原文地址:https://www.ca.com/us/services-support/ca-support/ca-support-online/knowledge-base-articles.tec1698523.html
Introduction/Summary:
The base Java JVM and SDK installs from Oracle are limited in strength for the cryptographic functions that they can perform. Oracle also provide a patch the "Java JCE Unlimited Strength Jurisdiction Policy Files" patch which when applied to the base JDK or JVM install allows for unlimited strength cryptographic functions.
Background:
Although the patch is a simple zip file there are often problems associated with installing it and installing it in the right location. This article covers how to do the install of the patch, and also some of the mis-install pitfalls that can occur.
Environment:
all (windows, linux, solaris)
Instructions:
- Have an existing Java JRE or JDK Installation.
First you will need a Java, either the Java Runtime (JVM) or the Java Development KIt (JDK) installation.
Many of the Siteminder (SSO) components require a specific 32bit rather than a 64bit version of the JDK/JRE so it is worth verifying you have the correct one installed. - Download the "JCE Unlimited Strength Jurisdiction Policy Files"
The "JCE Unlimited Strength Jurisdiction Policy Files" are available as a .zip file from :
http://www.oracle.com/technetwork/java/javase/downloads/index.html
Only the version is applicable (ie., the one jce_policy-8.zip applies to both the 32bit and 64bit editions of java 8 ) .
The version of the Jurisdiction file depends on the version of Java you have installed, as per:
- Java 8 : jce_policy-8.zip
- Java 7 : UnlimitedJCEPolicyJDK7.zip
- Java 6 : jce-policy-6.zip
- etc.
- The contents of the .zip file:
The zip file contain two jar files : local_policy.jar, US_export_policy.jar a README.txt and a COPYRIGHT.html file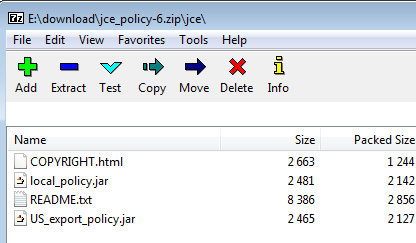
The two .jar files are the important ones. - Determine the version of java to install the .jar files
We need to apply these .jar files into the actual JDK that is being run.
As well as 64bit and 32bit version of java, appearing under directories C:Program FilesJava and C:Program Files (x86) respectively, a user may also have several minor versions of java installed and both JRE and JDK's installed. The same is true of Unix/Linux installs as well. Note: There are two directories, both a JDK and a JRE directory: jdk1.6.0_37 and jre6 both have an embedded jre and it is good policy to update both.
Note: There are two directories, both a JDK and a JRE directory: jdk1.6.0_37 and jre6 both have an embedded jre and it is good policy to update both.
Note2: There can also be several JDK/JRE versions installed - not necessarily in the expected directories.
Technically we only need to update the one that we are going to run, but it is good policy to update both the JDK and JRE, and a number of support cases have been solved because the JDK/JRE version being run was not the expected one, and solved once the correct version was updated.
Below we cover updating the JDK and the JRE.
- Update the distribution policy .jar files in the JDK distribution.
We need to copy the two .jar files from the "JCE Unlimited Strength Jurisdiction Policy Files" zip file, and replace the ones in the JDK distribution of the JRE. : /jdk1.6.0_37/jre/lib/security directories.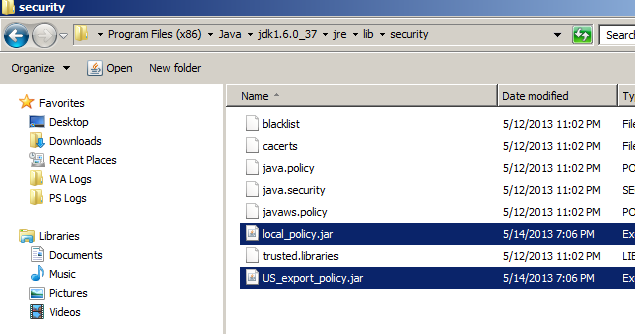
Note: Make sure you replace the .jar files. There have been cases where the .zip file was uncompressed from the cmd line, and the new .jar files were left in a sub-directory, rather than replacing the existing ones. This can easily be done on unix systems. - Update the distribution policy .jar files in the JRE distribution.
We need to copy the two .jar files from the "JCE Unlimited Strength Jurisdiction Policy Files" zip file, and replace the ones in the distribution for the JRE distribution /jre6/lib/security directories.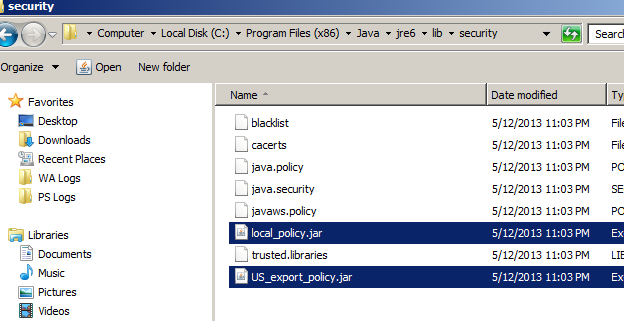
- How can I check they have been installed correctly?
Fails with Strong Crypto operations:
If it is not correctly installed the main problem will be that strong cryptography will be disabled usually giving an error when you want to use it.
Add -verbose to java startup:
If you add "-verbose" to the java startup printed to stdout will be a list of the absolute path to the .jar file where it loads each .class file. This is also useful to determine which JDK/JRE is actually loaded, so you can ensure you've patched the right version.
Some programs will also check at their startup and tell you if Unlimited Cryptography is available. - Program to Check if installed Correctly
Attached to this article is a simple java program that will check if unlimited strength cryptography is enabled. The core function is as follows: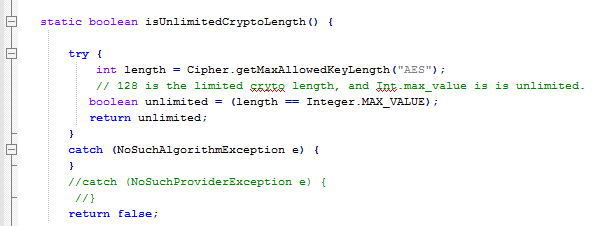
Where it gets the max length of the key allowed for AES encryption and compares that to the unlimited number (Integer.MAX_VALUE).
Additional Information:
Within CA Single Sign On, as well as install of the "Unlimited Strength Jurisdiction Policy Files" there can be issued with installing the RSA JSafe components cryptoj.jar and cryptoJFIPS.jar - these will be the topic of another knowledge base article.