使用IDA可以帮助我们模仿别人的功能如何实现,这对开发新的软件有很好的作用。
使用IDA也可以帮助我们验证我们的猜测是否是否确的。
1、在开发Gina中想知道VWare使用的认证凭据中怎么把Ctrl-Alt-Del界面去掉的,猜测是使用了SAS.dll中的接口。为了验证我们使用IDA工具来查看。
步一:
步二:
步三:
步四:
2、查看VWare中对于会话改变时是如何实现的,他们是采用对会话进行监控的方式。
二、分析CTXGina
真实的代码:
BOOL APIENTRY DllMain(HINSTANCE hModule, DWORD ul_reason_for_call, LPVOID lpReserved )
{
switch (ul_reason_for_call)
{
case DLL_PROCESS_ATTACH:
{
DisableThreadLibraryCalls((HMODULE)hModule);
L_INFO(L"====>XRedGina.dll DLL_PROCESS_ATTACH, CurrentProcessId = %d
", GetCurrentProcessId());
if ( FALSE == g_CXRedGinaApp.LoadMsginaDll())
{
L_FATAL(L"LoadMsginaDll failed(%d)
", GetLastError());
}
L_INFO(L"<====XRedGina.dll DLL_PROCESS_ATTACH
");
break;
}
case DLL_THREAD_ATTACH:
break;
case DLL_THREAD_DETACH:
break;
case DLL_PROCESS_DETACH:
{
L_DEBUG(L"=======>!!!XRedGina.dll DLL_PROCESS_DETACH, CurrentProcessId = %d
", GetCurrentProcessId());
g_CXRedGinaApp.ExitInstance();
L_DEBUG(L"<======!!!!XRedGina.dll DLL_PROCESS_DETACH
");
break;
}
}
return TRUE;
}
步一、分析DllMain
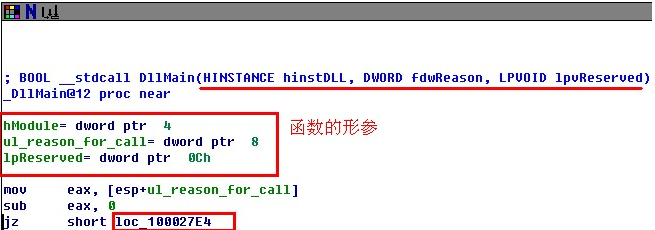
步二、代码中的case体现在IDA中是什么

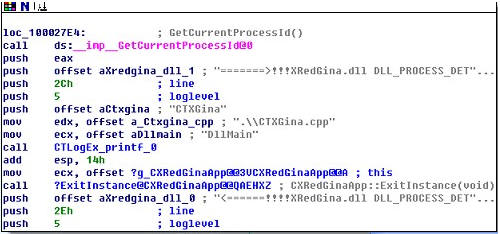
步三、分析case DLL_PROCESS_ATTACH时
步四、分析case DLL_PROCESS_DETACH时
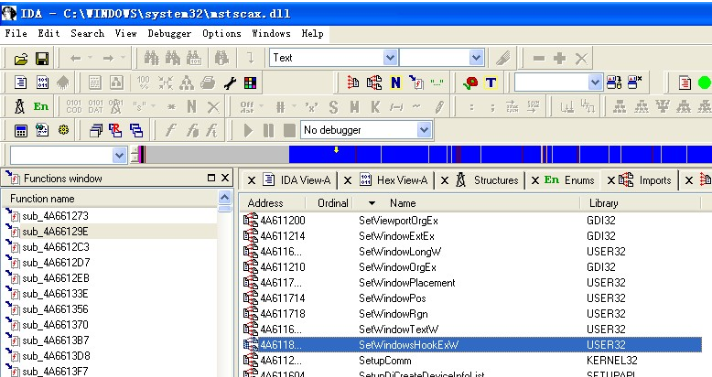
三、分析mstsc.exe,判断它是不是调用了键盘钩子。
我们一般关心在此mstsc.exe中究竟使用了Windows的哪些API,那么我们就应该看Imports项目。
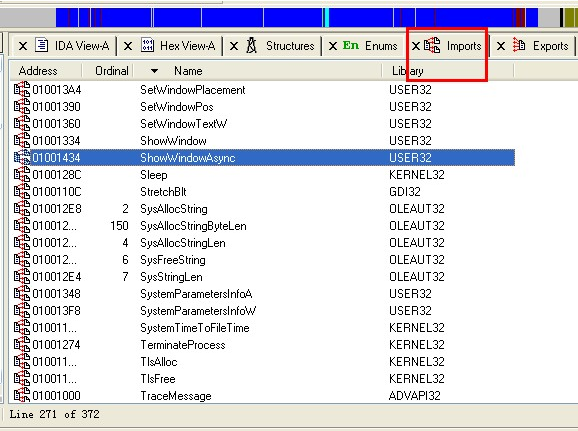
这样看到了RDP客户端调用了以下API:
0100153C ??_U@YAPAXI@Z msvcrt
010015C8 ??_V@YAXPAX@Z msvcrt
01001574 ?terminate@@YAXXZ msvcrt
01001368 AdjustWindowRect USER32
0100142C AdjustWindowRectEx USER32
010013A0 AppendMenuW USER32
010013E0 BeginPaint USER32
010010EC BitBlt GDI32
010010C8 CertCloseStore CRYPT32
010010A8 CertDuplicateCertificateChain CRYPT32
010010A4 CertDuplicateCertificateContext CRYPT32
010010D4 CertFindExtension CRYPT32
01001098 CertFreeCertificateChain CRYPT32
01001094 CertFreeCertificateContext CRYPT32
010010D8 CertGetCertificateChain CRYPT32
010010AC CertGetCertificateContextProperty CRYPT32
010010DC CertGetEnhancedKeyUsage CRYPT32
010010B8 CertOpenStore CRYPT32
010010B0 CertVerifyCertificateChainPolicy CRYPT32
0100147C CheckDlgButton USER32
010012A0 CloseHandle KERNEL32
01001600 CoCreateInstance ole32
01001610 CoInitialize ole32
0100160C CoTaskMemAlloc ole32
01001608 CoTaskMemFree ole32
01001604 CoUninitialize ole32
01001150 CombineRgn GDI32
010012B0 CompareStringW KERNEL32
01001374 CopyRect USER32
01001110 CreateCompatibleBitmap GDI32
010010F4 CreateCompatibleDC GDI32
01001488 CreateDialogIndirectParamW USER32
010013EC CreateDialogParamW USER32
01001168 CreateDirectoryW KERNEL32
010011B8 CreateEventW KERNEL32
01001174 CreateFileMappingW KERNEL32
0100129C CreateFileW KERNEL32
010010F8 CreateFontIndirectW GDI32
0100137C CreateMenu USER32
01001290 CreateMutexW KERNEL32
01001130 CreatePalette GDI32
0100118C CreateProcessW KERNEL32
01001138 CreateRectRgn GDI32
0100113C CreateRectRgnIndirect GDI32
010011BC CreateThread KERNEL32
010013D8 CreateWindowExW USER32
01001040 CredDeleteW ADVAPI32
01001044 CredFree ADVAPI32
01001048 CredReadDomainCredentialsW ADVAPI32
01001038 CredReadW ADVAPI32
010014D4 CredUIParseUserNameW credui
010014D0 CredUIPromptForCredentialsW credui
01001058 CredUnmarshalCredentialW ADVAPI32
0100104C CredWriteDomainCredentialsW ADVAPI32
01001034 CredWriteW ADVAPI32
0100109C CryptBinaryToStringW CRYPT32
010010D0 CryptDecodeObject CRYPT32
010010B4 CryptMsgClose CRYPT32
010010C0 CryptMsgOpenToDecode CRYPT32
010010BC CryptMsgUpdate CRYPT32
010010C4 CryptSignMessage CRYPT32
010010A0 CryptStringToBinaryW CRYPT32
010010E4 CryptUIDlgViewCertificateW CRYPTUI
010010CC CryptVerifyDetachedMessageSignature CRYPT32
0100126C DebugBreak KERNEL32
01001400 DefDlgProcW USER32
010013D0 DefWindowProcW USER32
0100120C DeleteCriticalSection KERNEL32
01001118 DeleteDC GDI32
01001294 DeleteFileW KERNEL32
01001140 DeleteObject GDI32
01001448 DestroyIcon USER32
010013CC DestroyWindow USER32
01001220 DeviceIoControl KERNEL32
010013E8 DialogBoxParamW USER32
01001458 DispatchMessageW USER32
01001498 DrawIcon USER32
01001468 DrawIconEx USER32
0100146C DrawTextW USER32
01001364 EnableMenuItem USER32
01001370 EnableWindow USER32
010014A0 EndDialog USER32
0100149C EndPaint USER32
0100121C EnterCriticalSection KERNEL32
01001378 EqualRect USER32
01001128 EqualRgn GDI32
01001204 ExpandEnvironmentStringsA KERNEL32
01001188 ExpandEnvironmentStringsW KERNEL32
01001304 ExtractIconW SHELL32
01001478 FillRect USER32
010011A4 FindClose KERNEL32
0100119C FindFirstFileW KERNEL32
010011A0 FindNextFileW KERNEL32
0100116C FindResourceExW KERNEL32
010011E0 FindResourceW KERNEL32
01001340 FindWindowW USER32
01001164 FormatMessageW KERNEL32
01001328 FreeContextBuffer Secur32
01001258 FreeLibrary KERNEL32
010011B4 GetACP KERNEL32
010013AC GetClassInfoExW USER32
010013FC GetClassInfoW USER32
0100138C GetClientRect USER32
0100114C GetClipBox GDI32
01001190 GetCommandLineW KERNEL32
010012BC GetCurrentDirectoryW KERNEL32
01001270 GetCurrentProcess KERNEL32
01001238 GetCurrentProcessId KERNEL32
0100123C GetCurrentThreadId KERNEL32
0100145C GetCursorPos USER32
010014A8 GetDC USER32
01001148 GetDCOrgEx GDI32
01001134 GetDIBColorTable GDI32
01001430 GetDesktopWindow USER32
01001120 GetDeviceCaps GDI32
01001428 GetDlgItem USER32
0100148C GetDlgItemTextW USER32
01001198 GetFileAttributesExW KERNEL32
010012AC GetFileAttributesW KERNEL32
01001160 GetFileSize KERNEL32
0100108C GetFileTitleW COMDLG32
010012A8 GetFullPathNameW KERNEL32
010012A4 GetLastError KERNEL32
0100117C GetLocaleInfoW KERNEL32
01001438 GetMenu USER32
01001450 GetMessageW USER32
0100122C GetModuleFileNameW KERNEL32
01001248 GetModuleHandleA KERNEL32
01001298 GetModuleHandleW KERNEL32
0100140C GetMonitorInfoW USER32
01001114 GetObjectW GDI32
01001088 GetOpenFileNameW COMDLG32
01001280 GetProcAddress KERNEL32
01001210 GetProcessHeap KERNEL32
01001084 GetSaveFileNameW COMDLG32
01001278 GetStartupInfoA KERNEL32
01001154 GetStockObject GDI32
010011C8 GetSystemDefaultUILanguage KERNEL32
01001384 GetSystemMenu USER32
010013BC GetSystemMetrics USER32
010011F8 GetSystemTime KERNEL32
01001234 GetSystemTimeAsFileTime KERNEL32
010011A8 GetTempPathW KERNEL32
01001240 GetTickCount KERNEL32
0100101C GetTraceEnableFlags ADVAPI32
01001020 GetTraceEnableLevel ADVAPI32
01001024 GetTraceLoggerHandle ADVAPI32
010011CC GetUserDefaultUILanguage KERNEL32
0100103C GetUserNameA ADVAPI32
0100132C GetUserNameExW Secur32
010011B0 GetVersion KERNEL32
01001284 GetVersionExA KERNEL32
010012C0 GetVersionExW KERNEL32
01001474 GetWindow USER32
01001464 GetWindowDC USER32
010013D4 GetWindowLongW USER32
0100133C GetWindowPlacement USER32
010013B4 GetWindowRect USER32
01001208 HeapAlloc KERNEL32
01001214 HeapFree KERNEL32
01001184 HeapSetInformation KERNEL32
01001078 ImageList_Create COMCTL32
01001070 ImageList_GetImageCount COMCTL32
0100106C ImageList_ReplaceIcon COMCTL32
0100107C 17 InitCommonControls COMCTL32
01001074 InitCommonControlsEx COMCTL32
010011DC InitializeCriticalSection KERNEL32
01001178 InterlockedCompareExchange KERNEL32
010011C4 InterlockedDecrement KERNEL32
01001254 InterlockedExchange KERNEL32
01001260 InterlockedIncrement KERNEL32
0100136C IntersectRect USER32
0100141C InvalidateRect USER32
010013C4 IsChild USER32
0100134C IsDialogMessageW USER32
01001480 IsDlgButtonChecked USER32
01001338 IsIconic USER32
01001358 IsWindow USER32
01001440 IsWindowEnabled USER32
01001424 IsWindowVisible USER32
01001394 IsZoomed USER32
010013F0 KillTimer USER32
01001218 LeaveCriticalSection KERNEL32
010013E4 LoadAcceleratorsW USER32
01001398 LoadCursorW USER32
010013B8 LoadIconW USER32
0100144C LoadImageW USER32
01001200 LoadLibraryA KERNEL32
01001228 LoadLibraryExW KERNEL32
0100125C LoadLibraryW KERNEL32
010011E4 LoadResource KERNEL32
01001410 LoadStringW USER32
010012B4 LocalAlloc KERNEL32
010012B8 LocalFree KERNEL32
010011E8 LockResource KERNEL32
01001420 LockWindowUpdate USER32
01001470 MapDialogRect USER32
01001170 MapViewOfFile KERNEL32
01001490 MapWindowPoints USER32
01001380 ModifyMenuW USER32
01001408 MonitorFromWindow USER32
01001388 MoveWindow USER32
01001268 MulDiv KERNEL32
0100127C MultiByteToWideChar KERNEL32
010012CC NetApiBufferFree NETAPI32
010012C8 NetGetJoinInformation NETAPI32
010015EC NtOpenFile ntdll
010013B0 OffsetRect USER32
01001250 OutputDebugStringA KERNEL32
01001318 PathAppendW SHLWAPI
01001314 PathFindExtensionW SHLWAPI
0100130C PathFindFileNameW SHLWAPI
01001310 PathRemoveFileSpecW SHLWAPI
01001354 PostMessageW USER32
010013C8 PostQuitMessage USER32
01001244 QueryPerformanceCounter KERNEL32
01001324 QuerySecurityPackageInfoW Secur32
0100115C ReadFile KERNEL32
01001124 RealizePalette GDI32
0100143C RedrawWindow USER32
01001004 RegCloseKey ADVAPI32
01001064 RegCreateKeyExA ADVAPI32
01001060 RegCreateKeyExW ADVAPI32
01001010 RegDeleteValueW ADVAPI32
01001018 RegEnumKeyExW ADVAPI32
01001014 RegEnumValueW ADVAPI32
01001054 RegOpenKeyExA ADVAPI32
01001008 RegOpenKeyExW ADVAPI32
01001050 RegQueryValueExA ADVAPI32
0100100C RegQueryValueExW ADVAPI32
01001030 RegSetValueExA ADVAPI32
0100105C RegSetValueExW ADVAPI32
010013DC RegisterClassExW USER32
01001404 RegisterClassW USER32
01001028 RegisterTraceGuidsW ADVAPI32
01001494 ReleaseDC USER32
010015F0 RtlInitUnicodeString ntdll
010015E8 RtlInitializeCriticalSection ntdll
010015F8 RtlUnwind ntdll
01001300 SHGetDesktopFolder SHELL32
010012F4 SHGetMalloc SHELL32
010012F8 SHGetPathFromIDListW SHELL32
010012FC SHGetSpecialFolderLocation SHELL32
0100131C 388 SHLWAPI_388 SHLWAPI
01001460 ScreenToClient USER32
010011D8 SearchPathW KERNEL32
010010F0 SelectObject GDI32
0100112C SelectPalette GDI32
01001484 SendDlgItemMessageW USER32
01001344 SendMessageTimeoutW USER32
0100135C SendMessageW USER32
01001104 SetBkMode GDI32
0100139C SetCursor USER32
010014A4 SetDlgItemTextW USER32
010011C0 SetEvent KERNEL32
010011AC SetFilePointer KERNEL32
01001414 SetFocus USER32
01001350 SetForegroundWindow USER32
01001288 SetLastError KERNEL32
01001100 SetMapMode GDI32
01001444 SetRect USER32
01001144 SetRectRgn GDI32
01001108 SetTextColor GDI32
010013F4 SetTimer USER32
0100124C SetUnhandledExceptionFilter KERNEL32
010014AC SetWindowLongW USER32
010013A4 SetWindowPlacement USER32
01001390 SetWindowPos USER32
01001360 SetWindowTextW USER32
01001334 ShowWindow USER32
01001434 ShowWindowAsync USER32
0100128C Sleep KERNEL32
0100110C StretchBlt GDI32
010012E8 2 SysAllocString OLEAUT32
010012D8 150 SysAllocStringByteLen OLEAUT32
010012D4 4 SysAllocStringLen OLEAUT32
010012EC 6 SysFreeString OLEAUT32
010012E4 7 SysStringLen OLEAUT32
01001348 SystemParametersInfoA USER32
010013F8 SystemParametersInfoW USER32
010011EC SystemTimeToFileTime KERNEL32
01001274 TerminateProcess KERNEL32
010011D4 TlsAlloc KERNEL32
010011D0 TlsFree KERNEL32
01001000 TraceMessage ADVAPI32
010013C0 TranslateAcceleratorW USER32
010010FC TranslateCharsetInfo GDI32
01001454 TranslateMessage USER32
01001230 UnhandledExceptionFilter KERNEL32
01001180 UnmapViewOfFile KERNEL32
010013A8 UnregisterClassW USER32
0100102C UnregisterTraceGuids ADVAPI32
0100111C UpdateColors GDI32
01001418 UpdateWindow USER32
010012E0 9 VariantClear OLEAUT32
010012DC 8 VariantInit OLEAUT32
010015F4 VerSetConditionMask ntdll
01001224 VerifyVersionInfoW KERNEL32
010011FC WaitForSingleObject KERNEL32
01001194 WideCharToMultiByte KERNEL32
010014B4 WinHttpCloseHandle WINHTTP
010014BC WinHttpConnect WINHTTP
010014B8 WinHttpOpen WINHTTP
010014C0 WinHttpOpenRequest WINHTTP
010014C8 WinHttpQueryOption WINHTTP
010014C4 WinHttpSendRequest WINHTTP
010011F0 WriteFile KERNEL32
010014F0 _XcptFilter msvcrt
01001594 __badioinfo msvcrt
01001568 __dllonexit msvcrt
010014E4 __getmainargs msvcrt
010015D8 __mb_cur_max msvcrt
01001558 __p__commode msvcrt
0100155C __p__fmode msvcrt
01001590 __pioinfo msvcrt
01001560 __set_app_type msvcrt
0100152C __setusermatherr msvcrt
01001520 _acmdln msvcrt
01001530 _adjust_fdiv msvcrt
01001528 _amsg_exit msvcrt
010014E8 _cexit msvcrt
01001578 _controlfp msvcrt
010014DC _errno msvcrt
010014EC _exit msvcrt
01001588 _fileno msvcrt
01001524 _initterm msvcrt
010014F4 _ismbblead msvcrt
0100156C _lock msvcrt
01001570 _onexit msvcrt
010015BC _purecall msvcrt
0100158C _read msvcrt
01001564 _unlock msvcrt
01001550 _vsnprintf msvcrt
010015B0 _vsnwprintf msvcrt
01001540 _wcsicmp msvcrt
010014E0 _wcslwr msvcrt
01001548 _wcsnicmp msvcrt
01001514 _wtoi msvcrt
01001538 _wtol msvcrt
01001580 bsearch msvcrt
0100157C calloc msvcrt
010014F8 exit msvcrt
01001554 free msvcrt
010015A0 isdigit msvcrt
010015D4 isleadbyte msvcrt
010015E0 iswctype msvcrt
01001534 iswdigit msvcrt
0100150C iswspace msvcrt
010015D0 isxdigit msvcrt
010015CC localeconv msvcrt
01001264 lstrcmpiW KERNEL32
010011F4 lstrlenW KERNEL32
010015C0 malloc msvcrt
010015DC mbtowc msvcrt
010015B8 memcpy msvcrt
010015AC memmove msvcrt
010015B4 memset msvcrt
01001598 realloc msvcrt
01001500 srand msvcrt
01001504 time msvcrt
01001510 toupper msvcrt
0100151C towlower msvcrt
0100154C towupper msvcrt
01001584 ungetc msvcrt
01001508 wcschr msvcrt
010015A4 wcsncmp msvcrt
01001518 wcspbrk msvcrt
010014FC wcsrchr msvcrt
010015A8 wcsstr msvcrt
01001544 wcstok msvcrt
0100159C wcstombs msvcrt
010015C4 wctomb msvcrt
看TotalCMD查看Lister,后发现mstsc.exe是一个COM组件:

用process explorer查看,它依赖于mstscax.dll文件C:WINDOWSsystem32下
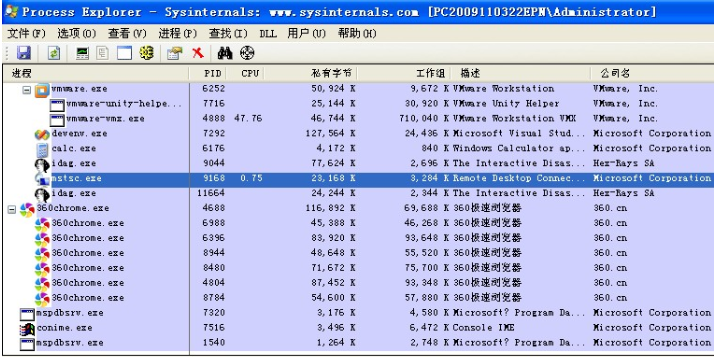
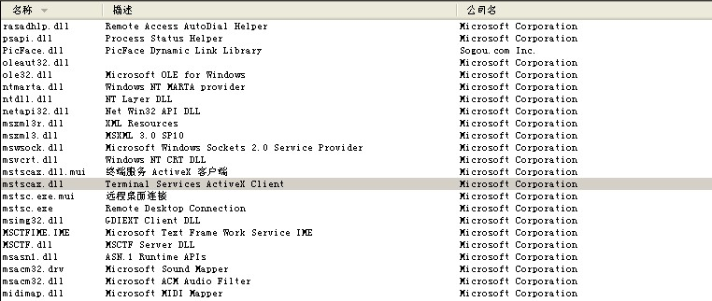
插一句: 在动态库中,我发现了它也调用了一个我们写的一个Hook组件:

所以我们想要知道我们调用的函数被谁HOOK了,可以用Process Explorer来查看。
接下来,我们用IDA来查看mstscax.dll文件,终于找到了SetWindowHook函数。^-^