不多说,直接上干货!
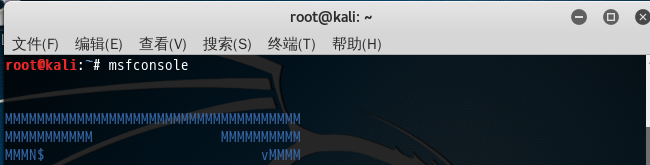
root@kali:~# msfconsole MMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMM MMMMMMMMMMM MMMMMMMMMM MMMN$ vMMMM MMMNl MMMMM MMMMM JMMMM MMMNl MMMMMMMN NMMMMMMM JMMMM MMMNl MMMMMMMMMNmmmNMMMMMMMMM JMMMM MMMNI MMMMMMMMMMMMMMMMMMMMMMM jMMMM MMMNI MMMMMMMMMMMMMMMMMMMMMMM jMMMM MMMNI MMMMM MMMMMMM MMMMM jMMMM MMMNI MMMMM MMMMMMM MMMMM jMMMM MMMNI MMMNM MMMMMMM MMMMM jMMMM MMMNI WMMMM MMMMMMM MMMM# JMMMM MMMMR ?MMNM MMMMM .dMMMM MMMMNm `?MMM MMMM` dMMMMM MMMMMMN ?MM MM? NMMMMMN MMMMMMMMNe JMMMMMNMMM MMMMMMMMMMNm, eMMMMMNMMNMM MMMMNNMNMMMMMNx MMMMMMNMMNMMNM MMMMMMMMNMMNMMMMm+..+MMNMMNMNMMNMMNMM http://metasploit.com Easy phishing: Set up email templates, landing pages and listeners in Metasploit Pro -- learn more on http://rapid7.com/metasploit =[ metasploit v4.12.41-dev ] + -- --=[ 1597 exploits - 912 auxiliary - 274 post ] + -- --=[ 458 payloads - 39 encoders - 8 nops ] + -- --=[ Free Metasploit Pro trial: http://r-7.co/trymsp ] msf > help Core Commands ============= Command Description ------- ----------- ? Help menu advanced Displays advanced options for one or more modules back Move back from the current context banner Display an awesome metasploit banner cd Change the current working directory color Toggle color connect Communicate with a host edit Edit the current module with $VISUAL or $EDITOR exit Exit the console get Gets the value of a context-specific variable getg Gets the value of a global variable grep Grep the output of another command help Help menu info Displays information about one or more modules irb Drop into irb scripting mode jobs Displays and manages jobs kill Kill a job load Load a framework plugin loadpath Searches for and loads modules from a path makerc Save commands entered since start to a file options Displays global options or for one or more modules popm Pops the latest module off the stack and makes it active previous Sets the previously loaded module as the current module pushm Pushes the active or list of modules onto the module stack quit Exit the console reload_all Reloads all modules from all defined module paths rename_job Rename a job resource Run the commands stored in a file route Route traffic through a session save Saves the active datastores search Searches module names and descriptions sess Interact with a given session sessions Dump session listings and display information about sessions set Sets a context-specific variable to a value setg Sets a global variable to a value show Displays modules of a given type, or all modules sleep Do nothing for the specified number of seconds spool Write console output into a file as well the screen threads View and manipulate background threads unload Unload a framework plugin unset Unsets one or more context-specific variables unsetg Unsets one or more global variables use Selects a module by name version Show the framework and console library version numbers Database Backend Commands ========================= Command Description ------- ----------- creds List all credentials in the database db_connect Connect to an existing database db_disconnect Disconnect from the current database instance db_export Export a file containing the contents of the database db_import Import a scan result file (filetype will be auto-detected) db_nmap Executes nmap and records the output automatically db_rebuild_cache Rebuilds the database-stored module cache db_status Show the current database status hosts List all hosts in the database loot List all loot in the database notes List all notes in the database services List all services in the database vulns List all vulnerabilities in the database workspace Switch between database workspaces msf >
creads:查看数据库中所有的证书
db_connect:连接到一个已经存在的数据库
disconnetc:断开数据库连接
export:导出数据库内容到一个文件
import:导入一个数据库文件
nmap:数据库扫描工具
rebuild cache:重建缓存
loot:查看数据库中有哪些主机被渗透攻击成功的
note:显示扫描主机的备注,目标主机的一些信息,例如目标主机的系统版本
vulns:查看数据库扫描的主机的漏洞
workspace:在数据库中创建不同的工作空间,相对于独立的
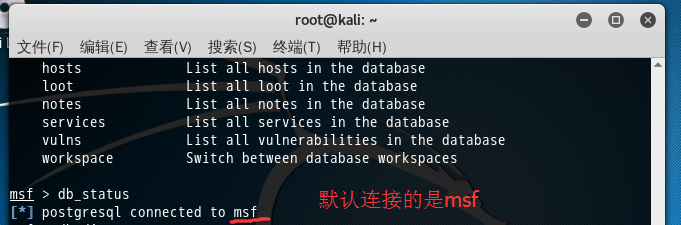
msf > db_status
[*] postgresql connected to msf
如果你在这一步,出现如下情况,则是你连接出问题了,请见
Kali linux2.0里Metasploit的postgresql selected, no connection问题解决
然后,接下来,大家可以跟我这里一样,自己新建用户和密码。
1、 postgresql启动
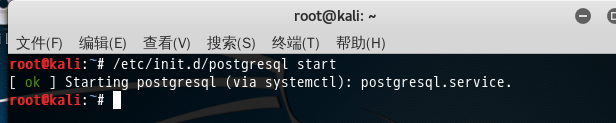
/etc/init.d/postgresql start 或者 service postgresql start
2、切换到postgre数据库,进行配置
sudo -u postgres psql postgres alter user postgres with password 'postgres'; //改变用户postgres的密码“postgres ”
即以管理员的身份切换到postgres用户下, psql postgres 即以切换到postgres数据库下。
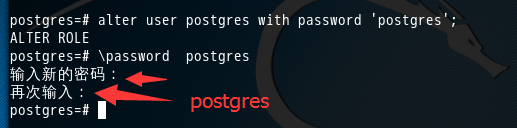
postgres=# alter user postgres with password 'postgres'; ALTER ROLE postgres=# password postgres 输入新的密码: 再次输入: postgres=#
注意1:’postgres ’ 这个是密码。
注意2:分号!!!! 一定要带上分号”;”。

注意3:q:退出数据库
再,
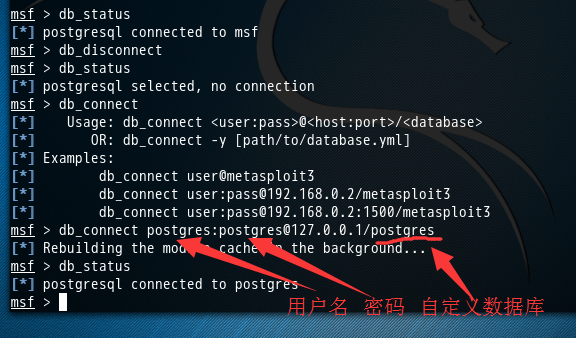
msf > db_status [*] postgresql connected to msf msf > db_disconnect msf > db_status [*] postgresql selected, no connection msf > db_connect [*] Usage: db_connect <user:pass>@<host:port>/<database> [*] OR: db_connect -y [path/to/database.yml] [*] Examples: [*] db_connect user@metasploit3 [*] db_connect user:pass@192.168.0.2/metasploit3 [*] db_connect user:pass@192.168.0.2:1500/metasploit3 msf > db_connect postgres:postgres@127.0.0.1/postgres [*] Rebuilding the module cache in the background... msf > db_status [*] postgresql connected to postgres msf >
欧克,成功!
成功链接到我们刚自定义创建好的数据库postgres后,可以用db_nmap命令,这个命令能够在MSF终端中运行nmap,并自动将
msf > db_nmap -sS -A 192.168.1.103
会保存到这个自定义创建的数据库postgres里。
后续工作,我不赘述了。