1、测试环境:
北京6云主机:120.92.51.75/10.0.3.13 VPC:10.0.0.0/16 Ren-test
上海2云主机:42.157.163.120/192.168.3.3 VPC:zxs_vpc
2、下载安装openwan: 1、安装依赖包: # yum -y install gmp-devel bison flex gcc 2、下载安装openswan https://download.openswan.org/openswan/ # wget https://download.openswan.org/openswan/openswan-2.6.43.1.tar.gz # tar zxf openswan-2.6.43.1.tar.gz # cd openswan-2.6.43.1 # make programs # sudo make install 3、启动openswan # /etc/init.d/ipsec start # 启动 # netstat -lnput |grep pluto # 查看监听端口 4、基础环境,内核参数等配置修改 # ipsec verify # 基础环境依赖、状态查看 ① 解决,更新如下配置: echo 0 > /proc/sys/net/ipv4/conf/all/rp_filter; echo 0 > /proc/sys/net/ipv4/conf/default/rp_filter; echo 0 > /proc/sys/net/ipv4/conf/eth0/rp_filter; echo 0 > /proc/sys/net/ipv4/conf/eth1/rp_filter; echo 0 > /proc/sys/net/ipv4/conf/lo/rp_filter; ② 配置服务器路由转发功能等操作 # vi /etc/sysctl.conf net.ipv4.ip_forward = 1 # 开启转发 net.ipv4.conf.default.rp_filter = 0 # 关闭icmp重定向 # sysctl -a | egrep "ipv4.*(accept|send)_redirects" | awk -F "=" '{print$1"= 0"}' >> /etc/sysctl.conf # sysctl -p ③ 检查最终效果 # ipsec verify
#北京6云主机配置: [root@vm10-0-3-13 ]# cat /etc/issue CentOS release 6.9 (Final) [root@vm10-0-3-13 ~]# curl myip.ksyun.com {"eip":"120.92.51.75"} [root@vm10-0-3-13 ~]# cat /etc/sysctl.conf net.ipv4.ip_forward = 1 net.ipv4.conf.default.rp_filter = 0 net.ipv4.conf.default.accept_source_route = 0 kernel.sysrq = 0 kernel.core_uses_pid = 1 net.ipv4.tcp_syncookies = 1 net.bridge.bridge-nf-call-ip6tables = 0 net.bridge.bridge-nf-call-iptables = 0 net.bridge.bridge-nf-call-arptables = 0 kernel.msgmnb = 65536 kernel.msgmax = 65536 kernel.shmmax = 68719476736 kernel.shmall = 4294967296 net.ipv4.tcp_keepalive_time = 1200 net.ipv4.ip_local_port_range = 1024 65535 net.ipv4.conf.all.rp_filter = 0 net.ipv4.conf.default.rp_filter = 0 net.ipv4.conf.eth0.rp_filter = 0 net.ipv4.conf.eth1.rp_filter = 0 net.ipv4.conf.all.arp_announce = 2 net.ipv4.conf.default.arp_announce = 2 net.ipv4.conf.eth0.arp_announce = 2 net.ipv4.conf.eth1.arp_announce = 2 net.ipv6.conf.all.disable_ipv6 = 0 net.ipv6.conf.default.disable_ipv6 = 0 net.ipv6.conf.lo.disable_ipv6 = 0 net.ipv4.conf.all.accept_redirects = 0 net.ipv4.conf.all.send_redirects = 0 net.ipv4.conf.default.accept_redirects = 0 net.ipv4.conf.default.send_redirects = 0 net.ipv4.conf.lo.accept_redirects = 0 net.ipv4.conf.lo.send_redirects = 0 net.ipv4.conf.eth0.accept_redirects = 0 net.ipv4.conf.eth0.send_redirects = 0 net.ipv4.conf.eth1.accept_redirects = 0 net.ipv4.conf.eth1.send_redirects = 0 [root@vm10-0-3-13 ~]# cat /etc/ipsec.d/ksyun.conf conn BJ-to-SH ike=3des-sha1 authby=secret phase2=esp phase2alg=3des-sha1 compress=no type=tunnel pfs=yes leftid=42.157.163.120 left=42.157.163.120 leftsubnet=192.168.0.0/16 leftnexthop=%defaultroute rightid=120.92.51.75 right=10.0.3.13 rightsubnet=10.0.0.0/16 rightnexthop=%defaultroute auto=start [root@vm10-0-3-13 ~]# cat /etc/ipsec.secrets #include /etc/ipsec.d/*.secrets 0.0.0.0 0.0.0.0 : PSK "kingsoft" [root@vm10-0-3-13 ~]# ip addr show 1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00 inet 127.0.0.1/8 scope host lo 2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP qlen 1000 link/ether fa:16:3e:0c:35:df brd ff:ff:ff:ff:ff:ff inet 10.0.3.13/24 brd 10.0.3.255 scope global eth0 3: eth1: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP qlen 1000 link/ether fa:16:3e:3e:72:2f brd ff:ff:ff:ff:ff:ff inet 10.0.2.208/24 brd 10.0.2.255 scope global eth1 [root@vm10-0-3-13 ~]# ip route show 10.0.2.0/24 dev eth1 proto kernel scope link src 10.0.2.208 10.0.3.0/24 dev eth0 proto kernel scope link src 10.0.3.13 169.254.0.0/16 dev eth0 scope link metric 1002 169.254.0.0/16 dev eth1 scope link metric 1003 default via 10.0.3.1 dev eth0 [root@vm10-0-3-13 log]# tail -20 /var/log/pluto.log Jul 25 15:30:57: listening for IKE messages Jul 25 15:30:57: adding interface eth1/eth1 10.0.2.208:500 Jul 25 15:30:57: adding interface eth1/eth1 10.0.2.208:4500 Jul 25 15:30:57: adding interface eth0/eth0 10.0.3.13:500 Jul 25 15:30:57: adding interface eth0/eth0 10.0.3.13:4500 Jul 25 15:30:57: adding interface lo/lo 127.0.0.1:500 Jul 25 15:30:57: adding interface lo/lo 127.0.0.1:4500 Jul 25 15:30:57: | setup callback for interface lo:4500 fd 23 Jul 25 15:30:57: | setup callback for interface lo:500 fd 22 Jul 25 15:30:57: | setup callback for interface eth0:4500 fd 21 Jul 25 15:30:57: | setup callback for interface eth0:500 fd 20 Jul 25 15:30:57: | setup callback for interface eth1:4500 fd 19 Jul 25 15:30:57: | setup callback for interface eth1:500 fd 18 Jul 25 15:30:57: loading secrets from "/etc/ipsec.secrets" Jul 25 15:30:57: "BJ-to-SH" #1: initiating Main Mode Jul 25 15:30:57: "BJ-to-SH" #1: ignoring Vendor ID payload [Openswan(xeleranized)] Jul 25 15:30:57: "BJ-to-SH" #1: received Vendor ID payload [Dead Peer Detection] Jul 25 15:30:57: "BJ-to-SH" #1: received Vendor ID payload [RFC 3947] Jul 25 15:30:57: "BJ-to-SH" #1: enabling possible NAT-traversal with method RFC 3947 (NAT-Traversal) Jul 25 15:30:57: "BJ-to-SH" #1: transition from state STATE_MAIN_I1 to state STATE_MAIN_I2 Jul 25 15:30:57: "BJ-to-SH" #1: STATE_MAIN_I2: sent MI2, expecting MR2 Jul 25 15:30:57: "BJ-to-SH" #1: NAT-Traversal: Result using RFC 3947 (NAT-Traversal) sender port 500: I am behind NAT+peer behind NAT Jul 25 15:30:57: "BJ-to-SH" #1: transition from state STATE_MAIN_I2 to state STATE_MAIN_I3 Jul 25 15:30:57: "BJ-to-SH" #1: STATE_MAIN_I3: sent MI3, expecting MR3 Jul 25 15:30:57: "BJ-to-SH" #1: received Vendor ID payload [CAN-IKEv2] Jul 25 15:30:57: "BJ-to-SH" #1: Main mode peer ID is ID_IPV4_ADDR: '42.157.163.120' Jul 25 15:30:57: "BJ-to-SH" #1: transition from state STATE_MAIN_I3 to state STATE_MAIN_I4 Jul 25 15:30:57: "BJ-to-SH" #1: STATE_MAIN_I4: ISAKMP SA established {auth=PRESHARED_KEY cipher=oakley_3des_cbc_192 integ=sha group=MODP2048} Jul 25 15:30:57: "BJ-to-SH" #2: initiating Quick Mode PSK+ENCRYPT+TUNNEL+PFS+UP+IKEV1_ALLOW+IKEV2_ALLOW+SAREF_TRACK+IKE_FRAG_ALLOW {using isakmp#1 msgid:8d92af45 proposal=3DES(3)_000-SHA1(2)_000 pfsgroup=OAKLEY_GROUP_MODP2048} Jul 25 15:30:57: "BJ-to-SH" #2: transition from state STATE_QUICK_I1 to state STATE_QUICK_I2 Jul 25 15:30:57: "BJ-to-SH" #2: STATE_QUICK_I2: sent QI2, IPsec SA established tunnel mode {ESP/NAT=>0x32aaec51 <0x73d0c6c9 xfrm=3DES_0-HMAC_SHA1 NATOA=none NATD=42.157.163.120:4500 DPD=passive}
上海2云主机配置: [root@vm192-168-3-9 ~]# cat /etc/issue S Kernel on an m [root@vm192-168-3-9 ~]# curl myip.ksyun.com {"eip":"42.157.163.120"} [root@vm192-168-3-9 ~]# cat /etc/ipsec.d/ksyun.conf conn SH-to-BJ ike=3des-sha1 authby=secret phase2=esp phase2alg=3des-sha1 compress=no type=tunnel pfs=yes leftid=42.157.163.120 left=192.168.3.9 leftsubnet=192.168.0.0/16 leftnexthop=%defaultroute rightid=120.92.51.75 right=120.92.51.75 rightsubnet=10.0.0.0/16 rightnexthop=%defaultroute auto=start [root@vm192-168-3-9 ~]# cat /etc/ipsec.secrets 0.0.0.0 0.0.0.0 : PSK "kingsoft" [root@vm192-168-3-9 ~]# ip addr show 1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000 link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00 inet 127.0.0.1/8 scope host lo valid_lft forever preferred_lft forever 2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP group default qlen 1000 link/ether fa:16:3e:7d:86:8f brd ff:ff:ff:ff:ff:ff inet 192.168.3.9/24 brd 192.168.3.255 scope global eth0 valid_lft forever preferred_lft forever [root@vm192-168-3-9 ~]# ip route show default via 192.168.3.1 dev eth0 169.254.0.0/16 dev eth0 scope link metric 1002 192.168.3.0/24 dev eth0 proto kernel scope link src 192.168.3.9 [root@vm192-168-3-9 ~]# tail -20 /var/log/messages Jul 25 15:07:32 vm192-168-3-9 ipsec_setup: Starting Openswan IPsec U2.6.43/K3.10.0-862.14.4.el7.x86_64... Jul 25 15:07:32 vm192-168-3-9 ipsec_setup: Using NETKEY(XFRM) stack Jul 25 15:07:32 vm192-168-3-9 kernel: IPv6: esp6_init: can't add xfrm type Jul 25 15:07:32 vm192-168-3-9 kernel: IPv6: ah6_init: can't add xfrm type Jul 25 15:07:32 vm192-168-3-9 kernel: AVX2 instructions are not detected. Jul 25 15:07:33 vm192-168-3-9 kernel: AVX2 or AES-NI instructions are not detected. Jul 25 15:07:33 vm192-168-3-9 ipsec_setup: ...Openswan IPsec started Jul 25 15:07:33 vm192-168-3-9 pluto: adjusting ipsec.d to /etc/ipsec.d Jul 25 15:07:33 vm192-168-3-9 ipsec__plutorun: 002 added connection description "SH-to-BJ" Jul 25 15:07:33 vm192-168-3-9 ipsec__plutorun: 002 listening for IKE messages Jul 25 15:07:33 vm192-168-3-9 ipsec__plutorun: 002 adding interface eth0/eth0 192.168.3.9:500 Jul 25 15:07:33 vm192-168-3-9 ipsec__plutorun: 002 adding interface eth0/eth0 192.168.3.9:4500 Jul 25 15:07:33 vm192-168-3-9 ipsec__plutorun: 002 adding interface lo/lo 127.0.0.1:500 Jul 25 15:07:33 vm192-168-3-9 ipsec__plutorun: 002 adding interface lo/lo 127.0.0.1:4500 Jul 25 15:07:33 vm192-168-3-9 ipsec__plutorun: 002 loading secrets from "/etc/ipsec.secrets" [root@vm192-168-3-9 ~]# 可以配置/etc/ipsec.conf中logfile=/var/log/pluto.log或plutostderrlog=/var/log/pluto.log开启openwan日志 added connection description "SH-to-BJ" listening for IKE messages adding interface eth0/eth0 192.168.3.9:500 adding interface eth0/eth0 192.168.3.9:4500 adding interface lo/lo 127.0.0.1:500 adding interface lo/lo 127.0.0.1:4500 loading secrets from "/etc/ipsec.secrets" packet from 120.92.51.75:500: received Vendor ID payload [Dead Peer Detection] packet from 120.92.51.75:500: ignoring Vendor ID payload [FRAGMENTATION] packet from 120.92.51.75:500: received Vendor ID payload [RFC 3947] method set to=115 packet from 120.92.51.75:500: received Vendor ID payload [draft-ietf-ipsec-nat-t-ike-03] meth=108, but already using method 115 packet from 120.92.51.75:500: received Vendor ID payload [draft-ietf-ipsec-nat-t-ike-02_n] meth=106, but already using method 115 packet from 120.92.51.75:500: received Vendor ID payload [draft-ietf-ipsec-nat-t-ike-02] meth=107, but already using method 115 "SH-to-BJ" #1: responding to Main Mode "SH-to-BJ" #1: transition from state STATE_MAIN_R0 to state STATE_MAIN_R1 "SH-to-BJ" #1: STATE_MAIN_R1: sent MR1, expecting MI2 "SH-to-BJ" #1: NAT-Traversal: Result using draft-ietf-ipsec-nat-t-ike (MacOS X): both are NATed "SH-to-BJ" #1: transition from state STATE_MAIN_R1 to state STATE_MAIN_R2 "SH-to-BJ" #1: STATE_MAIN_R2: sent MR2, expecting MI3 "SH-to-BJ" #1: Main mode peer ID is ID_IPV4_ADDR: '120.92.51.75' "SH-to-BJ" #1: transition from state STATE_MAIN_R2 to state STATE_MAIN_R3 "SH-to-BJ" #1: new NAT mapping for #1, was 120.92.51.75:500, now 120.92.51.75:4500 "SH-to-BJ" #1: STATE_MAIN_R3: sent MR3, ISAKMP SA established {auth=OAKLEY_PRESHARED_KEY cipher=oakley_3des_cbc_192 prf=oakley_sha group=modp2048} "SH-to-BJ" #1: the peer proposed: 192.168.0.0/16:0/0 -> 10.0.0.0/16:0/0 "SH-to-BJ" #2: responding to Quick Mode proposal {msgid:d6c02a77} "SH-to-BJ" #2: us: 192.168.0.0/16===192.168.3.9<192.168.3.9>[42.157.163.120]---192.168.3.1 "SH-to-BJ" #2: them: 192.168.3.1---120.92.51.75<120.92.51.75>===10.0.0.0/16 "SH-to-BJ" #2: transition from state STATE_QUICK_R0 to state STATE_QUICK_R1 "SH-to-BJ" #2: STATE_QUICK_R1: sent QR1, inbound IPsec SA installed, expecting QI2 "SH-to-BJ" #2: transition from state STATE_QUICK_R1 to state STATE_QUICK_R2 "SH-to-BJ" #2: STATE_QUICK_R2: IPsec SA established tunnel mode {ESP=>0xd85f23ba <0x232e6a69 xfrm=3DES_0-HMAC_SHA1 NATOA=none NATD=120.92.51.75:45 00 DPD=none}
3、VPC控制台路由配置:
北京6 VPC:

上海2 VPC:
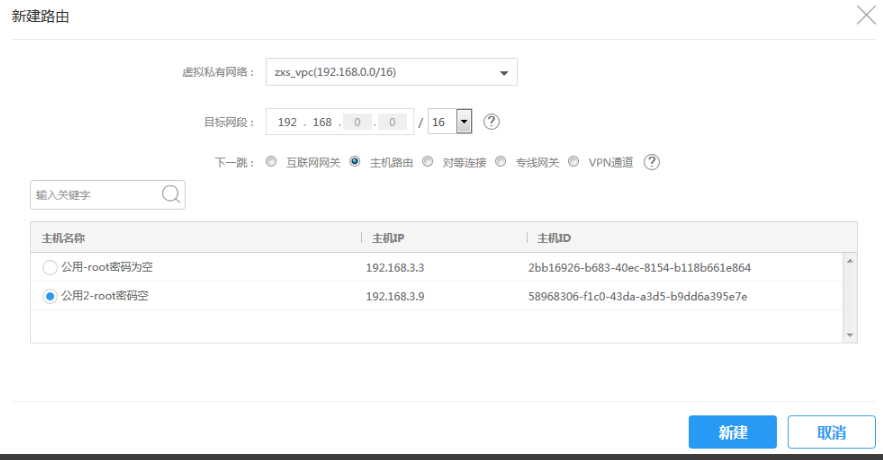
参考文档:https://www.172173.com/openswan.html#2-5-%E9%AA%8C%E8%AF%81%E7%8E%AF%E5%A2%83
zxs_vpc