参考视频:https://www.bilibili.com/video/BV1944y1y74f
先丢分析:
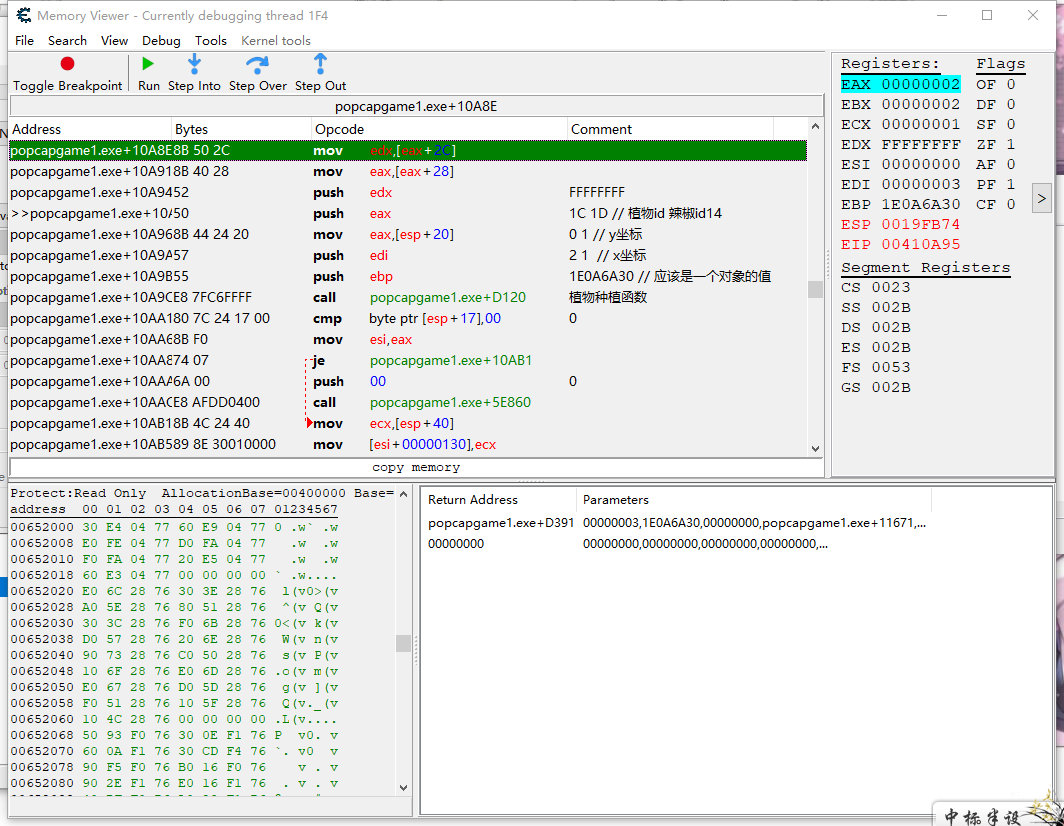
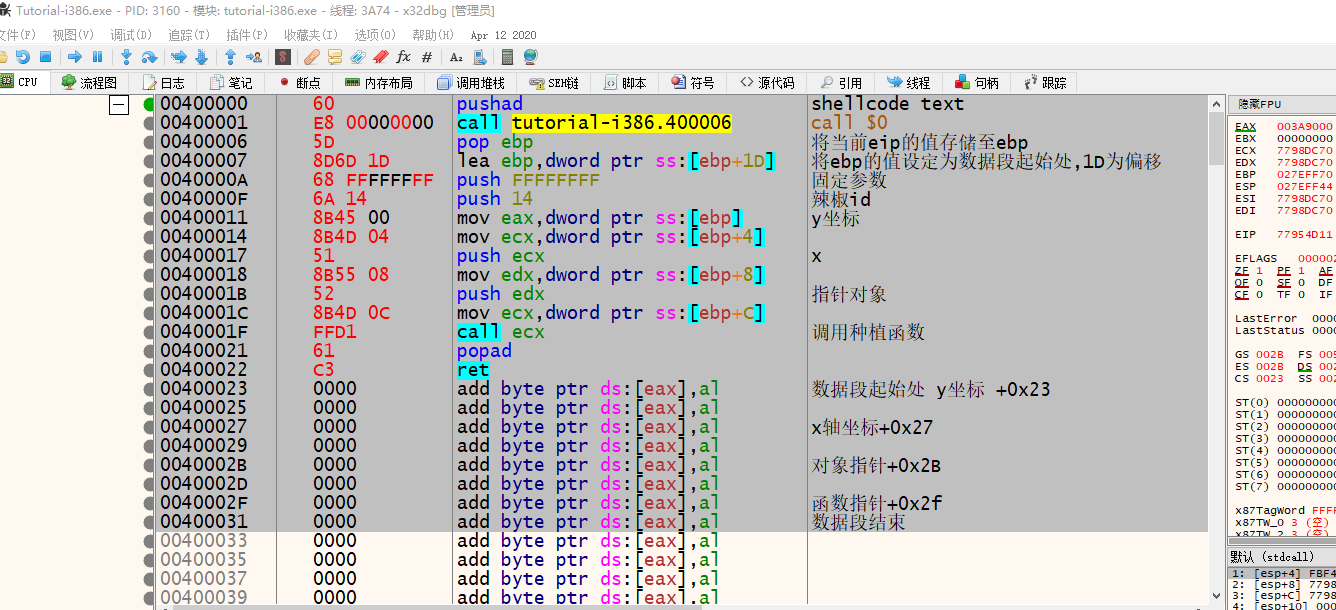
再丢代码:
int full_jalapeno(){
// 辣椒清场
/*
火爆辣椒的id是0x14
樱桃炸弹的id是0x02
找对象基地址
1E0A6A30
=[edi(00AA9E08)+00000768]
=[[6A9EC0]+00000768]
=[[popcapgame1.exe+2A9EC0]+00000768]
种植函数的偏移
=popcapgame1.exe+D120
*/
DWORD pid = GetPid("popcapgame1.exe"); // 获取进程pid
//获取进程句柄
HANDLE hProcess;
hProcess = OpenProcess(PROCESS_ALL_ACCESS,FALSE,pid);
printf("%x
", hProcess);
if (hProcess == NULL)
{
printf("fail to open process
");
CloseHandle(hProcess);
return -1;
}
// 获取模块地址
DWORD modaddr = NULL;
MODULEENTRY32 modentry;
HANDLE hSnapshot = CreateToolhelp32Snapshot(TH32CS_SNAPMODULE, pid);
modentry.dwSize = sizeof(MODULEENTRY32); // 初始化一下
Module32First(hSnapshot, &modentry);
do{
if (!strcmp(modentry.szModule, "popcapgame1.exe")){
modaddr = (DWORD)(modentry.hModule);
printf("Module Found, addr: %x
", modaddr);
CloseHandle(hSnapshot);
break;
}
//遍历查找模块名
}while (Module32Next(hSnapshot, &modentry));
// ---------创建并调用shellcode
BYTE shellcode[1024] = {
0x60, 0xE8, 0x00, 0x00, 0x00, 0x00, 0x5D, 0x8D, 0x6D, 0x1D, 0x68, 0xFF, 0xFF, 0xFF, 0xFF, 0x6A,
0x14, 0x8B, 0x45, 0x00, 0x8B, 0x4D, 0x04, 0x51, 0x8B, 0x55, 0x08, 0x52, 0x8B, 0x4D, 0x0C, 0xFF,
0xD1, 0x61, 0xC3, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00,
0x00, 0x00, 0x00
};
// 数据
DWORD x = 0;
DWORD y = 0;
DWORD pObj = modaddr; // 对象地址获取
ReadProcessMemory(hProcess, (LPCVOID)(0x6A9EC0), &pObj, 4, NULL);
ReadProcessMemory(hProcess, (LPCVOID)(pObj + 0x768), &pObj, 4, NULL);
DWORD pFunc = modaddr + 0xD120;
// 修改数据
*(DWORD*)(shellcode + 0x23) = y;
*(DWORD*)(shellcode + 0x27) = x;
*(DWORD*)(shellcode + 0x2B) = pObj;
*(DWORD*)(shellcode + 0x2F) = pFunc;
// 分配一块空间
LPVOID calladdr = VirtualAllocEx(hProcess, NULL, 1024, MEM_COMMIT, PAGE_EXECUTE_READWRITE);
// 写shellcode
WriteProcessMemory(hProcess, calladdr, shellcode, 1024, NULL);
while (1){
// 修改shellcode数据
WriteProcessMemory(hProcess, ((BYTE*)calladdr+0x23), &y, 4, NULL);
//创建远程线程
HANDLE hRemote = CreateRemoteThread(
hProcess, NULL, NULL, (LPTHREAD_START_ROUTINE)calladdr,NULL,NULL,NULL
);
WaitForSingleObject(hRemote, INFINITE);
CloseHandle(hRemote);
y++;
if (y==5){
break;
}
Sleep(100);
}
CloseHandle(hProcess);
return 1;
}