https://flangvik.com/privesc/windows/bypass/2019/06/25/Sideload-like-your-an-APT.html
我是按照这个链接进行复现的,文章里使用的是notepad++,但是最新的notepad++已经没有了libcurl,所以我自己找的是XunjiePDFEditor.exe 这个。安装文件的名字是:Installer_迅捷PDF编辑器_r1.7.4.exe
最后获得了反弹shell:
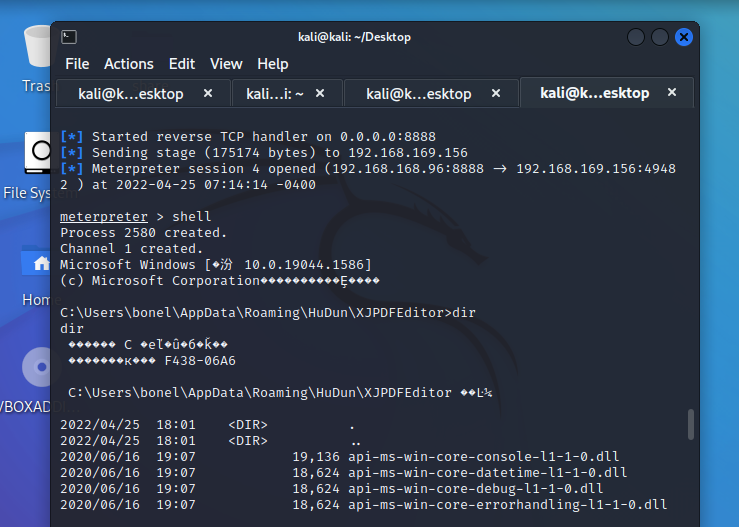
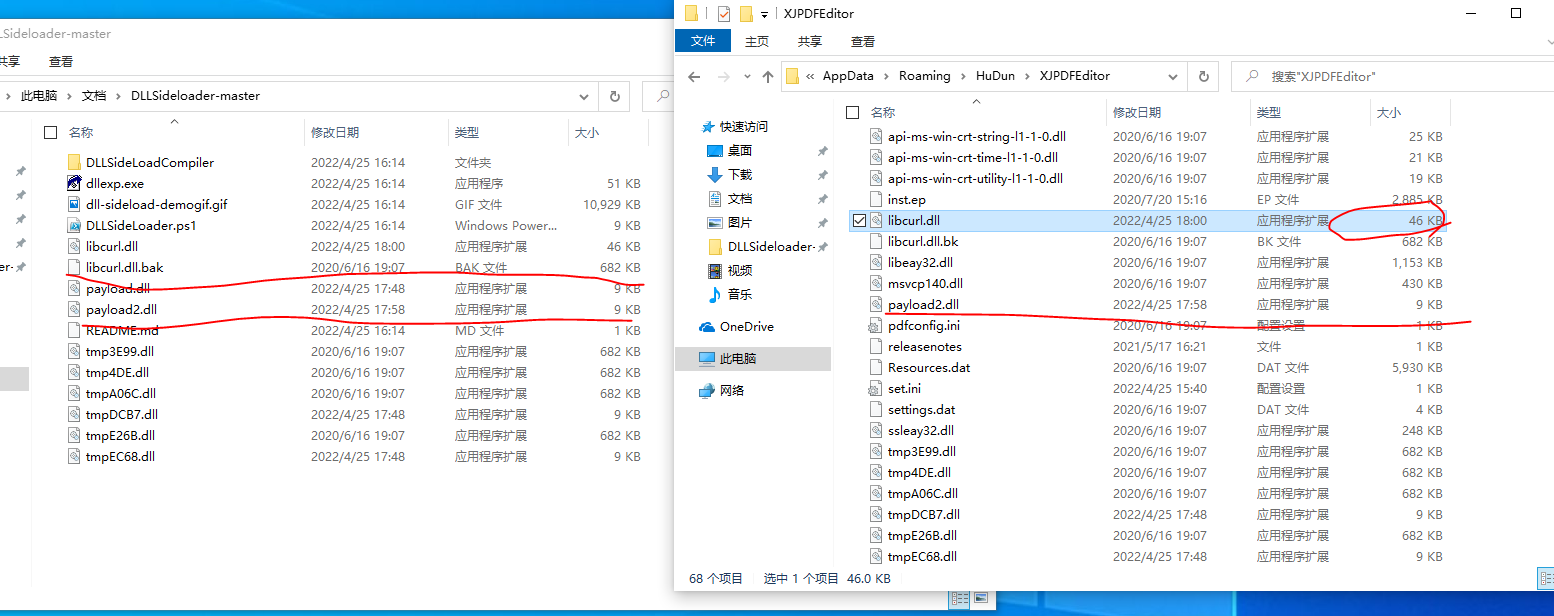
xunjiepdf的目录放置感染的DLL,原始的libcurl是682KB,而挂马的dll是46KB,双击xunjiepdfediter.exe即出现上图。
我们看下sysmon采集的数据:
1、首先是进程创建
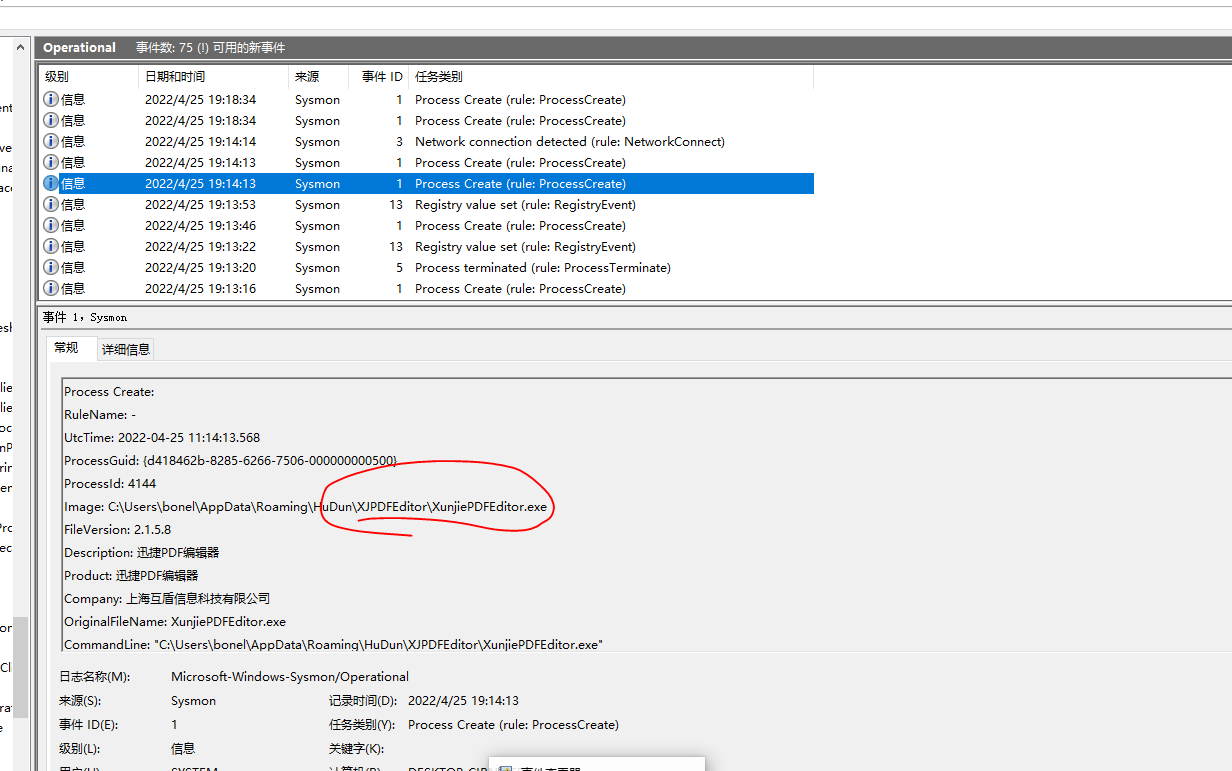
2、然后是调用dll,看来是会运行rundll32!!!所以
Process Create:
RuleName: -
UtcTime: 2022-04-25 11:14:13.608
ProcessGuid: {d418462b-8285-6266-7606-000000000500}
ProcessId: 5712
Image: C:\Windows\SysWOW64\rundll32.exe
FileVersion: 10.0.19041.746 (WinBuild.160101.0800)
Description: Windows host process (Rundll32)
Product: Microsoft® Windows® Operating System
Company: Microsoft Corporation
OriginalFileName: RUNDLL32.EXE
CommandLine: rundll32.exe
CurrentDirectory: C:\Users\bonel\AppData\Roaming\HuDun\XJPDFEditor\
User: DESKTOP-CIBNM6P\bonel
LogonGuid: {d418462b-52ca-6266-3898-030000000000}
LogonId: 0x39838
TerminalSessionId: 1
IntegrityLevel: Medium
Hashes: MD5=889B99C52A60DD49227C5E485A016679,SHA256=6CBE0E1F046B13B29BFA26F8B368281D2DDA7EB9B718651D5856F22CC3E02910,IMPHASH=30B6D4AA5B2B125B0ABCA749B5D12B3A
ParentProcessGuid: {d418462b-8285-6266-7506-000000000500}
ParentProcessId: 4144
ParentImage: C:\Users\bonel\AppData\Roaming\HuDun\XJPDFEditor\XunjiePDFEditor.exe
ParentCommandLine: "C:\Users\bonel\AppData\Roaming\HuDun\XJPDFEditor\XunjiePDFEditor.exe"
ParentUser: DESKTOP-CIBNM6P\bonel
3、这个网络连接也是rundll32这个进程发起的
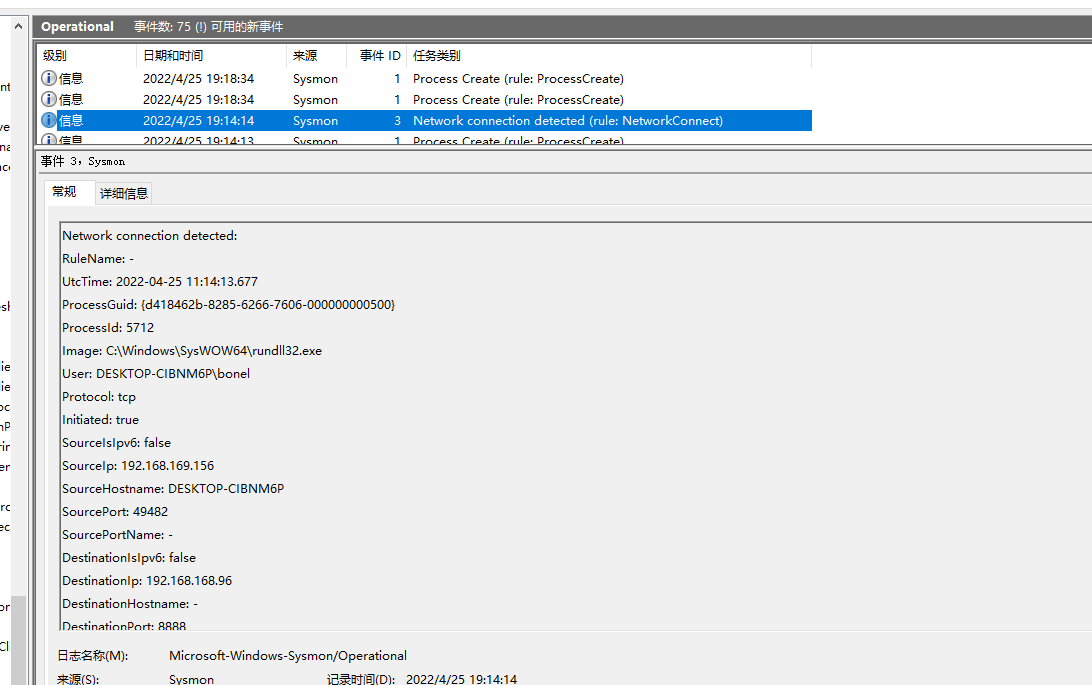
Network connection detected:
RuleName: -
UtcTime: 2022-04-25 11:14:13.677
ProcessGuid: {d418462b-8285-6266-7606-000000000500}
ProcessId: 5712
Image: C:\Windows\SysWOW64\rundll32.exe
User: DESKTOP-CIBNM6P\bonel
Protocol: tcp
Initiated: true
SourceIsIpv6: false
SourceIp: 192.168.169.156
SourceHostname: DESKTOP-CIBNM6P
SourcePort: 49482
SourcePortName: -
DestinationIsIpv6: false
DestinationIp: 192.168.168.96
DestinationHostname: -
DestinationPort: 8888
DestinationPortName: -
4、启动cmd的时候,可以看到cmd的父进程是rundll32。
Process Create:
RuleName: -
UtcTime: 2022-04-25 12:02:08.395
ProcessGuid: {d418462b-8dc0-6266-9e06-000000000500}
ProcessId: 4940
Image: C:\Windows\SysWOW64\cmd.exe
FileVersion: 10.0.19041.746 (WinBuild.160101.0800)
Description: Windows Command Processor
Product: Microsoft® Windows® Operating System
Company: Microsoft Corporation
OriginalFileName: Cmd.Exe
CommandLine: C:\Windows\system32\cmd.exe
CurrentDirectory: C:\Users\bonel\AppData\Roaming\HuDun\XJPDFEditor\
User: DESKTOP-CIBNM6P\bonel
LogonGuid: {d418462b-52ca-6266-3898-030000000000}
LogonId: 0x39838
TerminalSessionId: 1
IntegrityLevel: Medium
Hashes: MD5=D0FCE3AFA6AA1D58CE9FA336CC2B675B,SHA256=4D89FC34D5F0F9BABD022271C585A9477BF41E834E46B991DEAA0530FDB25E22,IMPHASH=392B4D61B1D1DADC1F06444DF258188A
ParentProcessGuid: {d418462b-8da8-6266-9d06-000000000500}
ParentProcessId: 1664
ParentImage: C:\Windows\SysWOW64\rundll32.exe ==》这个是检测点!!!
ParentCommandLine: rundll32.exe
ParentUser: DESKTOP-CIBNM6P\bonel
5、最后退出进程的时候会有一个注册表设置的动作
Registry value set:
RuleName: InvDB
EventType: SetValue
UtcTime: 2022-04-25 12:02:46.545
ProcessGuid: {d418462b-52a1-6266-1600-000000000500}
ProcessId: 496
Image: C:\Windows\System32\svchost.exe
TargetObject: HKU\S-1-5-21-3082954643-951221807-432565169-1001\SOFTWARE\Microsoft\Windows NT\CurrentVersion\AppCompatFlags\Compatibility Assistant\Store\C:\Users\bonel\AppData\Roaming\HuDun\XJPDFEditor\XunjiePDFEditor.exe
Details: Binary Data
User: NT AUTHORITY\SYSTEM