2019 SDN上机第5次作业
1.浏览RYU官网学习RYU控制器的安装和RYU开发入门教程,提交你对于教程代码的理解,包括但不限于:
- 描述官方教程实现了一个什么样的交换机功能?
该应用程序使用OFPP_FLOOD标志来指示应在所有端口上发送数据包。
- 控制器设定交换机支持什么版本的OpenFlow?
OpenFlow 1.0
- 控制器设定了交换机如何处理数据包?
@set_ev_cls(ofp_event.EventOFPPacketIn, MAIN_DISPATCHER)
def packet_in_handler(self, ev):
msg = ev.msg
dp = msg.datapath
ofp = dp.ofproto
ofp_parser = dp.ofproto_parser
actions = [ofp_parser.OFPActionOutput(ofp.OFPP_FLOOD)]
out = ofp_parser.OFPPacketOut(
datapath=dp, buffer_id=msg.buffer_id,in_port=msg.in_port,
actions=actions)
dp.send_msg(out)
当Ryu收到OpenFlow packet_in消息时,将产生事件(调用"packet_in_hander"方法);
ev.msg是表示packet_in数据结构的对象;
msg.dp是代表数据路径(开关)的对象;
dp.ofproto和dp.ofproto_parser是代表Ryu和交换机协商的OpenFlow协议的对象;
actions动作列表。OFPActionOutput类与packet_out消息一起使用,以指定要从中发送数据包的交换机端口。该应用程序使用OFPP_FLOOD标志来指示应在所有端口上发送数据包;
OFPPacketOut类用于构建packet_out消息;datapath类的send_msg方法,Ryu生成联机数据格式并将其发送到交换机。
2.根据官方教程和提供的示例代码(SimpleSwitch.py),将具有自学习功能的交换机代码(SelfLearning.py)补充完整
代码如下:
from ryu.base import app_manager
from ryu.controller import ofp_event
from ryu.controller.handler import MAIN_DISPATCHER
from ryu.controller.handler import set_ev_cls
from ryu.ofproto import ofproto_v1_0
from ryu.lib.mac import haddr_to_bin
from ryu.lib.packet import packet
from ryu.lib.packet import ethernet
from ryu.lib.packet import ether_types
class SimpleSwitch(app_manager.RyuApp):
# TODO define OpenFlow 1.0 version for the switch
# add your code here
OFP_VERSIONS = [ofproto_v1_0.OFP_VERSION]#
def __init__(self, *args, **kwargs):
super(SimpleSwitch, self).__init__(*args, **kwargs)
self.mac_to_port = {}
def add_flow(self, datapath, in_port, dst, src, actions):
ofproto = datapath.ofproto
match = datapath.ofproto_parser.OFPMatch(
in_port=in_port,
dl_dst=haddr_to_bin(dst), dl_src=haddr_to_bin(src))
mod = datapath.ofproto_parser.OFPFlowMod(
datapath=datapath, match=match, cookie=0,
command=ofproto.OFPFC_ADD, idle_timeout=0, hard_timeout=0,
priority=ofproto.OFP_DEFAULT_PRIORITY,
flags=ofproto.OFPFF_SEND_FLOW_REM, actions=actions)
# TODO send modified message out
# add your code here
datapath.send_msg(mod)#
@set_ev_cls(ofp_event.EventOFPPacketIn, MAIN_DISPATCHER)
def _packet_in_handler(self, ev):
msg = ev.msg
datapath = msg.datapath
ofproto = datapath.ofproto
pkt = packet.Packet(msg.data)
eth = pkt.get_protocol(ethernet.ethernet)
if eth.ethertype == ether_types.ETH_TYPE_LLDP:
# ignore lldp packet
return
if eth.ethertype == ether_types.ETH_TYPE_IPV6:
# ignore ipv6 packet
return
dst = eth.dst
src = eth.src
dpid = datapath.id
self.mac_to_port.setdefault(dpid, {})
self.logger.info("packet in DPID:%s MAC_SRC:%s MAC_DST:%s IN_PORT:%s", dpid, src, dst, msg.in_port)
# learn a mac address to avoid FLOOD next time.
self.mac_to_port[dpid][src] = msg.in_port
if dst in self.mac_to_port[dpid]:
out_port = self.mac_to_port[dpid][dst]
else:
out_port = ofproto.OFPP_FLOOD
# TODO define the action for output
# add your code here
actions = [datapath.ofproto_parser.OFPActionOutput(out_port)]
# install a flow to avoid packet_in next time
if out_port != ofproto.OFPP_FLOOD:
self.logger.info("add flow s:DPID:%s Match:[ MAC_SRC:%s MAC_DST:%s IN_PORT:%s ], Action:[OUT_PUT:%s] ", dpid, src, dst, msg.in_port, out_port)
self.add_flow(datapath, msg.in_port, dst, src, actions)
data = None
if msg.buffer_id == ofproto.OFP_NO_BUFFER:
data = msg.data
# TODO define the OpenFlow Packet Out
# add your code here
out = datapath.ofproto_parser.OFPPacketOut(
datapath=datapath,
buffer_id=msg.buffer_id,
in_port=msg.in_port,
actions=actions, data=data)
datapath.send_msg(out)
print ("PACKET_OUT...")
3.在mininet创建一个最简拓扑,并连接RYU控制器
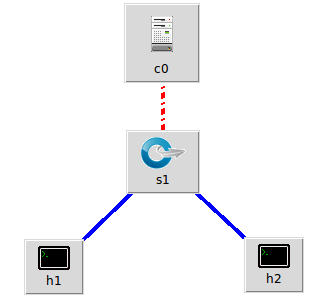
from mininet.topo import Topo
class Topo2( Topo ):
def __init__( self ):
# 初始化拓扑
Topo.__init__( self )
# 添加一台交换机和两台主机
h1 = self.addHost('h1')
h2 = self.addHost('h2')
sw1 = self.addSwitch('s1')
# 添加连接
self.addLink(h1,sw1,1,1)
self.addLink(h2,sw1,1,2)
topos = { 'mytopo': ( lambda: Topo2() ) }
通过如下指令执行py文件,语句如下:
sudo mn --custom mytopo.py --topo mytopo --controller=remote,ip=127.0.0.1,port=6633 --switch ovsk,protocols=OpenFlow10
创建成功:

4.验证自学习交换机的功能,提交分析过程和验证结果
- 打开的命令终端
- 查看流表:
sudo ovs-ofctl dump-flows s1

可看出此时流表为空。
- 测试是否ping通:

- 连接ryu控制器:
ryu-manager ./SelfLearning.py
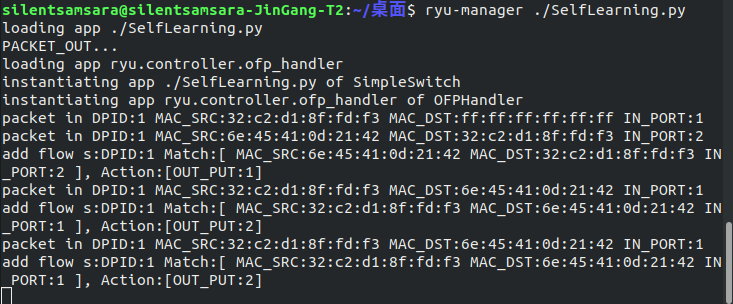
- 再次进行pingall测试
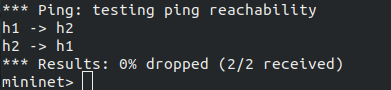
- 再次查看流表:
sudo ovs-ofctl dump-flows s1

5.实验体会
- RYU的安装过程还算顺利,但是在运行py文件时傻了一下,结果一直以为自己安装错误了。。。。
- 以为有了前几次的实验,这次实验应该很简单,但是后来发现自己对python代码还是一窍不通,只会建立简单的拓扑,通过与同学交流,才勉强补全自学习的代码