volatility
kdbgscan:这个插件可以扫描文件的profile的值,通常扫描结果有多个,只有一个结果是完全正确的,kdbgscan和imageinfo都只适用于windows的镜像
lsadump : 获取本地认证服务信息,lsass.exe是处理密码变更以及验证尝试登录到计算机的用户
内存取证第一题
PS D:\Tool\volatility_2.6_win64_standalone\volatility_2.6_win64_standalone> ./volatility_2.6_win64_standalone.exe -f .\Target.vmem kdbgscan
Volatility Foundation Volatility Framework 2.6
Interrupted
PS D:\Tool\volatility_2.6_win64_standalone\volatility_2.6_win64_standalone> ./volatility_2.6_win64_standalone.exe -f Target.vmem kdbgscan
Volatility Foundation Volatility Framework 2.6
**************************************************
Instantiating KDBG using: D:\Tool\volatility_2.6_win64_standalone\volatility_2.6_win64_standalone\Target.vmem WinXPSP2x86 (5.1.0 32bit)
Offset (P) : 0x403c0a0
KDBG owner tag check : True
Profile suggestion (KDBGHeader): Win7SP1x64
PsActiveProcessHead : 0x4072b90
PsLoadedModuleList : 0x4090e90
KernelBase : 0xfffff80003e4b000
**************************************************
Instantiating KDBG using: D:\Tool\volatility_2.6_win64_standalone\volatility_2.6_win64_standalone\Target.vmem WinXPSP2x86 (5.1.0 32bit)
Offset (P) : 0x403c0a0
KDBG owner tag check : True
Profile suggestion (KDBGHeader): Win7SP0x64
PsActiveProcessHead : 0x4072b90
PsLoadedModuleList : 0x4090e90
KernelBase : 0xfffff80003e4b000
**************************************************
Instantiating KDBG using: D:\Tool\volatility_2.6_win64_standalone\volatility_2.6_win64_standalone\Target.vmem WinXPSP2x86 (5.1.0 32bit)
Offset (P) : 0x403c0a0
KDBG owner tag check : True
Profile suggestion (KDBGHeader): Win2008R2SP1x64
PsActiveProcessHead : 0x4072b90
PsLoadedModuleList : 0x4090e90
KernelBase : 0xfffff80003e4b000
**************************************************
Instantiating KDBG using: D:\Tool\volatility_2.6_win64_standalone\volatility_2.6_win64_standalone\Target.vmem WinXPSP2x86 (5.1.0 32bit)
Offset (P) : 0x403c0a0
KDBG owner tag check : True
Profile suggestion (KDBGHeader): Win7SP1x64_23418
PsActiveProcessHead : 0x4072b90
PsLoadedModuleList : 0x4090e90
KernelBase : 0xfffff80003e4b000
**************************************************
Instantiating KDBG using: D:\Tool\volatility_2.6_win64_standalone\volatility_2.6_win64_standalone\Target.vmem WinXPSP2x86 (5.1.0 32bit)
Offset (P) : 0x403c0a0
KDBG owner tag check : True
Profile suggestion (KDBGHeader): Win2008R2SP0x64
PsActiveProcessHead : 0x4072b90
PsLoadedModuleList : 0x4090e90
KernelBase : 0xfffff80003e4b000
**************************************************
Instantiating KDBG using: D:\Tool\volatility_2.6_win64_standalone\volatility_2.6_win64_standalone\Target.vmem WinXPSP2x86 (5.1.0 32bit)
Offset (P) : 0x403c0a0
KDBG owner tag check : True
Profile suggestion (KDBGHeader): Win2008R2SP1x64_23418
PsActiveProcessHead : 0x4072b90
PsLoadedModuleList : 0x4090e90
KernelBase : 0xfffff80003e4b000
ERROR : volatility.debug : Please specify a dump directory (--dump-dir)
PS D:\Tool\volatility_2.6_win64_standalone\volatility_2.6_win64_standalone> ./volatility_2.6_win64_standalone.exe -f Target.vmem --profile=Win7SP1x64 lsadump
Volatility Foundation Volatility Framework 2.6
DefaultPassword
0x00000000 48 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 H...............
0x00000010 66 00 6c 00 61 00 67 00 7b 00 57 00 33 00 31 00 f.l.a.g.{.W.3.1.
0x00000020 43 00 30 00 4d 00 33 00 20 00 54 00 30 00 20 00 C.0.M.3...T.0...
0x00000030 54 00 48 00 69 00 53 00 20 00 33 00 34 00 53 00 T.H.i.S...3.4.S.
0x00000040 59 00 20 00 46 00 30 00 52 00 33 00 4e 00 53 00 Y...F.0.R.3.N.S.
0x00000050 69 00 43 00 58 00 7d 00 00 00 00 00 00 00 00 00 i.C.X.}.........
DPAPI_SYSTEM
0x00000000 2c 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ,...............
0x00000010 01 00 00 00 49 06 16 35 a7 90 b6 2a 53 69 03 27 ....I..5...*Si.'
0x00000020 b9 9a 60 9e 9a 15 90 37 7c cf 1d 3c f1 3f 60 05 ..`....7|..<.?`.
0x00000030 56 c1 59 68 53 9a dc e0 18 b3 55 ef 00 00 00 00 V.YhS.....U.....
PS D:\Tool\volatility_2.6_win64_standalone\volatility_2.6_win64_standalone>
内存取证第二题:虚拟机中有一个某品牌手机的备份文件,文件里的图片里的字符串为
filescan 发现可以目录CTF
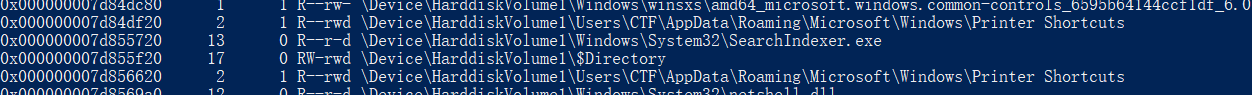filescan | grep "CTF",在最下面发现手机型号HUAWEI


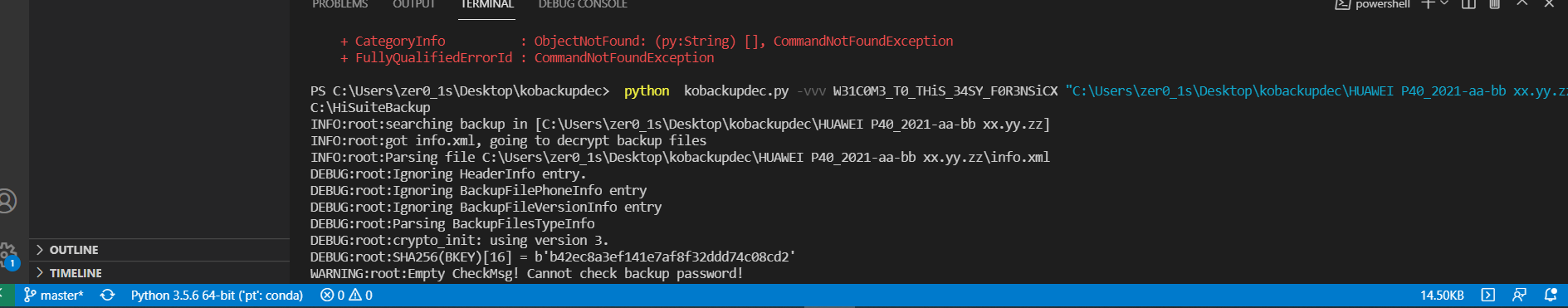
./volatility_2.6_win64_standalone.exe -f Target.vmem --profile=--profile=Win7SP1x64 dumpfiles -Q 0x7d8c7d10 -D ./ -u

python kobackupdec.py -vvv W31C0M3_T0_THiS_34SY_F0R3NSiCX "C:\Users\zer0_1s\Desktop\kobackupdec\HUAWEI P40_2021-aa-bb xx.yy.zz" C:\HiSuiteBackup
dump下来对应目录,之后解压