Kerbernetes使用Secret资源配置铭感信息
作者:尹正杰
版权声明:原创作品,谢绝转载!否则将追究法律责任。
Sercret的使用逻辑和ConfigMap并没什么区别,唯一不同的是Secret的数据是被base64编码后存储的。
一.基于环境变量引用Secret(保存MySQL的密码)案例
1>.查看secret的帮助信息
secret存在三种类型:
docker-registry: 用于提供docker镜像仓库的认证配置。
generic:
比较通用的配置,即保存私有的铭感信息,比如MySQL的root密码,Redis进行同步的密码等。
tls:
专用于把ssl/tls中的x509格式的证书和私钥打包进一个secret当中。
这个证书和私钥本身就是base64编码的,因此它可能需要特有的逻辑来组织,而且不管你的证书和私钥源文件名称叫什么,在secret的tls创建时证书文件名称时必须叫"tls.crt",私钥文件名称只能叫"tls.key"

[root@master200.yinzhengjie.org.cn ~]# kubectl create secret -h Create a secret using specified subcommand. Available Commands: docker-registry Create a secret for use with a Docker registry generic Create a secret from a local file, directory or literal value tls Create a TLS secret Usage: kubectl create secret [flags] [options] Use "kubectl <command> --help" for more information about a given command. Use "kubectl options" for a list of global command-line options (applies to all commands). [root@master200.yinzhengjie.org.cn ~]# [root@master200.yinzhengjie.org.cn ~]#
2>.以命令行方式创建secret资源

[root@master200.yinzhengjie.org.cn ~]# kubectl create secret generic mysql-root-password -n yinzhengjie-config --from-literal=password=yinzhengjie secret/mysql-root-password created [root@master200.yinzhengjie.org.cn ~]# [root@master200.yinzhengjie.org.cn ~]# kubectl get secret mysql-root-password -n yinzhengjie-config NAME TYPE DATA AGE mysql-root-password Opaque 1 22s [root@master200.yinzhengjie.org.cn ~]#

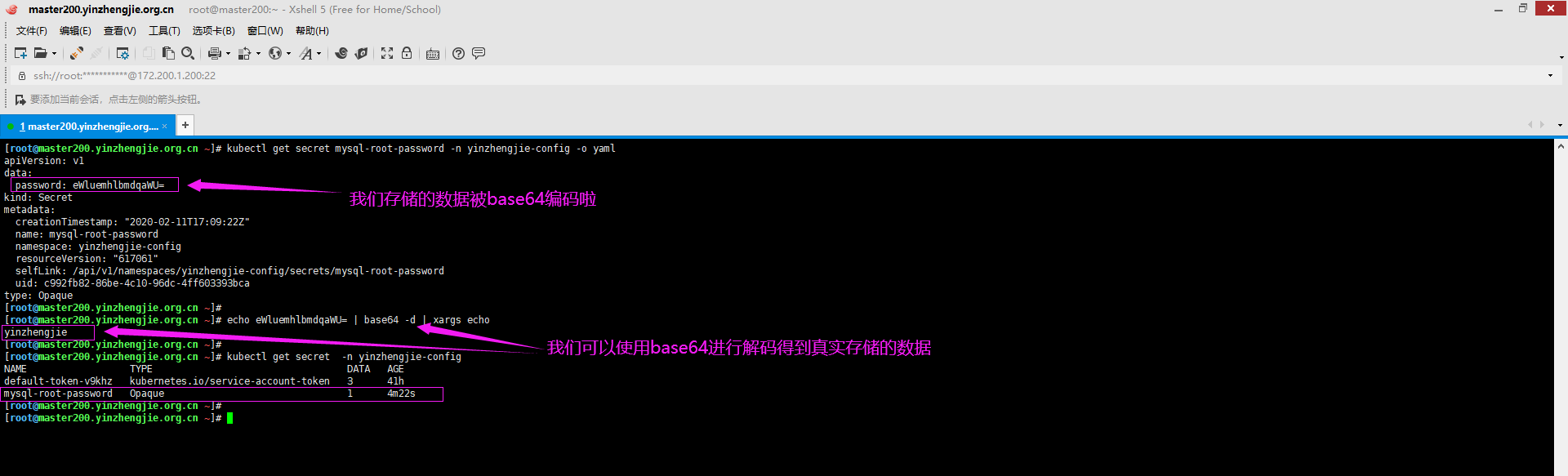
[root@master200.yinzhengjie.org.cn ~]# kubectl get secret mysql-root-password -n yinzhengjie-config -o yaml apiVersion: v1 data: password: eWluemhlbmdqaWU= kind: Secret metadata: creationTimestamp: "2020-02-11T17:09:22Z" name: mysql-root-password namespace: yinzhengjie-config resourceVersion: "617061" selfLink: /api/v1/namespaces/yinzhengjie-config/secrets/mysql-root-password uid: c992fb82-86be-4c10-96dc-4ff603393bca type: Opaque [root@master200.yinzhengjie.org.cn ~]# [root@master200.yinzhengjie.org.cn ~]#

[root@master200.yinzhengjie.org.cn ~]# kubectl get secret mysql-root-password -n yinzhengjie-config -o yaml apiVersion: v1 data: password: eWluemhlbmdqaWU= kind: Secret metadata: creationTimestamp: "2020-02-11T17:09:22Z" name: mysql-root-password namespace: yinzhengjie-config resourceVersion: "617061" selfLink: /api/v1/namespaces/yinzhengjie-config/secrets/mysql-root-password uid: c992fb82-86be-4c10-96dc-4ff603393bca type: Opaque [root@master200.yinzhengjie.org.cn ~]# [root@master200.yinzhengjie.org.cn ~]# echo eWluemhlbmdqaWU= | base64 -d | xargs echo yinzhengjie [root@master200.yinzhengjie.org.cn ~]# [root@master200.yinzhengjie.org.cn ~]# kubectl get secret -n yinzhengjie-config NAME TYPE DATA AGE default-token-v9khz kubernetes.io/service-account-token 3 41h mysql-root-password Opaque 1 4m22s [root@master200.yinzhengjie.org.cn ~]# [root@master200.yinzhengjie.org.cn ~]#
3>.创建pod并引用创建的secret

[root@master200.yinzhengjie.org.cn ~]# vim /yinzhengjie/data/k8s/manifests/basic/secret/mysql-pod.yaml [root@master200.yinzhengjie.org.cn ~]# [root@master200.yinzhengjie.org.cn ~]# cat /yinzhengjie/data/k8s/manifests/basic/secret/mysql-pod.yaml apiVersion: v1 kind: Pod metadata: name: mysql namespace: yinzhengjie-config spec: containers: - name: mysql image: mysql:5.6 env: - name: MYSQL_ROOT_PASSWORD valueFrom: secretKeyRef: key: password name: mysql-root-password [root@master200.yinzhengjie.org.cn ~]#

[root@master200.yinzhengjie.org.cn ~]# kubectl apply -f /yinzhengjie/data/k8s/manifests/basic/secret/mysql-pod.yaml pod/mysql created [root@master200.yinzhengjie.org.cn ~]# [root@master200.yinzhengjie.org.cn ~]# kubectl get pods -n yinzhengjie-config NAME READY STATUS RESTARTS AGE mynginx 1/1 Running 1 40h mysql 1/1 Running 0 57s pod-cfg-dome 1/1 Running 1 41h [root@master200.yinzhengjie.org.cn ~]# [root@master200.yinzhengjie.org.cn ~]#

[root@master200.yinzhengjie.org.cn ~]# kubectl get pods -n yinzhengjie-config NAME READY STATUS RESTARTS AGE mynginx 1/1 Running 1 40h mysql 1/1 Running 0 7m14s pod-cfg-dome 1/1 Running 1 41h [root@master200.yinzhengjie.org.cn ~]# [root@master200.yinzhengjie.org.cn ~]# [root@master200.yinzhengjie.org.cn ~]# kubectl describe pods mysql -n yinzhengjie-config Name: mysql Namespace: yinzhengjie-config Priority: 0 Node: node201.yinzhengjie.org.cn/172.200.1.201 Start Time: Wed, 12 Feb 2020 01:27:12 +0800 Labels: <none> Annotations: kubectl.kubernetes.io/last-applied-configuration: {"apiVersion":"v1","kind":"Pod","metadata":{"annotations":{},"name":"mysql","namespace":"yinzhengjie-config"},"spec":{"containers":[{"env"... Status: Running IP: 10.244.1.33 IPs: IP: 10.244.1.33 Containers: mysql: Container ID: docker://f970431d35c85ab7a57f0bb4b44207329878b515e723ae9498cb3fdb35585d21 Image: mysql:5.6 Image ID: docker-pullable://mysql@sha256:bef096aee20d73cbfd87b02856321040ab1127e94b707b41927804776dca02fc Port: <none> Host Port: <none> State: Running Started: Wed, 12 Feb 2020 01:27:35 +0800 Ready: True Restart Count: 0 Environment: MYSQL_ROOT_PASSWORD: <set to the key 'password' in secret 'mysql-root-password'> Optional: false Mounts: /var/run/secrets/kubernetes.io/serviceaccount from default-token-v9khz (ro) Conditions: Type Status Initialized True Ready True ContainersReady True PodScheduled True Volumes: default-token-v9khz: Type: Secret (a volume populated by a Secret) SecretName: default-token-v9khz Optional: false QoS Class: BestEffort Node-Selectors: <none> Tolerations: node.kubernetes.io/not-ready:NoExecute for 300s node.kubernetes.io/unreachable:NoExecute for 300s Events: Type Reason Age From Message ---- ------ ---- ---- ------- Normal Scheduled <unknown> default-scheduler Successfully assigned yinzhengjie-config/mysql to node201.yinzhengjie.org.cn Normal Pulling 7m23s kubelet, node201.yinzhengjie.org.cn Pulling image "mysql:5.6" Normal Pulled 7m1s kubelet, node201.yinzhengjie.org.cn Successfully pulled image "mysql:5.6" Normal Created 7m1s kubelet, node201.yinzhengjie.org.cn Created container mysql Normal Started 7m1s kubelet, node201.yinzhengjie.org.cn Started container mysql [root@master200.yinzhengjie.org.cn ~]# [root@master200.yinzhengjie.org.cn ~]#
4>.连接Pod中的MySQL容器并验证密码

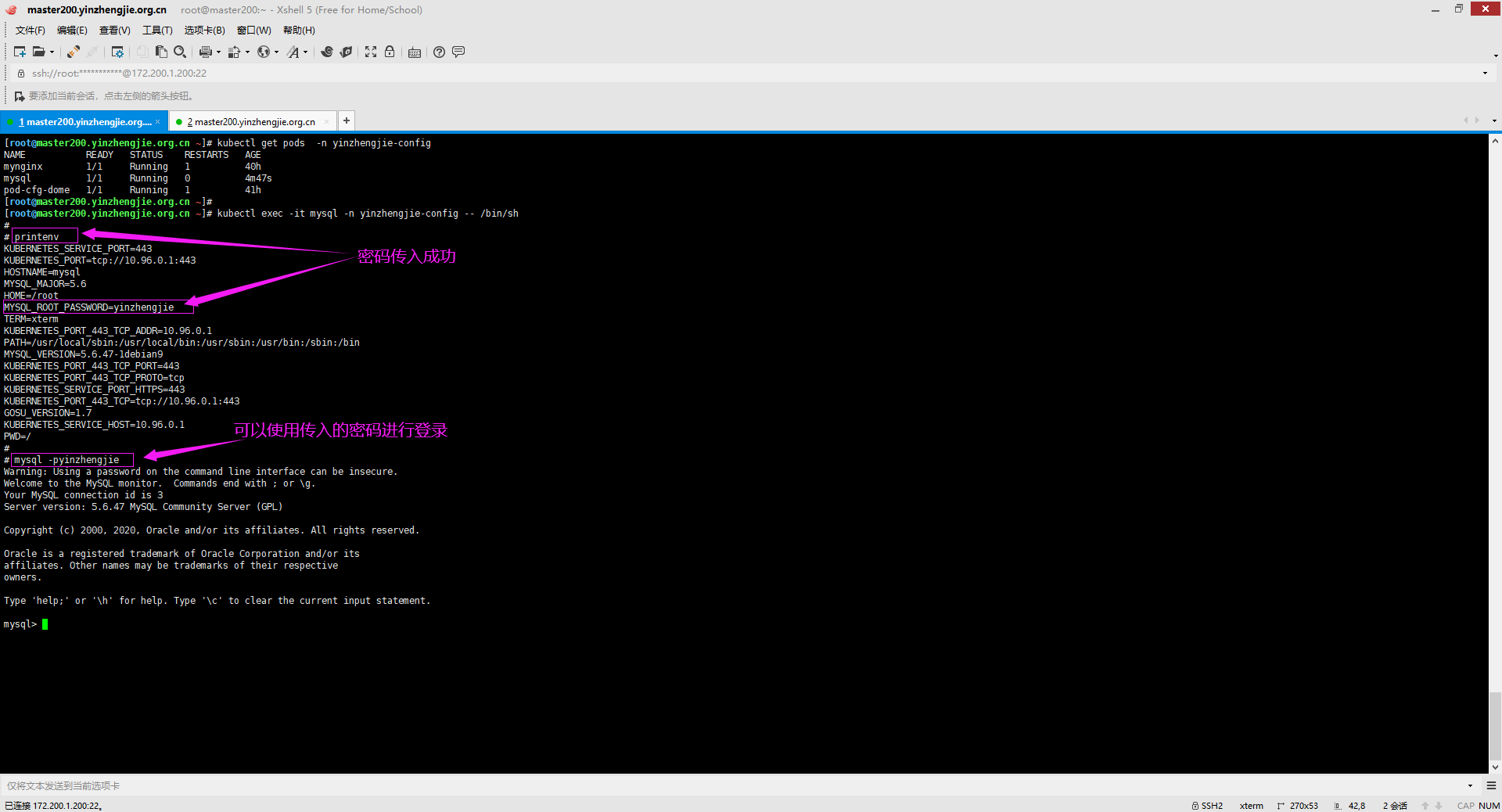
[root@master200.yinzhengjie.org.cn ~]# kubectl get pods -n yinzhengjie-config NAME READY STATUS RESTARTS AGE mynginx 1/1 Running 1 40h mysql 1/1 Running 0 4m47s pod-cfg-dome 1/1 Running 1 41h [root@master200.yinzhengjie.org.cn ~]# [root@master200.yinzhengjie.org.cn ~]# kubectl exec -it mysql -n yinzhengjie-config -- /bin/sh # # printenv KUBERNETES_SERVICE_PORT=443 KUBERNETES_PORT=tcp://10.96.0.1:443 HOSTNAME=mysql MYSQL_MAJOR=5.6 HOME=/root MYSQL_ROOT_PASSWORD=yinzhengjie TERM=xterm KUBERNETES_PORT_443_TCP_ADDR=10.96.0.1 PATH=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin MYSQL_VERSION=5.6.47-1debian9 KUBERNETES_PORT_443_TCP_PORT=443 KUBERNETES_PORT_443_TCP_PROTO=tcp KUBERNETES_SERVICE_PORT_HTTPS=443 KUBERNETES_PORT_443_TCP=tcp://10.96.0.1:443 GOSU_VERSION=1.7 KUBERNETES_SERVICE_HOST=10.96.0.1 PWD=/ # # mysql -pyinzhengjie Warning: Using a password on the command line interface can be insecure. Welcome to the MySQL monitor. Commands end with ; or g. Your MySQL connection id is 3 Server version: 5.6.47 MySQL Community Server (GPL) Copyright (c) 2000, 2020, Oracle and/or its affiliates. All rights reserved. Oracle is a registered trademark of Oracle Corporation and/or its affiliates. Other names may be trademarks of their respective owners. Type 'help;' or 'h' for help. Type 'c' to clear the current input statement. mysql>
5>.基于配置文件引用Secret实现配置容器(和配置ConfigMap步骤类似)
[root@master200.yinzhengjie.org.cn ~]# kubectl explain pods.spec.volumes.secret KIND: Pod VERSION: v1 RESOURCE: secret <Object> DESCRIPTION: Secret represents a secret that should populate this volume. More info: https://kubernetes.io/docs/concepts/storage/volumes#secret Adapts a Secret into a volume. The contents of the target Secret's Data field will be presented in a volume as files using the keys in the Data field as the file names. Secret volumes support ownership management and SELinux relabeling. FIELDS: defaultMode <integer> Optional: mode bits to use on created files by default. Must be a value between 0 and 0777. Defaults to 0644. Directories within the path are not affected by this setting. This might be in conflict with other options that affect the file mode, like fsGroup, and the result can be other mode bits set. items <[]Object> If unspecified, each key-value pair in the Data field of the referenced Secret will be projected into the volume as a file whose name is the key and content is the value. If specified, the listed keys will be projected into the specified paths, and unlisted keys will not be present. If a key is specified which is not present in the Secret, the volume setup will error unless it is marked optional. Paths must be relative and may not contain the '..' path or start with '..'. optional <boolean> Specify whether the Secret or its keys must be defined secretName <string> Name of the secret in the pod's namespace to use. More info: https://kubernetes.io/docs/concepts/storage/volumes#secret [root@master200.yinzhengjie.org.cn ~]#

[root@master200.yinzhengjie.org.cn ~]# kubectl explain pods.spec.volumes.secret.defaultMode KIND: Pod VERSION: v1 FIELD: defaultMode <integer> DESCRIPTION: Optional: mode bits to use on created files by default. Must be a value between 0 and 0777. Defaults to 0644. Directories within the path are not affected by this setting. This might be in conflict with other options that affect the file mode, like fsGroup, and the result can be other mode bits set. [root@master200.yinzhengjie.org.cn ~]#

[root@master200.yinzhengjie.org.cn ~]# kubectl explain pods.spec.volumes.secret.items KIND: Pod VERSION: v1 RESOURCE: items <[]Object> DESCRIPTION: If unspecified, each key-value pair in the Data field of the referenced Secret will be projected into the volume as a file whose name is the key and content is the value. If specified, the listed keys will be projected into the specified paths, and unlisted keys will not be present. If a key is specified which is not present in the Secret, the volume setup will error unless it is marked optional. Paths must be relative and may not contain the '..' path or start with '..'. Maps a string key to a path within a volume. FIELDS: key <string> -required- The key to project. mode <integer> Optional: mode bits to use on this file, must be a value between 0 and 0777. If not specified, the volume defaultMode will be used. This might be in conflict with other options that affect the file mode, like fsGroup, and the result can be other mode bits set. path <string> -required- The relative path of the file to map the key to. May not be an absolute path. May not contain the path element '..'. May not start with the string '..'. [root@master200.yinzhengjie.org.cn ~]# [root@master200.yinzhengjie.org.cn ~]#

[root@master200.yinzhengjie.org.cn ~]# kubectl explain pods.spec.volumes.secret.optional KIND: Pod VERSION: v1 FIELD: optional <boolean> DESCRIPTION: Specify whether the Secret or its keys must be defined [root@master200.yinzhengjie.org.cn ~]#

[root@master200.yinzhengjie.org.cn ~]# kubectl explain pods.spec.volumes.secret.secretName KIND: Pod VERSION: v1 FIELD: secretName <string> DESCRIPTION: Name of the secret in the pod's namespace to use. More info: https://kubernetes.io/docs/concepts/storage/volumes#secret [root@master200.yinzhengjie.org.cn ~]#
二.创建tls类型案例
1>.自建证书

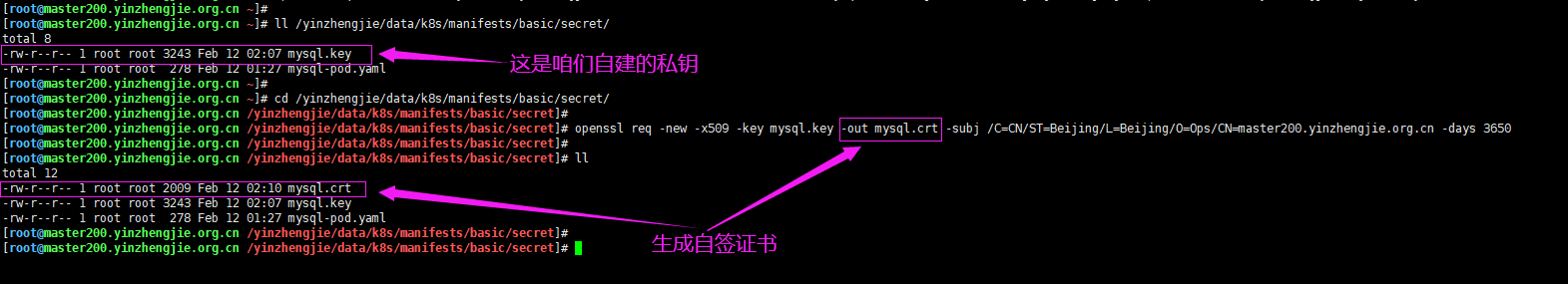
[root@master200.yinzhengjie.org.cn ~]# ll /yinzhengjie/data/k8s/manifests/basic/secret/ total 4 -rw-r--r-- 1 root root 278 Feb 12 01:27 mysql-pod.yaml [root@master200.yinzhengjie.org.cn ~]# [root@master200.yinzhengjie.org.cn ~]# openssl genrsa -out /yinzhengjie/data/k8s/manifests/basic/secret/mysql.key 4096 #创建私钥 Generating RSA private key, 4096 bit long modulus ...............................................................++ .....++ e is 65537 (0x10001) [root@master200.yinzhengjie.org.cn ~]# [root@master200.yinzhengjie.org.cn ~]# ll /yinzhengjie/data/k8s/manifests/basic/secret/ total 8 -rw-r--r-- 1 root root 3243 Feb 12 02:07 mysql.key -rw-r--r-- 1 root root 278 Feb 12 01:27 mysql-pod.yaml [root@master200.yinzhengjie.org.cn ~]# [root@master200.yinzhengjie.org.cn ~]#

[root@master200.yinzhengjie.org.cn ~]# ll /yinzhengjie/data/k8s/manifests/basic/secret/ total 8 -rw-r--r-- 1 root root 3243 Feb 12 02:07 mysql.key -rw-r--r-- 1 root root 278 Feb 12 01:27 mysql-pod.yaml [root@master200.yinzhengjie.org.cn ~]# [root@master200.yinzhengjie.org.cn ~]# cd /yinzhengjie/data/k8s/manifests/basic/secret/ [root@master200.yinzhengjie.org.cn /yinzhengjie/data/k8s/manifests/basic/secret]# [root@master200.yinzhengjie.org.cn /yinzhengjie/data/k8s/manifests/basic/secret]# openssl req -new -x509 -key mysql.key -out mysql.crt -subj /C=CN/ST=Beijing/L=Beijing/O=Ops/CN=master200.yinzhengjie.org.cn -days 3650 [root@master200.yinzhengjie.org.cn /yinzhengjie/data/k8s/manifests/basic/secret]# [root@master200.yinzhengjie.org.cn /yinzhengjie/data/k8s/manifests/basic/secret]# ll total 12 -rw-r--r-- 1 root root 2009 Feb 12 02:10 mysql.crt -rw-r--r-- 1 root root 3243 Feb 12 02:07 mysql.key -rw-r--r-- 1 root root 278 Feb 12 01:27 mysql-pod.yaml [root@master200.yinzhengjie.org.cn /yinzhengjie/data/k8s/manifests/basic/secret]# [root@master200.yinzhengjie.org.cn /yinzhengjie/data/k8s/manifests/basic/secret]#

[root@master200.yinzhengjie.org.cn ~]# cat /yinzhengjie/data/k8s/manifests/basic/secret/mysql.crt -----BEGIN CERTIFICATE----- MIIFnzCCA4egAwIBAgIJAPwwKhWyxksIMA0GCSqGSIb3DQEBCwUAMGYxCzAJBgNV BAYTAkNOMRAwDgYDVQQIDAdCZWlqaW5nMRAwDgYDVQQHDAdCZWlqaW5nMQwwCgYD VQQKDANPcHMxJTAjBgNVBAMMHG1hc3RlcjIwMC55aW56aGVuZ2ppZS5vcmcuY24w HhcNMjAwMjExMTgxMDQyWhcNMzAwMjA4MTgxMDQyWjBmMQswCQYDVQQGEwJDTjEQ MA4GA1UECAwHQmVpamluZzEQMA4GA1UEBwwHQmVpamluZzEMMAoGA1UECgwDT3Bz MSUwIwYDVQQDDBxtYXN0ZXIyMDAueWluemhlbmdqaWUub3JnLmNuMIICIjANBgkq hkiG9w0BAQEFAAOCAg8AMIICCgKCAgEAtWxMDOMHXUn70wT+plCv9Lnty9oqzdxv DTPbDZjypCIN4kIczuXLRJMhnT1Xqikc3fE3WAAURKl0RQsZfoBk94lONgCfpp3/ 1D0LIOERUMEnnQ+WeNkuTp1iN9G1RYUhfygcskeO1SV44K1koNo2yagJhlEKqS7D mBVJk3jODQNQXoR13IAszL7FDk9hLAEmY/3v2/l486KmmGaX5jJ4c36LOewimHK8 NSFIOcRPJTMCFWncSryR9zsPbtqhChHDSyhUowbydaJicVzGPNFG15VJ9jdiuKza KQKemd3GWsbVDxMqApDViSnsERM3NthWDEXF+3giOvVhlSFClVMBT365MBAUSOQ+ CCZYBm1nI/JL9n7KnJFQc3xjKKiou2VEUfnznXqVgHMQtaZ9j0ATRmU5V3SyRSoD 00037vfMu8Luzpfqcfco5WcM1nzMwl6mOqBU3tx5C7VmTAYKpc9QxvquqXOtE+dy y6XQ9B/mtVe3QsCBB0+03ga6HUw+8Ibt4EXblPCdvcprbSpm6K84JWES8N8GzIms zAZe2pqwwjP3xKX1xu4LrKXbXL2SUUSl11+jS+b1QmvMQR1MMCjFKv9uAnaXnvzm 9dDrULd4kJTJIlxHNBxOtP+CO5coWFP0aTGuDkR/lhwEZ6edk0/+cFZ6tOEtF7nl fAkweFmMEssCAwEAAaNQME4wHQYDVR0OBBYEFPMKNre6vUYCmndVuaQKHW3bP0TN MB8GA1UdIwQYMBaAFPMKNre6vUYCmndVuaQKHW3bP0TNMAwGA1UdEwQFMAMBAf8w DQYJKoZIhvcNAQELBQADggIBAI9JxfIHZUMlo/LMzYQ70Fmz6F+fGBt9f8CtnLY8 jmok9KoJef9NWwL+7my+K+CuILeRyzkW7KgSAjxNIme/Cm55krhWB5PX9Gt5mSPZ cXl5GjLaaOTh36XQsBDhM0rf5j4VKkhxJDUZbp/QAseLEAwi/uGhb5lKvjjOLg3U KVMGSUYLCA8QFizspk2OG5YMT6JPevWVsh/two7BlWHoxgNwyvRB8BI9QCA2UuHb Onglgf+MmVVin6ZETMMsXytwD2faJGwOFdxYToJXmChCSehu5qpNOaFt7PHXVm27 mD+GnxEX9wU3eRK8J2jft5m1DiIW9/K55ayZF/dYUYGkByw2CpvmJh5MEpeBbyb/ QKi79F5J5jihbxpj03E6RBPCpSqTRanRqQnOMIfH3AA+uDYDDQsMDHdJGOicQqXr tDT2vEwRrpQ/MOSFo5JK33fp2jzaQvf3yBn5eOc4v624eD0IxR6V+kAAmQql8QWS RGV6HYO0mZLw49M4d/0ho76YgY9kRsZ5qiyim6npUT+MV3fCHtXM03eBeu5WSpFh ORhF6xgaWyq7r2xasGk5o5il194J/g8Nwa50iSScrO1ByEF48NQEAXckJZD8b4RG 9nHC17No4ZvyY4+tW7qRu5v5SjbkHrSa/g8riSYVwjRC9fdXg7bLgGll6GrrLwcP rEAp -----END CERTIFICATE----- [root@master200.yinzhengjie.org.cn ~]#

[root@master200.yinzhengjie.org.cn ~]# cat /yinzhengjie/data/k8s/manifests/basic/secret/mysql.key -----BEGIN RSA PRIVATE KEY----- MIIJKAIBAAKCAgEAtWxMDOMHXUn70wT+plCv9Lnty9oqzdxvDTPbDZjypCIN4kIc zuXLRJMhnT1Xqikc3fE3WAAURKl0RQsZfoBk94lONgCfpp3/1D0LIOERUMEnnQ+W eNkuTp1iN9G1RYUhfygcskeO1SV44K1koNo2yagJhlEKqS7DmBVJk3jODQNQXoR1 3IAszL7FDk9hLAEmY/3v2/l486KmmGaX5jJ4c36LOewimHK8NSFIOcRPJTMCFWnc SryR9zsPbtqhChHDSyhUowbydaJicVzGPNFG15VJ9jdiuKzaKQKemd3GWsbVDxMq ApDViSnsERM3NthWDEXF+3giOvVhlSFClVMBT365MBAUSOQ+CCZYBm1nI/JL9n7K nJFQc3xjKKiou2VEUfnznXqVgHMQtaZ9j0ATRmU5V3SyRSoD00037vfMu8Luzpfq cfco5WcM1nzMwl6mOqBU3tx5C7VmTAYKpc9QxvquqXOtE+dyy6XQ9B/mtVe3QsCB B0+03ga6HUw+8Ibt4EXblPCdvcprbSpm6K84JWES8N8GzImszAZe2pqwwjP3xKX1 xu4LrKXbXL2SUUSl11+jS+b1QmvMQR1MMCjFKv9uAnaXnvzm9dDrULd4kJTJIlxH NBxOtP+CO5coWFP0aTGuDkR/lhwEZ6edk0/+cFZ6tOEtF7nlfAkweFmMEssCAwEA AQKCAgEAra7Y+7lY8omCiRmOBIDYgsyBCBh7xAsVUalkO5dCK7niWsp6M+SwfZzx oEv6og+r8BoepqOkw7sKcZLXvFCE2KndczuTm/pE0dYC0l5Fqm7QUr96iYU5nM91 GQUtqjlywP4QwuhYqFuwZj/5RzjBHLs/KxRoxWDcpbszbfhIIxMaHPJot0kKGpVD p5h86ZjMPQv9VjV2AqCjJuGI6DtHLyJlfXVABXxKC/8p2wvBzVYQ15k56V6vyuUC uFibtT0eHtSkelKLSezEm8x6h/y9+mOUpB+P5kassHguiBVV8M/LZxwsqrong6Hb utkPkfT4I9WkXUM8Wf9ShWeLC9OkOu6j6mvQK/3PSZaL6vcQ/98lpz31gyl07i73 1JejLUIekbpd/5jrNYCYvRc2u91ulQrlZ+LGygnhqCY+s2hA/2YdWteFylJK/H1Q hsPIUQByOTvKLW0Uo9zag6dUnJouzDEYihWFyXWFNVzajQaNNARtDCaY12pfWL8B OpCwVnj8YU8g/tCm/qFvbeYIDFxCnqco3qTGH+deTkFEQgCnmie+XpXuOssonEsQ gRsKAgACJ/UHeyDt2r1NxUvXjTSRQ+fc0npZPpJY8FqG8MQsVSNsML/HF2sH3RGI o3D4AHcMD5J9IaTg2T1fw3p9E5SgwNFQIXdDyBQnRvOdQTKpA/kCggEBAN/GUX8H sgZ5ml5wwYO7ID6E6W5yR/4WrvnGihgWw7bBJ2px9LggbAvzBfEVvegHy9X8kfAu T/JyyzHJd2lLrXmum5rvXLaIJgigVdSW1UIhQXXiNzdctaqndTvOkECtI4LHINn5 Nzau0vSyDRPh1Wr3oXnE2BqaZmqzXYmr7FDpv4vGwRT8zhAVOUJQMDS9pyCJnbQs lqPL2e7E2+eH18+QQdEH28Azk9SBbMat23LkFQsFjjUMXbRGdDseymfIN+QJJzs0 nRGS/YrUI87aPlMEsQnvDyL4K/huUnSGrekWcm6Qze0l75ujlhG8SemhGqlJvKwU 6Gr6H0DRB5l+qT8CggEBAM+MpGQp8IF3aYSGHa9m27gYreOeP9O67xrBuA5rNaCI uWUHJ0flJHrWx+BQeFtRyKydDOe9nvc0pWoAca1bgavpoeYEv/M3QdisMfjR76NX vq7sngKpqymYRjwkdbF0Wc7JYTN67iDX+CUWGQm3grJA60X9CknOwNlMwYXnuvPb +hB0jQSM6Mon2ojeJ39E0EQvpkrC0dbzxPyRU8xZUxxfjZ5mxOV8s4KaXj9rL7db XnkxqH4CQfmNMPpk8zp7+HGHjbbhmBEKMhwTJ7jhAPuqwsF4lO2GRiNiP3FTZ4eJ dHodjHRXsgogw2B/7VzMkKPjdBx6KrsBErbNZnn4B3UCggEAaB8BAJh2D2k5mMPi ZwcE49I4Q3nNYb7wP6xPyRGek0SgsHjBo4MCgzTbCOhS6snl4HWa+iSycl9TiKDz fP0HhNzn7ll9zDjhaZYhGb/tDs4mhVFy28G5jeRJOkDNAisNoOZCtOmu9TS3V8AZ Ma0c/p6mdeBPpWE+UluPJGXomWWKCOG8KaXPw8/8SozBQWkVgKBHzvQIS8Kobt8O a1bb5ep7lWWQrIfTO0fVc0SmHXlfCTfWiXxthVpa7r9O8qdIykQwCu5aPzkj3BsF ZlRKN5qxPawMYPsUio3as/mOpiwZprSd/MBwEv008J+pzJl3rFlw/qjj1BL5w9D/ Nj6nRQKCAQB0hed9fLZUWXBaQNnFsh/FWcW2tw/qlVbMVNo67iHrgRdlCwEYsiMq /A63dzY7Ps1Fa97k9GadL2d2/czUoT1KAR8t/pitueYz+WkM4wCBWi/qEVoc8Jjx /1XfSjDxcftBx3nU5z1uHxJn7+IavHaaESyF3Ky8B2HqHdfAj/s8EdJxDp5lYZ8I cBuXH/JY14992Kqp6nrZDX8YtZawca3hjhv6RIRiuwIlXvlu7YSakqeVrzWDmUzl CEnpKmgL+7HeO1ZqyHkRiAHeFTsF5v0gThyNdl9Wgz45e11XCJZlV9yW+qPyZZHF ceN++BOROCA0guybWFNJLi8Nhn/0FjZJAoIBAFOtBAd5+2qbmURSsRZT4W1BMMGt F7zPI4ScoDHJOjVYBDjdfGjtO6ycCvh/6sH0wAyFH1WAN/tLQHVls1BrJLpAeHcM PUxdrMd8z60T2bYAPDHCeAH/7SGfnrlQVA6Ss8OxnBaEex9ossBDrz1lq8/HZ1xR VtlQ26yvDs/HjYQX+T+MdUCPSrgtGXGY7nbnAqZd2mE2ewlIr7/Wv57LHGg7biCB n8KLvylb28aRXUzPGvJZDO5ZMx948y2d527+mh7Gm7td/yM+Of7xxy+hlFWajvkj J99LVZPmfD4kr9ZnIN32HlNCTUU1PS1UcTFgBnLv2bZUOJiWBLRrECw4akg= -----END RSA PRIVATE KEY----- [root@master200.yinzhengjie.org.cn ~]#
2>.基于证书创建secret资源

[root@master200.yinzhengjie.org.cn ~]# kubectl create secret tls -h Create a TLS secret from the given public/private key pair. The public/private key pair must exist before hand. The public key certificate must be .PEM encoded and match the given private key. Examples: # Create a new TLS secret named tls-secret with the given key pair: kubectl create secret tls tls-secret --cert=path/to/tls.cert --key=path/to/tls.key Options: --allow-missing-template-keys=true: If true, ignore any errors in templates when a field or map key is missing in the template. Only applies to golang and jsonpath output formats. --append-hash=false: Append a hash of the secret to its name. --cert='': Path to PEM encoded public key certificate. --dry-run=false: If true, only print the object that would be sent, without sending it. --generator='secret-for-tls/v1': The name of the API generator to use. --key='': Path to private key associated with given certificate. -o, --output='': Output format. One of: json|yaml|name|go-template|go-template-file|template|templatefile|jsonpath|jsonpath-file. --save-config=false: If true, the configuration of current object will be saved in its annotation. Otherwise, the annotation will be unchanged. This flag is useful when you want to perform kubectl apply on this object in the future. --template='': Template string or path to template file to use when -o=go-template, -o=go-template-file. The template format is golang templates [http://golang.org/pkg/text/template/#pkg-overview]. --validate=true: If true, use a schema to validate the input before sending it Usage: kubectl create secret tls NAME --cert=path/to/cert/file --key=path/to/key/file [--dry-run] [options] Use "kubectl options" for a list of global command-line options (applies to all commands). [root@master200.yinzhengjie.org.cn ~]# [root@master200.yinzhengjie.org.cn ~]#

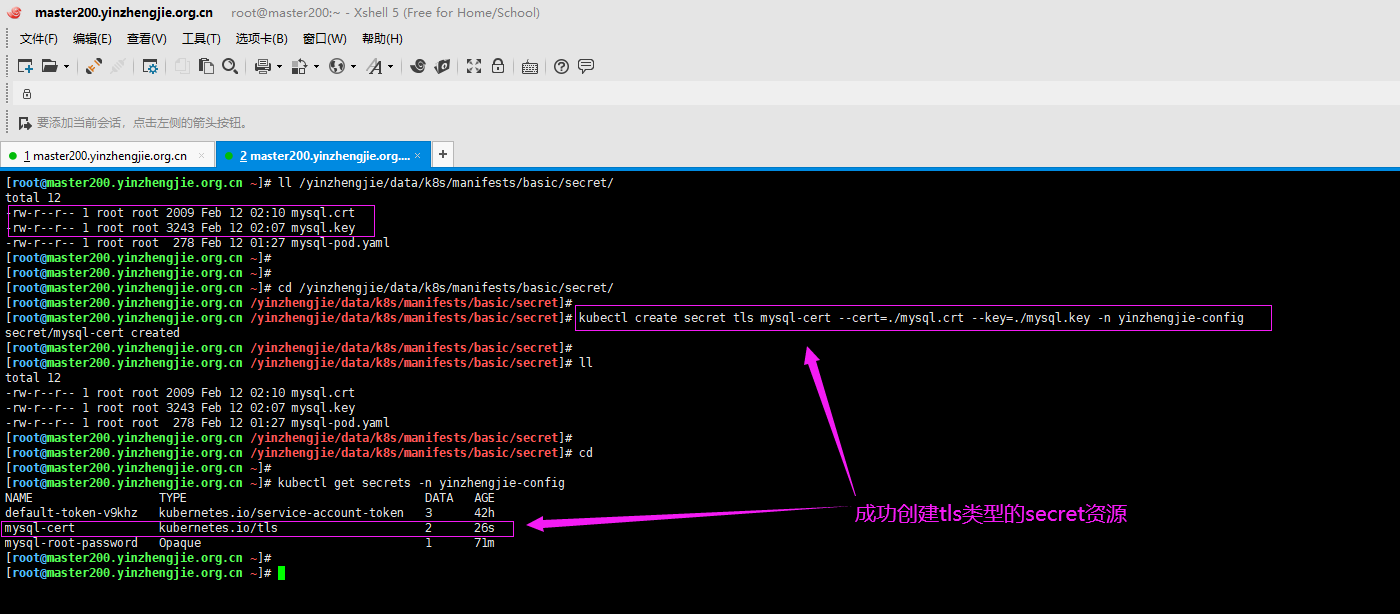
[root@master200.yinzhengjie.org.cn ~]# ll /yinzhengjie/data/k8s/manifests/basic/secret/ total 12 -rw-r--r-- 1 root root 2009 Feb 12 02:10 mysql.crt -rw-r--r-- 1 root root 3243 Feb 12 02:07 mysql.key -rw-r--r-- 1 root root 278 Feb 12 01:27 mysql-pod.yaml [root@master200.yinzhengjie.org.cn ~]# [root@master200.yinzhengjie.org.cn ~]# [root@master200.yinzhengjie.org.cn ~]# cd /yinzhengjie/data/k8s/manifests/basic/secret/ [root@master200.yinzhengjie.org.cn /yinzhengjie/data/k8s/manifests/basic/secret]# [root@master200.yinzhengjie.org.cn /yinzhengjie/data/k8s/manifests/basic/secret]# kubectl create secret tls mysql-cert --cert=./mysql.crt --key=./mysql.key -n yinzhengjie-config secret/mysql-cert created [root@master200.yinzhengjie.org.cn /yinzhengjie/data/k8s/manifests/basic/secret]# [root@master200.yinzhengjie.org.cn /yinzhengjie/data/k8s/manifests/basic/secret]# ll total 12 -rw-r--r-- 1 root root 2009 Feb 12 02:10 mysql.crt -rw-r--r-- 1 root root 3243 Feb 12 02:07 mysql.key -rw-r--r-- 1 root root 278 Feb 12 01:27 mysql-pod.yaml [root@master200.yinzhengjie.org.cn /yinzhengjie/data/k8s/manifests/basic/secret]# [root@master200.yinzhengjie.org.cn /yinzhengjie/data/k8s/manifests/basic/secret]# cd [root@master200.yinzhengjie.org.cn ~]# [root@master200.yinzhengjie.org.cn ~]# kubectl get secrets -n yinzhengjie-config NAME TYPE DATA AGE default-token-v9khz kubernetes.io/service-account-token 3 42h mysql-cert kubernetes.io/tls 2 26s mysql-root-password Opaque 1 71m [root@master200.yinzhengjie.org.cn ~]# [root@master200.yinzhengjie.org.cn ~]#
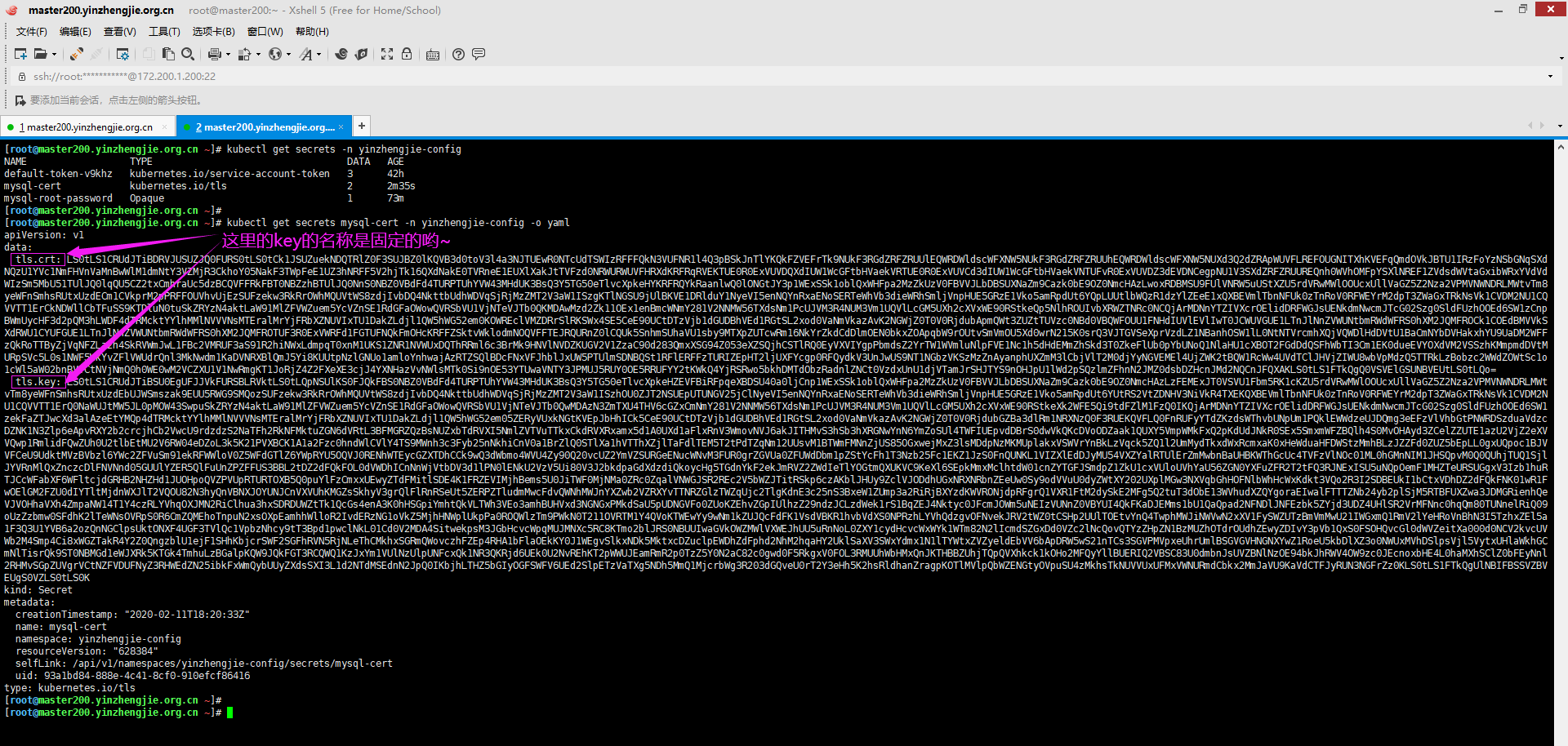
3>.查看tls类型的secrets资源(看到下图所示的信息,你就会发现使用资源清单的方式创建secret并不是明智之举哟~)

[root@master200.yinzhengjie.org.cn ~]# kubectl get secrets -n yinzhengjie-config NAME TYPE DATA AGE default-token-v9khz kubernetes.io/service-account-token 3 42h mysql-cert kubernetes.io/tls 2 2m35s mysql-root-password Opaque 1 73m [root@master200.yinzhengjie.org.cn ~]# [root@master200.yinzhengjie.org.cn ~]# kubectl get secrets mysql-cert -n yinzhengjie-config -o yaml apiVersion: v1 data: tls.crt: LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSUZuekNDQTRlZ0F3SUJBZ0lKQVB3d0toV3l4a3NJTUEwR0NTcUdTSWIzRFFFQkN3VUFNR1l4Q3pBSkJnTlYKQkFZVEFrTk9NUkF3RGdZRFZRUUlEQWRDWldscWFXNW5NUkF3RGdZRFZRUUhEQWRDWldscWFXNW5NUXd3Q2dZRApWUVFLREFOUGNITXhKVEFqQmdOVkJBTU1IRzFoYzNSbGNqSXd NQzU1YVc1NmFHVnVaMnBwWlM1dmNtY3VZMjR3CkhoY05NakF3TWpFeE1UZ3hNRFF5V2hjTk16QXdNakE0TVRneE1EUXlXakJtTVFzd0NRWURWUVFHRXdKRFRqRVEKTUE0R0ExVUVDQXdIUW1WcGFtbHVaekVRTUE0R0ExVUVCd3dIUW1WcGFtbHVaekVNTUFvR0ExVUVDZ3dEVDNCegpNU1V3SXdZRFZRUUREQnh0WVhOMFpYSXlNREF1ZVdsdWVtaGxibWRxYVdVdWIzSm5MbU51TUlJQ0lqQU5CZ2txCmhraUc5dzBCQVFFRkFBT0NBZzhBTUlJQ0NnS0NBZ0VBdFd4TURPTUhYVW43MHdUK3BsQ3Y5TG50eTlvcXpkeHYKRFRQYkRaanlwQ0lONGtJY3p1WExSSk1oblQxWHFpa2MzZkUzV0FBVVJLbDBSUXNaZm9Cazk0bE9OZ0NmcHAzLwoxRDBMSU9FUlVNRW5uUStXZU5rdVRwMWlOOUcxUllVaGZ5Z2Nza2VPMVNWNDRLMWtvTm8yeWFnSmhsRUtxUzdECm1CVkprM2pPRFFOUVhvUjEzSUFzekw3RkRrOWhMQUVtWS8zdjIvbDQ4NkttbUdhWDVqSjRjMzZMT2V3aW1ISzgKTlNGSU9jUlBKVE1DRlduY1NyeVI5enNQYnRxaENoSERTeWhVb3dieWRhSmljVnpHUE5GRzE1Vko5amRpdUt6YQpLUUtlbWQzR1dzYlZEeE1xQXBEVmlTbnNFUk0zTnRoV0RFWEYrM2dpT3ZWaGxTRkNsVk1CVDM2NU1CQVVTT1ErCkNDWllCbTFuSS9KTDluN0tuSkZRYzN4aktLaW91MlZFVWZuem5YcVZnSE1RdGFaOWowQVRSbVU1VjNTeVJTb0QKMDAwMzd2Zk11OEx1enBmcWNmY281V2NNMW56TXdsNm1PcUJVM3R4NUM3Vm1UQVlLcGM5UXh2cXVxWE90RStkeQp5NlhROUIvbXRWZTNRc0NCQjArMDNnYTZIVXcrOElidDRFWGJsUENkdmNwcmJTcG02Szg0SldFUzhOOEd6SW1zCnpBWmUycHF3d2pQM3hLWDF4dTRMcktYYlhMMlNVVVNsMTEralMrYjFRbXZNUVIxTU1DakZLdjl1QW5hWG52em0KOWREclVMZDRrSlRKSWx4SE5CeE90UCtDTzVjb1dGUDBhVEd1RGtSL2xod0VaNmVkazAvK2NGWjZ0T0V0RjdubApmQWt3ZUZtTUVzc0NBd0VBQWFOUU1FNHdIUVlEVlIwT0JCWUVGUE1LTnJlNnZVWUNtbmRWdWFRS0hXM2JQMFROCk1COEdBMVVkSXdRWU1CYUFGUE1LTnJlNnZVWUNtbmRWdWFRS0hXM2JQMFROTUF3R0ExVWRFd1FGTUFNQkFmOHcKRFFZSktvWklodmNOQVFFTEJRQURnZ0lCQUk5SnhmSUhaVU1sby9MTXpZUTcwRm16NkYrZkdCdDlmOEN0bkxZOApqbW9rOUtvSmVmOU5Xd0wrN215K0srQ3VJTGVSeXprVzdLZ1NBanhOSW1lL0NtNTVrcmhXQjVQWDlHdDVtU1BaCmNYbDVHakxhYU9UaDM2WFFzQkRoTTByZjVqNFZLa2h4SkRVWmJwL1FBc2VMRUF3aS91R2hiNWxLdmpqT0xnM1UKS1ZNR1NVWUxDQThRRml6c3BrMk9HNVlNVDZKUGV2V1ZzaC90d283QmxXSG94Z053eXZSQjhCSTlRQ0EyVXVIYgpPbmdsZ2YrTW1WVmluNlpFVE1Nc1h5dHdEMmZhSkd3T0ZkeFlUb0pYbUNoQ1NlaHU1cXBOT2FGdDdQSFhWbTI3Cm1EK0dueEVYOXdVM2VSSzhKMmpmdDVtMURpSVc5L0s1NWF5WkYvZFlVWUdrQnl3MkNwdm1KaDVNRXBlQmJ5Yi8KUUtpNzlGNUo1amloYnhwajAzRTZSQlBDcFNxVFJhblJxUW5PTUlmSDNBQSt1RFlERFFzTURIZEpHT2ljUXFYcgp0RFQydkV3UnJwUS9NT1NGbzVKSzMzZnAyanphUXZmM3lCbjVlT2M0djYyNGVEMEl4UjZWK2tBQW1RcWw4UVdTClJHVjZIWU8wbVpMdzQ5TTRkLzBobzc2WWdZOWtSc1o1cWl5aW02bnBVVCtNVjNmQ0h0WE0wM2VCZXU1V1NwRmgKT1JoRjZ4Z2FXeXE3cjJ4YXNHazVvNWlsMTk0Si9nOE53YTUwaVNTY3JPMUJ5RUY0OE5RRUFYY2tKWkQ4YjRSRwo5bkhDMTdObzRadnlZNCt0VzdxUnU1djVTamJrSHJTYS9nOHJpU1lWd2pSQzlmZFhnN2JMZ0dsbDZHcnJMd2NQCnJFQXAKLS0tLS1FTkQgQ0VSVElGSUNBVEUtLS0tLQo= tls.key: LS0tLS1CRUdJTiBSU0EgUFJJVkFURSBLRVktLS0tLQpNSUlKS0FJQkFBS0NBZ0VBdFd4TURPTUhYVW43MHdUK3BsQ3Y5TG50eTlvcXpkeHZEVFBiRFpqeXBDSU40a0ljCnp1WExSSk1oblQxWHFpa2MzZkUzV0FBVVJLbDBSUXNaZm9Cazk0bE9OZ0NmcHAzLzFEMExJT0VSVU1Fbm5RK1cKZU5rdVRwMWlOOUcxUllVaGZ5Z2Nza2VPMVNWNDRLMWt vTm8yeWFnSmhsRUtxUzdEbUJWSmszak9EUU5RWG9SMQozSUFzekw3RkRrOWhMQUVtWS8zdjIvbDQ4NkttbUdhWDVqSjRjMzZMT2V3aW1ISzhOU0ZJT2NSUEpUTUNGV25jClNyeVI5enNQYnRxaENoSERTeWhVb3dieWRhSmljVnpHUE5GRzE1Vko5amRpdUt6YUtRS2VtZDNHV3NiVkR4TXEKQXBEVmlTbnNFUk0zTnRoV0RFWEYrM2dpT3ZWaGxTRkNsVk1CVDM2NU1CQVVTT1ErQ0NaWUJtMW5JL0pMOW43SwpuSkZRYzN4aktLaW91MlZFVWZuem5YcVZnSE1RdGFaOWowQVRSbVU1VjNTeVJTb0QwMDAzN3ZmTXU4THV6cGZxCmNmY281V2NNMW56TXdsNm1PcUJVM3R4NUM3Vm1UQVlLcGM5UXh2cXVxWE90RStkeXk2WFE5Qi9tdFZlM1FzQ0IKQjArMDNnYTZIVXcrOElidDRFWGJsUENkdmNwcmJTcG02Szg0SldFUzhOOEd6SW1zekFaZTJwcXd3alAzeEtYMQp4dTRMcktYYlhMMlNVVVNsMTEralMrYjFRbXZNUVIxTU1DakZLdjl1QW5hWG52em05ZERyVUxkNGtKVEpJbHhICk5CeE90UCtDTzVjb1dGUDBhVEd1RGtSL2xod0VaNmVkazAvK2NGWjZ0T0V0RjdubGZBa3dlRm1NRXNzQ0F3RUEKQVFLQ0FnRUFyYTdZKzdsWThvbUNpUm1PQklEWWdzeUJDQmg3eEFzVlVhbGtPNWRDSzduaVdzcDZNK1N3Zlp6eApvRXY2b2crcjhCb2VwcU9rdzdzS2NaTFh2RkNFMktuZGN6dVRtL3BFMGRZQzBsNUZxbTdRVXI5NmlZVTVuTTkxCkdRVXRxamx5d1A0UXd1aFlxRnV3WmovNVJ6akJITHMvS3hSb3hXRGNwYnN6YmZoSUl4TWFIUEpvdDBrS0dwVkQKcDVoODZaak1QUXY5VmpWMkFxQ2pKdUdJNkR0SEx5SmxmWFZBQlh4S0MvOHAyd3ZCelZZUTE1azU2VjZ2eXVVQwp1RmlidFQwZUh0U2tlbEtMU2V6RW04eDZoL3k5K21PVXBCK1A1a2Fzc0hndWlCVlY4TS9MWnh3c3Fyb25nNkhiCnV0a1BrZlQ0STlXa1hVTThXZjlTaFdlTEM5T2tPdTZqNm12UUsvM1BTWmFMNnZjUS85OGxwejMxZ3lsMDdpNzMKMUplakxVSWVrYnBkLzVqck5ZQ1l2UmMydTkxdWxRcmxaK0xHeWduaHFDWStzMmhBLzJZZFd0ZUZ5bEpLL0gxUQpoc1BJVVFCeU9UdktMVzBVbzl6YWc2ZFVuSm91ekRFWWloV0Z5WFdGTlZ6YWpRYU5OQVJ0RENhWTEycGZXTDhCCk9wQ3dWbmo4WVU4Zy90Q20vcUZ2YmVZSURGeENucWNvM3FUR0grZGVUa0ZFUWdDbm1pZStYcFh1T3Nzb25Fc1EKZ1JzS0FnQUNKL1VIZXlEdDJyMU54VXZYalRTUlErZmMwbnBaUHBKWThGcUc4TVFzVlNOc01ML0hGMnNIM1JHSQpvM0Q0QUhjTUQ1SjlJYVRnMlQxZnczcDlFNVNnd05GUUlYZER5QlFuUnZPZFFUS3BBL2tDZ2dFQkFOL0dVWDhICnNnWjVtbDV3d1lPN0lENkU2VzV5Ui80V3J2bkdpaGdXdzdiQkoycHg5TGdnYkF2ekJmRVZ2ZWdIeTlYOGtmQXUKVC9KeXl6SEpkMmxMclhtdW01cnZYTGFJSmdpZ1ZkU1cxVUloUVhYaU56ZGN0YXFuZFR2T2tFQ3RJNExISU5uNQpOemF1MHZTeURSUGgxV3Izb1huRTJCcWFabXF6WFltcjdGRHB2NHZHd1JUOHpoQVZPVUpRTURTOXB5Q0puYlFzCmxxUEwyZTdFMitlSDE4K1FRZEVIMjhBems5U0JiTWF0MjNMa0ZRc0ZqalVNWGJSR2REc2V5bWZJTitRSkp6czAKblJHUy9ZclVJODdhUGxNRXNRbnZEeUw0Sy9odVVuU0dyZWtXY202UXplMGw3NXVqbGhHOFNlbWhHcWxKdkt3VQo2R3I2SDBEUkI1bCtxVDhDZ2dFQkFNK01wR1FwOElGM2FZU0dIYTltMjdnWXJlT2VQOU82N3hyQnVBNXJOYUNJCnVXVUhKMGZsSkhyV3grQlFlRnRSeUt5ZERPZTludmMwcFdvQWNhMWJnYXZwb2VZRXYvTTNRZGlzTWZqUjc2TlgKdnE3c25nS3BxeW1ZUmp3a2RiRjBXYzdKWVRONjdpRFgrQ1VXR1FtM2dySkE2MFg5Q2tuT3dObE13WVhudXZQYgoraEIwalFTTTZNb24yb2plSjM5RTBFUXZwa3JDMGRienhQeVJVOHhaVXh4ZmpaNW14T1Y4czRLYVhqOXJMN2RiClhua3hxSDRDUWZtTk1QcGs4enA3K0hHSGpiYmhtQkVLTWh3VEo3amhBUHVxd3NGNGxPMkdSaU5pUDNGVFo0ZUoKZEhvZGpIUlhzZ29ndzJCLzdWek1rS1BqZEJ4Nktyc0JFcmJOWm5uNEIzVUNnZ0VBYUI4QkFKaDJEMms1bU1QaQpad2NFNDlJNFEzbk5ZYjd3UDZ4UHlSR2VrMFNnc0hqQm80TUNnelRiQ09oUzZzbmw0SFdhK2lTeWNsOVRpS0R6CmZQMEhoTnpuN2xsOXpEamhhWlloR2IvdERzNG1oVkZ5MjhHNWplUkpPa0ROQWlzTm9PWkN0T211OVRTM1Y4QVoKTWEwYy9wNm1kZUJQcFdFK1VsdVBKR1hvbVdXS0NPRzhLYVhQdzgvOFNvekJRV2tWZ0tCSHp2UUlTOEtvYnQ4TwphMWJiNWVwN2xXV1FySWZUTzBmVmMwU21IWGxmQ1RmV2lYeHRoVnBhN3I5TzhxZEl5a1F3Q3U1YVB6a2ozQnNGClpsUktONXF4UGF3TVlQc1VpbzNhcy9tT3Bpd1pwclNkL01Cd0V2MDA4SitwekpsM3JGbHcvcWpqMUJMNXc5RC8KTmo2blJRS0NBUUIwaGVkOWZMWlVXWEJhUU5uRnNoL0ZXY1cydHcvcWxWYk1WTm82N2lIcmdSZGxDd0VZc2lNcQovQTYzZHpZN1BzMUZhOTdrOUdhZEwyZDIvY3pVb1QxS0FSOHQvcGl0dWVZeitXa000d0NCV2kvcUVWb2M4Smp4Ci8xWGZTakR4Y2Z0QngzblU1ejF1SHhKbjcrSWF2SGFhRVN5RjNLeThCMkhxSGRmQWovczhFZEp4RHA1bFlaOEkKY0J1WEgvSlkxNDk5MktxcDZuclpEWDhZdFphd2NhM2hqaHY2UklSaXV3SWxYdmx1N1lTYWtxZVZyeldEbVV6bApDRW5wS21nTCs3SGVPMVpxeUhrUmlBSGVGVHNGNXYwZ1RoeU5kbDlXZ3o0NWUxMVhDSlpsVjl5VytxUHlaWkhGCmNlTisrQk9ST0NBMGd1eWJXRk5KTGk4TmhuLzBGalpKQW9JQkFGT3RCQWQ1KzJxYm1VUlNzUlpUNFcxQk1NR3QKRjd6UEk0U2NvREhKT2pWWUJEamRmR2p0TzZ5Y0N2aC82c0gwd0F5RkgxV0FOL3RMUUhWbHMxQnJKTHBBZUhjTQpQVXhkck1kOHo2MFQyYllBUERIQ2VBSC83U0dmbnJsUVZBNlNzOE94bkJhRWV4OW9zc0JEcnoxbHE4L0haMXhSClZ0bFEyNnl2RHMvSGpZUVgrVCtNZFVDUFNyZ3RHWEdZN25ibkFxWmQybUUyZXdsSXI3L1d2NTdMSEdnN2JpQ0IKbjhLTHZ5bGIyOGFSWFV6UEd2SlpETzVaTXg5NDh5MmQ1MjcrbWg3R203dGQveU0rT2Y3eHh5K2hsRldhanZragpKOTlMVlpQbWZENGtyOVpuSU4zMkhsTkNUVVUxUFMxVWNURmdCbkx2MmJaVU9KaVdCTFJyRUN3NGFrZz0KLS0tLS1FTkQgUlNBIFBSSVZBVEUgS0VZLS0tLS0Kkind: Secret metadata: creationTimestamp: "2020-02-11T18:20:33Z" name: mysql-cert namespace: yinzhengjie-config resourceVersion: "628384" selfLink: /api/v1/namespaces/yinzhengjie-config/secrets/mysql-cert uid: 93a1bd84-888e-4c41-8cf0-910efcf86416 type: kubernetes.io/tls [root@master200.yinzhengjie.org.cn ~]# [root@master200.yinzhengjie.org.cn ~]#
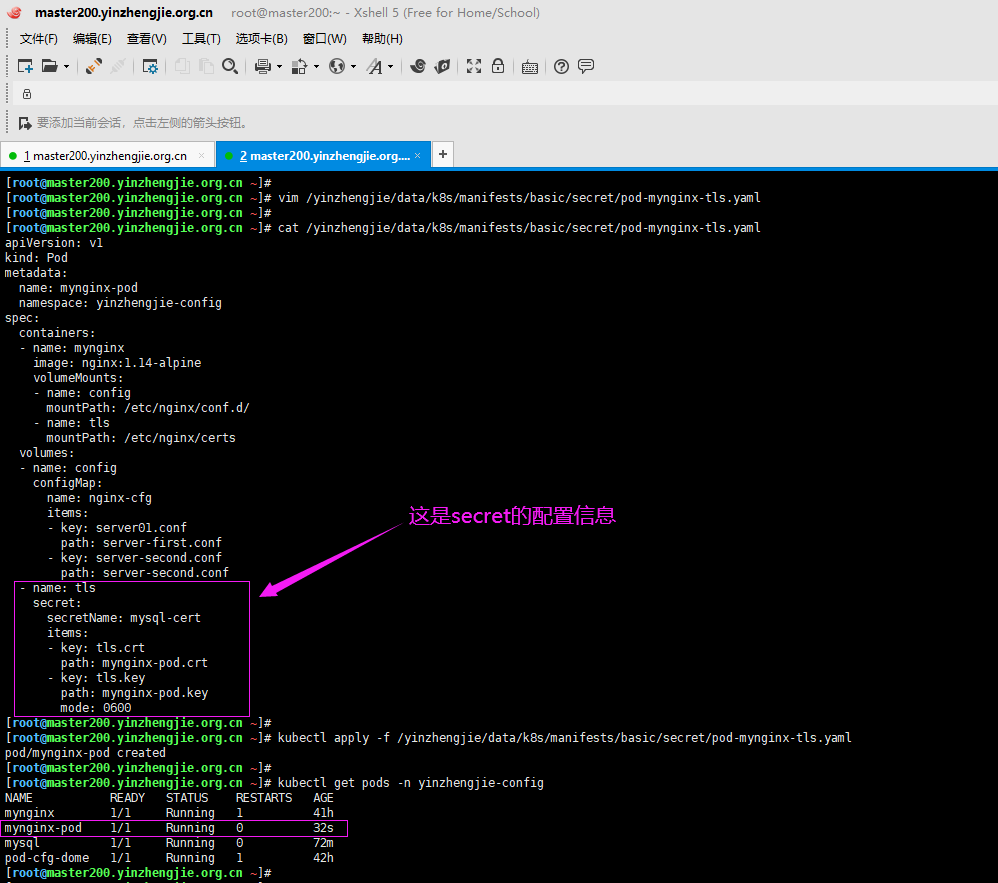
4>.创建nginx的配置文件

[root@master200.yinzhengjie.org.cn ~]# ll /yinzhengjie/data/k8s/manifests/basic/secret/ total 24 -rw-r--r-- 1 root root 2009 Feb 12 02:10 mysql.crt -rw-r--r-- 1 root root 3243 Feb 12 02:07 mysql.key -rw-r--r-- 1 root root 278 Feb 12 01:27 mysql-pod.yaml -rw-r--r-- 1 root root 668 Feb 12 02:38 pod-mynginx-tls.yaml -rw-r--r-- 1 root root 116 Feb 12 02:38 server01.conf -rw-r--r-- 1 root root 122 Feb 12 02:38 server02.conf [root@master200.yinzhengjie.org.cn ~]# [root@master200.yinzhengjie.org.cn ~]# cat /yinzhengjie/data/k8s/manifests/basic/secret/server01.conf server { server_name master.yinzhengjie.org.cn; listen 80; location / { root "/yinzhengjie/master/html/"; } } [root@master200.yinzhengjie.org.cn ~]#

[root@master200.yinzhengjie.org.cn ~]# ll /yinzhengjie/data/k8s/manifests/basic/secret/ total 24 -rw-r--r-- 1 root root 2009 Feb 12 02:10 mysql.crt -rw-r--r-- 1 root root 3243 Feb 12 02:07 mysql.key -rw-r--r-- 1 root root 278 Feb 12 01:27 mysql-pod.yaml -rw-r--r-- 1 root root 668 Feb 12 02:38 pod-mynginx-tls.yaml -rw-r--r-- 1 root root 116 Feb 12 02:38 server01.conf -rw-r--r-- 1 root root 122 Feb 12 02:38 server02.conf [root@master200.yinzhengjie.org.cn ~]# [root@master200.yinzhengjie.org.cn ~]# cat /yinzhengjie/data/k8s/manifests/basic/secret/server02.conf server { server_name master200.yinzhengjie.org.cn; listen 80; location / { root "/yinzhengjie/master200/html/"; } } [root@master200.yinzhengjie.org.cn ~]# [root@master200.yinzhengjie.org.cn ~]#
5>.编辑Pod的配置文件并创建Pod

[root@master200.yinzhengjie.org.cn ~]# ll /yinzhengjie/data/k8s/manifests/basic/secret/ total 24 -rw-r--r-- 1 root root 2009 Feb 12 02:10 mysql.crt -rw-r--r-- 1 root root 3243 Feb 12 02:07 mysql.key -rw-r--r-- 1 root root 278 Feb 12 01:27 mysql-pod.yaml -rw-r--r-- 1 root root 668 Feb 12 02:38 pod-mynginx-tls.yaml -rw-r--r-- 1 root root 116 Feb 12 02:38 server01.conf -rw-r--r-- 1 root root 122 Feb 12 02:38 server02.conf [root@master200.yinzhengjie.org.cn ~]# [root@master200.yinzhengjie.org.cn ~]# cat /yinzhengjie/data/k8s/manifests/basic/secret/pod-mynginx-tls.yaml apiVersion: v1 kind: Pod metadata: name: mynginx-pod namespace: yinzhengjie-config spec: containers: - name: mynginx image: nginx:1.14-alpine volumeMounts: - name: config mountPath: /etc/nginx/conf.d/ - name: tls mountPath: /etc/nginx/certs volumes: - name: config configMap: name: nginx-cfg items: - key: server01.conf path: server-first.conf - key: server-second.conf path: server-second.conf - name: tls secret: secretName: mysql-cert items: - key: tls.crt path: mynginx-pod.crt - key: tls.key path: mynginx-pod.key mode: 0600 [root@master200.yinzhengjie.org.cn ~]# [root@master200.yinzhengjie.org.cn ~]#

[root@master200.yinzhengjie.org.cn ~]# kubectl apply -f /yinzhengjie/data/k8s/manifests/basic/secret/pod-mynginx-tls.yaml pod/mynginx-pod created [root@master200.yinzhengjie.org.cn ~]# [root@master200.yinzhengjie.org.cn ~]# kubectl get pods -n yinzhengjie-config NAME READY STATUS RESTARTS AGE mynginx 1/1 Running 1 41h mynginx-pod 1/1 Running 0 32s mysql 1/1 Running 0 72m pod-cfg-dome 1/1 Running 1 42h [root@master200.yinzhengjie.org.cn ~]#
6>.连接Pod中的nginx容器验证配置是否生效

[root@master200.yinzhengjie.org.cn ~]# kubectl get pods -n yinzhengjie-config NAME READY STATUS RESTARTS AGE mynginx 1/1 Running 1 41h mynginx-pod 1/1 Running 0 32s mysql 1/1 Running 0 72m pod-cfg-dome 1/1 Running 1 42h [root@master200.yinzhengjie.org.cn ~]# [root@master200.yinzhengjie.org.cn ~]# [root@master200.yinzhengjie.org.cn ~]# kubectl exec -it mynginx-pod -n yinzhengjie-config -- /bin/sh / # / # ls /etc/nginx/ certs fastcgi.conf fastcgi_params koi-utf mime.types modules nginx.conf.default scgi_params.default uwsgi_params.default conf.d fastcgi.conf.default fastcgi_params.default koi-win mime.types.default nginx.conf scgi_params uwsgi_params win-utf / # / # ls -l /etc/nginx/certs/ total 0 lrwxrwxrwx 1 root root 22 Feb 11 18:38 mynginx-pod.crt -> ..data/mynginx-pod.crt lrwxrwxrwx 1 root root 22 Feb 11 18:38 mynginx-pod.key -> ..data/mynginx-pod.key / # / # cat /etc/nginx/certs/mynginx-pod.crt -----BEGIN CERTIFICATE----- MIIFnzCCA4egAwIBAgIJAPwwKhWyxksIMA0GCSqGSIb3DQEBCwUAMGYxCzAJBgNV BAYTAkNOMRAwDgYDVQQIDAdCZWlqaW5nMRAwDgYDVQQHDAdCZWlqaW5nMQwwCgYD VQQKDANPcHMxJTAjBgNVBAMMHG1hc3RlcjIwMC55aW56aGVuZ2ppZS5vcmcuY24w HhcNMjAwMjExMTgxMDQyWhcNMzAwMjA4MTgxMDQyWjBmMQswCQYDVQQGEwJDTjEQ MA4GA1UECAwHQmVpamluZzEQMA4GA1UEBwwHQmVpamluZzEMMAoGA1UECgwDT3Bz MSUwIwYDVQQDDBxtYXN0ZXIyMDAueWluemhlbmdqaWUub3JnLmNuMIICIjANBgkq hkiG9w0BAQEFAAOCAg8AMIICCgKCAgEAtWxMDOMHXUn70wT+plCv9Lnty9oqzdxv DTPbDZjypCIN4kIczuXLRJMhnT1Xqikc3fE3WAAURKl0RQsZfoBk94lONgCfpp3/ 1D0LIOERUMEnnQ+WeNkuTp1iN9G1RYUhfygcskeO1SV44K1koNo2yagJhlEKqS7D mBVJk3jODQNQXoR13IAszL7FDk9hLAEmY/3v2/l486KmmGaX5jJ4c36LOewimHK8 NSFIOcRPJTMCFWncSryR9zsPbtqhChHDSyhUowbydaJicVzGPNFG15VJ9jdiuKza KQKemd3GWsbVDxMqApDViSnsERM3NthWDEXF+3giOvVhlSFClVMBT365MBAUSOQ+ CCZYBm1nI/JL9n7KnJFQc3xjKKiou2VEUfnznXqVgHMQtaZ9j0ATRmU5V3SyRSoD 00037vfMu8Luzpfqcfco5WcM1nzMwl6mOqBU3tx5C7VmTAYKpc9QxvquqXOtE+dy y6XQ9B/mtVe3QsCBB0+03ga6HUw+8Ibt4EXblPCdvcprbSpm6K84JWES8N8GzIms zAZe2pqwwjP3xKX1xu4LrKXbXL2SUUSl11+jS+b1QmvMQR1MMCjFKv9uAnaXnvzm 9dDrULd4kJTJIlxHNBxOtP+CO5coWFP0aTGuDkR/lhwEZ6edk0/+cFZ6tOEtF7nl fAkweFmMEssCAwEAAaNQME4wHQYDVR0OBBYEFPMKNre6vUYCmndVuaQKHW3bP0TN MB8GA1UdIwQYMBaAFPMKNre6vUYCmndVuaQKHW3bP0TNMAwGA1UdEwQFMAMBAf8w DQYJKoZIhvcNAQELBQADggIBAI9JxfIHZUMlo/LMzYQ70Fmz6F+fGBt9f8CtnLY8 jmok9KoJef9NWwL+7my+K+CuILeRyzkW7KgSAjxNIme/Cm55krhWB5PX9Gt5mSPZ cXl5GjLaaOTh36XQsBDhM0rf5j4VKkhxJDUZbp/QAseLEAwi/uGhb5lKvjjOLg3U KVMGSUYLCA8QFizspk2OG5YMT6JPevWVsh/two7BlWHoxgNwyvRB8BI9QCA2UuHb Onglgf+MmVVin6ZETMMsXytwD2faJGwOFdxYToJXmChCSehu5qpNOaFt7PHXVm27 mD+GnxEX9wU3eRK8J2jft5m1DiIW9/K55ayZF/dYUYGkByw2CpvmJh5MEpeBbyb/ QKi79F5J5jihbxpj03E6RBPCpSqTRanRqQnOMIfH3AA+uDYDDQsMDHdJGOicQqXr tDT2vEwRrpQ/MOSFo5JK33fp2jzaQvf3yBn5eOc4v624eD0IxR6V+kAAmQql8QWS RGV6HYO0mZLw49M4d/0ho76YgY9kRsZ5qiyim6npUT+MV3fCHtXM03eBeu5WSpFh ORhF6xgaWyq7r2xasGk5o5il194J/g8Nwa50iSScrO1ByEF48NQEAXckJZD8b4RG 9nHC17No4ZvyY4+tW7qRu5v5SjbkHrSa/g8riSYVwjRC9fdXg7bLgGll6GrrLwcP rEAp -----END CERTIFICATE----- / # / # cat /etc/nginx/certs/mynginx-pod.key -----BEGIN RSA PRIVATE KEY----- MIIJKAIBAAKCAgEAtWxMDOMHXUn70wT+plCv9Lnty9oqzdxvDTPbDZjypCIN4kIc zuXLRJMhnT1Xqikc3fE3WAAURKl0RQsZfoBk94lONgCfpp3/1D0LIOERUMEnnQ+W eNkuTp1iN9G1RYUhfygcskeO1SV44K1koNo2yagJhlEKqS7DmBVJk3jODQNQXoR1 3IAszL7FDk9hLAEmY/3v2/l486KmmGaX5jJ4c36LOewimHK8NSFIOcRPJTMCFWnc SryR9zsPbtqhChHDSyhUowbydaJicVzGPNFG15VJ9jdiuKzaKQKemd3GWsbVDxMq ApDViSnsERM3NthWDEXF+3giOvVhlSFClVMBT365MBAUSOQ+CCZYBm1nI/JL9n7K nJFQc3xjKKiou2VEUfnznXqVgHMQtaZ9j0ATRmU5V3SyRSoD00037vfMu8Luzpfq cfco5WcM1nzMwl6mOqBU3tx5C7VmTAYKpc9QxvquqXOtE+dyy6XQ9B/mtVe3QsCB B0+03ga6HUw+8Ibt4EXblPCdvcprbSpm6K84JWES8N8GzImszAZe2pqwwjP3xKX1 xu4LrKXbXL2SUUSl11+jS+b1QmvMQR1MMCjFKv9uAnaXnvzm9dDrULd4kJTJIlxH NBxOtP+CO5coWFP0aTGuDkR/lhwEZ6edk0/+cFZ6tOEtF7nlfAkweFmMEssCAwEA AQKCAgEAra7Y+7lY8omCiRmOBIDYgsyBCBh7xAsVUalkO5dCK7niWsp6M+SwfZzx oEv6og+r8BoepqOkw7sKcZLXvFCE2KndczuTm/pE0dYC0l5Fqm7QUr96iYU5nM91 GQUtqjlywP4QwuhYqFuwZj/5RzjBHLs/KxRoxWDcpbszbfhIIxMaHPJot0kKGpVD p5h86ZjMPQv9VjV2AqCjJuGI6DtHLyJlfXVABXxKC/8p2wvBzVYQ15k56V6vyuUC uFibtT0eHtSkelKLSezEm8x6h/y9+mOUpB+P5kassHguiBVV8M/LZxwsqrong6Hb utkPkfT4I9WkXUM8Wf9ShWeLC9OkOu6j6mvQK/3PSZaL6vcQ/98lpz31gyl07i73 1JejLUIekbpd/5jrNYCYvRc2u91ulQrlZ+LGygnhqCY+s2hA/2YdWteFylJK/H1Q hsPIUQByOTvKLW0Uo9zag6dUnJouzDEYihWFyXWFNVzajQaNNARtDCaY12pfWL8B OpCwVnj8YU8g/tCm/qFvbeYIDFxCnqco3qTGH+deTkFEQgCnmie+XpXuOssonEsQ gRsKAgACJ/UHeyDt2r1NxUvXjTSRQ+fc0npZPpJY8FqG8MQsVSNsML/HF2sH3RGI o3D4AHcMD5J9IaTg2T1fw3p9E5SgwNFQIXdDyBQnRvOdQTKpA/kCggEBAN/GUX8H sgZ5ml5wwYO7ID6E6W5yR/4WrvnGihgWw7bBJ2px9LggbAvzBfEVvegHy9X8kfAu T/JyyzHJd2lLrXmum5rvXLaIJgigVdSW1UIhQXXiNzdctaqndTvOkECtI4LHINn5 Nzau0vSyDRPh1Wr3oXnE2BqaZmqzXYmr7FDpv4vGwRT8zhAVOUJQMDS9pyCJnbQs lqPL2e7E2+eH18+QQdEH28Azk9SBbMat23LkFQsFjjUMXbRGdDseymfIN+QJJzs0 nRGS/YrUI87aPlMEsQnvDyL4K/huUnSGrekWcm6Qze0l75ujlhG8SemhGqlJvKwU 6Gr6H0DRB5l+qT8CggEBAM+MpGQp8IF3aYSGHa9m27gYreOeP9O67xrBuA5rNaCI uWUHJ0flJHrWx+BQeFtRyKydDOe9nvc0pWoAca1bgavpoeYEv/M3QdisMfjR76NX vq7sngKpqymYRjwkdbF0Wc7JYTN67iDX+CUWGQm3grJA60X9CknOwNlMwYXnuvPb +hB0jQSM6Mon2ojeJ39E0EQvpkrC0dbzxPyRU8xZUxxfjZ5mxOV8s4KaXj9rL7db XnkxqH4CQfmNMPpk8zp7+HGHjbbhmBEKMhwTJ7jhAPuqwsF4lO2GRiNiP3FTZ4eJ dHodjHRXsgogw2B/7VzMkKPjdBx6KrsBErbNZnn4B3UCggEAaB8BAJh2D2k5mMPi ZwcE49I4Q3nNYb7wP6xPyRGek0SgsHjBo4MCgzTbCOhS6snl4HWa+iSycl9TiKDz fP0HhNzn7ll9zDjhaZYhGb/tDs4mhVFy28G5jeRJOkDNAisNoOZCtOmu9TS3V8AZ Ma0c/p6mdeBPpWE+UluPJGXomWWKCOG8KaXPw8/8SozBQWkVgKBHzvQIS8Kobt8O a1bb5ep7lWWQrIfTO0fVc0SmHXlfCTfWiXxthVpa7r9O8qdIykQwCu5aPzkj3BsF ZlRKN5qxPawMYPsUio3as/mOpiwZprSd/MBwEv008J+pzJl3rFlw/qjj1BL5w9D/ Nj6nRQKCAQB0hed9fLZUWXBaQNnFsh/FWcW2tw/qlVbMVNo67iHrgRdlCwEYsiMq /A63dzY7Ps1Fa97k9GadL2d2/czUoT1KAR8t/pitueYz+WkM4wCBWi/qEVoc8Jjx /1XfSjDxcftBx3nU5z1uHxJn7+IavHaaESyF3Ky8B2HqHdfAj/s8EdJxDp5lYZ8I cBuXH/JY14992Kqp6nrZDX8YtZawca3hjhv6RIRiuwIlXvlu7YSakqeVrzWDmUzl CEnpKmgL+7HeO1ZqyHkRiAHeFTsF5v0gThyNdl9Wgz45e11XCJZlV9yW+qPyZZHF ceN++BOROCA0guybWFNJLi8Nhn/0FjZJAoIBAFOtBAd5+2qbmURSsRZT4W1BMMGt F7zPI4ScoDHJOjVYBDjdfGjtO6ycCvh/6sH0wAyFH1WAN/tLQHVls1BrJLpAeHcM PUxdrMd8z60T2bYAPDHCeAH/7SGfnrlQVA6Ss8OxnBaEex9ossBDrz1lq8/HZ1xR VtlQ26yvDs/HjYQX+T+MdUCPSrgtGXGY7nbnAqZd2mE2ewlIr7/Wv57LHGg7biCB n8KLvylb28aRXUzPGvJZDO5ZMx948y2d527+mh7Gm7td/yM+Of7xxy+hlFWajvkj J99LVZPmfD4kr9ZnIN32HlNCTUU1PS1UcTFgBnLv2bZUOJiWBLRrECw4akg= -----END RSA PRIVATE KEY----- / # / #

三.创建镜像仓库类型的secret
[root@master200.yinzhengjie.org.cn ~]# kubectl create secret docker-registry -h Create a new secret for use with Docker registries. Dockercfg secrets are used to authenticate against Docker registries. When using the Docker command line to push images, you can authenticate to a given registry by running: '$ docker login DOCKER_REGISTRY_SERVER --username=DOCKER_USER --password=DOCKER_PASSWORD --email=DOCKER_EMAIL'. That produces a ~/.dockercfg file that is used by subsequent 'docker push' and 'docker pull' commands to authenticate to the registry. The email address is optional. When creating applications, you may have a Docker registry that requires authentication. In order for the nodes to pull images on your behalf, they have to have the credentials. You can provide this information by creating a dockercfg secret and attaching it to your service account. Examples: # If you don't already have a .dockercfg file, you can create a dockercfg secret directly by using: kubectl create secret docker-registry my-secret --docker-server=DOCKER_REGISTRY_SERVER --docker-username=DOCKER_USER --docker-password=DOCKER_PASSWORD --docker-email=DOCKER_EMAIL Options: --allow-missing-template-keys=true: If true, ignore any errors in templates when a field or map key is missing in the template. Only applies to golang and jsonpath output formats. --append-hash=false: Append a hash of the secret to its name. --docker-email='': Email for Docker registry --docker-password='': Password for Docker registry authentication --docker-server='https://index.docker.io/v1/': Server location for Docker registry --docker-username='': Username for Docker registry authentication --dry-run=false: If true, only print the object that would be sent, without sending it. --from-file=[]: Key files can be specified using their file path, in which case a default name will be given to them, or optionally with a name and file path, in which case the given name will be used. Specifying a directory will iterate each named file in the directory that is a valid secret key. --generator='secret-for-docker-registry/v1': The name of the API generator to use. -o, --output='': Output format. One of: json|yaml|name|go-template|go-template-file|template|templatefile|jsonpath|jsonpath-file. --save-config=false: If true, the configuration of current object will be saved in its annotation. Otherwise, the annotation will be unchanged. This flag is useful when you want to perform kubectl apply on this object in the future. --template='': Template string or path to template file to use when -o=go-template, -o=go-template-file. The template format is golang templates [http://golang.org/pkg/text/template/#pkg-overview]. --validate=true: If true, use a schema to validate the input before sending it Usage: kubectl create secret docker-registry NAME --docker-username=user --docker-password=password --docker-email=email [--docker-server=string] [--from-literal=key1=value1] [--dry-run] [options] Use "kubectl options" for a list of global command-line options (applies to all commands). [root@master200.yinzhengjie.org.cn ~]# [root@master200.yinzhengjie.org.cn ~]#
