原文来自:http://guojiping.blog.51cto.com/5635432/985885
一、原理介绍:
SNMP简介
目前网络中用得最广泛的网络管理协议是SNMP(Simple Network Management Protocol,简单网络管理协议)。SNMP是被广泛接受并投入使用的工业标准,用于保证管理信息在网络中任意两点间传送,便于网络管理员在网络上的任何节点检索信息、修改信息、定位故障、完成故障诊断、进行容量规划和生成报告。
SNMP采用轮询机制,只提供最基本的功能集,特别适合在小型、快速和低价格的环境中使用。SNMP的实现基于无连接的传输层协议UDP,因此可以实现和众多产品的无障碍连接
SNMP的工作机制
SNMP分为NMS和Agent两部分:
NMS(Network Management Station,网络管理站)是运行客户端程序的工作站,目前常用的网管平台有QuidView、Sun NetManager和IBM NetView。
Agent是运行在网络设备上的服务器端软件。
NMS可以向Agent发出GetRequest、GetNextRequest和SetRequest报文,Agent接收到NMS的这些请求报文后,根据报文类型进行Read或Write操作,生成Response报文,并将报文返回给NMS。
Agent在设备发生异常情况或状态改变时(如设备重新启动),也会主动向NMS发送Trap报文,向NMS汇报所发生的事件。
SNMP的版本
目前,设备中的SNMP Agent支持SNMP v3版本,兼容SNMP v1版本、SNMP v2C版本。
SNMP v3采用用户名和密码认证方式。
SNMP v1、SNMP v2C采用团体名(Community Name)认证,非设备认可团体名的SNMP报文将被丢弃。SNMP团体名用来定义SNMP NMS和SNMP Agent的关系。团体名起到了类似于密码的作用,可以限制SNMP NMS访问设备上的SNMP Agent。用户可以选择指定以下一个或者多个与团体名相关的特性:
1.定义团体名可以访问的MIB视图。
2.设置团体名对MIB对象的访问权限为读写权限(write)或者只读权限(read)。具有只读权限的团体名只能对设备信息进行查询,而具有读写权限的团体名还可以对设备进行配置。
3.设置团体名指定的基本访问控制列表。
设备支持的MIB
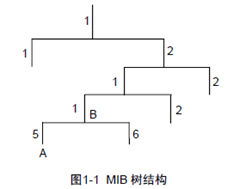
在SNMP报文中用管理变量来描述设备中的管理对象。为了唯一标识设备中的管理对象,SNMP用层次结构命名方案来识别管理对象。整个层次结构就像一棵树,树的节点表示管理对象,如下图1-1所示。每一个节点,都可以用从根开始的一条路径唯一地标识。
MIB(Management Information Base,管理信息库)的作用就是用来描述树的层次结构,它是所监控网络设备的标准变量定义的集合。在图1-1中,管理对象B可以用一串数字{1.2.1.1}唯一确定,这串数字是管理对象的对象标识符(Object Identifier)。
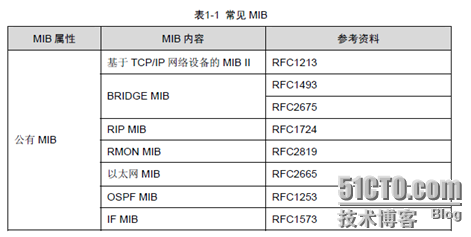
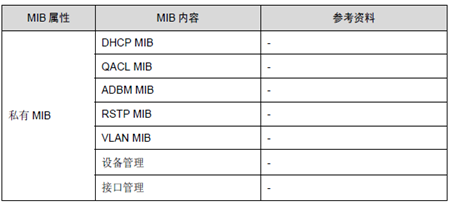
系统支持的常见MIB如下表1-1所示。
二、案例分析及使用:
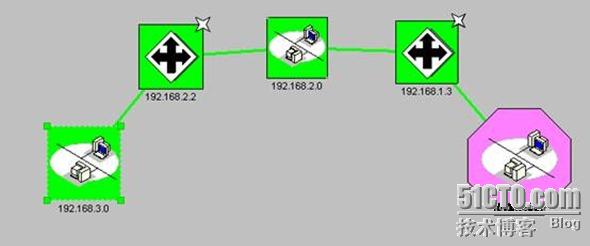
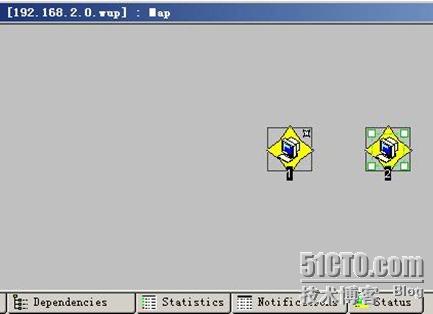
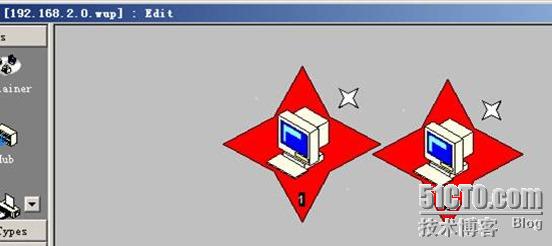
1.实验拓扑图:
注意:windows server 2003 是在虚拟机中安装,桥接到本地连接1上使用!
2.设备配置:
交换机配置:
[Quidway]int Vlan-interface 1
[Quidway-Vlan-interface1]ip add 192.168.1.2 255.255.255.0
[Quidway-Vlan-interface1]quit
[Quidway]ip route-static 0.0.0.0 0.0.0.0 192.168.1.3 //默认网关
[Quidway]snmp-agent // 启动snmp
[Quidway]snmp-agent ?
community Set a community for the access of SNMPv1&SNMPv2c
group Set an SNMP group based on USM
local-engineid Set the engineID of local SNMP entity
mib-view Set SNMP MIB view information
packet Set SNMP packet's parameters
sys-info Set system information of the node
target-host Set the target hosts to receive SNMP notification/trap
packets
trap Set trap or notification parameters
usm-user Set a new user for access to SNMP entity
<cr>
[Quidway]snmp-agent sys-info ?
contact Set the contact information for system maintenance
location Set the physical position information of this node
version Enable the SNMP protocol version
[Quidway]snmp-agent sys-info contact zhaoke
[Quidway]snmp-agent sys-info location zhengzhou
[Quidway]snmp-agent sys-info version ? //版本信息
all Enable the device to support SNMPv1, SNMPv2c and SNMPv3
v1 Enable the device to support SNMPv1
v2c Enable the device to support SNMPv2c
v3 Enable the device to support SNMPv3
[Quidway]snmp-agent sys-info version all
[Quidway]snmp-agent community ?
read Read-only access for this community in the view
write Read-write access for this community in the view
[Quidway]snmp-agent community read public
[Quidway]snmp-agent community write private
[Quidway]snmp-agent trap ?
enable SNMP trap/notification enable commands group
life Set the trap aging time
queue-size Length of each TRAP message queue
source Set the source address of SNMPv1 trap packet
[Quidway]snmp-agent trap enable //打开陷阱功能
[Quidway]snmp-agent target-host ?
trap Specify the target to be trap host
[Quidway]snmp-agent target-host trap ?
address Specify the transport addresses to be used in the generation of SNMP
messages
[Quidway]snmp-agent target-host trap address ?
udp-domain Specify transport domain over UDP for the target host
[Quidway]snmp-agent target-host trap address udp-d
[Quidway]snmp-agent target-host trap address udp-domain ?
X.X.X.X IP address of target host
[Quidway]snmp-agent target-host trap address udp-domain 192.168.1.100 ?
params Specify SNMP target information to be used in the generation of
SNMP messages
udp-port Set port to receive traps/notifications for this target host
[Quidway]snmp-agent target-host trap address udp-domain 192.168.1.100 params ?
securityname Specify the name for the principal on whose behalf SNMP
messages will be generated
[Quidway]snmp-agent target-host trap address udp-domain 192.168.1.100 params secu
[Quidway]snmp-agent target-host trap address udp-domain 192.168.1.100 params securityname ?
STRING<1-32> Specify the character string of security name
[Quidway]snmp-agent target-host trap address udp-domain 192.168.1.100 params securityname public
路由器R2的配置:
[Router]sysname R2
[R2]int e1
[R2-Ethernet1]ip add 192.168.1.3 24
[R2-Ethernet1]int s0
[R2 -Serial0]ip add 192.168.2.1 24
[R2-Serial0]
%01:02:44: Line protocol ip on the interface Serial0 is UP
[Router-Serial0]quit
[R2]display ip routing
Routing Tables:
Destination/Mask Proto Pref Metric Nexthop Interface
127.0.0.0/8 Direct 0 0 127.0.0.1 LoopBack0
127.0.0.1/32 Direct 0 0 127.0.0.1 LoopBack0
192.168.1.0/24 Direct 0 0 192.168.1.3 Ethernet1
192.168.1.3/32 Direct 0 0 127.0.0.1 LoopBack0
192.168.2.0/24 Direct 0 0 192.168.2.1 Serial0
192.168.2.1/32 Direct 0 0 127.0.0.1 LoopBack0
[R2]ip route-static 192.168.3.0 24 192.168.2.2
[R2]ping 192.168.1.2
PING 192.168.1.2: 56 data bytes, press CTRL_C to break
Request time out
Reply from 192.168.1.2: bytes=56 Sequence=1 ttl=255 time = 32 ms
Reply from 192.168.1.2: bytes=56 Sequence=2 ttl=255 time = 14 ms
Reply from 192.168.1.2: bytes=56 Sequence=3 ttl=255 time = 9 ms
Reply from 192.168.1.2: bytes=56 Sequence=4 ttl=255 time = 12 ms
[R2]snmp-agent ?
<cr> Enable SNMP agent
community Configure community string access
group Configure a group security version
local-engineID Configure the local-engine ID string
mib-view Specify MIB family inclusions and exclusions
packet Configure the max packet size
sys-info Specify the SNMP system information
target-host Specify the SNMP trap host address
trap Configure SNMP traps
usm-user Configure a SNMP user
[R2]snmp-agent
[R2]snmp-agent sys-info contact zouyunxia
[R2]snmp-agent sys-info location xuchang
[R2]snmp-agent sys-info version all
[R2]snmp-agent community ?
read Specify read-only access
write Specify read-write access
[R2]snmp-agent community read public
[R2]snmp-agent community write private
[R2]snmp-agent trap ?
enable Enable SNMP trap
life Specify timeout of SNMP trap
queue-size Specify the length of SNMP trap queue
source Specify source address for sending SNMP trap
[R2]snmp-agent trap enable
[R2]snmp-agent target-host ?
trap Specify trap host information
[R2]snmp-agent target-host trap ?
address host IP address
[R2]snmp-agent target-host trap address ?
X.X.X.X IP address
[R2]snmp-agent target-host trap address 192.168.1.100 ?
parameters Specify SNMP parameters
port Specify host's UDP port
securityname Specify securityname string information
[R2]snmp-agent target-host trap address 192.168.1.100 securityname ?
STRING<1-32> SNMP securityname string
[R2]snmp-agent target-host trap address 192.168.1.100 securityname public
路由器R1的配置:
[Router]sysname R1
[R1]int e1
[R1-Ethernet1]ip add 192.168.3.1 24
[R1-Ethernet1]int s0
[R1-Serial0]ip address 192.168.2.2 24
[R1-Serial0]
%01:37:43: Line protocol ip on the interface Serial0 is UP
[R1-Serial0]shutdown
% Interface Serial0 is shut down
[R1-Serial0]
%01:37:48: Interface Serial0 is DOWN
[R1-Serial0]undo shutdown
% Interface Serial0 is reset
[R1-Serial0]
%01:38:01: Interface Serial0 is UP
%01:38:01: Line protocol ip on the interface Serial0 is UP
[R1-Serial0]quit
[R1]ip route-static 192.168.1.0 24 192.168.2.1
[R1]snmp-agent
[R1]snmp-agent sys-info contact guojiping
[R1]snmp-agent sys-info location shanghai
[R1]snmp-agent sys-info version all
[R1]snmp-agent community read public
[R1]snmp-agent community write private
[R1]snmp-agent trap enable
[R1]snmp-agent target-host ?
trap Specify trap host information
[R1]snmp-agent target-host trap address 192.168.1.100 securityname ?
STRING<1-32> SNMP securityname string
[R1]snmp-agent target-host trap address 192.168.1.100 securityname public
[R1]display ip routing
Routing Tables:
Destination/Mask Proto Pref Metric Nexthop Interface
127.0.0.0/8 Direct 0 0 127.0.0.1 LoopBack0
127.0.0.1/32 Direct 0 0 127.0.0.1 LoopBack0
192.168.1.0/24 Static 60 0 192.168.2.1 Serial0
192.168.2.0/24 Direct 0 0 192.168.2.1 Serial0
192.168.2.1/32 Direct 0 0 192.168.2.1 Serial0
192.168.2.2/32 Direct 0 0 127.0.0.1 LoopBack0
192.168.3.0/24 Direct 0 0 192.168.3.1 Ethernet1
192.168.3.1/32 Direct 0 0 127.0.0.1 LoopBack0
[R1]ping 192.168.3.100
PING 192.168.3.100: 56 data bytes, press CTRL_C to break
Reply from 192.168.3.100: bytes=56 Sequence=0 ttl=64 time = 1 ms
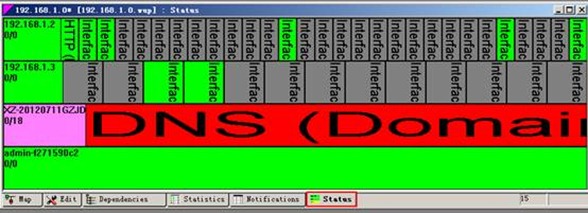
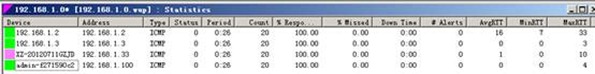
3.测试:
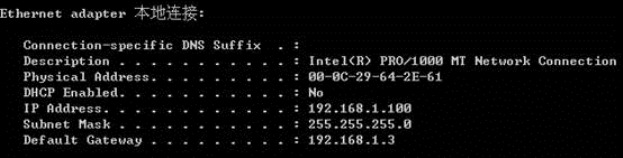
Windows server 2003 的配置:
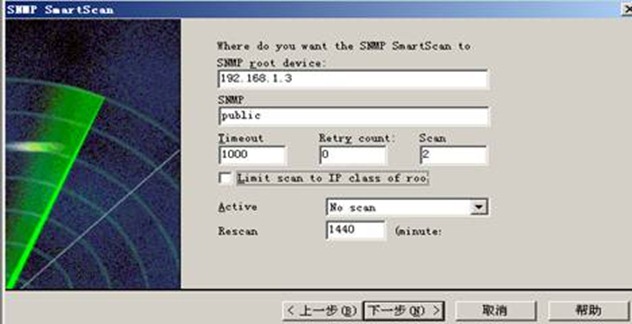
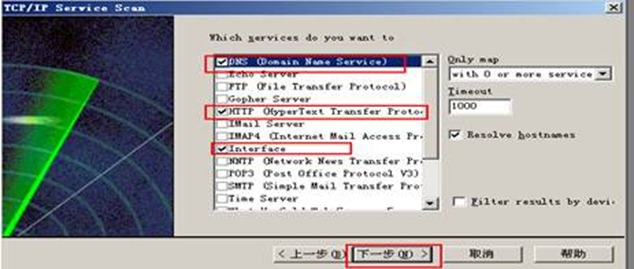
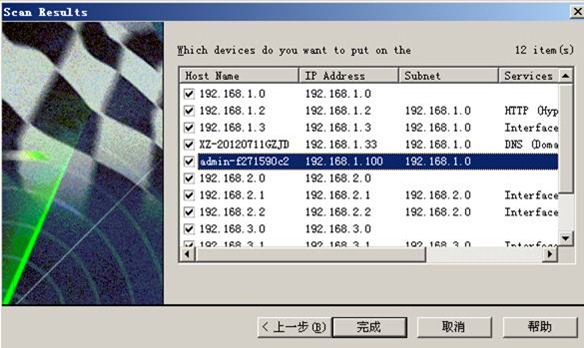
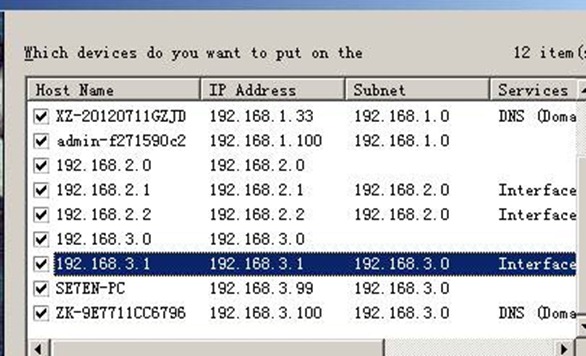
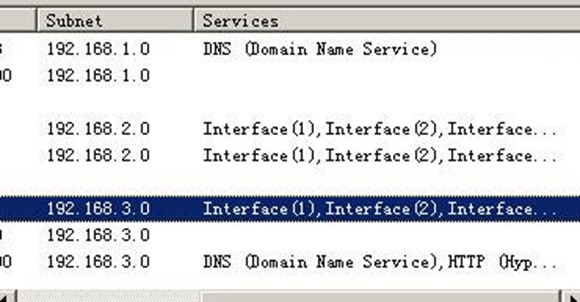
安装what‘s up软件 并设置:
整个网络拓扑图:
[R1]snmp-agent trap enable standard ?
authentication Send authentication trap
coldstart Send coldstart trap
linkdown Send linkdown trap
linkup Send linkup trap
warmstart Send warmstart trap
<cr>
[R1]snmp-agent trap enable standard linkup
[R1]snmp-agent trap enable standard linkdown