一、简介
pkcs12命令能生成和分析pkcs12文件
二、语法
openssl pkcs12 [-export] [-chain] [-inkey filename] [-certfile filename] [-CApath arg] [-CAfile arg] [-name name] [-caname name] [-in filename] [-out filename] [-noout] [-nomacver] [-nocerts] [-clcerts] [-cacerts] [-nokeys] [-info] [-noiter] [-maciter] [-nomaciter] [-nomac] [-twopass] [-descert] [-certpbe alg] [-keypbe alg] [-macalg digest] [-keyex] [-keysig] [-password arg] [-passin arg] [-passout arg] [-rand file(s)] [-LMK] [-CSP name][-engine e] [-des] [-des3] [-aes128] [-aes192] [-aes256] [-idea] [-camellia128] [-camellia192] [-camellia256] [-nodes]
选项
-export output PKCS12 file -chain add certificate chain -inkey file private key if not infile -certfile f add all certs in f -CApath arg - PEM format directory of CA's -CAfile arg - PEM format file of CA's -name "name" use name as friendly name -caname "nm" use nm as CA friendly name (can be used more than once). -in infile input filename -out outfile output filename -noout don't output anything, just verify. -nomacver don't verify MAC. -nocerts don't output certificates. -clcerts only output client certificates. -cacerts only output CA certificates. -nokeys don't output private keys. -info give info about PKCS#12 structure. -des encrypt private keys with DES -des3 encrypt private keys with triple DES (default) -idea encrypt private keys with idea -seed encrypt private keys with seed -aes128, -aes192, -aes256 encrypt PEM output with cbc aes -camellia128, -camellia192, -camellia256 encrypt PEM output with cbc camellia -nodes don't encrypt private keys -noiter don't use encryption iteration -nomaciter don't use MAC iteration -maciter use MAC iteration -nomac don't generate MAC -twopass separate MAC, encryption passwords -descert encrypt PKCS#12 certificates with triple DES (default RC2-40) -certpbe alg specify certificate PBE algorithm (default RC2-40) -keypbe alg specify private key PBE algorithm (default 3DES) -macalg alg digest algorithm used in MAC (default SHA1) -keyex set MS key exchange type -keysig set MS key signature type -password p set import/export password source -passin p input file pass phrase source -passout p output file pass phrase source -engine e use engine e, possibly a hardware device. -rand file:file:... load the file (or the files in the directory) into the random number generator -CSP name Microsoft CSP name -LMK Add local machine keyset attribute to private key
三、实例
1、PKCS与PEM格式互转
1)PEM转成PKCS12文件(包含CA证书、不包含CA证书)
openssl pkcs12 -export -inkey serverprikey.pem -in server.pem -CAfile demoCA/cacert.pem -password pass:"123456" -out server.pfx
openssl pkcs12 -export -inkey serverprikey.pem -in server.pem -password pass:"123456" -out server_nocret.pfx
2)PKCS12转成PEM文件
openssl pkcs12 -in server_nocret.pfx -out server_nocret.pem -nodes -password pass:"123456"
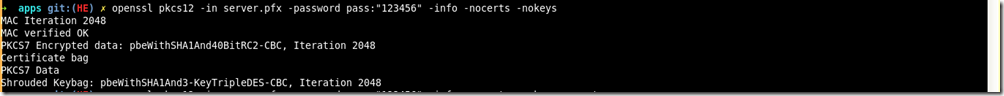
2、查看pkcs12信息
openssl pkcs12 -in server.pfx -password pass:"123456" -info -nocerts –nokeys