lvs DR配置
LVS负载均衡:三种负载均衡模式:DR,TUN(ip隧道),NAT,这里我们介绍DR模式
server1:
首先,配置server机yum源 方便后期实验流畅vim /etc/yum.repos.d/rhel-source.repo
[rhel-source]
name=Red Hat Enterprise Linux $releasever - $basearch - Source
baseurl=http://172.25.8.250/rhel6.5
enabled=1
gpgcheck=1
gpgkey=file:///etc/pki/rpm-gpg/RPM-GPG-KEY-redhat-release
[LoadBalancer]
name=LoadBalancer
baseurl=http://172.25.8.250/rhel6.5/LoadBalancer
gpgcheck=0
name=LoadBalancer
baseurl=http://172.25.8.250/rhel6.5/LoadBalancer
gpgcheck=0
[HighAvailability]
name=HighAvailability
baseurl=http://172.25.8.250/rhel6.5/HighAvailability
gpgcheck=0
name=HighAvailability
baseurl=http://172.25.8.250/rhel6.5/HighAvailability
gpgcheck=0
[ResilientStorage]
name=ResilientStorage
baseurl=http://172.25.8.250/rhel6.5/ResilientStorage
gpgcheck=0
name=ResilientStorage
baseurl=http://172.25.8.250/rhel6.5/ResilientStorage
gpgcheck=0
[ScalableFileSystem]
name=ScalableFileSystem
baseurl=http://172.25.8.250/rhel6.5/ScalableFileSystem
gpgcheck=0
name=ScalableFileSystem
baseurl=http://172.25.8.250/rhel6.5/ScalableFileSystem
gpgcheck=0
yum install ipvsadm -y
ipvsadm -A -t 172.25.8.100:80 -s rr ##添加策略 指定vip 172.25.8.100:80,-t指tcp,-s rr 指定轮询
ipvsadm -a -t 172.25.8.100:80 -r 172.25.8.2:80 -g ##将虚拟ip映射到真实的ip,-r指定realserver -t指定tcp协议 -g指dr模式
ipvsadm -a -t 172.25.8.100:80 -r 172.25.8.3:80 -g
ipvsadm -l #列出策略
[root@server1 html]# ipvsadm -l
IP Virtual Server version 1.2.1 (size=4096)
Prot LocalAddress:Port Scheduler Flags
-> RemoteAddress:Port Forward Weight ActiveConn InActConn
TCP 172.25.8.100:http rr
-> server2:http Route 1 0 0
-> server3:http Route 1 0 0
ipvsadm -A -t 172.25.8.100:80 -s rr ##添加策略 指定vip 172.25.8.100:80,-t指tcp,-s rr 指定轮询
ipvsadm -a -t 172.25.8.100:80 -r 172.25.8.2:80 -g ##将虚拟ip映射到真实的ip,-r指定realserver -t指定tcp协议 -g指dr模式
ipvsadm -a -t 172.25.8.100:80 -r 172.25.8.3:80 -g
ipvsadm -l #列出策略
[root@server1 html]# ipvsadm -l
IP Virtual Server version 1.2.1 (size=4096)
Prot LocalAddress:Port Scheduler Flags
-> RemoteAddress:Port Forward Weight ActiveConn InActConn
TCP 172.25.8.100:http rr
-> server2:http Route 1 0 0
-> server3:http Route 1 0 0
server2:
yum install httpdvim /var/www/html/index.html
/etc/init.d/httpd start
server3:yum install httpd
vim /var/www/html/index.html
/etc/init.d/httpd start
vim /var/www/html/index.html
/etc/init.d/httpd start
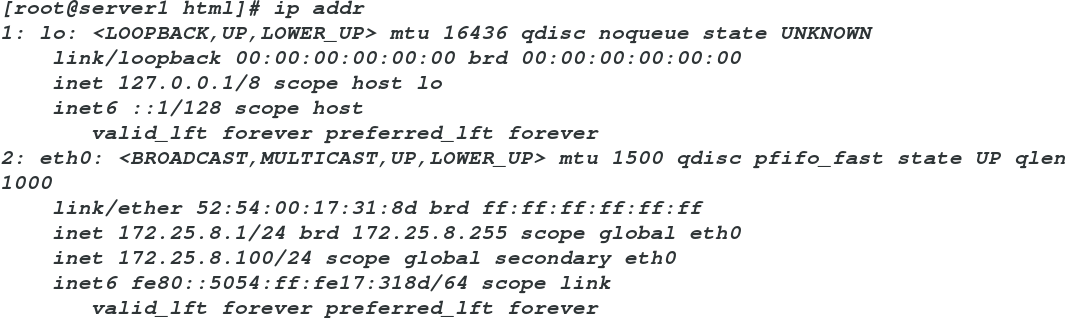
server1:
ip addr add 172.25.8.100/24 dev eth0 #添加一个虚拟ip
ip addr
ip addr add 172.25.8.100/24 dev eth0 #添加一个虚拟ip
ip addr
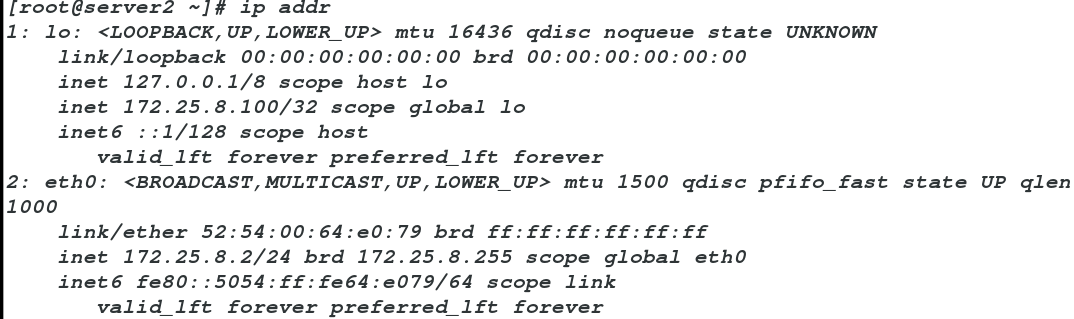
server2:
ip addr add 172.25.8.100/32 dev loip addr
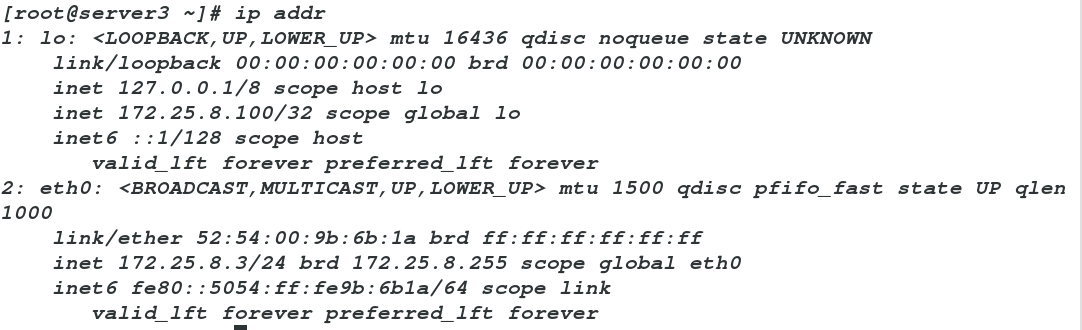
server3:
ip addr add 172.25.8.100/32 dev loip addr
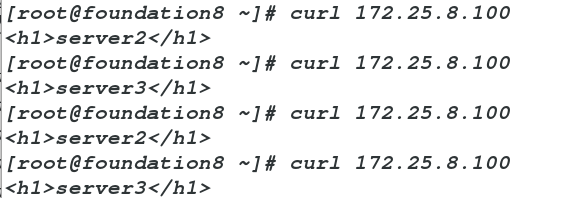
物理机测试:
curl 172.25.8.100[root@foundation8 ~]# curl 172.25.8.100
<h1>server3</h1>
[root@foundation8 ~]# curl 172.25.8.100
<h1>server2</h1>
[root@foundation8 ~]# curl 172.25.8.100
<h1>server3</h1>
[root@foundation8 ~]# curl 172.25.8.100
<h1>server2</h1>
<h1>server3</h1>
[root@foundation8 ~]# curl 172.25.8.100
<h1>server2</h1>
[root@foundation8 ~]# curl 172.25.8.100
<h1>server3</h1>
[root@foundation8 ~]# curl 172.25.8.100
<h1>server2</h1>
为防止客户端在访问vip时直接访问到realserver,需要在realserver设置一定的策略
server2:
yum install arptables_jfarptables -A IN -d 172.25.8.100 -j DROP ##访问realserver的100ip时的请求直接丢弃
arptables -A OUT -s 172.25.8.100 -j mangle --mangle-ip-s 172.25.8.2 ##realserver发出的信息全部转换为指定的真实ip
/etc/init.d/arptables_jf save ##保存策略
/etc/init.d/arptables_jf save ##保存策略
server3:
yum install arptables_jfarptables -A IN -d 172.25.8.100 -j DROP
arptables -A OUT -s 172.25.8.100 -j mangle --mangle-ip-s 172.25.8.3
/etc/init.d/arptables_jf save
测试:
在物理机中arp -d 172.25.8.100
curl 172.25.8.100
测试结果
[root@foundation8 ~]# curl 172.25.8.100
<h1>server3</h1>
[root@foundation8 ~]# curl 172.25.8.100
<h1>server2</h1>
[root@foundation8 ~]# curl 172.25.8.100
<h1>server3</h1>
[root@foundation8 ~]# curl 172.25.8.100
<h1>server2</h1>
但是此时无法实现健康检查,我们需要用ldirectord服务实现
Ldirector是一个监控集群服务节点运行状态的插件。Ldirector如果监控到集群节点中某个服务出现故障,就屏蔽此节点的对外连接功能,同时将后续请求转移到正常的节点提供服务,这个插件经常用在LVS负载均衡集群中
server1:
yum install ldirectord-3.9.5-3.1.x86_64.rpmcp /usr/share/doc/ldirectord-3.9.5/ldirectord.cf /etc/ha.d
cd /etc/ha.d/
vim ldirectord.cf
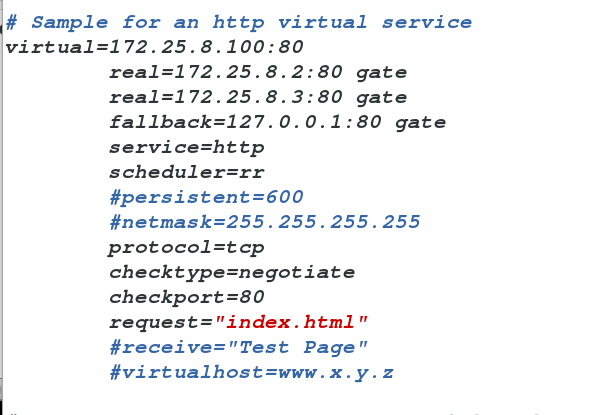
ipvsadm -C ##清空策略
/etc/init.d/ldirectord start
yum install httpd
vim /var/www/html/index.html
/etc/init.d/httpd start
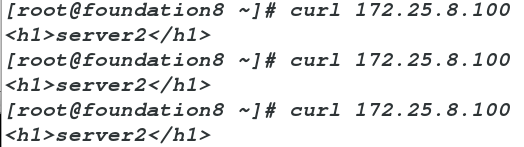
此时,当server3关闭httpd服务
测试结果如下
[root@foundation8 ~]# curl 172.25.8.100
<h1>server2</h1>
[root@foundation8 ~]# curl 172.25.8.100
<h1>server2</h1>
[root@foundation8 ~]# curl 172.25.8.100
<h1>server2</h1>
此时,当server2也关闭httpd服务
结果如下
[root@foundation8 ~]# curl 172.25.8.100
维护中。。
[root@foundation8 ~]# curl 172.25.8.100
维护中。。

keepalived:
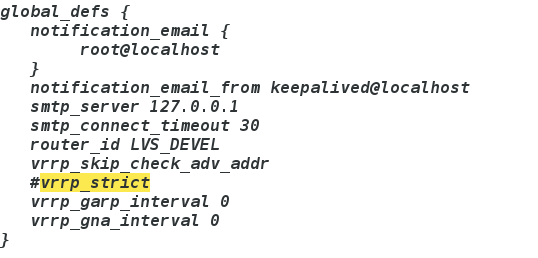
Keepalived的作用是检测服务器的状态,如果有一台web服务器宕机,或工作出现故障,Keepalived将检测到,并将有故障的服务器从系统中剔除,同时使用其他服务器代替该服务器的工作,当服务器工作正常后Keepalived自动将服务器加入到服务器群中,这些工作全部自动完成,不需要人工干涉,需要人工做的只是修复故障的服务器
主要用作RealServer的健康状态检查以及LoadBalance主机和BackUP主机之间failover的实现。
server1:
/etc/init.d/ldirectord stopchkconfig ldirectord off ##关闭ldirectord服务
下载keepalived-2.0.6.tar.gz
tar zxf keepalived-2.0.6.tar.gz ##解压
yum install rpm-build -y
yum install gcc -y
yum install openssl-devel -y
cd keepalived-2.0.6
[root@server1 keepalived-2.0.6]# ./configure --prefix=/usr/local/keepalived --with-init=SYSV ##编译
[root@server1 keepalived-2.0.6]# make
[root@server1 keepalived-2.0.6]# make install ##安装
cd /usr/local/keepalived/
[root@server1 keepalived]# ls ##软链接的制作
bin etc sbin share
cd sbin/
ln -s /usr/local/keepalived/sbin/keepalived /sbin/
cd etc/rc.d/init.d
chmod +x keepalived
ln -s /usr/local/keepalived/etc/rc.d/init.d/keepalived /etc/init.d/
cd etc/sysconfig
ln -s /usr/local/keepalived/etc/sysconfig/keepalived /etc/sysconfig/
cd etc/keeplived
ln -s /usr/local/keepalived/etc/keepalived/ /etc/
cd /usr/local/
scp -r keepalived/ server4:/usr/local/ ##将定制好的策略发送到server4中
scp -r keepalived/ server4:/usr/local/ ##将定制好的策略发送到server4中
yum install mailx -y
cd /etc/keeplived
vim keepalived.conf
cd /etc/keeplived
vim keepalived.conf
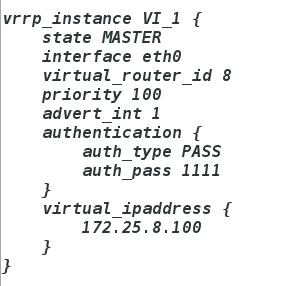
server4:
cd /usr/local/keeplivedls
[root@server4 keepalived]# ln -s /usr/local/keepalived/sbin/keepalived /sbin/
[root@server4 keepalived]# ln -s /usr/local/keepalived/etc/rc.d/init.d/keepalived /etc/init.d/
[root@server4 keepalived]# ln -s /usr/local/keepalived/etc/sysconfig/keepalived /etc/sysconfig/
mkdir /etc/keeplived
cd /etc/keepalived/
[root@server4 keepalived]# ln -s /usr/local/keepalived/etc/rc.d/init.d/keepalived /etc/init.d/
[root@server4 keepalived]# ln -s /usr/local/keepalived/etc/sysconfig/keepalived /etc/sysconfig/
mkdir /etc/keeplived
cd /etc/keepalived/
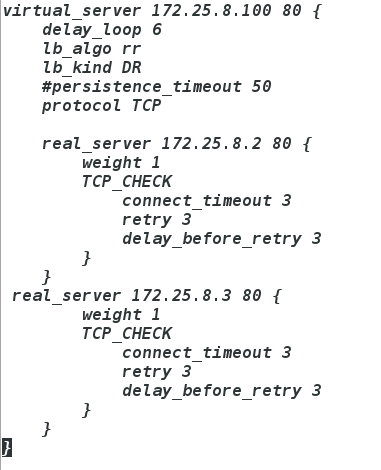
vim keepalived.conf

scp server1:/etc/yum.repos.d/rhel-source.repo /etc/yum.repos.d/rhel-source.repo
yum install ipvsadm -y
ipvsadm -l
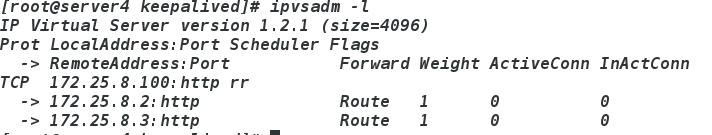
物理机测试
for i in range{1..6}; do curl 172.25.8.100; done;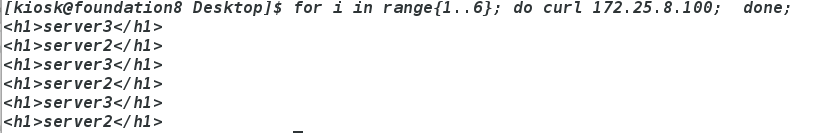

将server1中keepalived关闭
server4会自动获取ip,同时访问正常
server4会自动获取ip,同时访问正常
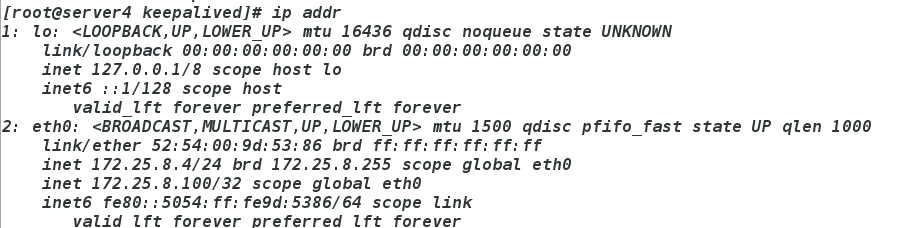
此时再将server1打开,ip又会回到server1中,因为server1的优先级比较高
server2:
yum install vsftpd -y/etc/init.d/vsftpd start
server3:
yum install vsftpd -y/etc/init.d/vsftpd start
cd /var/ftp
touch file
server1:
vim /etc/keepalived/keepalived.conf
在最下方添加
vim /etc/keepalived/keepalived.conf
在最下方添加
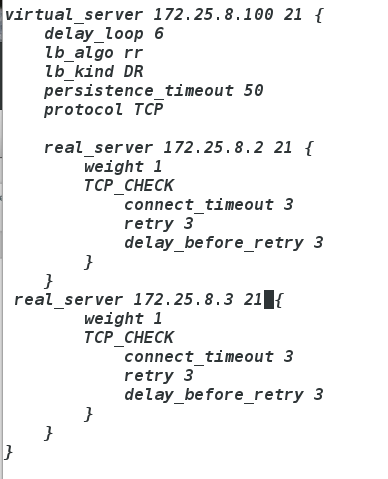
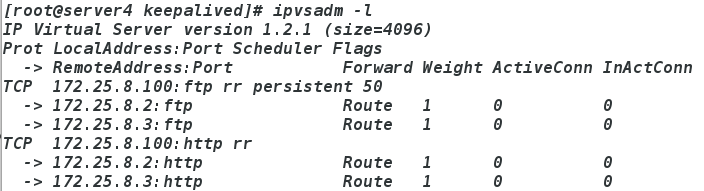
ipvsadm -l
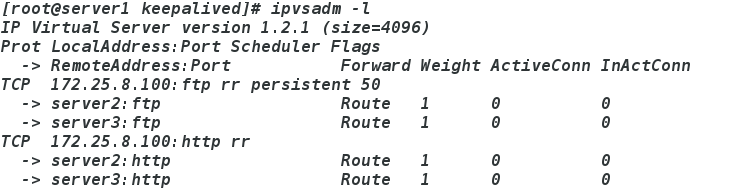
server4:
vim /etc/keepalived/keepalived.conf在最下方添加
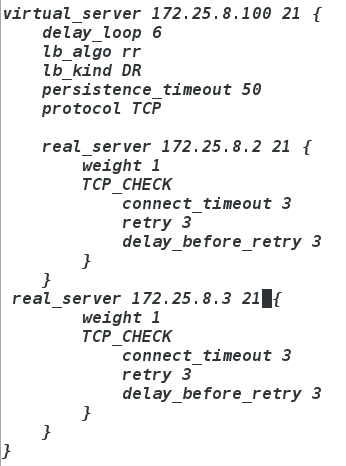
ipvsadm -l
测试
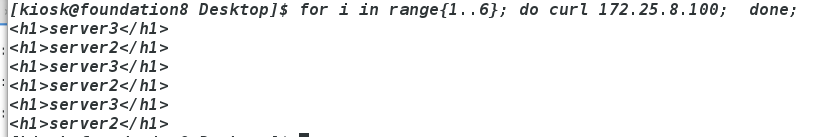
物理机for i in range{1..6}; do curl 172.25.8.100; done;
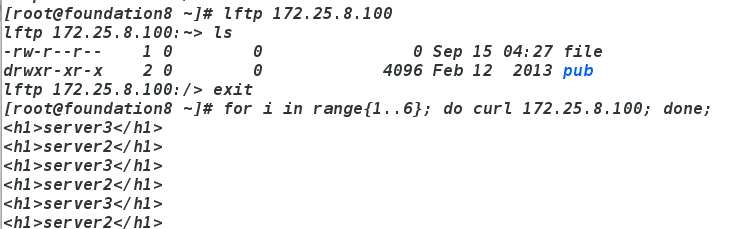
lftp 172.25.8.100
互备:
server1:
vim /etc/keepalived/keepalived.conf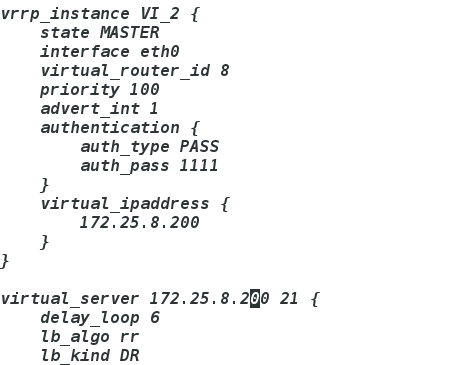
server4:
vim /etc/keepalived/keepalived.conf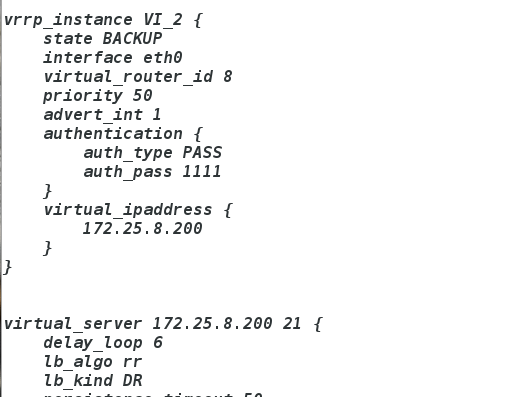
对server2,3需要添加新的策略
server2:
[root@server2 ftp]# ip addr add 172.25.8.200/32 dev lo
[root@server2 ftp]# arptables -A IN -d 172.25.8.200 -j DROP
[root@server2 ftp]# arptables -A OUT -s 172.25.8.200 -j mangle --mangle-ip-s 172.25.8.2
[root@server2 ftp]# /etc/init.d/arptables_jf save
[root@server2 ftp]# arptables -A OUT -s 172.25.8.200 -j mangle --mangle-ip-s 172.25.8.2
[root@server2 ftp]# /etc/init.d/arptables_jf save
server3:
[root@server3 ftp]# ip addr add 172.25.8.200/32 dev lo
[root@server3 ftp]# arptables -A IN -d 172.25.8.200 -j DROP[root@server3 ftp]# arptables -A OUT -s 172.25.8.200 -j mangle --mangle-ip-s 172.25.8.3
[root@server3 ftp]# /etc/init.d/arptables_jf save
测试
for i in range{1..6}; do curl 172.25.8.100; done;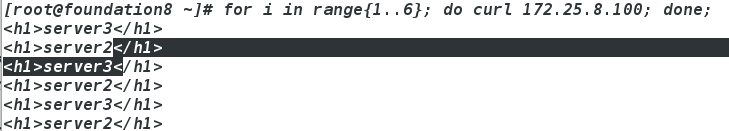
此时server1和server2互为主备
当server1或server4任意一个over时
另一台会自动获取ip并提供服务
当server1或server4任意一个over时
另一台会自动获取ip并提供服务