示例场景
当我们把系统的业务应用部署到容器中时候,由于主机的网络和容器网络相互影响。就会碰到一些异常问题.
主机的防火墙规则会影响到容器服务之间的相互调用
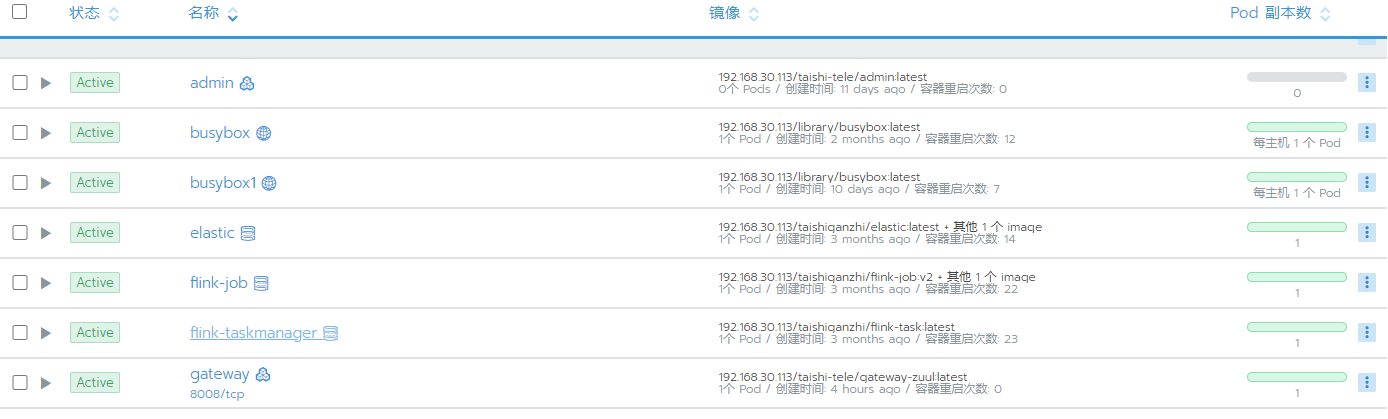
当容器服务之间是出现网络调用问题的时候首先停掉防火墙 重启服务看是否能正常运行。如果停掉防火墙服务正常则证明是防火墙问题
问题场景
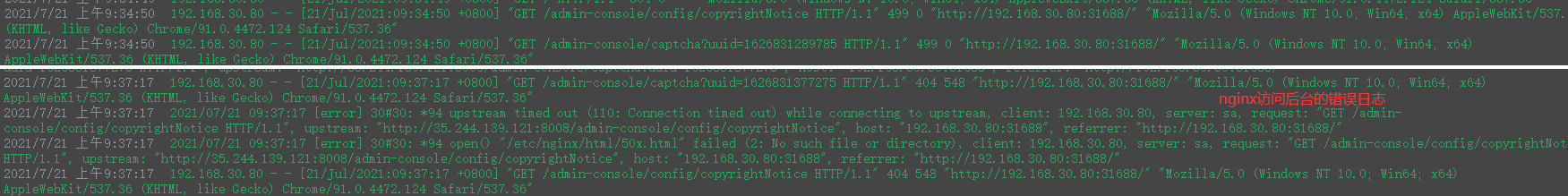
docker Nginx 反向代理宿主机服务 connect() failed (113: No route to host) while connecting to upstream
解决方案
设置主机上的防火墙白名单
1.按网卡名称单个添加白名单

set_firewall_cmd () { string='|%-3s|%-18s|%-10s|%-10s|%-10s|%-16s|%-16s|%-16s|'; br="`echo $string|grep -Eo '[0-9]+'|awk '{s=s+$1}END{s=s+NR;for(i=0;i<=s;i++){printf "-"};print""}';`"; for i in `ip a|awk -F ':' '/^[0-9]/{print $2}'|sort`; do DEVICE_DESC=$i; DEVICE=${DEVICE_DESC%@*}; STATUS=`ip a|grep ":.$DEVICE:"|awk '{print /LOWER_UP/?"UP":"DOWN"}'`; TYPE=` ethtool $DEVICE |grep 'Supported ports' |sed 's/]//g' |awk -F '[' '{print $2}'|sed 's/ //g'`; SPEED=` ethtool $DEVICE |awk '/Speed/{print $NF}'`; IPADDR=`ifconfig $DEVICE |grep -Eo '([0-9]+.){3}[0-9]{1,3}'|awk 'NR==1'`; MASK=` ifconfig $DEVICE |grep -Eo '([0-9]+.){3}[0-9]{1,3}'|awk '/^255/'`; BCAST=` ifconfig $DEVICE |grep -Eo '([0-9]+.){3}[0-9]{1,3}'|awk 'NR>1&&!/^255/'`; [ "x"$STATUS == "x" ] && STATUS='-'; [ "x"$TYPE == "x" ] && TYPE='-'; [ "x"$SPEED == "x" ] && SPEED='-'; [ "x"$IPADDR == "x" ] && IPADDR='-'; [ "x"$BCAST == "x" ] && BCAST='-'; [ "x"$MASK == "x" ] && MASK='-'; if [[ $ip_addr = $IPADDR ]]; then echo "public" $DEVICE; echo $br; else echo "trusted" $DEVICE; echo $br; firewall-cmd --zone=trusted --add-interface=$DEVICE fi done; } remove_firewall_cmd () { a=`firewall-cmd --zone=trusted --list-interfaces` OLD_IFS="$IFS" IFS=" " arr=($a) IFS="$OLD_IFS" for s in ${arr[@]} do echo "remove-interface:$s" firewall-cmd --zone=trusted --remove-interface=$s done } remove_firewall_cmd set_firewall_cmd firewall-cmd --zone=public --list-all firewall-cmd --zone=trusted --list-all
按照虚拟网卡添加的话,每次重启容器的时候就需要重新执行一次添加白名单指令。比较麻烦
2.按虚拟网段添加白名单
每次重启docker容器 虽然网卡名称会变,但是容器所处的网段并不会随便发生变化
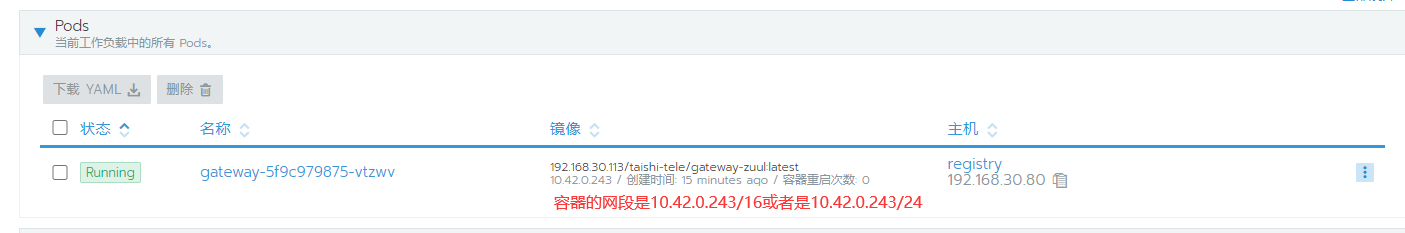
1.查询容器所在的网段
2.在宿主机上执行添加白名单
firewall-cmd --zone=trusted --add-source=10.42.0.0/16
firewall-cmd --zone=trusted --add-source=10.42.0.0/24
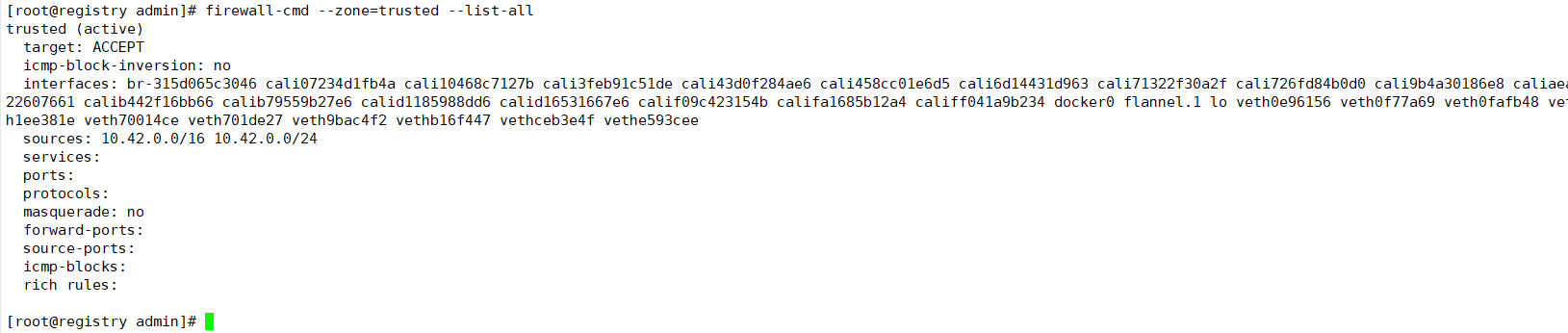
用网段的方式添加了白名单,即使容器服务重启。容器之间的网络调用也能继续正常进行。无需重新执行添加白名单命令
3.firewall-cmd设置白名单示例
1.使mysql服务的3306端口只允许192.168.1.1/24网段的服务器能访问
#添加规则
firewall-cmd --permanent --add-rich-rule="rule family="ipv4" source address="192.168.1.1/24" port protocol="tcp" port="3306" accept"
#reload使生效
firewall-cmd --reload
2.IP 列表逐一加入 trusted 区域,使用命令如下:
$ firewall-cmd --permanent --zone=trusted --add-source=173.245.48.0/20
$ firewall-cmd --permanent --zone=trusted --add-source=131.0.72.0/22
使 trusted 区域设置生效,使用命令如下:
$ firewall-cmd --reload
前后台微服务调用异常
当对后台的服务进行打包发版后,前台服务pod由于应用缓存问题导致调用后端pod接口出现异常。需要手动重启前端Pod,操作比较麻烦
/usr/local/sbin/kubectl --kubeconfig /home/aa/kubectl/k8s-cluster/80-cluster/kube_config.yml replace -f /home/aa/kubectl/k8s-cluster/80-cluster/main.yml --force
deployment.apps "main" deleted
deployment.apps/main replaced
1.后端发版操作
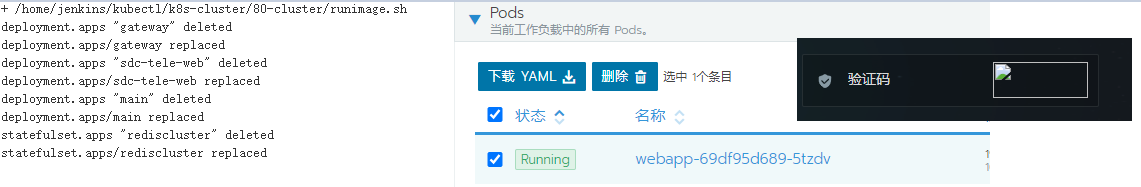
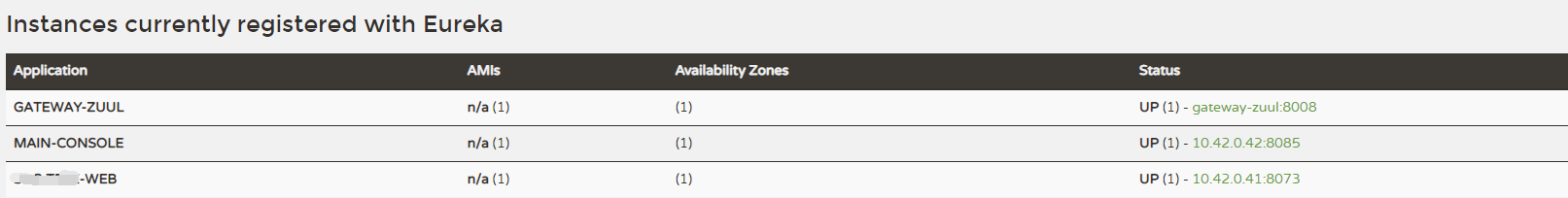
2.后端微服务发版后没有更新注册中心,导致注册中心的数据还是缓存的发版前的服务数据。前端调用后端服务接口就会出现异常
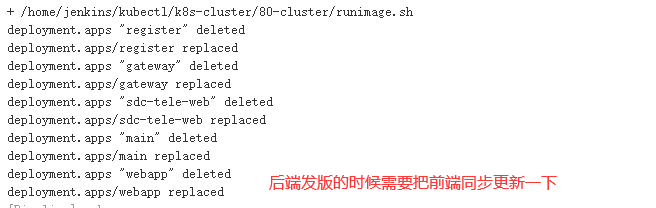
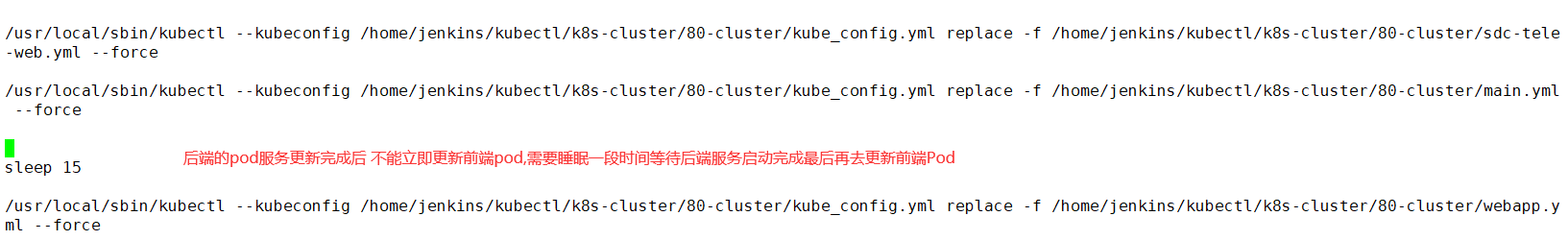

#!/bin/bash /usr/local/sbin/kubectl --kubeconfig /home/jenkins/kubectl/k8s-cluster/80-cluster/kube_config.yml replace -f /home/jenkins/kubectl/k8s-cluster/80-cluster/register.yml --force /usr/local/sbin/kubectl --kubeconfig /home/jenkins/kubectl/k8s-cluster/80-cluster/kube_config.yml replace -f /home/jenkins/kubectl/k8s-cluster/80-cluster/gateway.yml --force /usr/local/sbin/kubectl --kubeconfig /home/jenkins/kubectl/k8s-cluster/80-cluster/kube_config.yml replace -f /home/jenkins/kubectl/k8s-cluster/80-cluster/sdc-tele-web.yml --force /usr/local/sbin/kubectl --kubeconfig /home/jenkins/kubectl/k8s-cluster/80-cluster/kube_config.yml replace -f /home/jenkins/kubectl/k8s-cluster/80-cluster/main.yml --force sleep 15 /usr/local/sbin/kubectl --kubeconfig /home/jenkins/kubectl/k8s-cluster/80-cluster/kube_config.yml replace -f /home/jenkins/kubectl/k8s-cluster/80-cluster/webapp.yml --force
