基于bind软件部署DNS服务器
作者:尹正杰
版权声明:原创作品,谢绝转载!否则将追究法律责任。
一.DNS服务器类型
DNS服务器的类型大致分为三类,即NDS服务器,从DNS服务器和缓存DNS服务器(也可以叫"DNS转发器") 主DNS服务器: 管理和维护所负责解析的域内解析库的服务器。常用的专业数学与如下所示: 序列号: 解析库版本号,主服务器解析库变化时,其序列递增。 刷新时间间隔: 从服务器从主服务器请求同步解析的时间间隔。 重试时间间隔: 从服务器请求同步失败时,再次尝试时间间隔。 过期时长: 主服务器解析库发生变化时,会主动通知从服务器。 从DNS服务器: 从主服务器或从服务器"复制"(区域传输)解析库副本。 通知机制: 主服务器解析库发生变化时,会主动通知从服务器。 区域传输: 完全传输: 传送整个解析库。 增量传输: 传输解析库变化的那部分内容。 Domain(Fully Qualified Domain Name): 正向: FQDN ---> IP 反向: IP ---> FQDN 负责本地域名的正向和反向解析库。 正向区域: 略,前面的笔记已经说过了。 反向区域: 略。 温馨提示: 关于DNS原理的内容我就不在此赘述了,感兴趣的小伙伴可参考我之前的笔记: https://www.cnblogs.com/yinzhengjie/p/14204430.html
二.基于bind开源软件部署DNS服务器
1>.实验前准备(仅需关闭DNS服务器的防火墙即可)

[root@dns53.yinzhengjie.com ~]# cat /etc/redhat-release CentOS Linux release 7.9.2009 (Core) [root@dns53.yinzhengjie.com ~]# [root@dns53.yinzhengjie.com ~]# systemctl status firewalld ● firewalld.service - firewalld - dynamic firewall daemon Loaded: loaded (/usr/lib/systemd/system/firewalld.service; enabled; vendor preset: en abled) Active: active (running) since 四 2020-12-31 19:27:59 CST; 1h 57min ago Docs: man:firewalld(1) Main PID: 592 (firewalld) CGroup: /system.slice/firewalld.service └─592 /usr/bin/python2 -Es /usr/sbin/firewalld --nofork --nopid 12月 31 19:27:58 dns53.yinzhengjie.com systemd[1]: Starting firewalld - dynamic fir.... 12月 31 19:27:59 dns53.yinzhengjie.com systemd[1]: Started firewalld - dynamic fire.... 12月 31 19:27:59 dns53.yinzhengjie.com firewalld[592]: WARNING: AllowZoneDrifting i.... Hint: Some lines were ellipsized, use -l to show in full. [root@dns53.yinzhengjie.com ~]# [root@dns53.yinzhengjie.com ~]# [root@dns53.yinzhengjie.com ~]# systemctl stop firewalld [root@dns53.yinzhengjie.com ~]# [root@dns53.yinzhengjie.com ~]# systemctl disable firewalld Removed symlink /etc/systemd/system/multi-user.target.wants/firewalld.service. Removed symlink /etc/systemd/system/dbus-org.fedoraproject.FirewallD1.service. [root@dns53.yinzhengjie.com ~]# [root@dns53.yinzhengjie.com ~]# systemctl status firewalld ● firewalld.service - firewalld - dynamic firewall daemon Loaded: loaded (/usr/lib/systemd/system/firewalld.service; disabled; vendor preset: e nabled) Active: inactive (dead) Docs: man:firewalld(1) 12月 31 19:27:58 dns53.yinzhengjie.com systemd[1]: Starting firewalld - dynamic fir.... 12月 31 19:27:59 dns53.yinzhengjie.com systemd[1]: Started firewalld - dynamic fire.... 12月 31 19:27:59 dns53.yinzhengjie.com firewalld[592]: WARNING: AllowZoneDrifting i.... 12月 31 21:25:24 dns53.yinzhengjie.com systemd[1]: Stopping firewalld - dynamic fir.... 12月 31 21:25:25 dns53.yinzhengjie.com systemd[1]: Stopped firewalld - dynamic fire.... Hint: Some lines were ellipsized, use -l to show in full. [root@dns53.yinzhengjie.com ~]#
2>.选择bind软件部署DNS服务器
市面上跨平台且开源的DNS服务器软件有很多,比如: smartdns,CoreDNS,godoh,robdns等等,它们各有优势,你可以选择你感兴趣的开源DNS服务软件进行部署。
如下图所示,今天我们部署DNS服务器使用的是CentOS Linux 7.9中yum源自带的DNS服务器软件,即bind软件。

2>.安装DNS服务器
[root@dns53.yinzhengjie.com ~]# yum -y install bind

[root@dns53.yinzhengjie.com ~]# rpm -q --scripts bind preinstall scriptlet (using /bin/sh): if [ "$1" -eq 1 ]; then /usr/sbin/groupadd -g 25 -f -r named >/dev/null 2>&1 || :; /usr/sbin/useradd -u 25 -r -N -M -g named -s /sbin/nologin -d /var/named -c Named named >/dev/null 2>&1 || :; fi; :; postinstall scriptlet (using /bin/sh): /sbin/ldconfig if [ "$1" -eq 1 ]; then # Initial installation [ -x /sbin/restorecon ] && /sbin/restorecon /etc/rndc.* /etc/named.* >/dev/null 2>&1 ; # rndc.key has to have correct perms and ownership, CVE-2007-6283 [ -e /etc/rndc.key ] && chown root:named /etc/rndc.key [ -e /etc/rndc.key ] && chmod 0640 /etc/rndc.key else # Upgrade, use nologin shell again if getent passwd named | grep ':/bin/false$' >/dev/null; then /sbin/usermod -s /sbin/nologin named fi fi . /etc/selinux/config if /usr/sbin/selinuxenabled && [ "${SELINUX}" != "disabled" ] ; then . /etc/selinux/config _policytype=targeted if [ -z "${_policytype}" ]; then _policytype="targeted" fi if [ -d "/etc/selinux/${_policytype}" ]; then LOCAL_MODIFICATIONS=$(/usr/sbin/semanage boolean -E) if [ ! -f /etc/selinux/${_policytype}/rpmbooleans.custom ]; then /bin/echo "# This file is managed by macros.selinux-policy. Do not edit it manually" > /etc/selinux/${_policytype}/rpmbooleans.custom fi semanage_import='' for boolean in named_write_master_zones=1; do boolean_name=${boolean%=*} boolean_value=${boolean#*=} boolean_local_string=$(grep "$boolean_name$" <<<$LOCAL_MODIFICATIONS) if [ -n "$boolean_local_string" ]; then semanage_import="${semanage_import} boolean -m -$boolean_value $boolean_name" boolean_customized_string=$(grep "$boolean_name$" /etc/selinux/${_policytype}/rpmbooleans.custom | tail -n 1) if [ -n "$boolean_customized_string" ]; then /bin/echo $boolean_customized_string >> /etc/selinux/${_policytype}/rpmbooleans.custom else /bin/echo $boolean_local_string >> /etc/selinux/${_policytype}/rpmbooleans.custom fi else semanage_import="${semanage_import} boolean -m -$boolean_value $boolean_name" boolean_default_value=$(LC_ALL=C /usr/sbin/semanage boolean -l | grep "^$boolean_name " | sed 's/[^(]*([^,]*, *(on|off).*/1/') /bin/echo "boolean -m --$boolean_default_value $boolean_name" >> /etc/selinux/${_policytype}/rpmbooleans.custom fi done; if /usr/sbin/selinuxenabled && [ "${SELINUXTYPE}" = "${_policytype}" ]; then /bin/echo -e "$semanage_import" | /usr/sbin/semanage import -S "${_policytype}" elif test -d /usr/share/selinux/"${_policytype}"/base.lst; then /bin/echo -e "$semanage_import" | /usr/sbin/semanage import -S "${_policytype}" -N fi fi . /etc/selinux/config _policytype=mls if [ -z "${_policytype}" ]; then _policytype="targeted" fi if [ -d "/etc/selinux/${_policytype}" ]; then LOCAL_MODIFICATIONS=$(/usr/sbin/semanage boolean -E) if [ ! -f /etc/selinux/${_policytype}/rpmbooleans.custom ]; then /bin/echo "# This file is managed by macros.selinux-policy. Do not edit it manually" > /etc/selinux/${_policytype}/rpmbooleans.custom fi semanage_import='' for boolean in named_write_master_zones=1; do boolean_name=${boolean%=*} boolean_value=${boolean#*=} boolean_local_string=$(grep "$boolean_name$" <<<$LOCAL_MODIFICATIONS) if [ -n "$boolean_local_string" ]; then semanage_import="${semanage_import} boolean -m -$boolean_value $boolean_name" boolean_customized_string=$(grep "$boolean_name$" /etc/selinux/${_policytype}/rpmbooleans.custom | tail -n 1) if [ -n "$boolean_customized_string" ]; then /bin/echo $boolean_customized_string >> /etc/selinux/${_policytype}/rpmbooleans.custom else /bin/echo $boolean_local_string >> /etc/selinux/${_policytype}/rpmbooleans.custom fi else semanage_import="${semanage_import} boolean -m -$boolean_value $boolean_name" boolean_default_value=$(LC_ALL=C /usr/sbin/semanage boolean -l | grep "^$boolean_name " | sed 's/[^(]*([^,]*, *(on|off).*/1/') /bin/echo "boolean -m --$boolean_default_value $boolean_name" >> /etc/selinux/${_policytype}/rpmbooleans.custom fi done; if /usr/sbin/selinuxenabled && [ "${SELINUXTYPE}" = "${_policytype}" ]; then /bin/echo -e "$semanage_import" | /usr/sbin/semanage import -S "${_policytype}" elif test -d /usr/share/selinux/"${_policytype}"/base.lst; then /bin/echo -e "$semanage_import" | /usr/sbin/semanage import -S "${_policytype}" -N fi fi fi if [ $1 -eq 1 ] ; then # Initial installation systemctl preset named.service >/dev/null 2>&1 || : fi :; preuninstall scriptlet (using /bin/sh): # Package removal, not upgrade if [ $1 -eq 0 ] ; then # Package removal, not upgrade systemctl --no-reload disable named.service > /dev/null 2>&1 || : systemctl stop named.service > /dev/null 2>&1 || : fi postuninstall scriptlet (using /bin/sh): /sbin/ldconfig systemctl daemon-reload >/dev/null 2>&1 || : if [ $1 -ge 1 ] ; then # Package upgrade, not uninstall systemctl try-restart named.service >/dev/null 2>&1 || : fi # Unset on both upgrade and install. Boolean would be unset from now # until %posttrans on upgrade. Write requests might fail during update. . /etc/selinux/config if /usr/sbin/selinuxenabled && [ "${SELINUX}" != "disabled" ] ; then . /etc/selinux/config _policytype=targeted if [ -z "${_policytype}" ]; then _policytype="targeted" fi if [ -d "/etc/selinux/${_policytype}" ]; then semanage_import='' for boolean in named_write_master_zones=1; do boolean_name=${boolean%=*} boolean_customized_string=$(grep "$boolean_name$" /etc/selinux/${_policytype}/rpmbooleans.custom | tail -n 1) if [ -n "$boolean_customized_string" ]; then awk "/$boolean_customized_string/ && !f{f=1; next} 1" /etc/selinux/${_policytype}/rpmbooleans.custom > /etc/selinux/${_policytype}/rpmbooleans.custom.tmp && mv /etc/selinux/${_pol icytype}/rpmbooleans.custom.tmp /etc/selinux/${_policytype}/rpmbooleans.custom if ! grep -q "$boolean_name$" /etc/selinux/${_policytype}/rpmbooleans.custom; then semanage_import="${semanage_import} ${boolean_customized_string}" fi fi done; if /usr/sbin/selinuxenabled && [ "${SELINUXTYPE}" = "${_policytype}" ]; then /bin/echo -e "$semanage_import" | /usr/sbin/semanage import -S "${_policytype}" elif test -d /usr/share/selinux/"${_policytype}"/base.lst; then /bin/echo -e "$semanage_import" | /usr/sbin/semanage import -S "${_policytype}" -N fi fi . /etc/selinux/config _policytype=mls if [ -z "${_policytype}" ]; then _policytype="targeted" fi if [ -d "/etc/selinux/${_policytype}" ]; then semanage_import='' for boolean in named_write_master_zones=1; do boolean_name=${boolean%=*} boolean_customized_string=$(grep "$boolean_name$" /etc/selinux/${_policytype}/rpmbooleans.custom | tail -n 1) if [ -n "$boolean_customized_string" ]; then awk "/$boolean_customized_string/ && !f{f=1; next} 1" /etc/selinux/${_policytype}/rpmbooleans.custom > /etc/selinux/${_policytype}/rpmbooleans.custom.tmp && mv /etc/selinux/${_pol icytype}/rpmbooleans.custom.tmp /etc/selinux/${_policytype}/rpmbooleans.custom if ! grep -q "$boolean_name$" /etc/selinux/${_policytype}/rpmbooleans.custom; then semanage_import="${semanage_import} ${boolean_customized_string}" fi fi done; if /usr/sbin/selinuxenabled && [ "${SELINUXTYPE}" = "${_policytype}" ]; then /bin/echo -e "$semanage_import" | /usr/sbin/semanage import -S "${_policytype}" elif test -d /usr/share/selinux/"${_policytype}"/base.lst; then /bin/echo -e "$semanage_import" | /usr/sbin/semanage import -S "${_policytype}" -N fi fi fi [root@dns53.yinzhengjie.com ~]#

[root@dns53.yinzhengjie.com ~]# rpm -ql bind /etc/logrotate.d/named /etc/named /etc/named.conf /etc/named.iscdlv.key /etc/named.rfc1912.zones /etc/named.root.key /etc/rndc.conf /etc/rndc.key /etc/rwtab.d/named /etc/sysconfig/named /run/named /usr/bin/arpaname /usr/bin/named-rrchecker /usr/lib/python2.7/site-packages/isc /usr/lib/python2.7/site-packages/isc-2.0-py2.7.egg-info /usr/lib/python2.7/site-packages/isc/__init__.py /usr/lib/python2.7/site-packages/isc/__init__.pyc /usr/lib/python2.7/site-packages/isc/__init__.pyo /usr/lib/python2.7/site-packages/isc/checkds.py /usr/lib/python2.7/site-packages/isc/checkds.pyc /usr/lib/python2.7/site-packages/isc/checkds.pyo /usr/lib/python2.7/site-packages/isc/coverage.py /usr/lib/python2.7/site-packages/isc/coverage.pyc /usr/lib/python2.7/site-packages/isc/coverage.pyo /usr/lib/python2.7/site-packages/isc/dnskey.py /usr/lib/python2.7/site-packages/isc/dnskey.pyc /usr/lib/python2.7/site-packages/isc/dnskey.pyo /usr/lib/python2.7/site-packages/isc/eventlist.py /usr/lib/python2.7/site-packages/isc/eventlist.pyc /usr/lib/python2.7/site-packages/isc/eventlist.pyo /usr/lib/python2.7/site-packages/isc/keydict.py /usr/lib/python2.7/site-packages/isc/keydict.pyc /usr/lib/python2.7/site-packages/isc/keydict.pyo /usr/lib/python2.7/site-packages/isc/keyevent.py /usr/lib/python2.7/site-packages/isc/keyevent.pyc /usr/lib/python2.7/site-packages/isc/keyevent.pyo /usr/lib/python2.7/site-packages/isc/keymgr.py /usr/lib/python2.7/site-packages/isc/keymgr.pyc /usr/lib/python2.7/site-packages/isc/keymgr.pyo /usr/lib/python2.7/site-packages/isc/keyseries.py /usr/lib/python2.7/site-packages/isc/keyseries.pyc /usr/lib/python2.7/site-packages/isc/keyseries.pyo /usr/lib/python2.7/site-packages/isc/keyzone.py /usr/lib/python2.7/site-packages/isc/keyzone.pyc /usr/lib/python2.7/site-packages/isc/keyzone.pyo /usr/lib/python2.7/site-packages/isc/parsetab.py /usr/lib/python2.7/site-packages/isc/parsetab.pyc /usr/lib/python2.7/site-packages/isc/parsetab.pyo /usr/lib/python2.7/site-packages/isc/policy.py /usr/lib/python2.7/site-packages/isc/policy.pyc /usr/lib/python2.7/site-packages/isc/policy.pyo /usr/lib/python2.7/site-packages/isc/rndc.py /usr/lib/python2.7/site-packages/isc/rndc.pyc /usr/lib/python2.7/site-packages/isc/rndc.pyo /usr/lib/python2.7/site-packages/isc/utils.py /usr/lib/python2.7/site-packages/isc/utils.pyc /usr/lib/python2.7/site-packages/isc/utils.pyo /usr/lib/systemd/system/named-setup-rndc.service /usr/lib/systemd/system/named.service /usr/lib/tmpfiles.d/named.conf /usr/lib64/bind /usr/libexec/generate-rndc-key.sh /usr/sbin/ddns-confgen /usr/sbin/dnssec-checkds /usr/sbin/dnssec-coverage /usr/sbin/dnssec-dsfromkey /usr/sbin/dnssec-importkey /usr/sbin/dnssec-keyfromlabel /usr/sbin/dnssec-keygen /usr/sbin/dnssec-keymgr /usr/sbin/dnssec-revoke /usr/sbin/dnssec-settime /usr/sbin/dnssec-signzone /usr/sbin/dnssec-verify /usr/sbin/genrandom /usr/sbin/isc-hmac-fixup /usr/sbin/lwresd /usr/sbin/named /usr/sbin/named-checkconf /usr/sbin/named-checkzone /usr/sbin/named-compilezone /usr/sbin/named-journalprint /usr/sbin/nsec3hash /usr/sbin/rndc /usr/sbin/rndc-confgen /usr/sbin/tsig-keygen /usr/share/doc/bind-9.11.4 /usr/share/doc/bind-9.11.4/Bv9ARM.ch01.html /usr/share/doc/bind-9.11.4/Bv9ARM.ch02.html /usr/share/doc/bind-9.11.4/Bv9ARM.ch03.html /usr/share/doc/bind-9.11.4/Bv9ARM.ch04.html /usr/share/doc/bind-9.11.4/Bv9ARM.ch05.html /usr/share/doc/bind-9.11.4/Bv9ARM.ch06.html /usr/share/doc/bind-9.11.4/Bv9ARM.ch07.html /usr/share/doc/bind-9.11.4/Bv9ARM.ch08.html /usr/share/doc/bind-9.11.4/Bv9ARM.ch09.html /usr/share/doc/bind-9.11.4/Bv9ARM.ch10.html /usr/share/doc/bind-9.11.4/Bv9ARM.ch11.html /usr/share/doc/bind-9.11.4/Bv9ARM.ch12.html /usr/share/doc/bind-9.11.4/Bv9ARM.ch13.html /usr/share/doc/bind-9.11.4/Bv9ARM.html /usr/share/doc/bind-9.11.4/Bv9ARM.pdf /usr/share/doc/bind-9.11.4/CHANGES /usr/share/doc/bind-9.11.4/README /usr/share/doc/bind-9.11.4/isc-logo.pdf /usr/share/doc/bind-9.11.4/man.arpaname.html /usr/share/doc/bind-9.11.4/man.ddns-confgen.html /usr/share/doc/bind-9.11.4/man.delv.html /usr/share/doc/bind-9.11.4/man.dig.html /usr/share/doc/bind-9.11.4/man.dnssec-checkds.html /usr/share/doc/bind-9.11.4/man.dnssec-coverage.html /usr/share/doc/bind-9.11.4/man.dnssec-dsfromkey.html /usr/share/doc/bind-9.11.4/man.dnssec-importkey.html /usr/share/doc/bind-9.11.4/man.dnssec-keyfromlabel.html /usr/share/doc/bind-9.11.4/man.dnssec-keygen.html /usr/share/doc/bind-9.11.4/man.dnssec-keymgr.html /usr/share/doc/bind-9.11.4/man.dnssec-revoke.html /usr/share/doc/bind-9.11.4/man.dnssec-settime.html /usr/share/doc/bind-9.11.4/man.dnssec-signzone.html /usr/share/doc/bind-9.11.4/man.dnssec-verify.html /usr/share/doc/bind-9.11.4/man.dnstap-read.html /usr/share/doc/bind-9.11.4/man.genrandom.html /usr/share/doc/bind-9.11.4/man.host.html /usr/share/doc/bind-9.11.4/man.isc-hmac-fixup.html /usr/share/doc/bind-9.11.4/man.lwresd.html /usr/share/doc/bind-9.11.4/man.mdig.html /usr/share/doc/bind-9.11.4/man.named-checkconf.html /usr/share/doc/bind-9.11.4/man.named-checkzone.html /usr/share/doc/bind-9.11.4/man.named-journalprint.html /usr/share/doc/bind-9.11.4/man.named-nzd2nzf.html /usr/share/doc/bind-9.11.4/man.named-rrchecker.html /usr/share/doc/bind-9.11.4/man.named.conf.html /usr/share/doc/bind-9.11.4/man.named.html /usr/share/doc/bind-9.11.4/man.nsec3hash.html /usr/share/doc/bind-9.11.4/man.nslookup.html /usr/share/doc/bind-9.11.4/man.nsupdate.html /usr/share/doc/bind-9.11.4/man.pkcs11-destroy.html /usr/share/doc/bind-9.11.4/man.pkcs11-keygen.html /usr/share/doc/bind-9.11.4/man.pkcs11-list.html /usr/share/doc/bind-9.11.4/man.pkcs11-tokens.html /usr/share/doc/bind-9.11.4/man.rndc-confgen.html /usr/share/doc/bind-9.11.4/man.rndc.conf.html /usr/share/doc/bind-9.11.4/man.rndc.html /usr/share/doc/bind-9.11.4/named.conf.default /usr/share/doc/bind-9.11.4/notes.html /usr/share/doc/bind-9.11.4/notes.pdf /usr/share/doc/bind-9.11.4/sample /usr/share/doc/bind-9.11.4/sample/etc /usr/share/doc/bind-9.11.4/sample/etc/named.conf /usr/share/doc/bind-9.11.4/sample/etc/named.rfc1912.zones /usr/share/doc/bind-9.11.4/sample/var /usr/share/doc/bind-9.11.4/sample/var/named /usr/share/doc/bind-9.11.4/sample/var/named/data /usr/share/doc/bind-9.11.4/sample/var/named/my.external.zone.db /usr/share/doc/bind-9.11.4/sample/var/named/my.internal.zone.db /usr/share/doc/bind-9.11.4/sample/var/named/named.ca /usr/share/doc/bind-9.11.4/sample/var/named/named.empty /usr/share/doc/bind-9.11.4/sample/var/named/named.localhost /usr/share/doc/bind-9.11.4/sample/var/named/named.loopback /usr/share/doc/bind-9.11.4/sample/var/named/slaves /usr/share/doc/bind-9.11.4/sample/var/named/slaves/my.ddns.internal.zone.db /usr/share/doc/bind-9.11.4/sample/var/named/slaves/my.slave.internal.zone.db /usr/share/man/man1/arpaname.1.gz /usr/share/man/man1/named-rrchecker.1.gz /usr/share/man/man5/named.conf.5.gz /usr/share/man/man5/rndc.conf.5.gz /usr/share/man/man8/ddns-confgen.8.gz /usr/share/man/man8/dnssec-checkds.8.gz /usr/share/man/man8/dnssec-coverage.8.gz /usr/share/man/man8/dnssec-dsfromkey.8.gz /usr/share/man/man8/dnssec-importkey.8.gz /usr/share/man/man8/dnssec-keyfromlabel.8.gz /usr/share/man/man8/dnssec-keygen.8.gz /usr/share/man/man8/dnssec-keymgr.8.gz /usr/share/man/man8/dnssec-revoke.8.gz /usr/share/man/man8/dnssec-settime.8.gz /usr/share/man/man8/dnssec-signzone.8.gz /usr/share/man/man8/dnssec-verify.8.gz /usr/share/man/man8/genrandom.8.gz /usr/share/man/man8/isc-hmac-fixup.8.gz /usr/share/man/man8/lwresd.8.gz /usr/share/man/man8/named-checkconf.8.gz /usr/share/man/man8/named-checkzone.8.gz /usr/share/man/man8/named-compilezone.8.gz /usr/share/man/man8/named-journalprint.8.gz /usr/share/man/man8/named.8.gz /usr/share/man/man8/nsec3hash.8.gz /usr/share/man/man8/rndc-confgen.8.gz /usr/share/man/man8/rndc.8.gz /usr/share/man/man8/tsig-keygen.8.gz /var/log/named.log /var/named /var/named/data /var/named/dynamic /var/named/named.ca /var/named/named.empty /var/named/named.localhost /var/named/named.loopback /var/named/slaves [root@dns53.yinzhengjie.com ~]# [root@dns53.yinzhengjie.com ~]#
3>.bind服务软件常用文件说明
主配置文件: /etc/named.conf 服务名称: /usr/lib/systemd/system/named.service: 主程序: /usr/sbin/named 数据库文件: /var/named 日志文件: /var/log/named.log 存储根域服务器地址的文件: /var/named/named.ca 检查配置文件语法程序: /usr/sbin/named-checkconf 重新加载bind服务的配置文件,而无需重启服务: /usr/sbin/rndc
4>.启动DNS服务器
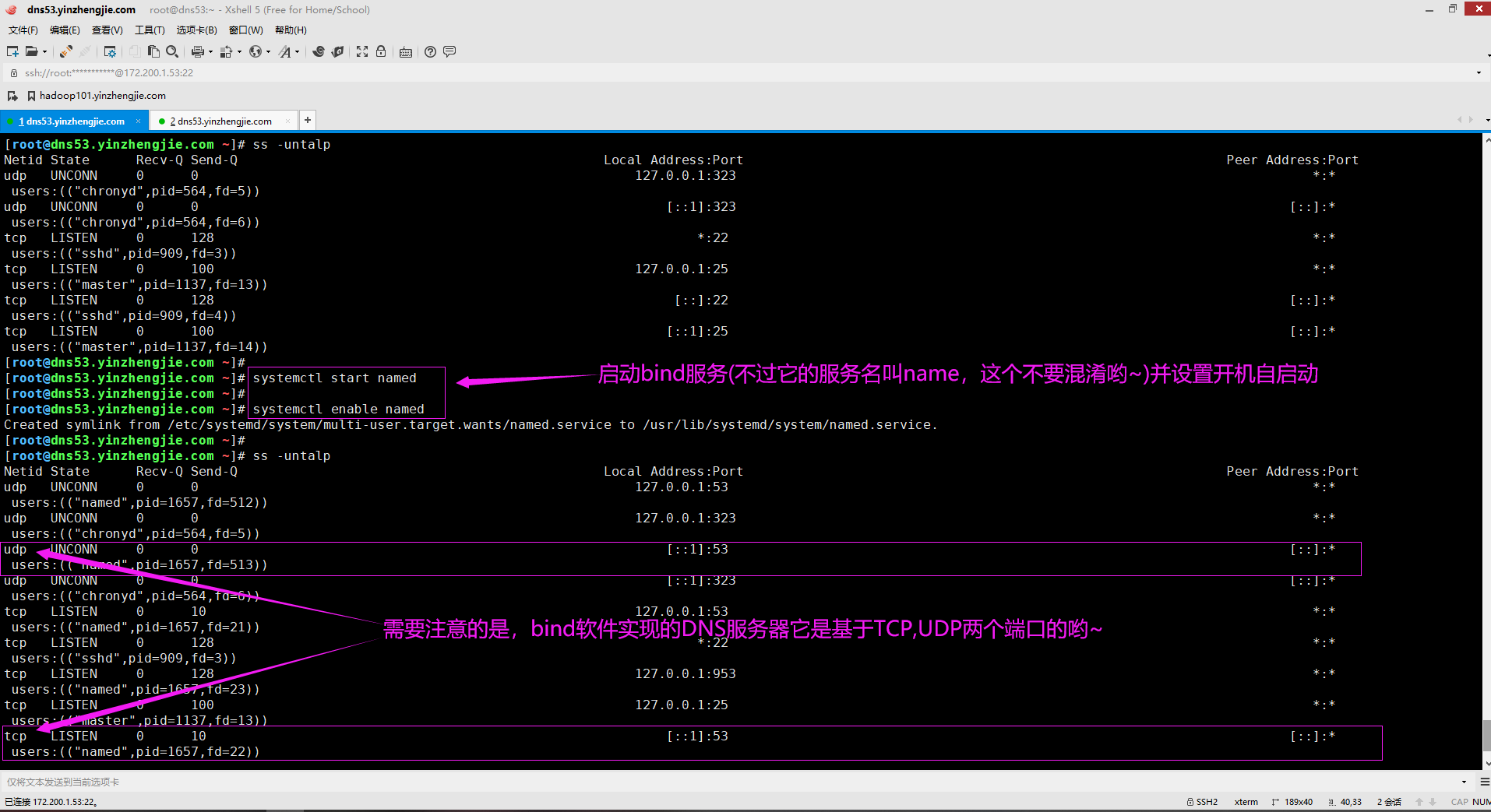
[root@dns53.yinzhengjie.com ~]# systemctl start named [root@dns53.yinzhengjie.com ~]# [root@dns53.yinzhengjie.com ~]# systemctl enable named Created symlink from /etc/systemd/system/multi-user.target.wants/named.service to /usr/lib/systemd/system/named.service. [root@dns53.yinzhengjie.com ~]#
温馨提示:
如下图所示,我们成功启动了DNS服务器,但我埋下了一个坑,因为我没有修改bind服务的配置文件,这意味着默认监听的服务器地址是本地回环地址(即127.0.0.1)哟~
5>.找一台客户端将其DNS服务器指向咱们自建的bind服务器哟
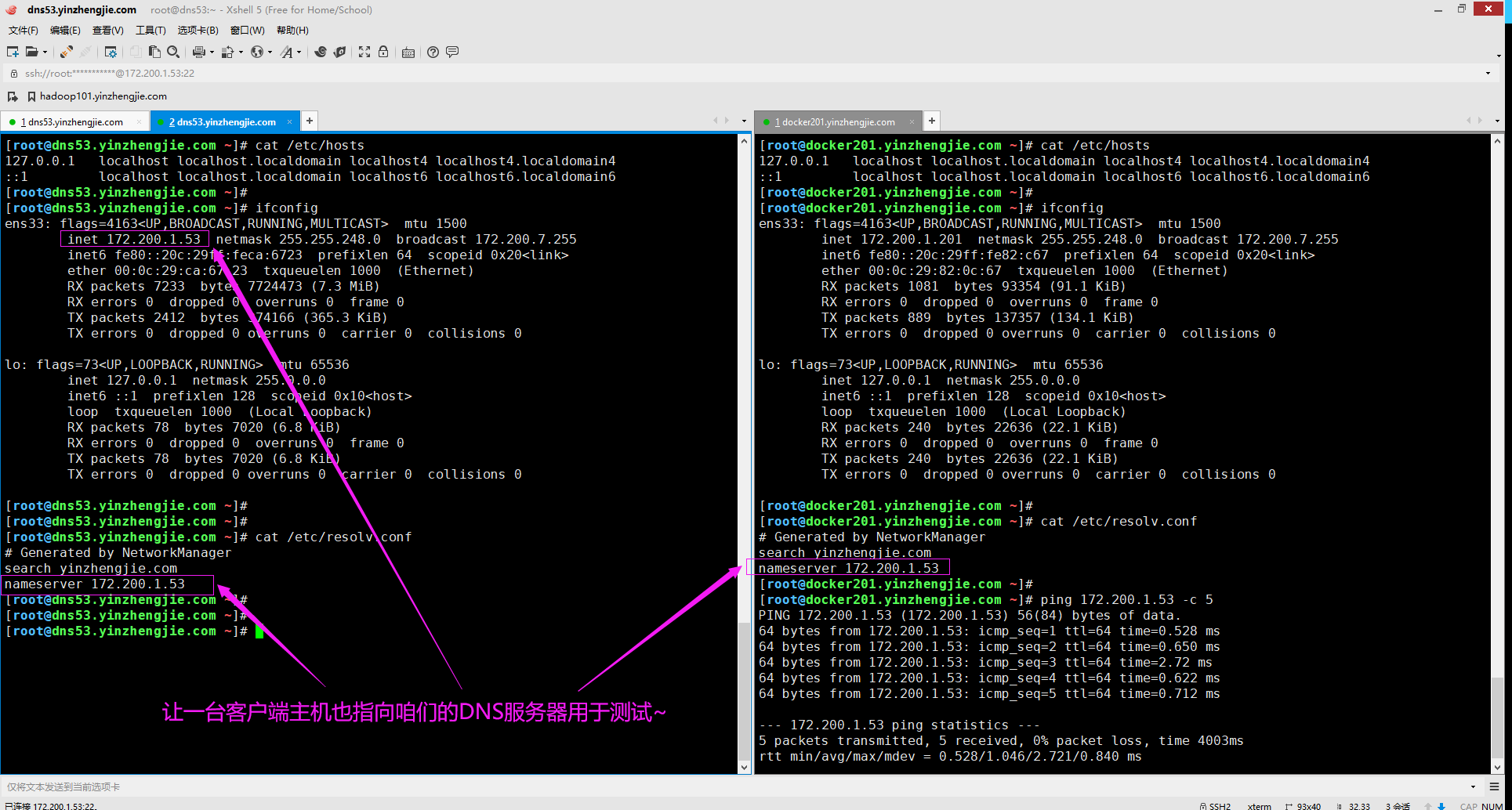
三.验证DNS服务器的可用性
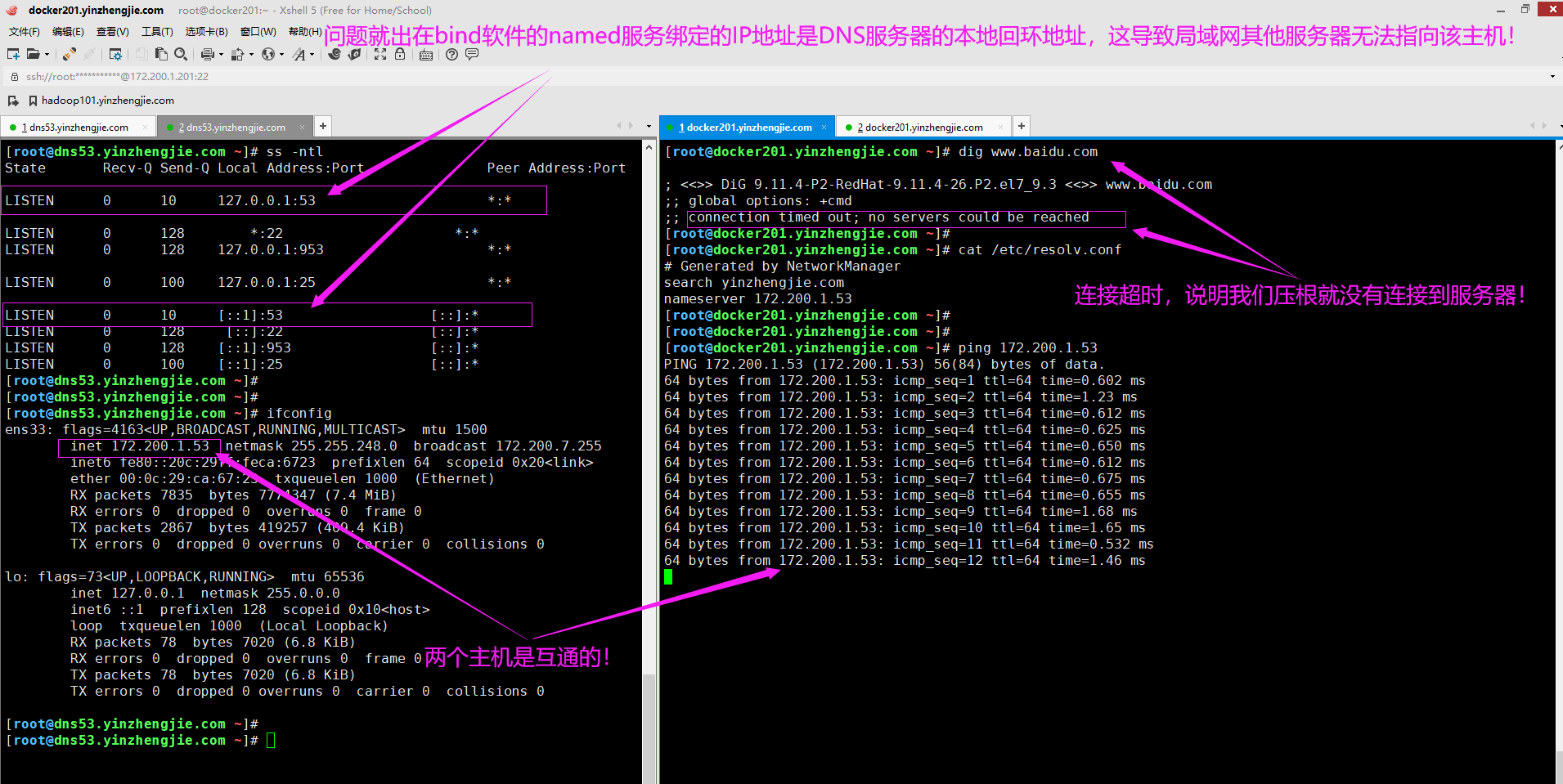
1>.客户端连接DNS服务器解析,发现超时
如下图所示,这就是我上面提到的,给大家埋了一个坑,因为我没有修改bind服务的配置服务,因此它会使用默认的配置文件。而默认的配置文件监听的都是IPv4和IPv6的本地回环地址。
温馨提示:
我们可以注释"listen-on"和"listen-on-v6",也会默认监听本地的所有主机哟。
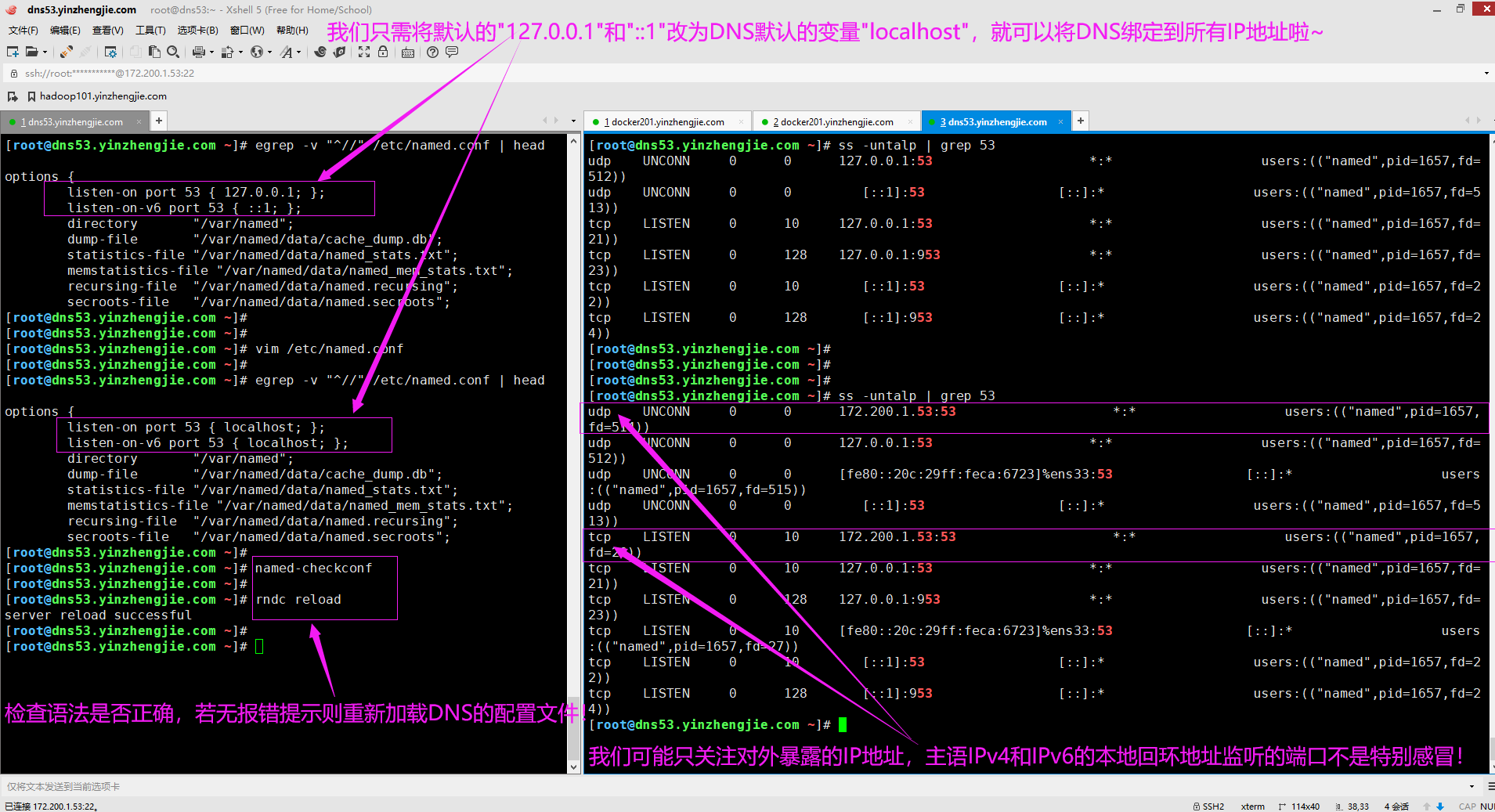
2>.修改bind服务的监听地址
如下图所示,我们可以将IPV4和IPV6的监听地址修改为"localhost",这样就会监听DNS服务器的所有网卡IP地址啦!
生产环境中,建议大家还是配置成对应DNS服务器实际的网卡地址,除非你明确知道你要监听所有的DNS服务器的所有网卡地址,因为有的服务器网卡接口不止一个,甚至一台服务有十几块网卡都是存在的哟~
3>.默认情况下,仅允许DNS服务器自己有权限访问DNS服务哟
如下图所示,DNS服务器是可以进行解析操作的,但是非DNS的其他主机却无法进行解析。这是DNS默认是有权限的,需要我们手动修改!
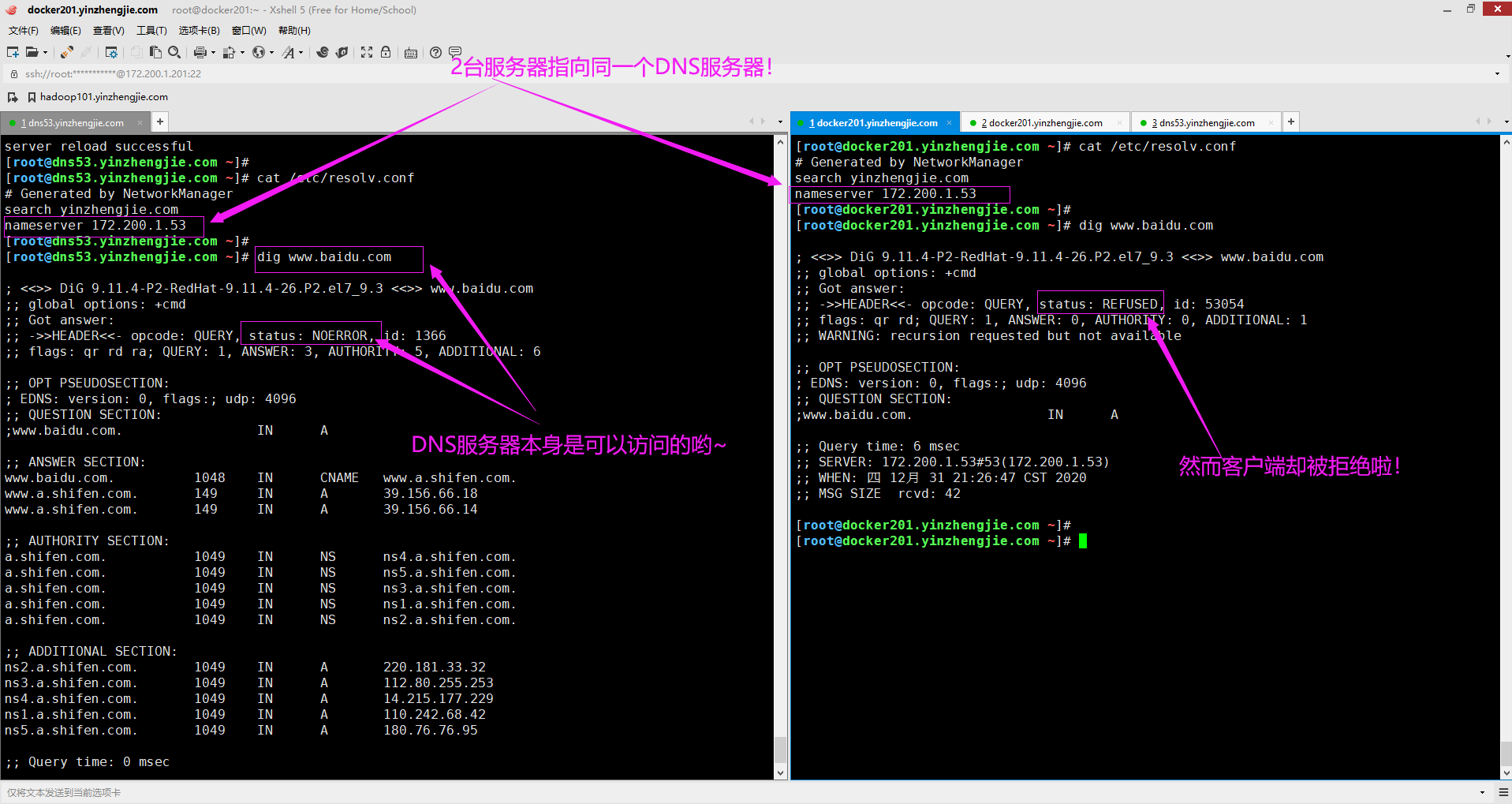
4>.修改DNS服务器的权限
[root@dns53.yinzhengjie.com ~]# egrep -v "^//|^$" /etc/named.conf | head options { listen-on port 53 { localhost; }; listen-on-v6 port 53 { localhost; }; directory "/var/named"; dump-file "/var/named/data/cache_dump.db"; statistics-file "/var/named/data/named_stats.txt"; memstatistics-file "/var/named/data/named_mem_stats.txt"; recursing-file "/var/named/data/named.recursing"; secroots-file "/var/named/data/named.secroots"; allow-query { any; }; [root@dns53.yinzhengjie.com ~]# [root@dns53.yinzhengjie.com ~]# [root@dns53.yinzhengjie.com ~]# named-checkconf # 检查bind程序的语法配置是否正确 [root@dns53.yinzhengjie.com ~]# [root@dns53.yinzhengjie.com ~]# rndc reload # 重新加载bind的配置文件! server reload successful [root@dns53.yinzhengjie.com ~]#
温馨提示:
需要注意的是,allow-query可以设置为any,表示允许所有客户端访问,当然,如果你注释改行的话默认就是any。
顺表说一句,除了将allow-query设置为any值外,我们还可以允许指定主机网段来访问本DNS服务器,比如仅允许"172.200.0.0/21"的网段访问!
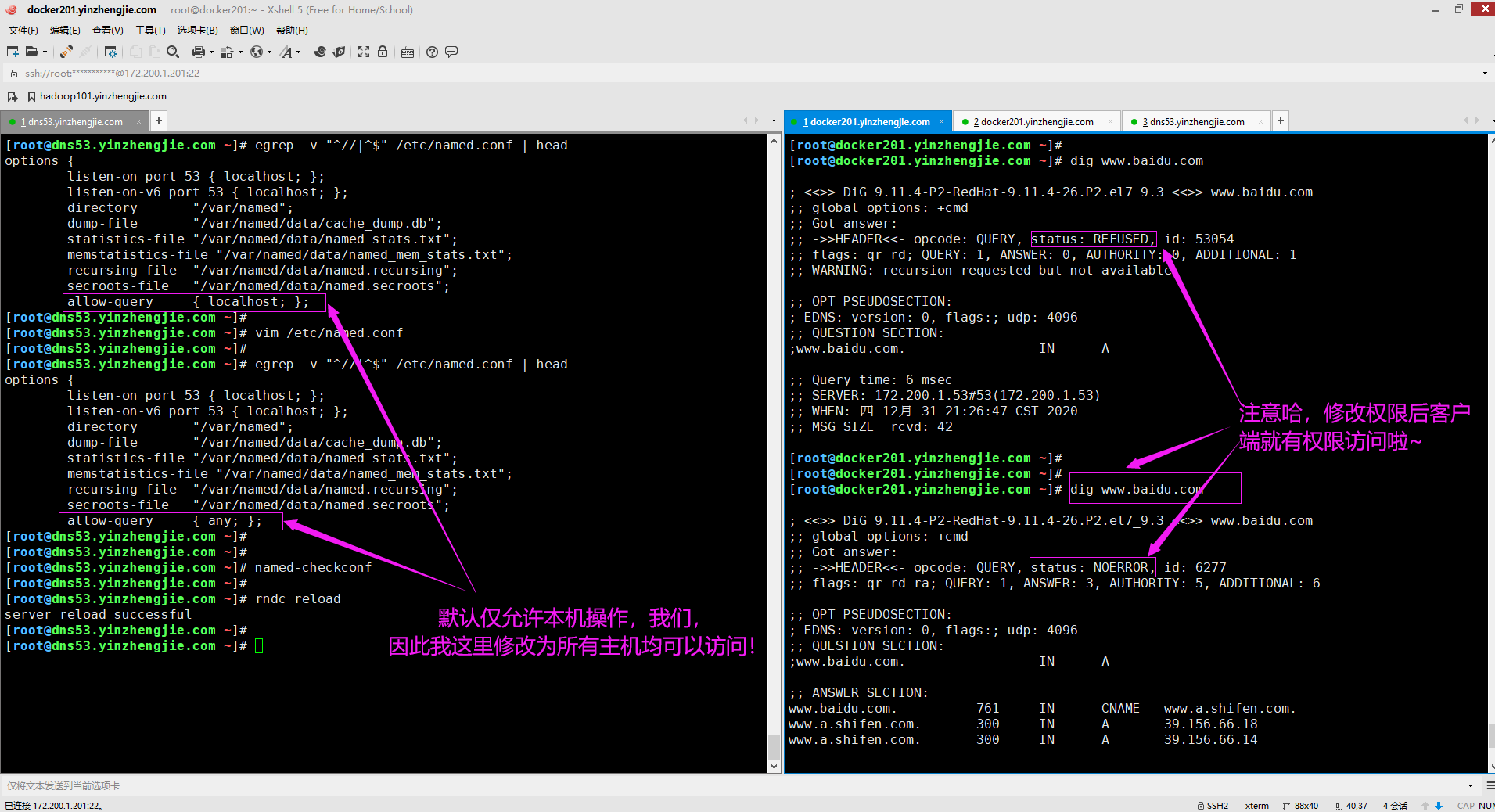
5>.DNS正向解析实现
如果能做到这一步,说明你的DNS服务器部署完毕了,那么接下来我们就开始来自定义DNS服务器来进行解析操作啦! DNS正向解析实现可以参考我另一篇笔记: https://www.cnblogs.com/yinzhengjie/p/14218718.html
