1、we know the kali linux desktop environmet can also be costomized ,Desktop environmet can use GNOME(default) ,KDE (K Desktop Environmet) ,and LXDE(Loghtweight x11 Desktop Environmet)
we set command under windows: nbtstat -A [ip address] .we will get the NetBIOS remote Macine Name Tables
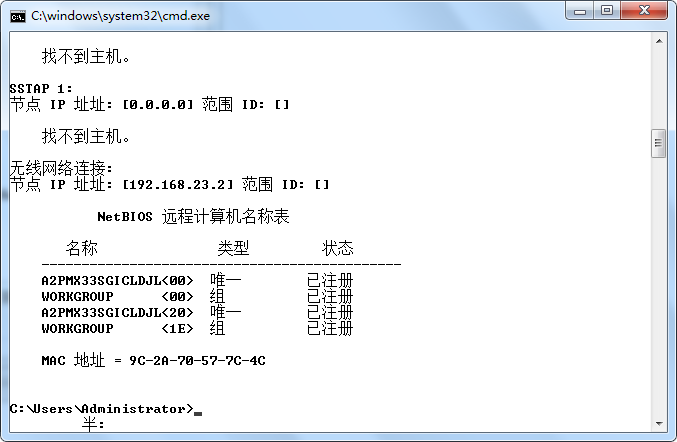
as we see in the picture ,if you do have a hex code <20> then you may have cause for concern now i will explain
if show code of <20> means you have file and printer sharing turned on ., aditional we cna use the command : net share to show the sharing file
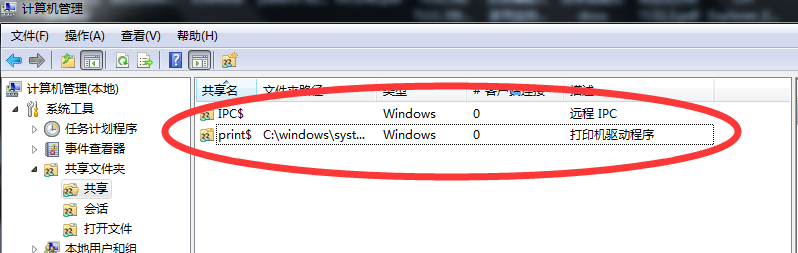

2、OK let we san on the local computer who sharing the file ,we can use the command : net view [ip_address]
then we use the command :net use [ip_address] get the touch the victim computer
above all,this attack was called Netbios attack ,if you want to improved the security closed the sharing
3、 we nest to see the Trojans
for example: Netbus and SubSeven
how we can installl a Trojans file in another computer .we can use the joiner utility will combine the two files together and output one executable file call nice name executed file
another way to spread the Trojans by the Email and Unsafe web Sites and IRC(Internet Relay Chat 因特网中继聊天)、 Chat Sites
4、acceptable file
there is no reasno for any files to be sent to you in any of the above formats if they are text douments ,there is no reason a file should have a double extension ,such files you shoud ever receive them should be treated with suspicion .
5、who are Hackers
A port scanner is a handy tool that scans a computer lookinh for active ports ,with this utility ,a potential hacker can figure out what services are acilable on the target computer form the responses the port scanner receives take a look at the list for reference
for example start scan the target Host: www.shutongyaming.com.cn
we looked the Sub Seven Trojan:
the Sub Seven Trojan has many features and capabilities ,it is in my opinion by far the most advance Trojan I hace seen Take a look at some of the features of SubSeven
- address book
- WWP Page Retrierve Get Windows CD-KEY update vicitim from URL ICQ takeover FTP root floder
- retrieve dial-up passwords along with phone number and usernames prot redirect IRCbot for a list of commands
- UIIn2IP eomte IP Scanner
6、SQL injection Question
While performing web application and penetration testing following scenario is very command and hides potential exploitable SQL injection scenario.
- We have SQL injection point but it is not throwing any error messages out as part of its response,Applicationg is sending customized erroe page ehich is not revealing any signature bu which we can deduce potential SQL flaw
- knowing SQL injectiong potin or loophole in web application xp_cmdshell seems to be worKing,but we can't say is it working or not since it doesn't return any meaningful signature tthis is blind xp_cmdShell
- FireWall don't allow outbound traffic so can't do ftp tftp ping etc from the box to the internet bu which you can confirm execution of the command on the target system
- we don't know the actual path to path to webroot so can't copy file to location whic can be accessed over Http or Https later to confirm the execution of the command
- if we know path to webroot adn directory structure but can't find execute permission on it so can't copy cmd.exe or any other binary and execute over HTTP/HTTPS