思维导图

已知CMS
如常见的dedecms,discuz,wordpress等源码结构,这种一般采用非框架类开发,但是也有少部分采用框架类开发,针对此类源码程序的安全检测,我们要利用公开的漏洞进行测试,如不存在可采用白盒代码审计自行挖掘。
搜索漏洞公布平台,寻找单点EXP:
- https://www.cnvd.org.cn/
- https://www.seebug.org/
- https://fr.0day.today/
- https://www.exploit-db.com/
- https://packetstormsecurity.com/
使用工具框架进行有针对性的扫描:
- CMSScan:综合类,一款适用于WordPress、Drupal、Joomla、vBulletin的安全扫描工具
- https://github.com/ajinabraham/CMSScan
- wpscan:WordPress扫描工具
- https://github.com/wpscanteam/wpscan
- kali系统,忍者系统自带
- 使用时需要在官方(https://wpscan.com)申请一个账号(谷歌人机身份验证,必须FQ),登录后得到一个token,使用wpscan时需要带着这个token。
- 用法:wpscan --url <URL> --api-token <YourToken>
- joomscan:Joomla扫描工具
- https://github.com/OWASP/joomscan
- DrupalScan:Drupal扫描工具
- https://github.com/rverton/DrupalScan
- 其他:先识别CMS,然后网上搜索针对该CMS的漏扫工具
代码审计:
- 函数点挖掘
- 功能点挖掘
- 框架类挖掘
开发框架
如常见的thinkphp,spring,flask等开发的源码程序,这种源码程序正常的安全测试思路:先获取对应的开发框架信息(名字,版本),通过公开的框架类安全问题进行测试,如不存在可采用白盒代码审计自行挖掘。
- 常见的PHP开发框架:Yii、Laravel、Thinkphp
- 常见的Java开发框架:Shiro、Struts、Spring、Maven
- 常见的Python开发框架:Flask、Django、Tornado
未知CMS
如常见的企业和个人内部程序源码,也可以是某CMS二次开发的源码结构,针对此类的程序源码测试思路:能识别二次开发就按已知CMS思路进行,不能确定二次开发的话可以采用常规综合类扫描工具或脚本进行探针,也可以采用人工探针(功能点,参数,盲猜),同样在有源码的情况下也可以进行代码审计自行挖掘。
案例1:开发框架类源码渗透测试-咨讯-thinkphp
1.fofa搜索"index/login/login",寻找测试网站。
2.构造错误的url,查看错误回显,确定网站使用thinkphp框架及其版本。
3.使用专门工具对thinkphp进行漏洞挖掘,比如
- TPScan(jar文件):一键ThinkPHP漏洞检测工具(参考:https://www.jeeinn.com/2021/03/1493/)
- https://github.com/tangxiaofeng7/TPScan
- TPScan(基于Python3):一键ThinkPHP漏洞检测工具:
- https://github.com/Lucifer1993/TPscan
- thinkPHP5.x远程命令执行(getshell)测试工具
- 地址:https://pan.baidu.com/s/17UOif8XD_-V_IMVAHXVlcw 提取码: 31x2
4.找到漏洞后,通过工具框架,漏洞公布平台,复现文章参考等进行漏洞利用。
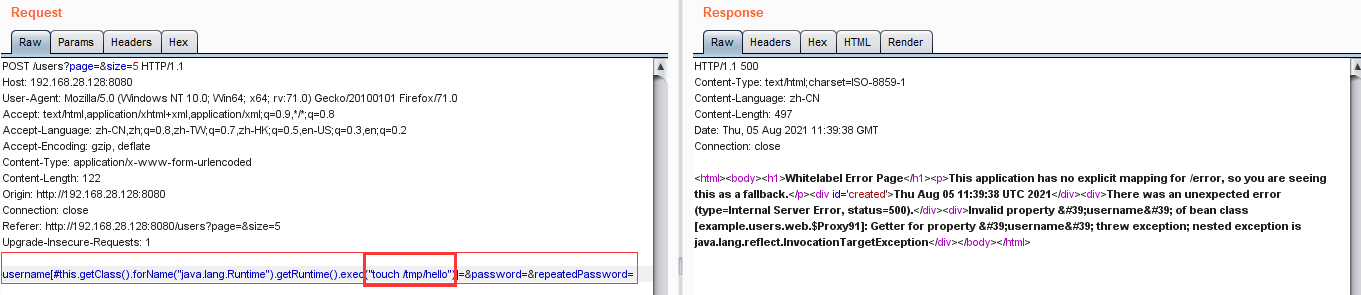
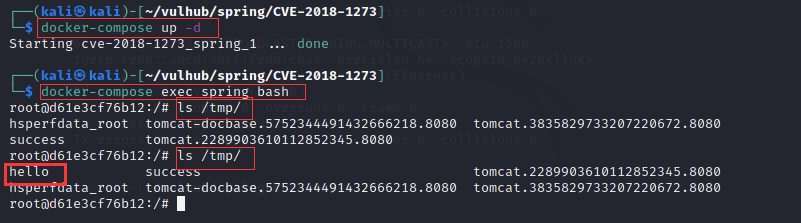
案例2:开发框架类源码渗透测试-咨讯-spring
1.使用Vulhub一键搭建漏洞测试靶场(https://vulhub.org/)
2.在Vulhub网站搜索某类漏洞,按照步骤,启动环境,漏洞复现。如图
案例3:已知CMS非框架类渗透测试-工具脚本-wordpress
1.环境准备:登录墨者学院,启动靶场环境:WordPress插件漏洞分析溯源。
2.CMS识别:进入首页,根据底部版权信息得知,该网站CMS使用的是WordPress。
3.使用wpscan工具扫描。
(1)wpscan官网注册并登录账号,得到token。
(2)kali下启动扫描:$ wpscan --url http://219.153.49.228:41640/ --api-token <mytoken>
扫描结果如下:

┌──(kali㉿kali)-[~] └─$ wpscan --url http://219.153.49.228:41640/ --api-token a9tjEZjFvgVoLnB5ROeC5As2VfozWT4MYKxmHg9bicw _______________________________________________________________ __ _______ _____ / / __ / ____| / / /| |__) | (___ ___ __ _ _ __ ® / / / | ___/ \___ / __|/ _` | '_ / / | | ____) | (__| (_| | | | | / / |_| |_____/ \___|\__,_|_| |_| WordPress Security Scanner by the WPScan Team Version 3.8.17 Sponsored by Automattic - https://automattic.com/ @_WPScan_, @ethicalhack3r, @erwan_lr, @firefart _______________________________________________________________ [+] URL: http://219.153.49.228:41640/ [219.153.49.228] [+] Started: Thu Aug 5 08:54:47 2021 Interesting Finding(s): [+] Headers | Interesting Entries: | - Server: Apache/2.4.7 (Ubuntu) | - X-Powered-By: PHP/5.5.9-1ubuntu4.14 | Found By: Headers (Passive Detection) | Confidence: 100% [+] XML-RPC seems to be enabled: http://219.153.49.228:41640/xmlrpc.php | Found By: Direct Access (Aggressive Detection) | Confidence: 100% | References: | - http://codex.wordpress.org/XML-RPC_Pingback_API | - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_ghost_scanner/ | - https://www.rapid7.com/db/modules/auxiliary/dos/http/wordpress_xmlrpc_dos/ | - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_xmlrpc_login/ | - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_pingback_access/ [+] Upload directory has listing enabled: http://219.153.49.228:41640/wp-content/uploads/ | Found By: Direct Access (Aggressive Detection) | Confidence: 100% [+] The external WP-Cron seems to be enabled: http://219.153.49.228:41640/wp-cron.php | Found By: Direct Access (Aggressive Detection) | Confidence: 60% | References: | - https://www.iplocation.net/defend-wordpress-from-ddos | - https://github.com/wpscanteam/wpscan/issues/1299 [+] WordPress version 3.5.2 identified (Insecure, released on 2013-06-21). | Found By: Rss Generator (Passive Detection) | - http://219.153.49.228:41640/?feed=rss2, <generator>http://wordpress.org/?v=3.5.2</generator> | - http://219.153.49.228:41640/?feed=comments-rss2, <generator>http://wordpress.org/?v=3.5.2</generator> | | [!] 41 vulnerabilities identified: | | [!] Title: WordPress 3.5.2 - Media Library Multiple Function Path Disclosure | References: | - https://wpscan.com/vulnerability/9994989b-2ec3-4e3d-884a-6227a88ba097 | - http://websecurity.com.ua/6795/ | | [!] Title: WordPress 3.5.2 - SWFUpload Content Spoofing | References: | - https://wpscan.com/vulnerability/956f952f-9362-4cea-9e08-dc7e5195dcc2 | - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-4144 | - https://github.com/wpscanteam/wpscan/issues/243 | - https://github.com/wordpress/secure-swfupload/issues/1 | - https://openwall.com/lists/oss-security/2013/07/18/11 | - https://github.com/wordpress/secure-swfupload/issues/1 | | [!] Title: WordPress 3.0 - 3.6 Crafted String URL Redirect Restriction Bypass | Fixed in: 3.6.1 | References: | - https://wpscan.com/vulnerability/16837700-a6dc-4825-8c7b-1486e0fb9c76 | - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-4339 | - https://www.exploit-db.com/exploits/28958/ | - https://packetstormsecurity.com/files/123589/ | - https://core.trac.wordpress.org/changeset/25323 | - http://www.gossamer-threads.com/lists/fulldisc/full-disclosure/91609 | | [!] Title: WordPress 3.5-3.7.1 - XML-RPC Denial of Service | Fixed in: 3.9.2 | References: | - https://wpscan.com/vulnerability/6214e783-978a-4ecb-95c0-2b7f12d7c348 | - https://wordpress.org/news/2014/08/wordpress-3-9-2/ | - http://mashable.com/2014/08/06/wordpress-xml-blowup-dos/ | - https://web.archive.org/web/20140825133704/http://www.breaksec.com/?p=6362 | | [!] Title: WordPress 2.0.3 - 3.9.1 (except 3.7.4 / 3.8.4) CSRF Token Brute Forcing | Fixed in: 3.9.2 | References: | - https://wpscan.com/vulnerability/90a3565c-852e-43de-a8ed-2679ab22cc9b | - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-5204 | - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-5205 | - https://core.trac.wordpress.org/changeset/29384 | - https://core.trac.wordpress.org/changeset/29408 | | [!] Title: WordPress 3.0 - 3.9.1 Authenticated Cross-Site Scripting (XSS) in Multisite | Fixed in: 3.9.2 | References: | - https://wpscan.com/vulnerability/4ea0b732-468c-4f3b-9b43-d7e897e1d665 | - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-5240 | - https://core.trac.wordpress.org/changeset/29398 | | [!] Title: WordPress 3.4.2 - 3.9.2 Does Not Invalidate Sessions Upon Logout | Fixed in: 4.0 | References: | - https://wpscan.com/vulnerability/8ee5c93f-6dd4-4001-b805-0d62a2475932 | - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2012-5868 | - http://whiteoaksecurity.com/blog/2012/12/17/cve-2012-5868-wordpress-342-sessions-not-terminated-upon-explicit-user-logout | - https://www.trustwave.com/en-us/resources/blogs/spiderlabs-blog/leveraging-lfi-to-get-full-compromise-on-wordpress-sites/ | | [!] Title: WordPress 3.0-3.9.2 - Unauthenticated Stored Cross-Site Scripting (XSS) | Fixed in: 4.0 | References: | - https://wpscan.com/vulnerability/a30dff57-91a5-433e-8282-90d0115ddcca | - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-9031 | - https://klikki.fi/adv/wordpress.html | - https://wordpress.org/news/2014/11/wordpress-4-0-1/ | - https://klikki.fi/adv/wordpress_update.html | | [!] Title: WordPress <= 4.0 - Long Password Denial of Service (DoS) | Fixed in: 4.0.1 | References: | - https://wpscan.com/vulnerability/aa6a0791-5d59-4c80-b943-bfec7fff7862 | - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-9034 | - https://www.exploit-db.com/exploits/35413/ | - https://www.exploit-db.com/exploits/35414/ | - http://www.behindthefirewalls.com/2014/11/wordpress-denial-of-service-responsible-disclosure.html | - https://wordpress.org/news/2014/11/wordpress-4-0-1/ | - https://www.rapid7.com/db/modules/auxiliary/dos/http/wordpress_long_password_dos/ | | [!] Title: WordPress <= 4.0 - Server Side Request Forgery (SSRF) | Fixed in: 4.0.1 | References: | - https://wpscan.com/vulnerability/894714e0-e582-4ae8-86d2-9826604bd823 | - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-9038 | - https://www.securityfocus.com/bid/71234/ | - https://core.trac.wordpress.org/changeset/30444 | | [!] Title: WordPress <= 4.2.2 - Authenticated Stored Cross-Site Scripting (XSS) | Fixed in: 4.2.3 | References: | - https://wpscan.com/vulnerability/0f027d7d-674b-4a63-9603-25ea68069c1d | - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-5622 | - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-5623 | - https://wordpress.org/news/2015/07/wordpress-4-2-3/ | - https://twitter.com/klikkioy/status/624264122570526720 | - https://klikki.fi/adv/wordpress3.html | | [!] Title: WordPress <= 4.4.2 - SSRF Bypass using Octal & Hexedecimal IP addresses | Fixed in: 4.5 | References: | - https://wpscan.com/vulnerability/0810e7fe-7212-49ae-8dd1-75260130b7f5 | - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4029 | - https://codex.wordpress.org/Version_4.5 | - https://github.com/WordPress/WordPress/commit/af9f0520875eda686fd13a427fd3914d7aded049 | | [!] Title: WordPress <= 4.4.2 - Reflected XSS in Network Settings | Fixed in: 4.5 | References: | - https://wpscan.com/vulnerability/238b69c9-4d56-4820-b09f-e778f108faf7 | - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6634 | - https://codex.wordpress.org/Version_4.5 | - https://github.com/WordPress/WordPress/commit/cb2b3ed3c7d68f6505bfb5c90257e6aaa3e5fcb9 | | [!] Title: WordPress <= 4.4.2 - Script Compression Option CSRF | Fixed in: 4.5 | References: | - https://wpscan.com/vulnerability/c0775703-ed52-4b6b-b395-7bf440ee0d77 | - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6635 | - https://codex.wordpress.org/Version_4.5 | | [!] Title: WordPress 2.6.0-4.5.2 - Unauthorized Category Removal from Post | Fixed in: 4.5.3 | References: | - https://wpscan.com/vulnerability/897d068a-d3c1-4193-bc55-f65225265967 | - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5837 | - https://wordpress.org/news/2016/06/wordpress-4-5-3/ | - https://github.com/WordPress/WordPress/commit/6d05c7521baa980c4efec411feca5e7fab6f307c | | [!] Title: WordPress 2.5-4.6 - Authenticated Stored Cross-Site Scripting via Image Filename | Fixed in: 4.6.1 | References: | - https://wpscan.com/vulnerability/e84eaf3f-677a-465a-8f96-ea4cf074c980 | - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-7168 | - https://wordpress.org/news/2016/09/wordpress-4-6-1-security-and-maintenance-release/ | - https://github.com/WordPress/WordPress/commit/c9e60dab176635d4bfaaf431c0ea891e4726d6e0 | - https://sumofpwn.nl/advisory/2016/persistent_cross_site_scripting_vulnerability_in_wordpress_due_to_unsafe_processing_of_file_names.html | - https://seclists.org/fulldisclosure/2016/Sep/6 | | [!] Title: WordPress 2.8-4.6 - Path Traversal in Upgrade Package Uploader | Fixed in: 4.6.1 | References: | - https://wpscan.com/vulnerability/7dcebd34-1a38-4f61-a116-bf8bf977b169 | - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-7169 | - https://wordpress.org/news/2016/09/wordpress-4-6-1-security-and-maintenance-release/ | - https://github.com/WordPress/WordPress/commit/54720a14d85bc1197ded7cb09bd3ea790caa0b6e | | [!] Title: WordPress 2.9-4.7 - Authenticated Cross-Site scripting (XSS) in update-core.php | Fixed in: 4.7.1 | References: | - https://wpscan.com/vulnerability/8b098363-1efb-4831-9b53-bb5d9770e8b4 | - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-5488 | - https://github.com/WordPress/WordPress/blob/c9ea1de1441bb3bda133bf72d513ca9de66566c2/wp-admin/update-core.php | - https://wordpress.org/news/2017/01/wordpress-4-7-1-security-and-maintenance-release/ | | [!] Title: WordPress 3.4-4.7 - Stored Cross-Site Scripting (XSS) via Theme Name fallback | Fixed in: 4.7.1 | References: | - https://wpscan.com/vulnerability/6737b4a2-080c-454a-a16e-7fc59824c659 | - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-5490 | - https://www.mehmetince.net/low-severity-wordpress/ | - https://wordpress.org/news/2017/01/wordpress-4-7-1-security-and-maintenance-release/ | - https://github.com/WordPress/WordPress/commit/ce7fb2934dd111e6353784852de8aea2a938b359 | | [!] Title: WordPress <= 4.7 - Post via Email Checks mail.example.com by Default | Fixed in: 4.7.1 | References: | - https://wpscan.com/vulnerability/0a666ddd-a13d-48c2-85c2-bfdc9cd2a5fb | - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-5491 | - https://github.com/WordPress/WordPress/commit/061e8788814ac87706d8b95688df276fe3c8596a | - https://wordpress.org/news/2017/01/wordpress-4-7-1-security-and-maintenance-release/ | | [!] Title: WordPress 2.8-4.7 - Accessibility Mode Cross-Site Request Forgery (CSRF) | Fixed in: 4.7.1 | References: | - https://wpscan.com/vulnerability/e080c934-6a98-4726-8e7a-43a718d05e79 | - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-5492 | - https://github.com/WordPress/WordPress/commit/03e5c0314aeffe6b27f4b98fef842bf0fb00c733 | - https://wordpress.org/news/2017/01/wordpress-4-7-1-security-and-maintenance-release/ | | [!] Title: WordPress 3.0-4.7 - Cryptographically Weak Pseudo-Random Number Generator (PRNG) | Fixed in: 4.7.1 | References: | - https://wpscan.com/vulnerability/3e355742-6069-4d5d-9676-613df46e8c54 | - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-5493 | - https://github.com/WordPress/WordPress/commit/cea9e2dc62abf777e06b12ec4ad9d1aaa49b29f4 | - https://wordpress.org/news/2017/01/wordpress-4-7-1-security-and-maintenance-release/ | | [!] Title: WordPress 3.5-4.7.1 - WP_Query SQL Injection | Fixed in: 4.7.2 | References: | - https://wpscan.com/vulnerability/481e3398-ed2e-460a-af67-ff58027901d1 | - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-5611 | - https://wordpress.org/news/2017/01/wordpress-4-7-2-security-release/ | - https://github.com/WordPress/WordPress/commit/85384297a60900004e27e417eac56d24267054cb | | [!] Title: WordPress 2.8.1-4.7.2 - Control Characters in Redirect URL Validation | Fixed in: 4.7.3 | References: | - https://wpscan.com/vulnerability/d40374cf-ee95-40b7-9dd5-dbb160b877b1 | - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-6815 | - https://wordpress.org/news/2017/03/wordpress-4-7-3-security-and-maintenance-release/ | - https://github.com/WordPress/WordPress/commit/288cd469396cfe7055972b457eb589cea51ce40e | | [!] Title: WordPress 2.3-4.8.3 - Host Header Injection in Password Reset | References: | - https://wpscan.com/vulnerability/b3f2f3db-75e4-4d48-ae5e-d4ff172bc093 | - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-8295 | - https://exploitbox.io/vuln/WordPress-Exploit-4-7-Unauth-Password-Reset-0day-CVE-2017-8295.html | - https://blog.dewhurstsecurity.com/2017/05/04/exploitbox-wordpress-security-advisories.html | - https://core.trac.wordpress.org/ticket/25239 | | [!] Title: WordPress 2.7.0-4.7.4 - Insufficient Redirect Validation | Fixed in: 4.7.5 | References: | - https://wpscan.com/vulnerability/e9e59e08-0586-4332-a394-efb648c7cd84 | - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-9066 | - https://github.com/WordPress/WordPress/commit/76d77e927bb4d0f87c7262a50e28d84e01fd2b11 | - https://wordpress.org/news/2017/05/wordpress-4-7-5/ | | [!] Title: WordPress 2.5.0-4.7.4 - Post Meta Data Values Improper Handling in XML-RPC | Fixed in: 4.7.5 | References: | - https://wpscan.com/vulnerability/973c55ed-e120-46a1-8dbb-538b54d03892 | - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-9062 | - https://wordpress.org/news/2017/05/wordpress-4-7-5/ | - https://github.com/WordPress/WordPress/commit/3d95e3ae816f4d7c638f40d3e936a4be19724381 | | [!] Title: WordPress 3.4.0-4.7.4 - XML-RPC Post Meta Data Lack of Capability Checks | Fixed in: 4.7.5 | References: | - https://wpscan.com/vulnerability/a5a4f4ca-19e5-4665-b501-5c75e0f56001 | - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-9065 | - https://wordpress.org/news/2017/05/wordpress-4-7-5/ | - https://github.com/WordPress/WordPress/commit/e88a48a066ab2200ce3091b131d43e2fab2460a4 | | [!] Title: WordPress 2.5.0-4.7.4 - Filesystem Credentials Dialog CSRF | Fixed in: 4.7.5 | References: | - https://wpscan.com/vulnerability/efe46d58-45e4-4cd6-94b3-1a639865ba5b | - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-9064 | - https://wordpress.org/news/2017/05/wordpress-4-7-5/ | - https://github.com/WordPress/WordPress/commit/38347d7c580be4cdd8476e4bbc653d5c79ed9b67 | - https://sumofpwn.nl/advisory/2016/cross_site_request_forgery_in_wordpress_connection_information.html | | [!] Title: WordPress 3.3-4.7.4 - Large File Upload Error XSS | Fixed in: 4.7.5 | References: | - https://wpscan.com/vulnerability/78ae4791-2703-4fdd-89b2-76c674994acf | - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-9061 | - https://wordpress.org/news/2017/05/wordpress-4-7-5/ | - https://github.com/WordPress/WordPress/commit/8c7ea71edbbffca5d9766b7bea7c7f3722ffafa6 | - https://hackerone.com/reports/203515 | - https://hackerone.com/reports/203515 | | [!] Title: WordPress 3.4.0-4.7.4 - Customizer XSS & CSRF | Fixed in: 4.7.5 | References: | - https://wpscan.com/vulnerability/e9535a5c-c6dc-4742-be40-1b94a718d3f3 | - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-9063 | - https://wordpress.org/news/2017/05/wordpress-4-7-5/ | - https://github.com/WordPress/WordPress/commit/3d10fef22d788f29aed745b0f5ff6f6baea69af3 | | [!] Title: WordPress 2.3.0-4.8.1 - $wpdb->prepare() potential SQL Injection | Fixed in: 4.8.2 | References: | - https://wpscan.com/vulnerability/9b3414c0-b33b-4c55-adff-718ff4c3195d | - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-14723 | - https://wordpress.org/news/2017/09/wordpress-4-8-2-security-and-maintenance-release/ | - https://github.com/WordPress/WordPress/commit/70b21279098fc973eae803693c0705a548128e48 | - https://github.com/WordPress/WordPress/commit/fc930d3daed1c3acef010d04acc2c5de93cd18ec | | [!] Title: WordPress 2.3.0-4.7.4 - Authenticated SQL injection | Fixed in: 4.7.5 | References: | - https://wpscan.com/vulnerability/95e87ae5-eb01-4e27-96d3-b1f013deff1c | - https://medium.com/websec/wordpress-sqli-bbb2afcc8e94 | - https://wordpress.org/news/2017/09/wordpress-4-8-2-security-and-maintenance-release/ | - https://github.com/WordPress/WordPress/commit/70b21279098fc973eae803693c0705a548128e48 | - https://wpvulndb.com/vulnerabilities/8905 | | [!] Title: WordPress 2.9.2-4.8.1 - Open Redirect | Fixed in: 4.8.2 | References: | - https://wpscan.com/vulnerability/571beae9-d92d-4f9b-aa9f-7c94e33683a1 | - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-14725 | - https://wordpress.org/news/2017/09/wordpress-4-8-2-security-and-maintenance-release/ | - https://core.trac.wordpress.org/changeset/41398 | | [!] Title: WordPress 3.0-4.8.1 - Path Traversal in Unzipping | Fixed in: 4.8.2 | References: | - https://wpscan.com/vulnerability/d74ee25a-d845-46b5-afa6-b0a917b7737a | - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-14719 | - https://wordpress.org/news/2017/09/wordpress-4-8-2-security-and-maintenance-release/ | - https://core.trac.wordpress.org/changeset/41457 | - https://hackerone.com/reports/205481 | | [!] Title: WordPress <= 4.8.2 - $wpdb->prepare() Weakness | Fixed in: 4.8.3 | References: | - https://wpscan.com/vulnerability/c161f0f0-6527-4ba4-a43d-36c644e250fc | - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-16510 | - https://wordpress.org/news/2017/10/wordpress-4-8-3-security-release/ | - https://github.com/WordPress/WordPress/commit/a2693fd8602e3263b5925b9d799ddd577202167d | - https://twitter.com/ircmaxell/status/923662170092638208 | - https://blog.ircmaxell.com/2017/10/disclosure-wordpress-wpdb-sql-injection-technical.html | | [!] Title: WordPress 2.8.6-4.9 - Authenticated JavaScript File Upload | Fixed in: 4.9.1 | References: | - https://wpscan.com/vulnerability/0d2323bd-aecd-4d58-ba4b-597a43034f57 | - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-17092 | - https://wordpress.org/news/2017/11/wordpress-4-9-1-security-and-maintenance-release/ | - https://github.com/WordPress/WordPress/commit/67d03a98c2cae5f41843c897f206adde299b0509 | | [!] Title: WordPress 1.5.0-4.9 - RSS and Atom Feed Escaping | Fixed in: 4.9.1 | References: | - https://wpscan.com/vulnerability/1f71a775-e87e-47e9-9642-bf4bce99c332 | - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-17094 | - https://wordpress.org/news/2017/11/wordpress-4-9-1-security-and-maintenance-release/ | - https://github.com/WordPress/WordPress/commit/f1de7e42df29395c3314bf85bff3d1f4f90541de | | [!] Title: WordPress <= 4.9.4 - Application Denial of Service (DoS) (unpatched) | References: | - https://wpscan.com/vulnerability/5e0c1ddd-fdd0-421b-bdbe-3eee6b75c919 | - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-6389 | - https://baraktawily.blogspot.fr/2018/02/how-to-dos-29-of-world-wide-websites.html | - https://github.com/quitten/doser.py | - https://thehackernews.com/2018/02/wordpress-dos-exploit.html | | [!] Title: WordPress <= 4.9.6 - Authenticated Arbitrary File Deletion | References: | - https://wpscan.com/vulnerability/42ab2bd9-bbb1-4f25-a632-1811c5130bb4 | - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-12895 | - https://blog.ripstech.com/2018/wordpress-file-delete-to-code-execution/ | - http://blog.vulnspy.com/2018/06/27/Wordpress-4-9-6-Arbitrary-File-Delection-Vulnerbility-Exploit/ | - https://github.com/WordPress/WordPress/commit/c9dce0606b0d7e6f494d4abe7b193ac046a322cd | - https://wordpress.org/news/2018/07/wordpress-4-9-7-security-and-maintenance-release/ | - https://www.wordfence.com/blog/2018/07/details-of-an-additional-file-deletion-vulnerability-patched-in-wordpress-4-9-7/ | | [!] Title: WordPress <= 5.2.2 - Cross-Site Scripting (XSS) in URL Sanitisation | Fixed in: 5.2.3 | References: | - https://wpscan.com/vulnerability/4494a903-5a73-4cad-8c14-1e7b4da2be61 | - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-16222 | - https://wordpress.org/news/2019/09/wordpress-5-2-3-security-and-maintenance-release/ | - https://github.com/WordPress/WordPress/commit/30ac67579559fe42251b5a9f887211bf61a8ed68 | - https://hackerone.com/reports/339483 [+] WordPress theme in use: twentytwelve | Location: http://219.153.49.228:41640/wp-content/themes/twentytwelve/ | Last Updated: 2021-07-26T00:00:00.000Z | [!] The version is out of date, the latest version is 3.5 | Style URL: http://219.153.49.228:41640/wp-content/themes/twentytwelve/style.css?ver=3.5.2 | Style Name: Twenty Twelve | Style URI: http://wordpress.org/extend/themes/twentytwelve | Description: The 2012 theme for WordPress is a fully responsive theme that looks great on any device. Features in... | Author: the WordPress team | Author URI: http://wordpress.org/ | | Found By: Css Style In Homepage (Passive Detection) | | Version: 1.1 (80% confidence) | Found By: Style (Passive Detection) | - http://219.153.49.228:41640/wp-content/themes/twentytwelve/style.css?ver=3.5.2, Match: 'Version: 1.1' [+] Enumerating All Plugins (via Passive Methods) [+] Checking Plugin Versions (via Passive and Aggressive Methods) [i] Plugin(s) Identified: [+] comment-rating | Location: http://219.153.49.228:41640/wp-content/plugins/comment-rating/ | | Found By: Urls In Homepage (Passive Detection) | | [!] 1 vulnerability identified: | | [!] Title: Comment Rating 2.9.32 - Security Bypass Weakness & SQL Injection | References: | - https://wpscan.com/vulnerability/076efd7b-09f6-4893-9733-57930794b43e | - https://www.exploit-db.com/exploits/24552/ | - https://packetstormsecurity.com/files/120569/ | | Version: 2.9.32 (100% confidence) | Found By: Readme - Stable Tag (Aggressive Detection) | - http://219.153.49.228:41640/wp-content/plugins/comment-rating/readme.txt | Confirmed By: Readme - ChangeLog Section (Aggressive Detection) | - http://219.153.49.228:41640/wp-content/plugins/comment-rating/readme.txt [+] Enumerating Config Backups (via Passive and Aggressive Methods) Checking Config Backups - Time: 00:00:07 <===========================> (137 / 137) 100.00% Time: 00:00:07 [i] No Config Backups Found. [+] WPScan DB API OK | Plan: free | Requests Done (during the scan): 3 | Requests Remaining: 22 [+] Finished: Thu Aug 5 08:55:24 2021 [+] Requests Done: 183 [+] Cached Requests: 5 [+] Data Sent: 48.761 KB [+] Data Received: 166.807 KB [+] Memory used: 212.305 MB [+] Elapsed time: 00:00:36 ┌──(kali㉿kali)-[~] └─$
发现一个插件漏洞
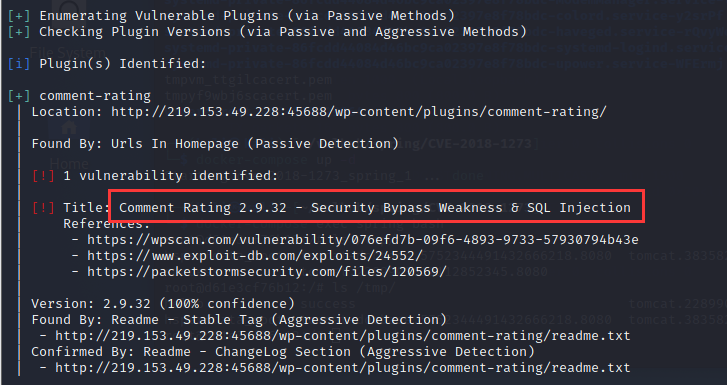
4.去网上找到相关文章、poc等,进行漏洞利用。
