参考:
Elasticsearch从6.8开始, 允许免费用户使用X-Pack的安全功能, 以前安装es都是裸奔。接下来记录配置安全认证的方法。
为了简化物理安装过程,我们将使用docker安装我们的服务。
一些基础配置
es需要修改linux的一些参数。
永久修改
设置 vm.max_map_count=262144
vim /etc/sysctl.conf
vm.max_map_count=262144
临时修改
# 不重启, 直接生效当前的命令
sysctl -w vm.max_map_count=262144
我们假设安装3个实力的es集群,先创建对应的数据存储文件
mkdir -p es1/data
mkdir -p es1/logs
mkdir -p es2/data
mkdir -p es2/logs
mkdir -p es3/data
mkdir -p es3/logs
关于版本和docker镜像
Elasticsearch分几种licenses,其中Open Source和Basic是免费的, 而在6.8之后安全功能才开始集成在es的Basic授权上。
Basic对应docker镜像为
docker pull elasticsearch:6.8.18
docker pull kibana:6.8.18
同时dockerhub同步为elasticsearch. 我们直接拉取elasticsearch:6.8.18 就好
首先,创建docker-compose.yml,此版本只测试单es版本
version: '2.2'
services:
es1:
image: elasticsearch:6.8.18
container_name: es1
environment:
- node.name=es1
#- cluster.name=es-docker-cluster
#- discovery.seed_hosts=es2,es3
#- cluster.initial_master_nodes=es1,es2,es3
- bootstrap.memory_lock=true
- "ES_JAVA_OPTS=-Xms256m -Xmx256m"
ulimits:
memlock:
soft: -1
hard: -1
volumes:
- ./es1/data:/usr/share/elasticsearch/data
- ./es1/logs:/usr/share/elasticsearch/logs
- ./elasticsearch.yaml:/usr/share/elasticsearch/config/elasticsearch.yml
- ./elastic-certificates.p12:/usr/share/elasticsearch/config/elastic-certificates.p12 # 运行前需要创建证书,下文会详细展开
ports:
- 9400:9200 # 因本机9200已经占用,映射主机9400给容器9200
networks:
- elastic
command: elasticsearch
# es2:
# image: elasticsearch:6.8.18
# container_name: es2
# environment:
# - node.name=es2
# - cluster.name=es-docker-cluster
# - discovery.seed_hosts=es1,es3
# - cluster.initial_master_nodes=es1,es2,es3
# - bootstrap.memory_lock=true
# - "ES_JAVA_OPTS=-Xms256m -Xmx256m"
# ulimits:
# memlock:
# soft: -1
# hard: -1
# volumes:
# - ./es2/data:/usr/share/elasticsearch/data
# - ./es2/logs:/usr/share/elasticsearch/logs
# - ./elasticsearch.yaml:/usr/share/elasticsearch/config/elasticsearch.yml
# - ./elastic-certificates.p12:/usr/share/elasticsearch/config/elastic-certificates.p12
# ports:
# - 9401:9200
# networks:
# - elastic
# es3:
# image: elasticsearch:6.8.18
# container_name: es3
# environment:
# - node.name=es3
# - cluster.name=es-docker-cluster
# - discovery.seed_hosts=es1,es2
# - cluster.initial_master_nodes=es1,es2,es3
# - bootstrap.memory_lock=true
# - "ES_JAVA_OPTS=-Xms256m -Xmx256m"
# ulimits:
# memlock:
# soft: -1
# hard: -1
# volumes:
# - ./es3/data:/usr/share/elasticsearch/data
# - ./es3/logs:/usr/share/elasticsearch/logs
# - ./elasticsearch.yaml:/usr/share/elasticsearch/config/elasticsearch.yml
# - ./elastic-certificates.p12:/usr/share/elasticsearch/config/elastic-certificates.p12 # 实测时,发现证书需要设置权限,我的是644
# ports:
# - 9402:9200
# networks:
# - elastic
kib01:
depends_on:
- es1
image: kibana:6.8.18
container_name: kib01
ports:
- 5701:5601
environment:
ELASTICSEARCH_URL: http://es1:9200 #由于同一网段,可以dns出es1
ELASTICSEARCH_HOSTS: http://es1:9200
volumes:
- ./kibana.yaml:/usr/share/kibana/config/kibana.yml # 后文会详细展开
networks:
- elastic
networks:
elastic:
driver: bridge
关于elasticsearch.yml
network.host: 0.0.0.0
xpack.security.enabled: true
xpack.security.transport.ssl.enabled: true
xpack.security.transport.ssl.keystore.type: PKCS12
xpack.security.transport.ssl.verification_mode: certificate
xpack.security.transport.ssl.keystore.path: elastic-certificates.p12
xpack.security.transport.ssl.truststore.path: elastic-certificates.p12
xpack.security.transport.ssl.truststore.type: PKCS12
xpack.security.audit.enabled: true
- network.host 设置允许其他ip访问,解除ip绑定
- xpack.security 则是安全相关配置,其中ssl的证书需要自己生成
关于kibana.yaml
server.name: kibana
server.host: 0.0.0.0
elasticsearch.hosts: "http://172.17.0.2:9200" # es1的ip为172.17.0.2
elasticsearch.username: admin #同后设置的超级用户
elasticsearch.password: 123456 #超级用户对应的密码
生成证书elastic-certificates.p12
es提供了生成证书的工具elasticsearch-certutil,我们可以在docker实例中生成它,然后复制出来,后面统一使用。
首先运行es实例
sudo docker run -dit --name=es elasticsearch:7.6.2 /bin/bash
进入实例内部
sudo docker exec -it es /bin/bash
生成ca: elastic-stack-ca.p12
[root@25dee1848942 elasticsearch]# ./bin/elasticsearch-certutil ca
This tool assists you in the generation of X.509 certificates and certificate
signing requests for use with SSL/TLS in the Elastic stack.
The 'ca' mode generates a new 'certificate authority'
This will create a new X.509 certificate and private key that can be used
to sign certificate when running in 'cert' mode.
Use the 'ca-dn' option if you wish to configure the 'distinguished name'
of the certificate authority
By default the 'ca' mode produces a single PKCS#12 output file which holds:
* The CA certificate
* The CA's private key
If you elect to generate PEM format certificates (the -pem option), then the output will
be a zip file containing individual files for the CA certificate and private key
Please enter the desired output file [elastic-stack-ca.p12]:
Enter password for elastic-stack-ca.p12 :
再生成cert: elastic-certificates.p12
[root@25dee1848942 elasticsearch]# ./bin/elasticsearch-certutil cert --ca elastic-stack-ca.p12
This tool assists you in the generation of X.509 certificates and certificate
signing requests for use with SSL/TLS in the Elastic stack.
The 'cert' mode generates X.509 certificate and private keys.
这个生成elastic-certificates.p12 就是我们需要使用的。
复制出证书, ctrl+d退出容器内部
sudo docker cp es:/usr/share/elasticsearch/elastic-certificates.p12 .
# 关闭这个容器
sudo docker kill es
sudo docker rm es
如此获取了证书。
生成密码
我们首先要启动es集群,去里面生成密码。
sudo docker-compose up
然后进入其中一台
sudo docker exec -it es01 /bin/bash
# 自行创建超级用户
./bin/elasticsearch-users useradd admin -r superuser
Enter new password:
Retype new password:
docker-compose启动服务
# cd到docker-compose.yaml目录
docker-compose up -d
# 查看服务
docker-compose ps
# 如果有不是up状态的容器
docker-compose logs -f 容器名
测试是否开启了认证
# 测试不输入密码下get
curl localhost:9400 #主机映射的端口是9400
{"error":{"root_cause":[{"type":"security_exception","reason":"missing authentication token for REST request [/]","header":{"WWW-Authenticate":"Basic realm="security" charset="UTF-8""}}],"type":"security_exception","reason":"missing authentication token for REST request [/]","header":{"WWW-Authenticate":"Basic realm="security" charset="UTF-8""}},"status":401}
# 测试输入密码时
curl -u admin:123456 localhost:9400
{
"name" : "hoGlED6",
"cluster_name" : "elasticsearch",
"cluster_uuid" : "9o_94RdASQyvRNzIBagRfg",
"version" : {
"number" : "6.8.18",
"build_flavor" : "default",
"build_type" : "docker",
"build_hash" : "aca2329",
"build_date" : "2021-07-28T16:06:05.232873Z",
"build_snapshot" : false,
"lucene_version" : "7.7.3",
"minimum_wire_compatibility_version" : "5.6.0",
"minimum_index_compatibility_version" : "5.0.0"
},
"tagline" : "You Know, for Search"
}
# 测试kibana是否需要密码登录
地址栏输入:localhost:5701
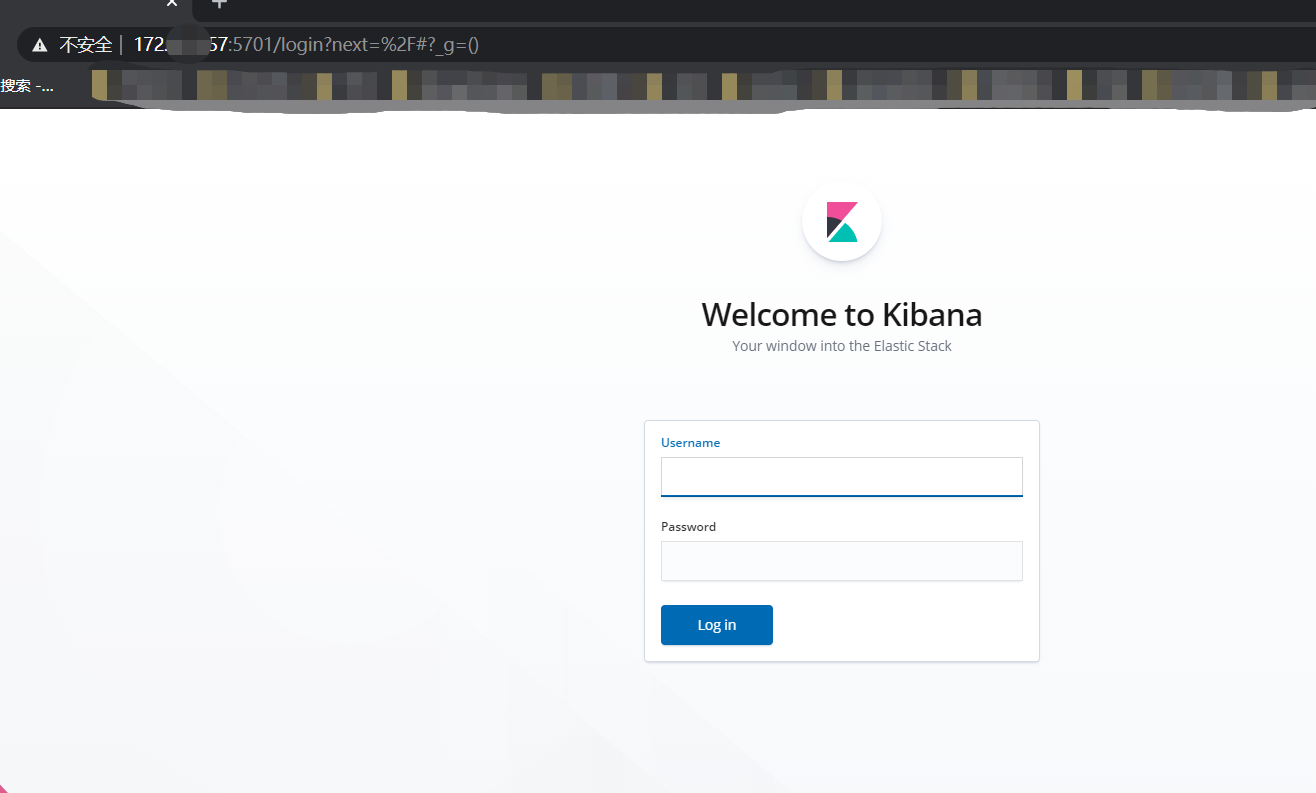
待正确输入密码后可登录查看。