Protocol[edit]
Description[edit]
The client authenticates itself to the Authentication Server (AS) which forwards the username to a key distribution center(KDC). The KDC issues a ticket-granting ticket (TGT), which is time stamped, encrypts it using the user's password and returns the encrypted result to the user's workstation. This is done infrequently, typically at user logon; the TGT expires at some point, though may be transparently renewed by the user's session manager while they are logged in.
When the client needs to communicate with another node ("principal" in Kerberos parlance) the client sends the TGT to the ticket-granting service (TGS), which usually shares the same host as the KDC. After verifying the TGT is valid and the user is permitted to access the requested service, the TGS issues a ticket and session keys, which are returned to the client. The client then sends the ticket to the service server (SS) along with its service request.
The protocol is described in detail below.
User Client-based Logon[edit]
- A user enters a username and password on the client machines. Other credential mechanisms like pkinit (RFC4556) allow for the use of public keys in place of a password.
- The client transforms the password into the key of a symmetric cipher. This either uses the built in key scheduling or a one-way hash depending on the cipher-suite used.
Client Authentication[edit]
- The client sends a cleartext message of the user ID to the AS (Authentication Server) requesting services on behalf of the user. (Note: Neither the secret key nor the password is sent to the AS.) The AS generates the secret key by hashing the password of the user found at the database (e.g., Active Directory in Windows Server).
- The AS checks to see if the client is in its database. If it is, the AS sends back the following two messages to the client:
- Message A: Client/TGS Session Key encrypted using the secret key of the client/user.
- Message B: Ticket-Granting-Ticket (TGT, which includes the client ID, client network address, ticket validity period, and the client/TGS session key) encrypted using the secret key of the TGS.
- Once the client receives messages A and B, it attempts to decrypt message A with the secret key generated from the password entered by the user. If the user entered password does not match the password in the AS database, the client's secret key will be different and thus unable to decrypt message A. With a valid password and secret key the client decrypts message A to obtain the Client/TGS Session Key. This session key is used for further communications with the TGS. (Note: The client cannot decrypt Message B, as it is encrypted using TGS's secret key.) At this point, the client has enough information to authenticate itself to the TGS.
Client Service Authorization[edit]
- When requesting services, the client sends the following two messages to the TGS:
- Message C: Composed of the TGT from message B and the ID of the requested service.
- Message D: Authenticator (which is composed of the client ID and the timestamp), encrypted using the Client/TGS Session Key.
- Upon receiving messages C and D, the TGS retrieves message B out of message C. It decrypts message B using the TGS secret key. This gives it the "client/TGS session key". Using this key, the TGS decrypts message D (Authenticator) and sends the following two messages to the client:
- Message E: Client-to-server ticket (which includes the client ID, client network address, validity period andClient/Server Session Key) encrypted using the service's secret key.
- Message F: Client/Server Session Key encrypted with the Client/TGS Session Key.
Client Service Request[edit]
- Upon receiving messages E and F from TGS, the client has enough information to authenticate itself to the SS. The client connects to the SS and sends the following two messages:
- Message E from the previous step (the client-to-server ticket, encrypted using service's secret key).
- Message G: a new Authenticator, which includes the client ID, timestamp and is encrypted using Client/Server Session Key.
- The SS decrypts the ticket using its own secret key to retrieve the Client/Server Session Key. Using the sessions key, SS decrypts the Authenticator and sends the following message to the client to confirm its true identity and willingness to serve the client:
- The client decrypts the confirmation using the Client/Server Session Key and checks whether the timestamp is correct. If so, then the client can trust the server and can start issuing service requests to the server.
- The server provides the requested services to the client.
一、Kerberos认证简介
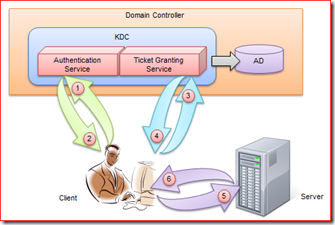 Windows认证协议有两种NTLM(NT LAN Manager)和Kerberos,前者主要应用于用于Windows NT 和 Windows 2000 Server(or Later) 工作组环境,而后者则主要应用于Windows 2000 Server(or Later) 域(Domain)环境。Kerberos较之NTLM更高效、更安全,同时认证过程也相对复杂。Kerberos这个名字来源于希腊神话,是冥界守护神兽的名字。Kerberos是一个三头怪兽,之所以用它来命名一种完全认证协议,是因为整个认证过程涉及到三方:客户端、服务端和KDC(Key Distribution Center)。在Windows域环境中,KDC的角色由DC(Domain Controller)来担当。
Windows认证协议有两种NTLM(NT LAN Manager)和Kerberos,前者主要应用于用于Windows NT 和 Windows 2000 Server(or Later) 工作组环境,而后者则主要应用于Windows 2000 Server(or Later) 域(Domain)环境。Kerberos较之NTLM更高效、更安全,同时认证过程也相对复杂。Kerberos这个名字来源于希腊神话,是冥界守护神兽的名字。Kerberos是一个三头怪兽,之所以用它来命名一种完全认证协议,是因为整个认证过程涉及到三方:客户端、服务端和KDC(Key Distribution Center)。在Windows域环境中,KDC的角色由DC(Domain Controller)来担当。
某个用户采用某个域帐号登录到某台主机,并远程访问处于相同域中另一台主机时,如何对访问者和被访问者进行身份验证(这是一种双向的验证)?这就是Kerberos需要解决的场景。接下来我尽量以比较直白的语言来介绍我所知道的Kerberos认证的整个流程。
Kerberos实际上是一种基于票据(Ticket)的认证方式。客户端要访问服务器的资源,需要首先购买服务端认可的票据。也就是说,客户端在访问服务器之前需要预先买好票,等待服务验票之后才能入场。在这之前,客户端需要先买票,但是这张票不能直接购买,需要一张认购权证。客户端在买票之前需要预先获得一张认购权证。这张认购权证和进入服务器的入场券均有KDC发售。右图(点击看大图)一张图基本揭示了Kerberos整个认证的过程。
二、如何获得“认购权证”?
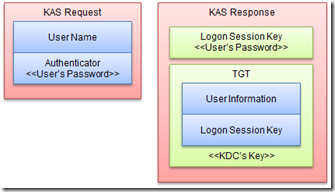 首先,我们来看看客户端如何获得“认购权证”。这里的认购权证有个专有的名称——TGT(Ticket Granting Ticket),而TGT的是KDC一个重要的服务——认证服务(KAS:Kerberos Authentication Service)。当某个用户通过输入域帐号和密码试图登录某台主机的时候,本机的Kerberos服务会向KDC的认证服务发送一个认证请求。该请求主要包括两部分内容,明文形式的用户名和经过加密的用于证明访问者身份的Authenticator(我实在找不到一个比较贴切的中文翻译没,Authenticator在这里可以理解为仅限于验证双反预先知晓的内容,相当于联络暗号)。
首先,我们来看看客户端如何获得“认购权证”。这里的认购权证有个专有的名称——TGT(Ticket Granting Ticket),而TGT的是KDC一个重要的服务——认证服务(KAS:Kerberos Authentication Service)。当某个用户通过输入域帐号和密码试图登录某台主机的时候,本机的Kerberos服务会向KDC的认证服务发送一个认证请求。该请求主要包括两部分内容,明文形式的用户名和经过加密的用于证明访问者身份的Authenticator(我实在找不到一个比较贴切的中文翻译没,Authenticator在这里可以理解为仅限于验证双反预先知晓的内容,相当于联络暗号)。
当KDC接收到请求之后,通过AD获取该用户的信息。通过获取的密码信息生成一个秘钥对Authenticator进行解密。如果解密后的内容和已知的内容一致,则证明请求着提供的密码正确,即确定了登录者的真实身份。
KAS成功认证对方的身份之后,会先生成一个用于确保该用户和KDC之间通信安全的会话秘钥——Logon Session Key,并采用该用户密码派生的秘钥进行加密。KAS接着为该用户创建“认购权证”——TGT。TGT主要包含两方面的内容:用户相关信息和Logon Session Key,而整个TGT则通过KDC自己的密钥进行加密。最终,被不同密钥加密的Logon Session Key和TGT返回给客户端。(以上的内容对应流程图中的步骤1、2)
三、如何通过“认购权证”购买“入场券”?
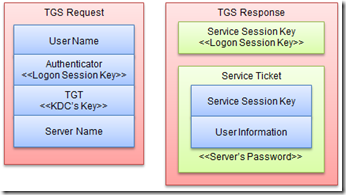 经过上面的步骤,客户端获取了购买进入同域中其他主机入场券的“认购凭证”——TGT,以及Logon Session Key,它会在本地缓存此TGT和Logon Session Key。如果现在它需要访问某台服务器的资源,它就需要凭借这张TGT向KDC购买相应的入场券。这里的入场券也有一个专有的名称——服务票据(ST:Service Ticket)。
经过上面的步骤,客户端获取了购买进入同域中其他主机入场券的“认购凭证”——TGT,以及Logon Session Key,它会在本地缓存此TGT和Logon Session Key。如果现在它需要访问某台服务器的资源,它就需要凭借这张TGT向KDC购买相应的入场券。这里的入场券也有一个专有的名称——服务票据(ST:Service Ticket)。
具体来说,ST是通过KDC的另一个服务TGS(Ticket Granting Service)出售的。客户端先向TGS发送一个ST购买请求,该请求主要包含如下的内容:客户端用户名;通过Logon Session Key加密的Authenticator;TGT和访问的服务器(其实是服务)名。
TGS接收到请求之后,现通过自己的密钥解密TGT并获取Logon Session Key,然后通过Logon Session Key解密Authenticator,进而验证了对方的真实身份。
TGS存在的一个根本的目有两点:其一是避免让用户的密码客户端和KDC之间频繁传输而被窃取。其二是因为密码属于Long Term Key(我们一般不会频繁的更新自己的密码),让它作为加密密钥的安全系数肯定小于一个频繁变换得密钥(Short Term Key)。而这个Short Term Key就是Logon Session Key,它确保了客户端和KDC之间的通信安全。
TGS完成对客户端的认证之后,会生成一个用于确保客户端-服务器之间通信安全的会话秘钥——Service Session Key,该会话秘钥通过Logon Session Key进行加密。然后出售给客户端需要的入场券——ST。ST主要包含两方面的内容:客户端用户信息和Service Session Key,整个ST通过服务器密码派生的秘钥进行加密。最终两个被加密的Service Session Key和ST回复给客户端。(以上的内容对应流程图中的步骤3、4)
四、凭票入场
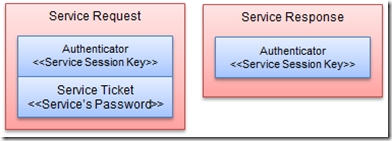 客户端接收到TGS回复后,通过缓存的Logon Session Key解密获取Service Session Key。同时它也得到了进入服务器的入场券——ST。那么它在进行服务访问的时候就可以借助这张ST凭票入场了。该Serivce Session Key和ST会被客户端缓存。
客户端接收到TGS回复后,通过缓存的Logon Session Key解密获取Service Session Key。同时它也得到了进入服务器的入场券——ST。那么它在进行服务访问的时候就可以借助这张ST凭票入场了。该Serivce Session Key和ST会被客户端缓存。
但是,服务端在接收到ST之后,如何确保它是通过TGS购买,而不是自己伪造的呢?这很好办,不要忘了ST是通过自己密码派生的秘钥进行加密的。具体的操作过程是这样的,除了ST之外,服务请求还附加一份通过Service Session Key加密的Authenticator。服务器在接收到请求之后,先通过自己密码派生的秘钥解密ST,并从中提取Service Session Key。然后通过提取出来的Service Session Key解密Authenticator,进而验证了客户端的真实身份。
实际上,到目前为止,服务端已经完成了对客户端的验证,但是,整个认证过程还没有结束。谈到认证,很多人都认为只是服务器对客户端的认证,实际上在大部分场合,我们需要的是双向验证(Mutual Authentication)——访问者和被访问者互相验证对方的身份。现在服务器已经可以确保客户端是它所声称的那么用户,客户端还没有确认它所访问的不是一个钓鱼服务呢。
为了解决客户端对服务器的验证,服务要需要将解密后的Authenticator再次用Service Session Key进行加密,并发挥给客户端。客户端再用缓存的Service Session Key进行解密,如果和之前的内容完全一样,则可以证明自己正在访问的服务器和自己拥有相同的Service Session Key,而这个会话秘钥不为外人知晓(以上的内容对应流程图中的步骤5、6)
以上的内容仅仅讲述的是基于Kerberos的Windows认证的大体流程,并不涉及到一些细节的东西,比如如何确保时间的同步,如何抵御Replay Attack等。
