ldap首先我们要知道这个ldap的概念,
LDAP是轻量目录访问协议(Lightweight Directory Access Protocol)的缩写
目录是一个为查询、浏览和搜索而优化的专业分布式数据库,它呈树状结构组织数据,就好象Linux/Unix系统中的文件目录一样。目录数据库和关系数据库不同,它有优异的读性能,但写性能差,并且没有事务处理、回滚等复杂功能,不适于存储修改频繁的数据。所以目录天生是用来查询的,就好象它的名字一样。
目录服务是由目录数据库和一套访问协议组成的系统。类似以下的信息适合储存在目录中:
- 企业员工信息,如姓名、电话、邮箱等;
- 公用证书和安全密钥;
- 公司的物理设备信息,如服务器,它的IP地址、存放位置、厂商、购买时间等;
2. LDAP特点
- LDAP的结构用树来表示,而不是用表格。正因为这样,就不能用SQL语句了
- LDAP可以很快地得到查询结果,不过在写方面,就慢得多
- LDAP提供了静态数据的快速查询方式
- Client/server模型,Server 用于存储数据,Client提供操作目录信息树的工具
- 这些工具可以将数据库的内容以文本格式(LDAP 数据交换格式,LDIF)呈现在您的面前
- LDAP是一种开放Internet标准,LDAP协议是跨平台的Interent协议
ldap的搭建也是分为单模式配置,或者主从模式的配置,也有主主模式的配置
下面搭建单模式
参考:https://cloud.tencent.com/developer/article/1155424
首先要关闭服务器防火墙
systemctl stop firewalld.service
systemctl disable firewalld.service
firewall-cmd --state
OpenLDAP安装
下载ldap:
yum install -y openldap yum install -y openldap openldap-*
启动:
systemctl start slapd systemctl enable slapd
然后选择一个你要存储的配置文件的目录 ,我的习惯是再/opt下
vim installOpenldap.sh 写入: #!/bin/bash echo "install ldap rpm"
执行:
chmod 755 installOpenldap.sh
sh -x installOpenldap.sh
查看安装的ldpa服务:
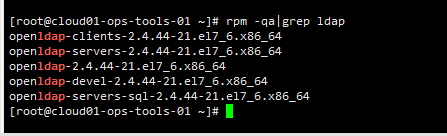
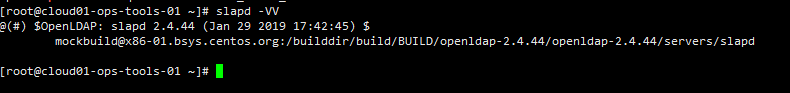
查看OpenLDAP版本;
查看ldap启动状态
systemctl status slapd
[root@cloud01-ops-tools-01 ~]# systemctl status slapd ● slapd.service - OpenLDAP Server Daemon Loaded: loaded (/usr/lib/systemd/system/slapd.service; disabled; vendor preset: disabled) Active: active (running) since Mon 2019-03-18 00:15:46 CST; 9h ago Docs: man:slapd man:slapd-config man:slapd-hdb man:slapd-mdb file:///usr/share/doc/openldap-servers/guide.html Process: 24933 ExecStart=/usr/sbin/slapd -u ldap -h ${SLAPD_URLS} $SLAPD_OPTIONS (code=exited, status=0/SUCCESS) Process: 24899 ExecStartPre=/usr/libexec/openldap/check-config.sh (code=exited, status=0/SUCCESS) Main PID: 24935 (slapd) Memory: 9.8M CGroup: /system.slice/slapd.service └─24935 /usr/sbin/slapd -u ldap -h ldapi:/// ldap:/// Mar 18 00:26:27 cloud01-ops-tools-01 slapd[24935]: conn=1001 op=6 SRCH base="c=cn" scope=1 deref=0 filter="(objectClass=*)" Mar 18 00:26:27 cloud01-ops-tools-01 slapd[24935]: conn=1001 op=6 SRCH attr=objectclass Mar 18 00:26:27 cloud01-ops-tools-01 slapd[24935]: conn=1001 op=6 SEARCH RESULT tag=101 err=0 nentries=2 text= Mar 18 00:26:29 cloud01-ops-tools-01 slapd[24935]: conn=1001 op=7 SRCH base="ou=People,c=cn" scope=1 deref=0 filter="(objectClass=*)" Mar 18 00:26:29 cloud01-ops-tools-01 slapd[24935]: conn=1001 op=7 SRCH attr=objectclass Mar 18 00:26:29 cloud01-ops-tools-01 slapd[24935]: conn=1001 op=7 SEARCH RESULT tag=101 err=0 nentries=0 text= Mar 18 00:26:56 cloud01-ops-tools-01 slapd[24935]: conn=1001 op=8 SRCH base="cn=Manager,c=cn" scope=1 deref=0 filter="(objectClass=*)" Mar 18 00:26:56 cloud01-ops-tools-01 slapd[24935]: conn=1001 op=8 SRCH attr=objectclass Mar 18 00:26:56 cloud01-ops-tools-01 slapd[24935]: conn=1001 op=8 SEARCH RESULT tag=101 err=0 nentries=0 text= Mar 18 02:38:14 cloud01-ops-tools-01 slapd[24935]: conn=1001 fd=11 closed (connection lost)
查看openldap默认监听的389端口(centos7最小化安装默认没有netstat命令,需安装)
[root@openldap-master ~]# yum install net-tools -y [root@openldap-master ~]# netstat -antup| grep 389 tcp 0 0 0.0.0.0:389 0.0.0.0:* LISTEN 26195/slapd tcp6 0 0 :::389 :::* LISTEN 26195/slapd
温馨提示: 本案例测试时,已关闭了iptables防火墙。如果开启了iptables,则需要开放389端口
[root@openldap-master ~]# firewall-cmd --zone=public --add-port=389/tcp --permanent [root@openldap-master ~]# firewall-cmd --reload ======================================
配置OpenLDAP数据库
cp /usr/share/openldap-servers/DB_CONFIG.example /var/lib/ldap/DB_CONFIG
[root@cloud01-ops-tools-01 openldap-servers]# cp /usr/share/openldap-servers/DB_CONFIG.example /var/lib/ldap/DB_CONFIG [root@cloud01-ops-tools-01 openldap-servers]# chown ldap:ldap -R /var/lib/ldap/ [root@cloud01-ops-tools-01 openldap-servers]# chmod 700 -R /var/lib/ldap [root@cloud01-ops-tools-01 openldap-servers]# ll /var/lib/ldap/ total 348 -rwx------ 1 ldap ldap 2048 Mar 17 23:25 alock -rwx------ 1 ldap ldap 286720 Mar 17 23:25 __db.001 -rwx------ 1 ldap ldap 32768 Mar 17 23:25 __db.002 -rwx------ 1 ldap ldap 49152 Mar 17 23:25 __db.003 -rwx------ 1 ldap ldap 845 Mar 17 23:28 DB_CONFIG -rwx------ 1 ldap ldap 8192 Mar 17 23:25 dn2id.bdb -rwx------ 1 ldap ldap 32768 Mar 17 23:25 id2entry.bdb -rwx------ 1 ldap ldap 10485760 Mar 17 23:25 log.0000000001
配置ldap服务 设置OpenLDAP的管理员密码(这里密码为:123456)
[root@cloud01-ops-tools-01 openldap-servers]# slappasswd New password: Re-enter new password: {SSHA}ago8nKNyfjhYa/btKgHDIpyEPxSBZrMm
然后进入你要保存配置文件的目录,我的目录是/opt
编辑chrootpw.ldif文件
vim chrootpw.ldif [root@openldap-master ~]# cd /opt/ [root@openldap-master opt]# vim chrootpw.ldif # specify the password generated above for "olcRootPW" section dn: olcDatabase={0}config,cn=config changetype: modify add: olcRootPW olcRootPW: {SSHA}ago8nKNyfjhYa/btKgHDIpyEPxSBZrMm # 这里是存放你的上面生成的密码
导入chrootpw.ldif
ldapadd -Y EXTERNAL -H ldapi:/// -f chrootpw.ldif [root@cloud01-ops-tools-01 opt]# ldapadd -Y EXTERNAL -H ldapi:/// -f chrootpw.ldif SASL/EXTERNAL authentication started SASL username: gidNumber=0+uidNumber=0,cn=peercred,cn=external,cn=auth SASL SSF: 0 modifying entry "olcDatabase={0}config,cn=config"
============================================================= 温馨提示: 如果上面的命令出现下面报错:
[root@openldap-master opt]# ldapadd -Y EXTERNAL -H ldapi:/// -f chrootpw.ldif SASL/EXTERNAL authentication started SASL username: gidNumber=0+uidNumber=0,cn=peercred,cn=external,cn=auth SASL SSF: 0 modifying entry "olcDatabase={0}config,cn=config" ldap_modify: Inappropriate matching (18) additional info: modify/add: olcRootPW: no equality matching rule
解决办法: 修改modify.ldif中对应选项的"add"为"replace"即可
即:
root@openldap-master opt]# cat chrootpw.ldif # specify the password generated above for "olcRootPW" section dn: olcDatabase={0}config,cn=config changetype: modify replace: olcRootPW olcRootPW: {SSHA}ago8nKNyfjhYa/btKgHDIpyEPxSBZrMm
然后再次执行:
[root@openldap-master opt]# ldapadd -Y EXTERNAL -H ldapi:/// -f chrootpw.ldif SASL/EXTERNAL authentication started SASL username: gidNumber=0+uidNumber=0,cn=peercred,cn=external,cn=auth SASL SSF: 0 modifying entry "olcDatabase={0}config,cn=config"
导入基本模式:
vim ldapaddBaseSchema.sh
[root@openldap-master opt]# vim ldapaddBaseSchema.sh #!/bin/bash ldapadd -Y EXTERNAL -H ldapi:/// -f /etc/openldap/schema/cosine.ldif ldapadd -Y EXTERNAL -H ldapi:/// -f /etc/openldap/schema/nis.ldif ldapadd -Y EXTERNAL -H ldapi:/// -f /etc/openldap/schema/inetorgperson.ldif
执行上面脚本:
[root@openldap-master opt]# chmod 755 ldapaddBaseSchema.sh [root@openldap-master opt]# sh -x ldapaddBaseSchema.sh + ldapadd -Y EXTERNAL -H ldapi:/// -f /etc/openldap/schema/cosine.ldif SASL/EXTERNAL authentication started SASL username: gidNumber=0+uidNumber=0,cn=peercred,cn=external,cn=auth SASL SSF: 0 adding new entry "cn=cosine,cn=schema,cn=config" + ldapadd -Y EXTERNAL -H ldapi:/// -f /etc/openldap/schema/nis.ldif SASL/EXTERNAL authentication started SASL username: gidNumber=0+uidNumber=0,cn=peercred,cn=external,cn=auth SASL SSF: 0 adding new entry "cn=nis,cn=schema,cn=config" + ldapadd -Y EXTERNAL -H ldapi:/// -f /etc/openldap/schema/inetorgperson.ldif SASL/EXTERNAL authentication started SASL username: gidNumber=0+uidNumber=0,cn=peercred,cn=external,cn=auth SASL SSF: 0 adding new entry "cn=inetorgperson,cn=schema,cn=config"
======================================================== 温馨提示: 如果上面的命令出现下面报错:
...... ldap_add: Other (e.g., implementation specific) error (80) additional info: olcAttributeTypes: Duplicate attributeType: "2.16.840.1.113730.3.1.1"
原因是: LDIF已经加载,所以尝试再次加载它们就报错这些信息,忽略这个步骤即可。 =======================================================
接着在ldap服务的DB中设置域名,即编辑chdomain.ldif文件
# replace to your own domain name for "dc=***,dc=***" section # specify the password generated above for "olcRootPW" section dn: olcDatabase={1}monitor,cn=config changetype: modify replace: olcAccess olcAccess: {0}to * by dn.base="gidNumber=0+uidNumber=0,cn=peercred,cn=external,cn=auth" read by dn.base="cn=Manager,c=cn" read by * none dn: olcDatabase={2}hdb,cn=config changetype: modify replace: olcSuffix olcSuffix: c=cn dn: olcDatabase={2}hdb,cn=config changetype: modify replace: olcRootDN olcRootDN: cn=Manager,c=cn dn: olcDatabase={2}hdb,cn=config changetype: modify replace: olcRootPW olcRootPW: {SSHA}ago8nKNyfjhYa/btKgHDIpyEPxSBZrMm # 你上面生成的密码密钥 dn: olcDatabase={2}hdb,cn=config changetype: modify replace: olcAccess olcAccess: {0}to attrs=userPassword,shadowLastChange by dn="cn=Manager,c=cn" write by anonymous auth by self write by * none olcAccess: {1}to dn.base="" by * read olcAccess: {2}to * by dn="cn=Manager,c=cn" write by * read
导入chdomain.ldif文件
ldapmodify -Y EXTERNAL -H ldapi:/// -f chdomain.ldif
[root@cloud01-ops-tools-01 opt]# ldapmodify -Y EXTERNAL -H ldapi:/// -f chdomain.ldif SASL/EXTERNAL authentication started SASL username: gidNumber=0+uidNumber=0,cn=peercred,cn=external,cn=auth SASL SSF: 0 modifying entry "olcDatabase={1}monitor,cn=config" modifying entry "olcDatabase={2}hdb,cn=config" modifying entry "olcDatabase={2}hdb,cn=config" modifying entry "olcDatabase={2}hdb,cn=config" modifying entry "olcDatabase={2}hdb,cn=config"
============================================================= 温馨提示: 如果上面的命令出现下面报错: .......
....... ldap_modify: Inappropriate matching (18) additional info: modify/add: olcRootPW: no equality matching rule
解决办法:将chdomain.ldif文件中的"add"全部替换成"replace",然后重新执行上面命令即可! ============================================================
导入管理员基础数据
vim rootdn.ldif
#vim rootdn.ldif
dn: c=cn objectclass: country c: cn dn: cn=Manager,c=cn objectclass: organizationalRole cn: Manager
执行下面命令,输入上面设置的密码:123456 (就是输入你上面设置的密码)
[root@openldap-master opt]# ldapadd -x -D cn=Manager,c=cn -W -f rootdn.ldif Enter LDAP Password: adding new entry "c=cn" adding new entry "cn=Manager,c=cn"
开启日志配置 查看OpenLDAP的日志级别,日志主要用于对OpenLDAP排查
[root@openldap-master opt]# slapd -d ? Installed log subsystems: Any (-1, 0xffffffff) Trace (1, 0x1) Packets (2, 0x2) Args (4, 0x4) Conns (8, 0x8) BER (16, 0x10) Filter (32, 0x20) Config (64, 0x40) ACL (128, 0x80) Stats (256, 0x100) Stats2 (512, 0x200) Shell (1024, 0x400) Parse (2048, 0x800) Sync (16384, 0x4000) None (32768, 0x8000) NOTE: custom log subsystems may be later installed by specific code
编辑logLevel.ldif文件:
dn: cn=config
changetype: modify
replace: olcLogLevel
olcLogLevel: stats
[root@openldap-master opt]# vim logLevel.ldif [root@openldap-master opt]# cat logLevel.ldif dn: cn=config changetype: modify replace: olcLogLevel olcLogLevel: stats
导入logLevel.ldif
[root@openldap-master opt]# ldapmodify -Y EXTERNAL -H ldapi:/// -f logLevel.ldif SASL/EXTERNAL authentication started SASL username: gidNumber=0+uidNumber=0,cn=peercred,cn=external,cn=auth SASL SSF: 0 modifying entry "cn=config"
创建slapd.log文件;
日志文件;
[root@openldap-master opt]# touch /var/log/slapd.log [root@openldap-master opt]# vim /etc/rsyslog.conf +73 #"+73"表示指定位到文件73行 ....... local4.* /var/log/slapd.log
重启系统日志服务与ldap服务:
root@openldap-master opt]# systemctl restart rsyslog [root@openldap-master opt]# systemctl restart slapd [root@openldap-master opt]# systemctl status slapd [root@openldap-master opt]# tail -f /var/log/slapd.log May 17 18:24:38 openldap-master slapd[26195]: daemon: shutdown requested and initiated. May 17 18:24:38 openldap-master slapd[26195]: slapd shutdown: waiting for 0 operations/tasks to finish May 17 18:24:38 openldap-master slapd[26195]: slapd stopped. May 17 18:24:38 openldap-master slapd[26399]: @(#) $OpenLDAP: slapd 2.4.44 (Apr 12 2018 19:17:38) $#012#011mockbuild@x86-01.bsys.centos.org:/builddir/build/BUILD/openldap-2.4.44/openldap-2.4.44/servers/slapd May 17 18:24:39 openldap-master slapd[26402]: slapd starting
然后下载ldapadmin就可以进行连接了
ldapadmin:http://www.ldapadmin.org/download/ldapadmin.html
然后打开你的连接设置

名字就是你的管理员配置的时候设置的:
cn=Manager,c=cn密码就是123456