Windbg有很多命令和命令变体,因此有时您可能会忘记其中的一些命令,比如当您需要挖掘调用堆栈以提取更多信息时。或者您可能记得获取调用堆栈详细信息的命令,但您需要确保获得整个堆栈。或者,您可能需要一种快速挖掘堆栈的方法,首先从帧中获取信息,然后从局部变量获取信息,而无需花费太多时间键入命令或使用箭头键。
如果你在下面场景中看到你自己需要的,这个脚本就是为你准备的!
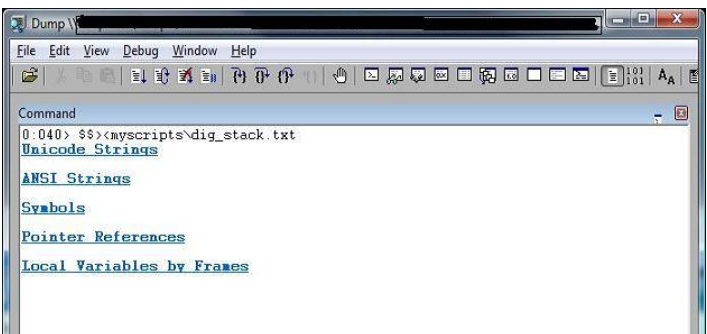
此脚本使您能够从调用堆栈快速获取以下信息:
- ANSI字符串。
- Unicode字符串。
- 符号。
- 指针引用。
- 帧局部变量。(需要专用符号)
界面非常简单,可能不太漂亮。下面是两个截图,让您了解:
Source code - DIG_STACK.TXT:
$$
$$ =============================================================================
$$ Dig information from the current call stack:
$$ - Unicode Strings
$$ - ANSI Strings
$$ - Symbols
$$ - Pointer references
$$ - Local variables by frames
$$
$$ Compatibility: Win32, should work on Win64.
$$
$$ Usage: $$>< to run the script.
$$
$$ If necessary change the filename below to include your path and filename.
$$ By default it uses the WinDbg path and the default file name is DIG_STACK.TXT
$$
$$ Roberto Alexis Farah
$$ Blog: http://blogs.msdn.com/debuggingtoolbox/
$$
$$ All my scripts are provided "AS IS" with no warranties, and confer no rights.
$$ =============================================================================
$$
.block
{
as ${/v:ScriptName} MYSCRIPTS\DIG_STACK.txt
}
.block
{
.printf /D "<link cmd="dpu @$csp poi(@$teb+0x4);ad ${/v:ScriptName}; $$><${ScriptName}"><b>Unicode Strings</b></link>
"
.printf /D "<link cmd="dpa @$csp poi(@$teb+0x4);ad ${/v:ScriptName}; $$><${ScriptName}"><b>ANSI Strings</b></link>
"
.printf /D "<link cmd="dps @$csp poi(@$teb+0x4);ad ${/v:ScriptName}; $$><${ScriptName}"><b>Symbols</b></link>
"
.printf /D "<link cmd="dpp @$csp poi(@$teb+0x4);ad ${/v:ScriptName}; $$><${ScriptName}"><b>Pointer References</b></link>
"
.printf /D "<link cmd="kpM 2000;ad ${/v:ScriptName}; $$><${ScriptName}"><b>Local Variables by Frames</b></link>
"
}
$$ ===========================================================================