一、脚本配置
1.监控脚本
/etc/zabbix/zabbix_agent2.d/scripts/web_site_code_status.sh
#!/bin/bash
url_discovery() {
WEB_SITE=($(grep -v "^#" /etc/zabbix/zabbix_agent2.d/scripts/urllist.txt))
printf '{
'
printf ' "data":[
'
for((i=0;i<${#WEB_SITE[@]};++i))
{
num=$(echo $((${#WEB_SITE[@]}-1)))
tmp=${WEB_SITE[$i]}
arr=(${tmp//||/ })
name=${arr[0]}
url=${arr[1]}
code=${arr[2]}
text=${arr[3]}
if [[ "$i" != ${num} ]]
then
printf " {
"
printf " "{#WEBNAME}":"${name}",
"
printf " "{#WEBURL}":"${url}",
"
printf " "{#WEBCODE}":"${code}",
"
printf " "{#WEBTEXT}":"${text}"
},
"
else
printf " {
"
printf " "{#WEBNAME}":"${name}",
"
printf " "{#WEBURL}":"${url}",
"
printf " "{#WEBCODE}":"${code}",
"
printf " "{#WEBTEXT}":"${text}"
}"
printf "
]
}
"
fi
}
}
function get_url_code(){
tmp=`curl --connect-timeout 10 -i "$1" 2> /dev/null`
code=`echo $tmp | grep 'HTTP' | awk '{print $2}'`
#判断$3是否为空
text=$3
if [ -z "$text" ];then
textline=1
else
textline=`echo $tmp | grep $3 | wc -l`
fi
#判断是否为数字
expr $code + 0 1>/dev/null 2>&1
if [ $? -ne 0 ];then
code=0
fi
#汇总判断
if [ $code -eq $2 -a $textline -gt 0 ];then
echo 正常
else
echo 异常
fi
}
case "$1" in
web_site_discovery)
url_discovery
;;
web_site_code)
#url,code,text
get_url_code $2 $3 $4
;;
*)
echo "Usage:$0 {web_site_discovery|web_site_code URL NAME}"
;;
esac
2.监控项
路径可脚本内修改/etc/zabbix/zabbix_agent2.d/scripts/urllist.txt
#项目名||url||状态码||关键字
百度||https://www.baidu.com||200||baidu
163||www.163.com||200||163
test||www.test.com||200||ok
3.监控命令配置
/etc/zabbix/zabbix_agent2.d/web_check.conf
UserParameter=urlcheck.discovery,/etc/zabbix/zabbix_agent2.d/scripts/web_site_code_status.sh web_site_discovery
UserParameter=urlcheck.code[*],/etc/zabbix/zabbix_agent2.d/scripts/web_site_code_status.sh web_site_code $1 $2 $3 $4
4.修改agent2配置文件,启用不安全用户参数,设置下超时
Timeout=15
UnsafeUserParameters=1
5.重启agent2服务
systemctl restart zabbix-agent2
systemctl restart zabbix-server
6.测试脚本是否正常-zabbix-server端测试
zabbix_get -s 192.168.1.200 -p 10050 -k "urlcheck.discovery"
zabbix_get -s 192.168.1.200 -p 10050 -k "urlcheck.code[http://www.baidu.com,200,百度]"
二、模板配置
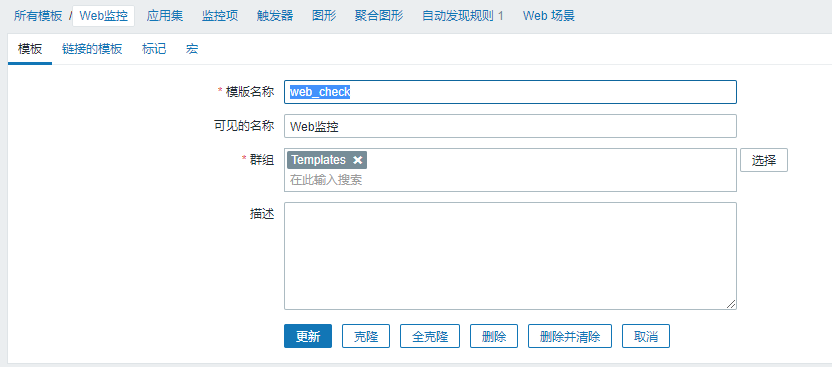
1.创建模板
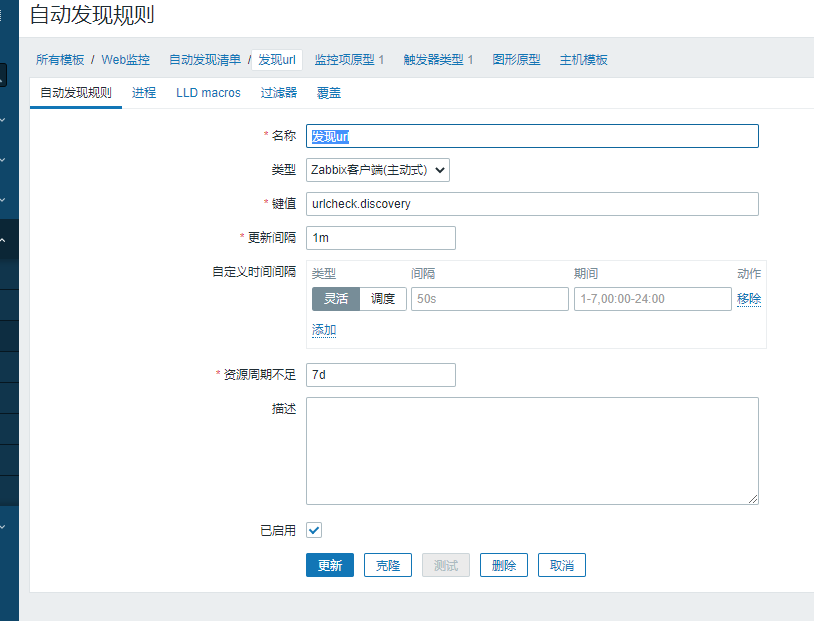
2.创建自动发现规则
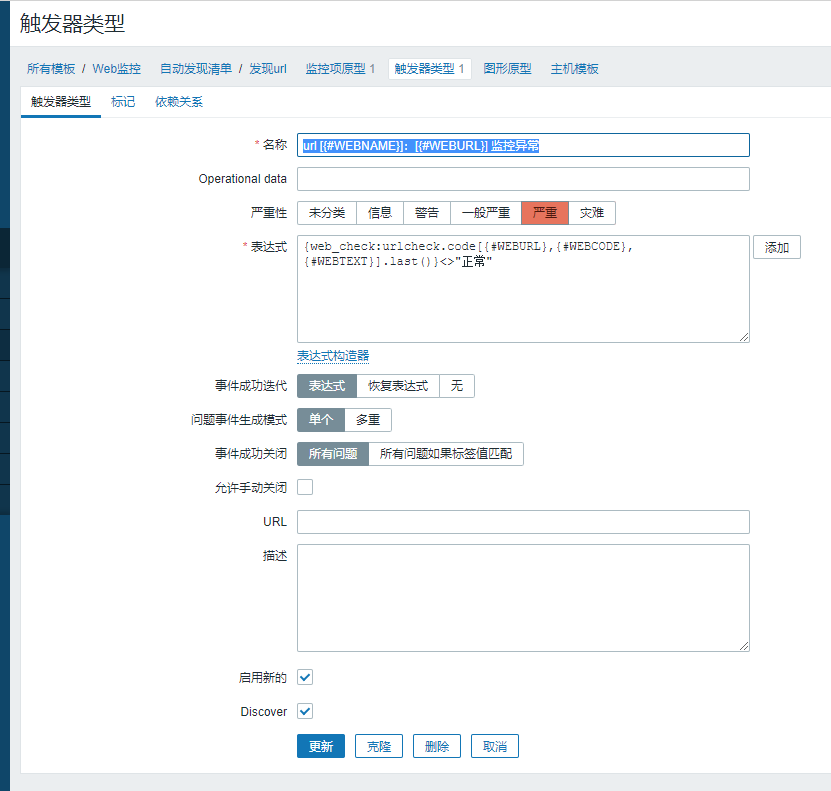
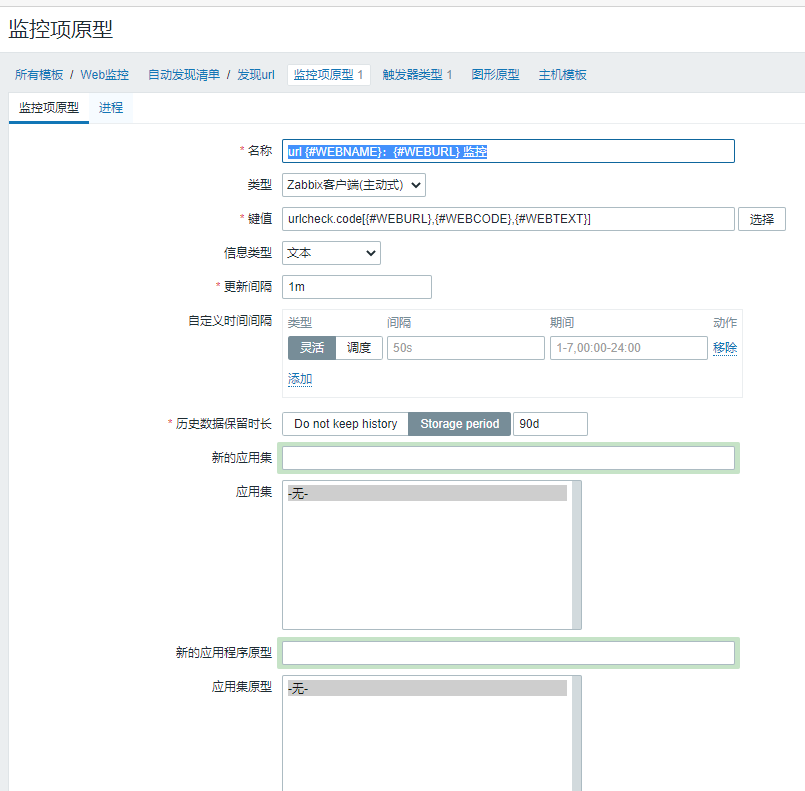
3.创建监控原型
4.创建触发器类型