
bond_active_slave : []
bond_downdelay : 0
bond_fake_iface : false
bond_mode : []
bond_updelay : 0
cvlans : []
external_ids : {}
fake_bridge : false
interfaces : [202a2f21-c8f3-4f23-8a64-5dc5de6c6e72]
lacp : []
mac : []
name : "tap0_br"
other_config : {}
protected : false
qos : []
rstp_statistics : {}
rstp_status : {}
statistics : {}
status : {}
tag : 100
trunks : []
vlan_mode : []
2、添加几条flow
[root@kunpeng82 devuser]# ovs-ofctl dump-flows vswitch0 cookie=0x0, duration=2352.210s, table=0, n_packets=407, n_bytes=17262, priority=3,in_port="tap4_br",vlan_tci=0x0000 actions=mod_vlan_vid:100,NORMAL cookie=0x0, duration=2155.729s, table=0, n_packets=111, n_bytes=4858, priority=3,in_port="tap3_br",vlan_tci=0x0000 actions=mod_vlan_vid:100,NORMAL cookie=0x0, duration=2499.930s, table=0, n_packets=387, n_bytes=16422, priority=1,in_port="tap0_br" actions=strip_vlan,output:"tap3_br" cookie=0x0, duration=8697.389s, table=0, n_packets=114, n_bytes=6244, priority=0 actions=NORMAL
但是ip netns exec ns2 ping 192.168.1.100 ping通
[root@kunpeng82 devuser]# ip netns exec ns4 ping 192.168.1.100 PING 192.168.1.100 (192.168.1.100) 56(84) bytes of data. ^C --- 192.168.1.100 ping statistics --- 3 packets transmitted, 0 received, 100% packet loss, time 2058ms
但是ip netns exec ns4 ping 192.168.1.100无法ping通
[root@kunpeng82 devuser]# ip netns exec ns2 ping 192.168.1.100 PING 192.168.1.100 (192.168.1.100) 56(84) bytes of data. 64 bytes from 192.168.1.100: icmp_seq=1 ttl=64 time=0.306 ms 64 bytes from 192.168.1.100: icmp_seq=2 ttl=64 time=0.023 ms ^C --- 192.168.1.100 ping statistics --- 2 packets transmitted, 2 received, 0% packet loss, time 1048ms rtt min/avg/max/mdev = 0.023/0.164/0.306/0.142 ms
tcpdump竟然在tap3_br上发现了arp 回应报文,在tap4_br上没发发现arp 回应报文
[root@kunpeng82 devuser]# tcpdump -i tap3_br tcpdump: verbose output suppressed, use -v or -vv for full protocol decode listening on tap3_br, link-type EN10MB (Ethernet), capture size 262144 bytes 14:21:53.729020 ARP, Request who-has 192.168.1.100 tell 192.168.1.44, length 28 14:21:53.729147 ARP, Reply 192.168.1.100 is-at ca:03:87:45:02:90 (oui Unknown), length 28 14:21:54.787148 ARP, Request who-has 192.168.1.100 tell 192.168.1.44, length 28 14:21:54.787173 ARP, Reply 192.168.1.100 is-at ca:03:87:45:02:90 (oui Unknown), length 28 14:21:55.827157 ARP, Request who-has 192.168.1.100 tell 192.168.1.44, length 28 14:21:55.827176 ARP, Reply 192.168.1.100 is-at ca:03:87:45:02:90 (oui Unknown), length 28 14:21:56.867251 ARP, Request who-has 192.168.1.100 tell 192.168.1.44, length 28 14:21:56.867270 ARP, Reply 192.168.1.100 is-at ca:03:87:45:02:90 (oui Unknown), length 28 14:21:57.907144 ARP, Request who-has 192.168.1.100 tell 192.168.1.44, length 28 14:21:57.907163 ARP, Reply 192.168.1.100 is-at ca:03:87:45:02:90 (oui Unknown), length 28 ^C 10 packets captured 10 packets received by filter 0 packets dropped by kernel [root@kunpeng82 devuser]# tcpdump -i tap4_br tcpdump: verbose output suppressed, use -v or -vv for full protocol decode listening on tap4_br, link-type EN10MB (Ethernet), capture size 262144 bytes 14:22:09.598737 ARP, Request who-has 192.168.1.100 tell 192.168.1.44, length 28 14:22:10.627128 ARP, Request who-has 192.168.1.100 tell 192.168.1.44, length 28 14:22:11.667130 ARP, Request who-has 192.168.1.100 tell 192.168.1.44, length 28 ^C 3 packets captured 3 packets received by filter 0 packets dropped by kernel
ovs-appctl ofproto/trace vswitch0 in_port=1诊断
[root@kunpeng82 devuser]# ovs-appctl ofproto/trace vswitch0 in_port=1 Flow: in_port=1,vlan_tci=0x0000,dl_src=00:00:00:00:00:00,dl_dst=00:00:00:00:00:00,dl_type=0x0000 bridge("vswitch0") ------------------ 0. in_port=1, priority 1 strip_vlan output:2 Final flow: unchanged Megaflow: recirc_id=0,eth,in_port=1,dl_type=0x0000 Datapath actions: 3
删除 这条flow: cookie=0x0, duration=2499.930s, table=0, n_packets=387, n_bytes=16422, priority=1,in_port="tap0_br" actions=strip_vlan,output:"tap3_br"
[root@kunpeng82 devuser]# ovs-ofctl del-flows vswitch0 in_port="tap0_br" [root@kunpeng82 devuser]# ovs-ofctl add-flow vswitch0 priority=1,in_port=1,actions=strip_vlan,normal [root@kunpeng82 devuser]# ip netns exec ns4 ping 192.168.1.100 PING 192.168.1.100 (192.168.1.100) 56(84) bytes of data. From 192.168.1.44 icmp_seq=1 Destination Host Unreachable From 192.168.1.44 icmp_seq=2 Destination Host Unreachable From 192.168.1.44 icmp_seq=3 Destination Host Unreachable From 192.168.1.44 icmp_seq=4 Destination Host Unreachable From 192.168.1.44 icmp_seq=5 Destination Host Unreachable
tcpdump能抓到包了
[root@kunpeng82 devuser]# tcpdump -i tap4_br
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on tap4_br, link-type EN10MB (Ethernet), capture size 262144 bytes
14:28:26.387130 ARP, Request who-has 192.168.1.100 tell 192.168.1.44, length 28
14:28:26.387165 ARP, Reply 192.168.1.100 is-at ca:03:87:45:02:90 (oui Unknown), length 28
14:28:27.427221 ARP, Request who-has 192.168.1.100 tell 192.168.1.44, length 28
14:28:27.427245 ARP, Reply 192.168.1.100 is-at ca:03:87:45:02:90 (oui Unknown), length 28
14:28:28.467130 ARP, Request who-has 192.168.1.100 tell 192.168.1.44, length 28
14:28:28.467165 ARP, Reply 192.168.1.100 is-at ca:03:87:45:02:90 (oui Unknown), length 28
14:28:29.507129 ARP, Request who-has 192.168.1.100 tell 192.168.1.44, length 28
14:28:29.507169 ARP, Reply 192.168.1.100 is-at ca:03:87:45:02:90 (oui Unknown), length 28
14:28:30.547224 ARP, Request who-has 192.168.1.100 tell 192.168.1.44, length 28
14:28:30.547247 ARP, Reply 192.168.1.100 is-at ca:03:87:45:02:90 (oui Unknown), length 28
14:28:31.587131 ARP, Request who-has 192.168.1.100 tell 192.168.1.44, length 28
14:28:31.587162 ARP, Reply 192.168.1.100 is-at ca:03:87:45:02:90 (oui Unknown), length 28
14:28:32.627130 ARP, Request who-has 192.168.1.100 tell 192.168.1.44, length 28
14:28:32.627164 ARP, Reply 192.168.1.100 is-at ca:03:87:45:02:90 (oui Unknown), length 28
^C
14 packets captured
14 packets received by filter
0 packets dropped by kernel
[root@kunpeng82 devuser]#
还是不通哦
[root@kunpeng82 devuser]# ip netns exec ns4 ping 192.168.1.100 PING 192.168.1.100 (192.168.1.100) 56(84) bytes of data. ^C --- 192.168.1.100 ping statistics --- 3 packets transmitted, 0 received, 100% packet loss, time 2118ms [root@kunpeng82 devuser]#
删除流表,重新添加两条
root@kunpeng82 devuser]# ovs-ofctl del-flows vswitch0 in_port="tap0_br" [root@kunpeng82 devuser]# ovs-ofctl add-flow vswitch0 priority=1,ip,in_port=1,nw_dst=192.168.1.200/32,actions=strip_vlan,output:2 [root@kunpeng82 devuser]# ovs-ofctl add-flow vswitch0 priority=1,ip,in_port=1,nw_dst=192.168.1.44/32,actions=strip_vlan,output:4 [root@kunpeng82 devuser]# ip netns exec ns4 ping 192.168.1.100 PING 192.168.1.100 (192.168.1.100) 56(84) bytes of data. 64 bytes from 192.168.1.100: icmp_seq=1 ttl=64 time=0.268 ms 64 bytes from 192.168.1.100: icmp_seq=2 ttl=64 time=0.035 ms ^C --- 192.168.1.100 ping statistics --- 2 packets transmitted, 2 received, 0% packet loss, time 1038ms rtt min/avg/max/mdev = 0.035/0.151/0.268/0.117 ms [root@kunpeng82 devuser]# ovs-ofctl dump-flows vswitch0 cookie=0x0, duration=4618.262s, table=0, n_packets=848, n_bytes=35812, priority=3,in_port="tap4_br",vlan_tci=0x0000 actions=mod_vlan_vid:100,NORMAL cookie=0x0, duration=4421.781s, table=0, n_packets=157, n_bytes=7518, priority=3,in_port="tap3_br",vlan_tci=0x0000 actions=mod_vlan_vid:100,NORMAL cookie=0x0, duration=361.150s, table=0, n_packets=10, n_bytes=756, priority=1,in_port="tap0_br" actions=strip_vlan,output:"tap3_br" cookie=0x0, duration=90.099s, table=0, n_packets=0, n_bytes=0, priority=1,in_port="tap0_br" actions=strip_vlan,output:"tap3_br" cookie=0x0, duration=26.201s, table=0, n_packets=0, n_bytes=0, priority=1,ip,in_port="tap0_br",nw_dst=192.168.1.200 actions=strip_vlan,output:"tap3_br" cookie=0x0, duration=8.072s, table=0, n_packets=0, n_bytes=0, priority=1,ip,in_port="tap0_br",nw_dst=192.168.1.44 actions=strip_vlan,output:"tap4_br" cookie=0x0, duration=10963.441s, table=0, n_packets=114, n_bytes=6244, priority=0 actions=NORMAL [root@kunpeng82 devuser]#
[root@kunpeng82 devuser]# ip netns exec ns2 ping 192.168.1.100
PING 192.168.1.100 (192.168.1.100) 56(84) bytes of data.
From 192.168.1.200 icmp_seq=1 Destination Host Unreachable
From 192.168.1.200 icmp_seq=2 Destination Host Unreachable
From 192.168.1.200 icmp_seq=3 Destination Host Unreachable
From 192.168.1.200 icmp_seq=4 Destination Host Unreachable
From 192.168.1.200 icmp_seq=5 Destination Host Unreachable
ip netns exec ns2 ping 192.168.1.100 和ip netns exec ns4 ping 192.168.1.100都没成功
抓包发现没收到arp reply
[root@kunpeng82 devuser]# tcpdump -i tap4_br
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on tap4_br, link-type EN10MB (Ethernet), capture size 262144 bytes
15:12:49.267241 ARP, Request who-has 192.168.1.100 tell 192.168.1.200, length 28
15:12:50.307154 ARP, Request who-has 192.168.1.100 tell 192.168.1.200, length 28
15:12:51.347151 ARP, Request who-has 192.168.1.100 tell 192.168.1.200, length 28
15:12:52.387235 ARP, Request who-has 192.168.1.100 tell 192.168.1.200, length 28
15:12:53.427156 ARP, Request who-has 192.168.1.100 tell 192.168.1.200, length 28
15:12:54.467152 ARP, Request who-has 192.168.1.100 tell 192.168.1.200, length 28
15:12:55.507229 ARP, Request who-has 192.168.1.100 tell 192.168.1.200, length 28
15:12:56.547151 ARP, Request who-has 192.168.1.100 tell 192.168.1.200, length 28
15:12:57.587144 ARP, Request who-has 192.168.1.100 tell 192.168.1.200, length 28
15:12:58.627214 ARP, Request who-has 192.168.1.100 tell 192.168.1.200, length 28
15:12:59.667148 ARP, Request who-has 192.168.1.100 tell 192.168.1.200, length 28
15:13:00.707148 ARP, Request who-has 192.168.1.100 tell 192.168.1.200, length 28
^C
12 packets captured
12 packets received by filter
0 packets dropped by kernel
[root@kunpeng82 devuser]#
再添加两条arp的flow
[root@kunpeng82 devuser]# ovs-ofctl add-flow vswitch0 priority=1,arp,in_port=1,nw_dst=192.168.1.200/32,actions=strip_vlan,output:2 [root@kunpeng82 devuser]# ovs-ofctl add-flow vswitch0 priority=1,arp,in_port=1,nw_dst=192.168.1.44/32,actions=strip_vlan,output:4 [root@kunpeng82 devuser]# ip netns exec ns2 ping 192.168.1.100 PING 192.168.1.100 (192.168.1.100) 56(84) bytes of data. 64 bytes from 192.168.1.100: icmp_seq=1 ttl=64 time=0.587 ms 64 bytes from 192.168.1.100: icmp_seq=2 ttl=64 time=0.024 ms ^C --- 192.168.1.100 ping statistics --- 2 packets transmitted, 2 received, 0% packet loss, time 1038ms rtt min/avg/max/mdev = 0.024/0.305/0.587/0.282 ms [root@kunpeng82 devuser]# ip netns exec ns4 ping 192.168.1.100 PING 192.168.1.100 (192.168.1.100) 56(84) bytes of data. 64 bytes from 192.168.1.100: icmp_seq=1 ttl=64 time=0.528 ms 64 bytes from 192.168.1.100: icmp_seq=2 ttl=64 time=0.025 ms ^C --- 192.168.1.100 ping statistics --- 2 packets transmitted, 2 received, 0% packet loss, time 1008ms rtt min/avg/max/mdev = 0.025/0.276/0.528/0.252 ms [root@kunpeng82 devuser]#