puppet是什么
puppet是一种基于ruby语言开发的Lnux、Unix、windows平台的集中配置管理系统。它使用自有的puppet描述语言,可管理配置文件file、用户user、cron任务、软件包、系统服务等系统实体。
puppet把这些系统实体称之为资源,puppet设计目标是简化对这些资源的管理以及妥善处理资源间的依赖关系。
puppet依赖于C/S(客户端/服务器)的部署架构。它需要在puppet服务器上安装puppet-server软件包(以下简称master),在需要管理的目标主机上安装puppet客户端软件(以下简称agent)。
当agent连接上master后,定义在master端的配置文件会被编译,然后在agent上运行。每个agent默认30分钟会连接一次master,确认配置信息的更新情况。但是这种方式在很多场景下不是很符合系统管理员的要求,所以很多系统管理员也会将agent通过crontab(任务计划)来管理,这样会更加灵活一些。
puppet优点
puppet的语法允许你创建一个单独的脚本,用来在你所有的目标主机上建立一个用户。所有的目标主机会依次使用适合本地系统的语法来解释和执行这个模块。如果这个配置是在Red Hat服务器上执行的话,建立用户使用useradd命令,如果这个配置是在FreddBSD服务器上执行的话,则使用adduser命令。
puppet另外一个卓越的地方就是它的灵活性。源于开源软件的天性,你可以自由地获得puppet的源代码。如果你遇到问题并且有能力处理的话,你可以修改或加强puppet的代码使其适用于你的环境,然后解决这个问题。
puppet也是易于扩展的。定制软件包的支持功能和特殊的系统环境配置能够快速简单地添加至puppet的安装程序中。
基本安装环境centos6.5
IP配置图
192.168.186.151 Master-node.localdomain #主
192.168.186.178 Agent-node1.localdomain #从
192.168.186.163 Agent-node2.localdomain #从
192.168.186.175 Agent-node3.localdomain #从
需要先设置域名解析
127.0.0.1 localhost localhost.localdomain localhost4 localhost4.localdomain4 ::1 localhost localhost.localdomain localhost6 localhost6.localdomain6 192.168.80.130 master-node.localdomain 192.168.80.136 agent1-node.localdomain 192.168.80.137 agent2-node.localdomain 192.168.80.139 agent3-node.localdomain
需要官方提供的yum源
wget http://yum.puppetlabs.com/el/6/products/x86_64/puppetlabs-release-6-10.noarch.rpm
yum install puppetlabs-release-6-1.noarch.rpm
在四台主机上去安装官方yum源如上:^
在master主机上安装如下:
yum install -y ruby facter puppet-server
service puppet start #启动客户端
service puppetmaster start #启动服务端
chkconfig puppet on
chkconfig puppetmaster on
在客户端(agent)安装如下:
[root@Agent-node1 ~]# yum install -y ruby facter puppet
[root@Agent-node1 ~]# service puppet start #启动
[root@Agent-node1 ~]# chkconfig puppet on
[root@Agent-node1 ~]# vim /etc/puppet/puppet.conf
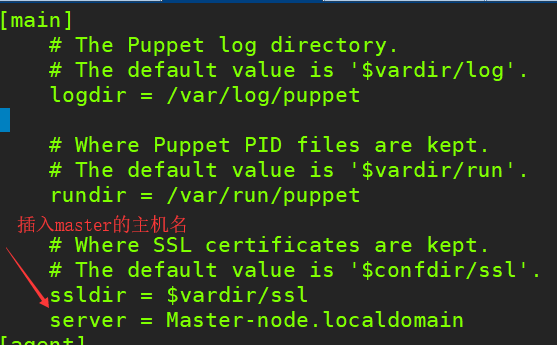
[root@Agent-node1 ~]# /etc/init.d/puppet restart #重启服务
从日志中我们可以看出第一次启动master端时,puppet服务会在本地创建认证中心,给自己授权证书和key,我们可以查看/var/lib/puppet/ssl看到那些证书和key。如下:
[root@Master-node ~]# tail -f /var/log/messages
......Jul 25 15:02:13 puppet01 puppet-master[23689]: Signed certificate request for caJul 25 15:02:14 puppet01 puppet-master[23689]: Master-node has a waiting certificate requestJul 25 15:02:14 puppet01 puppet-master[23689]: Signed certificate request for Master-nodeJul 25 15:02:14 puppet01 puppet-master[23689]: Removing file Puppet::SSL::CertificateRequest Master-node at '/var/lib/puppet/ssl/ca/requests/Master-node.pem'Jul 25 15:02:14 puppet01 puppet-master[23689]: Removing file Puppet::SSL::CertificateRequest Master-node at '/var/lib/puppet/ssl/certificate_requests/Master-node.pem'Jul 25 15:02:14 puppet01 puppet-master[23727]: Reopening log filesJul 25 15:02:14 puppet01 puppet-master[23727]: Starting Puppet master version 3.8.7Jul 25 15:03:00 puppet01 puppet-master[23727]: puppet02.bkjk.cn has a waiting certificate request[root@Master-node ~]# ll /var/lib/puppet/ssldrwxr-xr-x. 5 puppet puppet 4096 1月 1 19:38 ca
drwxr-xr-x. 2 puppet puppet 4096 1月 1 19:39 certificate_requests
drwxr-xr-x. 2 puppet puppet 4096 1月 1 19:39 certs
drwxr-x---. 2 puppet puppet 4096 1月 1 19:38 private
drwxr-x---. 2 puppet puppet 4096 1月 1 19:39 private_keys
drwxr-xr-x. 2 puppet puppet 4096 1月 1 19:39 public_keys
这个目录下的信息和/etc/puppet/puppet.conf文件中配置的ssldir路径是对应的在查看master端给自己授权的证书文件[root@Master-node ~]# ll /var/lib/puppet/ssl/ca/signed-rw-r--r--. 1 puppet puppet 2098 1月 1 19:39 master-node.localdomain.pem
一、手动注册(批量效率高)手动注册是由Agent端先发起证书申请请求,然后由Puppetserver端确认认证方可注册成功,这种注册方式安全系数中等,逐一注册(puppet cert --sign certnmame)在节点数量较大的情况下是比较麻烦的,效率也低,批量注册(puppet cert --sign --all)效率很高,一次性便可注册所有的Agent的请求,但是这种方式安全系数较低,因为错误的请求也会被注册上。 1)需要先在Agent节点申请注册(三台Agent节点机都要操作)由于已经Agent的puppet.conf文件里设置了server地址,因此下面向Master请求认证的命令中不需要跟服务端地址。否则需要在下面的命令中添加Master服务端地址,即添加"--server Master-node"[root@agent2-node ~]# puppet agent --test
Info: Creating a new SSL key for agent2-node.localdomain
Info: Caching certificate for ca
Info: Caching certificate_request for agent2-node.localdomain
Info: Caching certificate for ca
Exiting; no certificate found and waitforcert is disabled
2) Master服务器端查看认证情况[root@master-node opt]# puppet cert --list "agent1-node.localdomain" (SHA256) F7:23:7D:79:90:A8:18:99:B9:74:39:83:D1:BC:7C:6D:47:A5:0E:E2:4D:3C:00:9F:62:BC:9E:66:14:EC:E9:7D "agent2-node.localdomain" (SHA256) 89:86:B9:CB:99:B8:F3:B6:71:E5:4E:67:E7:7C:84:7E:FF:A5:E6:B3:1A:06:93:E0:AB:A6:B0:CA:5A:FD:63:3B "agent3-node.localdomain" (SHA256) 22:89:82:22:B1:CE:D5:E7:51:C2:00:57:01:54:C6:F7:B2:0E:21:09:72:3B:32:28:31:CF:8E:5A:B9:AC:3C:13
3)查看到puppet所有签发的本地证书了[root@master-node opt]# puppet cert --list --all #加--all参数 "agent1-node.localdomain" (SHA256) F7:23:7D:79:90:A8:18:99:B9:74:39:83:D1:BC:7C:6D:47:A5:0E:E2:4D:3C:00:9F:62:BC:9E:66:14:EC:E9:7D "agent2-node.localdomain" (SHA256) 89:86:B9:CB:99:B8:F3:B6:71:E5:4E:67:E7:7C:84:7E:FF:A5:E6:B3:1A:06:93:E0:AB:A6:B0:CA:5A:FD:63:3B "agent3-node.localdomain" (SHA256) 22:89:82:22:B1:CE:D5:E7:51:C2:00:57:01:54:C6:F7:B2:0E:21:09:72:3B:32:28:31:CF:8E:5A:B9:AC:3C:13 + "master-node.localdomain" (SHA256) 1D:A9:62:4D:29:48:B9:BC:A1:C2:32:0B:89:7B:D1:2B:5A:B3:EB:22:D1:6A:06:FC:31:F0:F8:62:F2:0B:AB:EE (alt names: "DNS:master-node.localdomain", "DNS:puppet", "DNS:puppet.localdomain") + "master.localdomain" (SHA256) 27:CE:03:2A:D1:6F:FD:5E:62:D0:1B:9B:64:CC:FD:45:E3:4F:26:B0:E0:37:B9:DE:38:7B:44:00:D8:CF:BF:D5 (alt names: "DNS:master.localdomain", "DNS:puppet", "DNS:puppet.localdomain")
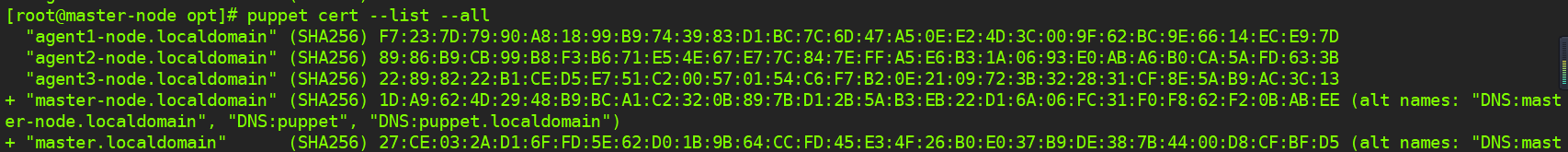
以上结果中:左边有+号的,表示已经签发,puppet首先会给自己签发一个本地证书;客户端的证书前没+号,这就等待服务端签发。 4)接着Master服务端签发证书,及注册Agent节点[root@Master-node ~]# puppet cert --list agent1-node[root@Master-node ~]# puppet cert --list agent2-node[root@Master-node ~]# puppet cert --list agent3-node[root@Master-node ~]# puppet cert --sign --all #可以使用这个命令代替单个认证,表示签发所有Agent的证书 [root@master-node opt]# puppet cert --sign --all Notice: Signed certificate request for agent2-node.localdomain Notice: Removing file Puppet::SSL::CertificateRequest agent2-node.localdomain at '/var/lib/puppet/ssl/ca/requests/agent2-node.localdomain.pem' Notice: Signed certificate request for agent3-node.localdomain Notice: Removing file Puppet::SSL::CertificateRequest agent3-node.localdomain at '/var/lib/puppet/ssl/ca/requests/agent3-node.localdomain.pem' Notice: Signed certificate request for agent1-node.localdomain Notice: Removing file Puppet::SSL::CertificateRequest agent1-node.localdomain at '/var/lib/puppet/ssl/ca/requests/agent1-node.localdomain.pem'
再次查看认证情况,发现已经都认证了(+号代表已经认证)[root@master-node opt]# puppet cert --list --all + "agent1-node.localdomain" (SHA256) B9:93:D1:55:2E:2B:B3:F4:B1:E9:A9:A1:69:01:3A:46:EF:0A:A5:83:86:FF:07:DC:93:75:C6:69:59:43:88:E7 + "agent2-node.localdomain" (SHA256) 18:29:E7:C1:39:3C:18:48:62:70:D6:24:9E:27:3B:8C:94:DB:5D:3A:5A:D2:48:3A:11:8B:13:9D:54:1E:02:D0 + "agent3-node.localdomain" (SHA256) B7:38:42:2F:D0:5B:C4:54:28:2A:58:CA:22:79:2C:25:DD:C0:1F:A4:8F:8D:32:51:48:E1:0E:91:2C:83:90:D3 + "master-node.localdomain" (SHA256) 1D:A9:62:4D:29:48:B9:BC:A1:C2:32:0B:89:7B:D1:2B:5A:B3:EB:22:D1:6A:06:FC:31:F0:F8:62:F2:0B:AB:EE (alt names: "DNS:master-node.localdomain", "DNS:puppet", "DNS:puppet.localdomain") + "master.localdomain" (SHA256) 27:CE:03:2A:D1:6F:FD:5E:62:D0:1B:9B:64:CC:FD:45:E3:4F:26:B0:E0:37:B9:DE:38:7B:44:00:D8:CF:BF:D5 (alt names: "DNS:master.localdomain", "DNS:puppet", "DNS:puppet.localdomain") [root@master-node opt]#
另一种查看认证的方法:yum安装tree命令
[root@master-node opt]# tree /var/lib/puppet/ssl/ /var/lib/puppet/ssl/ ├── ca │ ├── ca_crl.pem │ ├── ca_crt.pem │ ├── ca_key.pem │ ├── ca_pub.pem │ ├── inventory.txt │ ├── private │ │ └── ca.pass │ ├── requests │ ├── serial │ └── signed │ ├── agent1-node.localdomain.pem │ ├── agent2-node.localdomain.pem │ ├── agent3-node.localdomain.pem │ ├── master.localdomain.pem │ └── master-node.localdomain.pem ├── certificate_requests ├── certs │ ├── ca.pem │ ├── master.localdomain.pem │ └── master-node.localdomain.pem ├── crl.pem ├── private ├── private_keys │ ├── master.localdomain.pem │ └── master-node.localdomain.pem └── public_keys ├── master.localdomain.pem └── master-node.localdomain.pem
最后在Agent端进行motd模块测试(即客户端取回通过的证书)[root@Agent-node1 ~]# puppet agent --test //--test也可以替换为-tInfo: Caching certificate for agent-node1.localdomain
Info: Caching certificate_revocation_list for ca
Info: Caching certificate for agent-node1.localdomain
Warning: Unable to fetch my node definition, but the agent run will continue:
Warning: undefined method `include?' for nil:NilClass
Info: Retrieving pluginfacts
Info: Retrieving plugin
Info: Caching catalog for agent-node1.localdomain
Info: Applying configuration version '1546343527'
Info: Creating state file /var/lib/puppet/state/state.yaml
-------------------------------------------------------------------------------也可以直接使用命令"puppet agent --no-daemonize --onetime --verbose --debug",打印证书申请过程中的详细信息--no-daemonize 前台输出日志--verbose 输入更加详细的日志--debug 更加详细的日志,排错的时候使用--test 表示测试,就带一个–test参数就可以------------------------------------------------------------------------------- -------------------------------证书管理------------------------------当出现问题需要重新申请证书或重新安装puppet时使用,需要注销证书和删除证书 注销证书既是要证书过期(--revoke)[root@Master-node ~]# puppet cert --revoke agent-node1 Notice: Revoked certificate with serial 10[root@Master-node ~]# puppet cert --list --all //如下,过期的证书签名是"-"号+ "agent-node1.localdomain" (SHA256) 26:6B:8F:36:BD:5D:58:E6:9A:99:49:13:24:7C:1D:43:6A:32:94:D7:FF:DD:2C:16:B0:A1:15:7B:9F:E9:D5:7C
+ "agent-node2.localdomain" (SHA256) 7F:18:02:1F:7B:AB:F6:15:41:1C:C5:5A:ED:9A:40:16:22:55:AA:13:FF:A1:F0:4A:80:E9:AC:0B:3D:6D:88:5F
+ "agent-node3.localdomain" (SHA256) 35:B6:F8:D0:2A:CC:FD:2A:66:A1:43:D9:CA:4A:C9:CC:12:42:1E:5A:04:2C:4F:1B:C3:CC:49:1A:AB:C5:19:14
- "master-node.localdomain" (SHA256) D4:A4:44:54:FA:2B:A0:A2:53:CD:DA:FE:B7:85:F0:26:49:24:2A:06:E1:89:B1:41:5B:04:97:4D:76:07:AD:34 (alt names: "DNS:Master-node.localdomain", "DNS:master-node.localdomain", "DNS:puppet", "DNS:puppet.localdomain")
[root@Master-node ~]# puppet cert --revoke --all //注销所有证书 上面只是让证书失效,客户端连接会失败,并没有删除证书文件。 删除证书(--clean)[root@Master-node ~]# puppet cert --clean agent-node1 //删除agent-node1证书[root@Master-node ~]# puppet cert --clean --all //删除所有证书 证书签名的过期或删除需要重启puppetmaster服务后才能生效。[root@Master-node ~]# /etc/init.d/puppetmaster restartStopping puppetmaster: [ OK ]Starting puppetmaster: [ OK ] 重启后,puppet会给自己自动签发一个本地证书[root@Master-node ~]# puppet cert --list --all+ "master-node.localdomain" (SHA256) D4:A4:44:54:FA:2B:A0:A2:53:CD:DA:FE:B7:85:F0:26:49:24:2A:06:E1:89:B1:41:5B:04:97:4D:76:07:AD:34 (alt names: "DNS:Master-node.localdomain", "DNS:master-node.localdomain", "DNS:puppet", "DNS:puppet.localdomain")
注意删除证书到重新请求证书的流程:在Master端删除证书(puppet cert --clean agent-node1)在Agent端删除注册过的证书文件:rm -rf /var/lib/puppet/ssl/*在Agent端重新请求证书(puppet agent ----test )----------------------------------------------------------------------------------------------------------------------------------------------- 二、自动注册(安全系数低,效率高)这种注册方式简单来讲是通过Puppetmaster端的ACL列表进行控制的,安全系统较低,也就是说符合预先定义的ACL列表中的所有节点请求不需要确认都会被自动注册上,也就是说你只需要知道ACL列表要求,其次能和PuppetMaster端通信便可轻易注册成功。当然,它的最大优点就是效率非常高。 1)清除Master端已经注册的agent的证书[root@Master-node ~]# puppet cert --clean agent-node1 //可以一个个的针对单个agent节点进行清除[root@Master-node ~]# puppet cert --clean --all //也可以清除所有agent节点的证书 2)在agent端删除注册的所有信息,包括证书。这个很重要!!当在PupperMaster端删除agent的证书后,一定要登录对应的agent节点上执行下面的操作:删除注册过的证书,否则再次注册就会报错失败![root@Agent-node1 ~]# rm -rf /var/lib/puppet/ssl/* 3)在master端编写ACL列表设置master自动签发所有的证书[root@Master-node ~]# vim /etc/puppet/puppet.conf //在文件底部添加下面内容[main] autosign = true autosign = /etc/puppet/autosign.conf[root@Master-node ~]# vim /etc/puppet/autosign.conf //设置下面内容,*表示允许所有域下的主机注册本Master端的证书* [root@Master-node ~]# /etc/init.d/puppet restart[root@Master-node ~]# service puppetmaster restart[root@Master-node ~]# puppet cert --list --all+ "master-node.localdomain" (SHA256) D4:A4:44:54:FA:2B:A0:A2:53:CD:DA:FE:B7:85:F0:26:49:24:2A:06:E1:89:B1:41:5B:04:97:4D:76:07:AD:34 (alt names: "DNS:Master-node.localdomain", "DNS:master-node.localdomain", "DNS:puppet", "DNS:puppet.localdomain")
接着在所有的Agent节点申请证书[root@Agent-node1 ~]# puppet agent --testInfo: Creating a new SSL key for agent-node1Info: Caching certificate for caInfo: csr_attributes file loading from /etc/puppet/csr_attributes.yamlInfo: Creating a new SSL certificate request for agent-node1Info: Certificate Request fingerprint (SHA256): 79:F5:6B:9B:0C:38:68:B7:A6:C3:9E:E4:7E:19:76:8B:61:35:CA:D0:66:E4:81:B4:15:09:DB:24:ED:3F:E2:3FInfo: Caching certificate for agent-node1Info: Caching certificate_revocation_list for caInfo: Caching certificate for caInfo: Retrieving pluginfactsInfo: Retrieving pluginInfo: Caching catalog for agent-node1Info: Applying configuration version '1495879417'Notice: Finished catalog run in 0.05 seconds 然后在Master端查看证书是否已经自动注册上了。如下,发现已经自动注册了[root@Master-node ~]# puppet cert --list --all+ "agent-node1.localdomain" (SHA256) 26:6B:8F:36:BD:5D:58:E6:9A:99:49:13:24:7C:1D:43:6A:32:94:D7:FF:DD:2C:16:B0:A1:15:7B:9F:E9:D5:7C
+ "agent-node2.localdomain" (SHA256) 7F:18:02:1F:7B:AB:F6:15:41:1C:C5:5A:ED:9A:40:16:22:55:AA:13:FF:A1:F0:4A:80:E9:AC:0B:3D:6D:88:5F
+ "agent-node3.localdomain" (SHA256) 35:B6:F8:D0:2A:CC:FD:2A:66:A1:43:D9:CA:4A:C9:CC:12:42:1E:5A:04:2C:4F:1B:C3:CC:49:1A:AB:C5:19:14
+ "master-node.localdomain" (SHA256) D4:A4:44:54:FA:2B:A0:A2:53:CD:DA:FE:B7:85:F0:26:49:24:2A:06:E1:89:B1:41:5B:04:97:4D:76:07:AD:34 (alt names: "DNS:Master-node.localdomain", "DNS:master-node.localdomain", "DNS:puppet", "DNS:puppet.localdomain")
最后在Agent节点测试[root@Agent-node1 ~]# puppet agent --testInfo: Retrieving pluginfactsInfo: Retrieving pluginInfo: Caching catalog for agent-node1Info: Applying configuration version '1495879417'Notice: Finished catalog run in 0.07 seconds----------------------------------------------------------------------------------------------------------------------------------------------- 三、预签名注册(推荐生产环境中使用此方式进行注册,既安全预签名注册是在agent端未提出申请的情况下,预先在puppet master端生成agent端的证书,然后把证书复制到agent节点对应的目录下即可注册成功,这样可以避免自动签名的危险。这种方式安全系数最高,但是操作麻烦,需要提前预知所有节点服务器的certname名称,其次需要将生成的证书逐步copy到所有节点上去。不过,如果你的系统中安装了kickstart或者cobbler这样的自动化工具,倒是可以将证书部分转换成脚本集成到统一自动化部署中 1)清除Master端已经注册的agent的证书[root@Master-node ~]# puppet cert --clean --all //清除所有注册过的证书,也可以指定某个Agent节点的证书清除[root@Master-node ~]# puppet cert --list --all //查看证书是否已清除[root@Master-node ~]# /etc/init.d/puppetmaster restart 2)在agent端删除注册的所有信息,包括证书。[root@Agent-node1 ~]# rm -rf /var/lib/puppet/* 3)在Master端删除自动注册ACL列表[root@Master-node ~]# mv /etc/puppet/autosign.conf /etc/puppet/autosign.conf.bak 4)在Master端预先生成Agent证书(这个只能针对agent端的节点一个个的生成证书了)[root@Master-node ~]# puppet cert generate agent-node1[root@Master-node ~]# puppet cert generate agent-node2[root@Master-node ~]# puppet cert generate agent-node3 查看证书[root@Master-node ~]# puppet cert --list --all+ "agent-node1.localdomain" (SHA256) 26:6B:8F:36:BD:5D:58:E6:9A:99:49:13:24:7C:1D:43:6A:32:94:D7:FF:DD:2C:16:B0:A1:15:7B:9F:E9:D5:7C
+ "agent-node2.localdomain" (SHA256) 7F:18:02:1F:7B:AB:F6:15:41:1C:C5:5A:ED:9A:40:16:22:55:AA:13:FF:A1:F0:4A:80:E9:AC:0B:3D:6D:88:5F
+ "agent-node3.localdomain" (SHA256) 35:B6:F8:D0:2A:CC:FD:2A:66:A1:43:D9:CA:4A:C9:CC:12:42:1E:5A:04:2C:4F:1B:C3:CC:49:1A:AB:C5:19:14
+ "master-node.localdomain" (SHA256) D4:A4:44:54:FA:2B:A0:A2:53:CD:DA:FE:B7:85:F0:26:49:24:2A:06:E1:89:B1:41:5B:04:97:4D:76:07:AD:34 (alt names: "DNS:Master-node.localdomain", "DNS:master-node.localdomain", "DNS:puppet", "DNS:puppet.localdomain")
6)然后把Master端预先生成的证书copy到agent端的各个节点上[root@Agent-node1 ~]# mkdir -p /var/lib/puppet/ssl/private_keys[root@Agent-node1 ~]# mkdir -p /var/lib/puppet/ssl/certs[root@Agent-node1 ~]# rsync -e "ssh -p22" -avpgolr 182.48.115.233:/var/lib/puppet/ssl/private_keys/agent-node1.pem /var/lib/puppet/ssl/private_keys/[root@Agent-node1 ~]# rsync -e "ssh -p22" -avpgolr 182.48.115.233:/var/lib/puppet/ssl/certs/agent-node1.pem /var/lib/puppet/ssl/certs/[root@Agent-node1 ~]# rsync -e "ssh -p22" -avpgolr 182.48.115.233:/var/lib/puppet/ssl/certs/ca.pem /var/lib/puppet/ssl/certs/ [root@Agent-node2 ~]# mkdir -p /var/lib/puppet/ssl/private_keys[root@Agent-node2 ~]# mkdir -p /var/lib/puppet/ssl/certs[root@Agent-node2 ~]# rsync -e "ssh -p22" -avpgolr 182.48.115.233:/var/lib/puppet/ssl/private_keys/agent-node2.pem /var/lib/puppet/ssl/private_keys/[root@Agent-node2 ~]# rsync -e "ssh -p22" -avpgolr 182.48.115.233:/var/lib/puppet/ssl/certs/agent-node2.pem /var/lib/puppet/ssl/certs/[root@Agent-node2 ~]# rsync -e "ssh -p22" -avpgolr 182.48.115.233:/var/lib/puppet/ssl/certs/ca.pem /var/lib/puppet/ssl/certs/ [root@Agent-node3 ~]# mkdir -p /var/lib/puppet/ssl/private_keys[root@Agent-node3 ~]# mkdir -p /var/lib/puppet/ssl/certs[root@Agent-node3 ~]# rsync -e "ssh -p22" -avpgolr 182.48.115.233:/var/lib/puppet/ssl/private_keys/agent-node3.pem /var/lib/puppet/ssl/private_keys/[root@Agent-node3 ~]# rsync -e "ssh -p22" -avpgolr 182.48.115.233:/var/lib/puppet/ssl/certs/agent-node3.pem /var/lib/puppet/ssl/certs/[root@Agent-node3 ~]# rsync -e "ssh -p22" -avpgolr 182.48.115.233:/var/lib/puppet/ssl/certs/ca.pem /var/lib/puppet/ssl/certs/ 最后在各个Agent节点测试[root@Agent-node1 ~]# puppet agent -tInfo: Caching certificate_revocation_list for caInfo: Retrieving pluginfactsInfo: Retrieving pluginInfo: Caching catalog for agent-node1Info: Applying configuration version '1495896021'Info: Creating state file /var/lib/puppet/state/state.yamlNotice: Finished catalog run in 0.07 seconds在Master端查看证书情况[root@Master-node ~]# tree /var/lib/puppet/ssl/ /var/lib/puppet/ssl/├── ca│ ├── ca_crl.pem│ ├── ca_crt.pem│ ├── ca_key.pem│ ├── ca_pub.pem│ ├── inventory.txt│ ├── private│ │ └── ca.pass│ ├── requests│ ├── serial│ └── signed│ ├── agent-node1.pem│ ├── agent-node2.pem│ ├── agent-node3.pem│ └── master-node.pem├── certificate_requests├── certs│ ├── agent-node1.pem│ ├── agent-node2.pem│ ├── agent-node3.pem│ ├── ca.pem│ └── master-node.pem├── crl.pem├── private├── private_keys│ ├── agent-node1.pem│ ├── agent-node2.pem│ ├── agent-node3.pem│ └── master-node.pem└── public_keys ├── agent-node1.pem ├── agent-node2.pem ├── agent-node3.pem └── master-node.pem