Frida 启动
attach 启动
直接附加到指定包名的应用中
1
|
frida -U com.kevin.android -l hook.js --no-pause
|
直接附加到当前应用中
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
|
frida -UF -l hook.js --no-pause
import sys
import time
import frida
def on_message(message,data):
print("message",message)
print("data",data)
device = frida.get_usb_device()
session = device.attach("com.kevin.demo1")
with open("./demo1.js","r") as f:
script = session.create_script(f.read())
script.on("message",on_message)
script.load()
sys.stdin.read()
|
spawn 启动
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
|
frida -U -f com.kevin.android -l demo1.js --no-pause
import sys
import time
import frida
def on_message(message,data):
print("message",message)
print("data",data)
device = frida.get_usb_device()
pid = device.spawn(["com.kevin.demo1"])
device.resume(pid)
session = device.attach(pid)
with open("./rpc_demo.js",'r') as f:
script = session.create_script(f.read())
script.on("message",on_message)
script.load()
sys.stdin.read()
|
frida-server 自定义端口
frida server
更改 frida server 默认端口: 27042 并开启远程连接
1
2
3
4
5
6
7
8
9
|
adb shell
su -
cd /data/local/tmp
|
frida
frida 远程连接自定义端口
python
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
|
|
Frida rpc 远程调用
python
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
|
import frida
import json
from flask import Flask, jsonify, request
def message(message, data):
if message['type'] == 'send':
print(f"[*] {message['payload']}")
else:
print(message)
|
js
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
|
|
压力测试
tmp.json
1
|
{"data": "62feb9a98a01945ab06c0dd7823adc57"}
|
命令
1
|
siege -c30 -r1 "<http://127.0.0.1:5000/encrypt> POST < tmp.json"
|
nps 进行内网穿透
-
nps server 启动
mac: sudo nps start
-
新建客户端
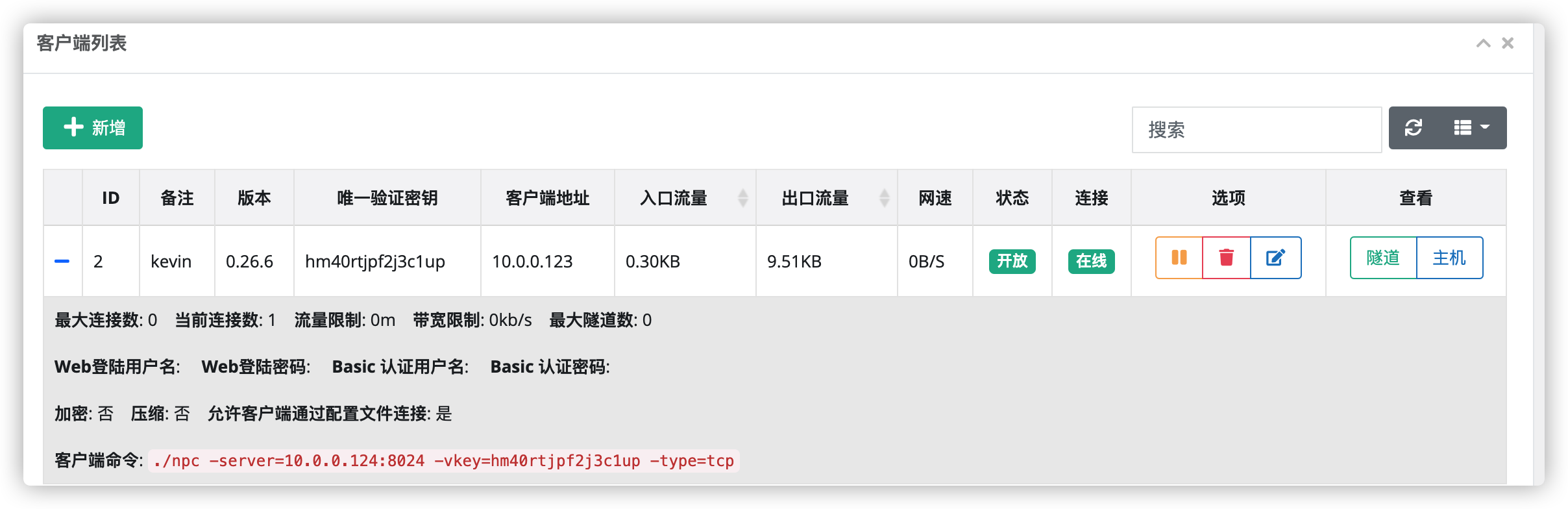
安卓手机连接客户端 ./npc -server=10.0.0.124:8024 -vkey=hm40rtjpf2j3c1up -type=tcp
-
给客户端添加和 frida server 的端口映射
安卓手机启动 frida-server: ./fs12800 -l 0.0.0.0:6666
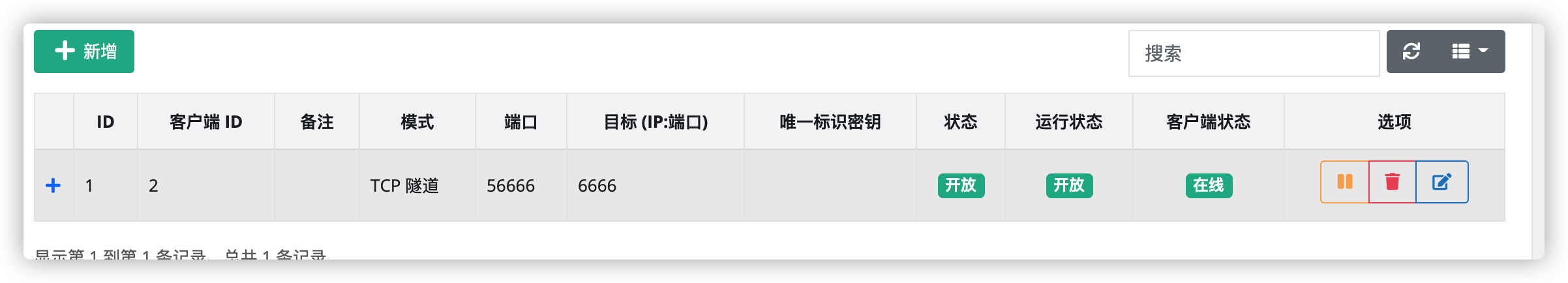
将目标 frida-server 的端口映射到 56666 端口上
-
python 脚本更改和 frida-server 的连接
1
|
session = frida.get_device_manager().add_remote_device('10.0.0.124:56666').attach('com.example.demoso1')
|
此时就可以将 frida-server 开放到公网了;
Hook 普通方法
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
|
function main(){
Java.perform(function(){
var UtilsClass = Java.use("com.kevin.app.Utils");
UtilsClass.getCalc.implementation = function (a,b){
|
Hook 重载方法
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
|
function main(){
Java.perform(function(){
var UtilsClass = Java.use("com.kevin.app.Utils");
|
Hook 构造方法
1
2
3
4
5
6
7
8
9
10
11
12
|
function main(){
Java.perform(function (){
|
Hook 对象
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
|
function main(){
Java.perform(function(){
|
Hook 动静态成员属性
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
|
function main(){
Java.perform(function(){
var MoneyClass = Java.use("com.xiaojianbang.app.Money");
|
Hook 内部类
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
|
function main(){
Java.perfor(function(){
|
Hook 匿名类
Hook 类的所有方法
Java.enumerateLoadedClasses()
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
|
function main(){
Java.perform(function(){
Java.enumerateLoadedClasses({
onMatch: function(name,handle){
if (name.indexOf("com.xiaojianbang.app.Money") != -1){
console.log(name,handle);
|
Java.enumerateLoadedClassesSync()
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
|
function main(){
Java.perform(function(){
|
Hook 类的所有方法及重载
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
|
function main(){
Java.perform(function(){
|
Hook 动态加载的 dex
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
|
function main(){
Java.perform(function(){
Java.enumerateClassLoaders({
onMatch : function(loader){
try {
|
经常在加壳的 app 中, 没办法正确找到正常加载 app 类的 classloader, 可以使用以下代码:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
|
function hook() {
Java.perform(function () {
Java.enumerateClassLoadersSync().forEach(function (classloader) {
try {
console.log("classloader", classloader);
classloader.loadClass("com.kanxue.encrypt01.MainActivity");
Java.classFactory.loader = classloader;
var mainActivityClass = Java.use("com.kanxue.encrypt01.MainActivity");
console.log("mainActivityClass", mainActivityClass);
} catch (error) {
console.log("error", error);
}
});
})
}
|
Hook 主动构造数组
1
2
3
4
5
6
7
8
9
|
function mainArray(){
Java.perform(function(){
var myCharList = Java.array("char",['一','去','二','三','里']);
var myStringList = Java.array("java.lang.String",["一","二","三"]);
var ArrayClass = Java.use("java.util.Arrays");
console.log(ArrayClass.toString(myCharList));
console.log(ArrayClass.toString(myStringList));
})
}
|
Hook cast 强制类型转换
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
|
|
Hook 打印类实现的接口
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
|
function searchInterface(){
Java.perform(function(){
Java.enumerateLoadedClasses({
onComplete: function(){},
onMatch: function(name,handle){
if (name.indexOf("com.r0ysue.a0526printout") > -1) {
|
Hook enum 枚举
1
2
3
4
5
6
7
8
9
10
11
|
function enumPrint(){
Java.perform(function(){
Java.choose("com.r0ysue.a0526printout.Signal",{
onComplete: function(){},
onMatch: function(instance){
console.log('find it ,',instance);
console.log(instance.class.getName());
}
})
})
}
|
Hook 获取 context
1
2
3
4
5
6
7
8
9
10
11
|
function getContext(){
Java.perform(function(){
var currentApplication = Java.use("android.app.ActivityThread").currentApplication();
console.log(currentApplication);
var context = currentApplication.getApplicationContext();
console.log(context);
var packageName = context.getPackageName();
console.log(packageName);
console.log(currentApplication.getPackageName());
})
}
|
Hook 主动调用构造方法
1
2
3
4
5
6
7
8
9
10
11
12
13
14
|
function main(){
Java.perform(function(){
var StringClass = Java.use("java.lang.String");
var MoneyClass = Java.use("com.xiaojianbang.app.Money");
MoneyClass.$init.overload('java.lang.String','int').implementation = function(x,y){
console.log('hook Money init');
var myX = StringClass.new("Hello World!");
var myY = 9999;
this.$init(myX,myY);
}
})
}
setImmediate(main);
|
Hook 主动调用静态方法
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
|
function main_rsa(){
Java.perform(function(){
var RSA = Java.use("com.xiaojianbang.app.RSA");
var StringClass = Java.use("java.lang.String");
var base64Class = Java.use("android.util.Base64");
var myBytes = StringClass.$new("Hello World").getBytes();
var result = RSA.encrypt(myBytes);
console.log("result is :", result);
console.log("json result is: ",JSON.stringify(result));
console.log("base64 result is :", base64Class.encodeToString(result,0));
|
Hook 主动调用动态方法
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
|
|
Hook frida 和 python 交互
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
|
frida 传递参数
function main(){
Java.perform(function () {
console.log("enter perform");
// 获取要hook的类
var TextViewClass = Java.use("android.widget.TextView");
// 要hook的方法
TextViewClass.setText.overload('java.lang.CharSequence').implementation = function (ori_input) {
console.log('enter', 'java.lang.CharSequence');
console.log('ori_input',ori_input.toString());
// 定义用于接受python传参的data
var receive_data;
// 将原参数传递给python 在python中进行处理
send(ori_input.toString());
// recv 从python接收传递的内容 默认传过来的是个json对象
recv(function (json_data) {
console.log('data from python ' + json_data.data);
receive_data = json_data.data;
console.log(typeof (receive_data));
}).wait(); //wait() 等待python处理 阻塞
// 转java字符串
receive_data = Java.use("java.lang.String").$new(receive_data);
this.setText(receive_data);
};
})
}
setImmediate(main);
python 处理收到的参数
# -*- coding: utf-8 -*-
__author__ = "K"
__time__ = "2020-08-06 09:48"
import sys
import time
import base64
import frida
from loguru import logger
def on_message(message,data):
logger.info(str(message)) # dict
logger.info(str(data) if data else "None")
if message['type'] == 'error':
logger.error('error:' + str(message['description']))
logger.error('stack: ' + str(message['stack']))
if message['type'] == 'send':
logger.info('get message [*] --> ' + message['payload'])
payload = message['payload']
# 处理逻辑 sending to the server: YWFhOmJiYg==
tmp = payload.split(':')
sts = tmp[0]
need_to_db64 = tmp[1]
user_pass = base64.b64decode(need_to_db64.encode()).decode()
mine_str = 'admin' + ':' + user_pass.split(':')[-1]
mine_b64_str = base64.b64encode(mine_str.encode()).decode()
mine_b64_str = sts + mine_b64_str
logger.info(mine_b64_str)
# python返回数据给js script.post
script.post({'data':mine_b64_str})
logger.info('python complete')
device = frida.get_usb_device()
# pid = device.spawn(['com.kevin.demo04'])
# time.sleep(1)
session = device.attach('com.kevin.demo02')
with open('./hulianhutong.js','r') as f:
script = session.create_script(f.read())
script.on("message",on_message)
script.load()
input()
|
Hook 打印 char
Hook 打印 char 数组
Hook 打印和修改 HashMap
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
|
遍历打印
function main(){
Java.perform(function(){
var targetClass = Java.use("com.xiaojianbang.app.ShufferMap");
targetClass.show.implementation = function(map){
// 遍历 map
var result = "";
var it = map.keySet().iterator();
while (it.hasNext()){
var keyStr = it.next();
var valueStr = map.get(keyStr);
result += valueStr;
}
console.log("result :", result);
// 修改 map
map.put("pass","fxxk");
map.put("code","Hello World");
console.log(JSON.stringify(map));
this.show(map);
return this.show(map);
}
})
}
setImmediate(main);
cast打印 HashMap
function main(){
Java.perform(function(){
var HashMapNode = Java.use("java.util.HashMap$Node");
var targetClass = Java.use("com.xiaojianbang.app.ShufferMap");
var targetClass.show.implementation = function(map){
var result = "";
var iterator = map.entrySet().iterator();
while (iterator.hasNext()) {
console.log("entry", iterator.next());
var entry = Java.cast(iterator.next(), HashMapNode);
console.log(entry.getKey());
console.log(entry.getValue());
return += entry.getValue();
}
console.log("result is :", result);
}
})
}
setImmediate(main);
|
toString()打印
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
|
function main(){
Java.perform(function(){
var targetClass = Java.use("com.xiaojianbang.app.ShufferMap");
targetClass.show.implementation = function(map){
|
Hook 打印 byte 数组
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
|
方法 1
function main(){
Java.perform(function(){
var StringClass = Java.use("java.lang.String");
var byteArray = StringClass.$new("Hello World").getBytes();
// load r0gson
// openClassFile 返回 dex对象, dex对象.load()加载dex文件内容
Java.openClassFile("/data/local/tmp/r0gson.dex").load();
var gson = Java.use("com.r0ysue.gson.Gson");
console.log(gson.$new().toJson(byteArray));
// // console byte[]
// var ByteString = Java.use("com.android.okhttp.okio.ByteString");
// console.log(ByteString.of(byteArray).hex()); // byte转16进制字符串
// // 创建自定义Java数组 并打印
// var MyArray = Java.array("byte",[13,4,4,2]);
// console.log(gson.$new().toJson(MyArray));
var TargetClass = Java.use("com.xiaojianbang.app.ShufferMap");
TargetClass.show.implementation = function(map){
console.log(gson.$new().toJson(map));
return this.show(map);
}
})
}
setImmediate(main);
方法 2
// 1. 使用 java.util.Arrays.toString() 打印 [B
// 2. 使用 javascript JSON.stringify() 打印 [B
function printByteArray(){
Java.perform(function(){
var ArrayClass = Java.use("java.util.Arrays");
ArrayClass.toString.overload('[B').implementation = function(byteArray){
// 1. 使用 java.util.Arrays.toString() 打印 [B
var result = this.toString(byteArray);
// 2. 使用 javascript JSON.stringify() 打印 [B
var result1 = JSON.stringify(byteArray);
console.log('byteArray,result: ', byteArray, result);
console.log('byteArray,result1 :', byteArray, result1);
return result
}
})
}
方法 3
function printByteArray(byteArray){
Java.perform(function(){
var ByteString = Java.use("com.android.okhttp.okio.ByteString");
console.log(ByteString.of(byteArray).hex())
})
}
|
Hook 打印调用栈
1
2
3
4
5
6
7
8
9
10
11
12
13
|
function printStacks(name){
console.log("====== printStacks start ====== " + name + "==============================")
|
Hook gson 打印
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
|
function main(){
Java.perform(function(){
var StringClass = Java.use("java.lang.String");
var byteArray = StringClass.$new("Hello World").getBytes();
|
Hook 打印 non-ascii 和特殊字符
一些特殊字符和不可见字符, 可以先通过编码再解码的方式进行 hook
1
2
3
|
int ֏(int x) {
return x + 100;
}
|
针对上面的֏, 直接用js编码, 在通过类名[js解码的方法名]进行implementation
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
|
Java.perform(
function x() {
var targetClass = "com.example.hooktest.MainActivity";
var hookCls = Java.use(targetClass);
var methods = hookCls.class.getDeclaredMethods();
for (var i in methods) {
console.log(methods[i].toString());
console.log(encodeURIComponent(methods[i].toString().replace(/^.*?\.([^\s\.\(\)]+)\(.*?$/, "$1")));
}
hookCls[decodeURIComponent("%D6%8F")]
.implementation = function (x) {
console.log("original call: fun(" + x + ")");
var result = this[decodeURIComponent("%D6%8F")](900);
return result;
}
}
)
|
简易 wallbreaker 内存打印
内存漫游, 打印实例的字段和方法
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
|
function main(){
Java.perform(function(){
var Class = Java.use("java.lang.Class");
function inspectObject(obj){
var obj_class = Java.cast(obj.getClass(), Class);
var fields = obj_class.getDeclaredFields();
var methods = obj_class.getMethods();
console.log("Inspectiong " + obj.getClass().toString());
console.log("\t Fields:")
for (var i in fields){
console.log("\t\t" + fields[i].toString());
}
console.log("\t Methods:")
for (var i in methods){
console.log("\t\t" + methods[i].toString())
}
}
Java.choose("com.baidu.lbs.waimai.WaimaiActivity",{
onComplete: function(){
console.log("complete!");
},
onMatch: function(instance){
console.log("find instance", instance);
inspectObject(instance);
}
})
})
}
setImmediate(main)
|
hook frida 实现 runnable
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
|
Java.perform(function() {
|
Hook 监控控件 onClick
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
|
var jclazz = null;
var jobj = null;
function getObjClassName(obj) {
if (!jclazz) {
var jclazz = Java.use("java.lang.Class");
}
if (!jobj) {
var jobj = Java.use("java.lang.Object");
}
return jclazz.getName.call(jobj.getClass.call(obj));
}
function watch(obj, mtdName) {
var listener_name = getObjClassName(obj);
var target = Java.use(listener_name);
if (!target || !mtdName in target) {
return;
}
|
Hook startActivity
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
|
Java.perform(function () {
var Activity = Java.use("android.app.Activity");
|
Hook frida 绕过 root 检测
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
166
167
168
169
170
171
172
173
174
175
176
177
178
179
180
181
182
183
184
185
186
187
188
189
190
191
192
193
194
195
196
197
198
199
200
201
202
203
204
205
206
207
208
209
210
211
212
213
214
215
216
217
218
219
220
221
222
223
224
225
226
227
228
229
230
231
232
233
234
235
236
237
238
239
240
241
242 |

