Habor是由VMWare公司开源的容器镜像仓库。事实上,Habor是在Docker Registry上进行了相应的企业级扩展,从而获得了更加广泛的应用,这些新的企业级特性包括:管理用户界面,基于角色的访问控制,AD/LDAP集成以及审计日志等,足以满足基本企业需求。
官方地址:https://vmware.github.io/harbor/cn/
harbor部署:
安装docker
#安装依赖包
yum install -y yum-utils device-mapper-persistent-data lvm2 #设置yum源 yum-config-manager --add-repo https://download.docker.com/linux/centos/docker-ce.repo #更新yum缓存 yum makecache fast #安装docker-ce yum -y install docker-ce #启动docker后台服务 systemctl start docker systemctl enable docker
#配置镜像加速
curl -sSL https://get.daocloud.io/daotools/set_mirror.sh | sh -s http://f1361db2.m.daocloud.io
systemctl daemon-reload
systemctl restart docker
安装docker-compose
[root@localhost ~]# sudo curl -L "https://github.com/docker/compose/releases/download/1.23.1/docker-compose-$(uname -s)-$(uname -m)" -o /usr/local/bin/docker-compose [root@localhost ~]# chmod +x /usr/local/bin/docker-compose [root@localhost ~]# docker-compose --version docker-compose version 1.23.1, build b02f1306
安装harbor
#下载安装包 [root@localhost ~]# wget https://storage.googleapis.com/harbor-releases/release-1.6.0/harbor-offline-installer-v1.6.2.tgz [root@localhost ~]# tar xf harbor-offline-installer-v1.6.2.tgz [root@localhost ~]# cd harbor #使用https访问harbor配置 #获得证书授权 [root@localhost harbor]# mkdir ssl && cd ssl [root@localhost ssl]# openssl genrsa -out ca.key 4096 [root@localhost ssl]# openssl req -x509 -new -nodes -sha512 -days 3650 -subj "/C=TW/ST=Taipei/L=Taipei/O=example/OU=Personal/CN=reg.hb.com" -key ca.key -out ca.crt #创建自己的私钥 [root@localhost ssl]# openssl genrsa -out reg.hb.com.key 4096 #生成证书签名请求 [root@localhost ssl]# openssl req -sha512 -new -subj "/C=TW/ST=Taipei/L=Taipei/O=example/OU=Personal/CN=reg.hb.com" -key reg.hb.com.key -out reg.hb.com.csr #生成注册表主机证书 [root@localhost ssl]# vim v3.ext authorityKeyIdentifier=keyid,issuer basicConstraints=CA:FALSE keyUsage = digitalSignature, nonRepudiation, keyEncipherment, dataEncipherment extendedKeyUsage = serverAuth subjectAltName = @alt_names [alt_names] DNS.1=reg.hb.com DNS.2=reg.hb DNS.3=hostname [root@localhost ssl]# openssl x509 -req -sha512 -days 3650 -extfile v3.ext -CA ca.crt -CAkey ca.key -CAcreateserial -in reg.hb.com.csr -out reg.hb.com.crt #配置服务器证书和密钥 [root@localhost ssl]# mkdir /data/cert/ [root@localhost ssl]# cp reg.hb.com.crt /data/cert/ [root@localhost ssl]# cp reg.hb.com.key /data/cert/ #为docker配置证书密钥和CA [root@localhost ssl]# mkdir -p /etc/docker/certs.d/reg.hb.com [root@localhost ssl]# cp reg.hb.com.cert /etc/docker/certs.d/reg.hb.com/ [root@localhost ssl]# cp reg.hb.com.key /etc/docker/certs.d/reg.hb.com/ #配置harbor [root@localhost harbor]# vim harbor.cfg hostname = reg.hb.com ui_url_protocol = https ssl_cert = /data/cert/reg.hb.com.crt ssl_cert_key = /data/cert/reg.hb.com.key #生成harbor配置文件 [root@localhost harbor]# ./prepare #开始安装 [root@localhost harbor]# ./install.sh
查看harbor状态
[root@localhost harbor]# docker-compose ps Name Command State Ports ------------------------------------------------------------------------------------------------------------------------------------- harbor-adminserver /harbor/start.sh Up (healthy) harbor-db /entrypoint.sh postgres Up (healthy) 5432/tcp harbor-jobservice /harbor/start.sh Up harbor-log /bin/sh -c /usr/local/bin/ ... Up (healthy) 127.0.0.1:1514->10514/tcp harbor-ui /harbor/start.sh Up (healthy) nginx nginx -g daemon off; Up (healthy) 0.0.0.0:443->443/tcp, 0.0.0.0:4443->4443/tcp, 0.0.0.0:80->80/tcp redis docker-entrypoint.sh redis ... Up 6379/tcp registry /entrypoint.sh /etc/regist ... Up (healthy) 5000/tcp 组件 功能 harbor-adminserver 配置管理中心 harbor-db Mysql数据库 harbor-jobservice 负责镜像复制 harbor-log 记录操作日志 harbor-ui Web管理页面和API nginx 前端代理,负责前端页面和镜像上传/下载转发 redis 会话 registry 镜像存储
访问harbor

新建项目
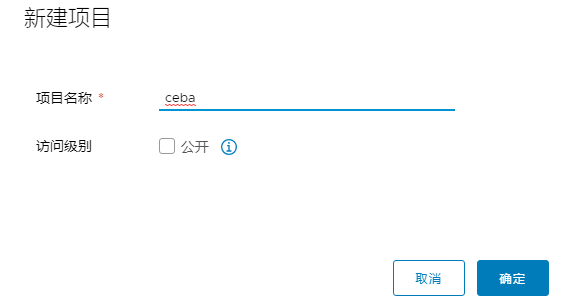
新建用户

项目中添加成员
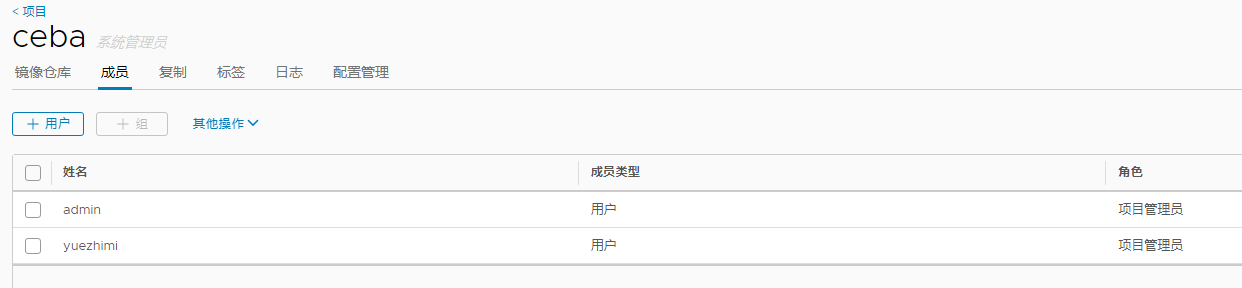
docker登陆harbor仓库
[root@localhost harbor]# docker login reg.hb.com Username: yuezhimi Password: WARNING! Your password will be stored unencrypted in /root/.docker/config.json. Configure a credential helper to remove this warning. See https://docs.docker.com/engine/reference/commandline/login/#credentials-store Login Succeeded
上传镜像
[root@localhost ~]# docker tag nginx:v1 reg.hb.com/ceba/nginx:v1 [root@localhost ~]# docker push reg.hb.com/ceba/nginx:v1 The push refers to repository [reg.hb.com/ceba/nginx] dee7742caaad: Pushed d042a4fec9fc: Pushed f972d139738d: Pushed v1: digest: sha256:ffa77a4671b33f668ecad1ef74dac4236f9a03d270d9f6f21c3fbede8af4d0c4 size: 952
查看仓库
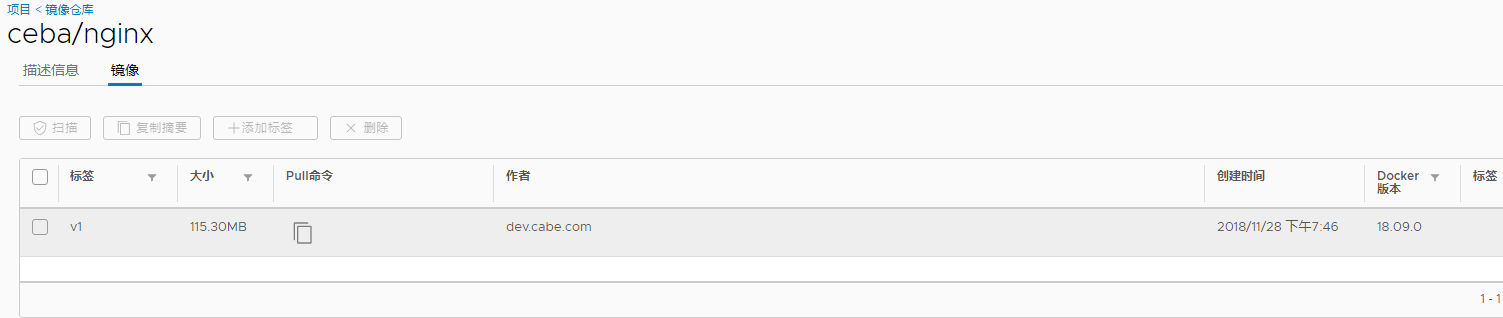
管理命令
docker-compose stop docker-compose start docker-compose down -v docker-compose up -d