1,基本概念
- 前几章部署了harbor和ldap,本节将部署harbor使用openLDAP验证,部署方式与之前相同,只是改了adminserver-cm.yaml的AUTH_MODE: "ldap_auth"。另外harbor配置ldap登录非必须,按需。
2,部署 harbor-helm-ldap
2.1 下载项目
git clone https://github.com/xiaoqshuo/k8s-cluster.git
[root@k8s-master01 harbor-helm-ldap]# pwd
/opt/k8s-cluster/harbor-helm-ldap
[root@k8s-master01 harbor-helm-ldap]# ls
Chart.yaml CONTRIBUTING.md LICENSE README.md requirements.yaml templates values.yaml
2.2 部署服务
helm install --name hb-ldap . --set externalDomain=harbor.k8s.net --wait --timeout 1500 --debug --namespace harbor
[root@k8s-master01 harbor-helm-ldap]# helm install --name hb-ldap . --set externalDomain=harbor.k8s.net --wait --timeout 1500 --debug --namespace harbor
[debug] Created tunnel using local port: '41715'
[debug] SERVER: "127.0.0.1:41715"
[debug] Original chart version: ""
[debug] CHART PATH: /opt/k8s-cluster/harbor-helm-ldap
....
配置文件
....
LAST DEPLOYED: Wed Dec 19 17:12:08 2018
NAMESPACE: harbor
STATUS: DEPLOYED
RESOURCES:
==> v1/ConfigMap
NAME AGE
hb-ldap-harbor-adminserver 3m
hb-ldap-harbor-chartmuseum 3m
hb-ldap-harbor-clair 3m
hb-ldap-harbor-jobservice 3m
hb-ldap-harbor-notary 3m
hb-ldap-harbor-registry 3m
hb-ldap-harbor-ui 3m
==> v1/PersistentVolumeClaim
hb-ldap-redis 3m
hb-ldap-harbor-chartmuseum 3m
hb-ldap-harbor-registry 3m
==> v1/Service
hb-ldap-redis-master 3m
hb-ldap-harbor-adminserver 3m
hb-ldap-harbor-chartmuseum 3m
hb-ldap-harbor-clair 3m
hb-ldap-harbor-database 3m
hb-ldap-harbor-jobservice 3m
hb-ldap-harbor-notary-signer 3m
hb-ldap-harbor-notary-server 3m
hb-ldap-harbor-registry 3m
hb-ldap-harbor-ui 3m
==> v1beta1/Deployment
hb-ldap-redis 3m
hb-ldap-harbor-adminserver 3m
hb-ldap-harbor-chartmuseum 3m
hb-ldap-harbor-clair 3m
hb-ldap-harbor-jobservice 3m
hb-ldap-harbor-notary-server 3m
hb-ldap-harbor-notary-signer 3m
hb-ldap-harbor-registry 3m
hb-ldap-harbor-ui 3m
==> v1beta2/StatefulSet
hb-ldap-harbor-database 3m
==> v1beta1/Ingress
hb-ldap-harbor-ingress 3m
==> v1/Pod(related)
NAME READY STATUS RESTARTS AGE
hb-ldap-redis-84c4cdd468-hnjnv 1/1 Running 0 3m
hb-ldap-harbor-adminserver-674db969cd-4wt6d 0/1 CrashLoopBackOff 2 3m
hb-ldap-harbor-chartmuseum-78ccf8b66f-n84qr 1/1 Running 0 3m
hb-ldap-harbor-clair-58c4d87fc5-9m7z4 1/1 Running 3 3m
hb-ldap-harbor-jobservice-6b4db888f6-nmt2n 1/1 Running 1 3m
hb-ldap-harbor-notary-server-7bbd64b6cb-p49rz 1/1 Running 0 3m
hb-ldap-harbor-notary-signer-59c5b9fb6f-qfvjr 1/1 Running 0 3m
hb-ldap-harbor-registry-84d59c495f-dkm76 1/1 Running 0 3m
hb-ldap-harbor-ui-86dcbc99b-bldfz 1/1 Running 2 3m
hb-ldap-harbor-database-0 1/1 Running 0 3m
==> v1/Secret
NAME AGE
hb-ldap-harbor-adminserver 3m
hb-ldap-harbor-chartmuseum 3m
hb-ldap-harbor-database 3m
hb-ldap-harbor-ingress 3m
hb-ldap-harbor-jobservice 3m
hb-ldap-harbor-registry 3m
hb-ldap-harbor-ui 3m
NOTES:
Please wait for several minutes for Harbor deployment to complete.
Then you should be able to visit the UI portal at https://harbor.k8s.net.
For more details, please visit https://github.com/goharbor/harbor.
2.3 查看pods
[root@k8s-master01 harbor-helm-ldap]# kubectl get po -n harbor | grep ldap
hb-ldap-harbor-adminserver-674db969cd-4wt6d 1/1 Running 3 4m31s
hb-ldap-harbor-chartmuseum-78ccf8b66f-n84qr 1/1 Running 0 4m30s
hb-ldap-harbor-clair-58c4d87fc5-9m7z4 1/1 Running 3 4m29s
hb-ldap-harbor-database-0 1/1 Running 0 4m14s
hb-ldap-harbor-jobservice-6b4db888f6-nmt2n 1/1 Running 2 4m29s
hb-ldap-harbor-notary-server-7bbd64b6cb-p49rz 1/1 Running 0 4m27s
hb-ldap-harbor-notary-signer-59c5b9fb6f-qfvjr 1/1 Running 0 4m27s
hb-ldap-harbor-registry-84d59c495f-dkm76 1/1 Running 0 4m26s
hb-ldap-harbor-ui-86dcbc99b-bldfz 1/1 Running 3 4m24s
hb-ldap-redis-84c4cdd468-hnjnv 1/1 Running 0 4m32s
2.4 访问测试
- 将 harbor.k8s.net 添加解析至集群
- admin/Harbor12345

3,配置使用ldap登录
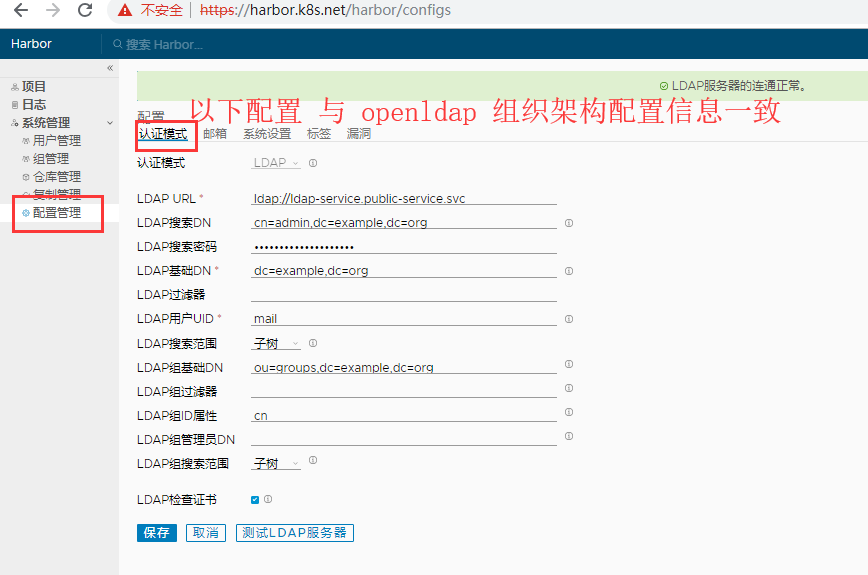
- 注意:因为openLDAP部署在了public-service的namespace中,而harbor部署在了harbor的namespace中,此时两个ns的service是不同的,有两个解决方案
- 使用nodeport或者使用service全地址,格式为ServiceName.NAMESPACE.svc。
- 配置如下,注意harbor也使用mail进行认证,非cn:
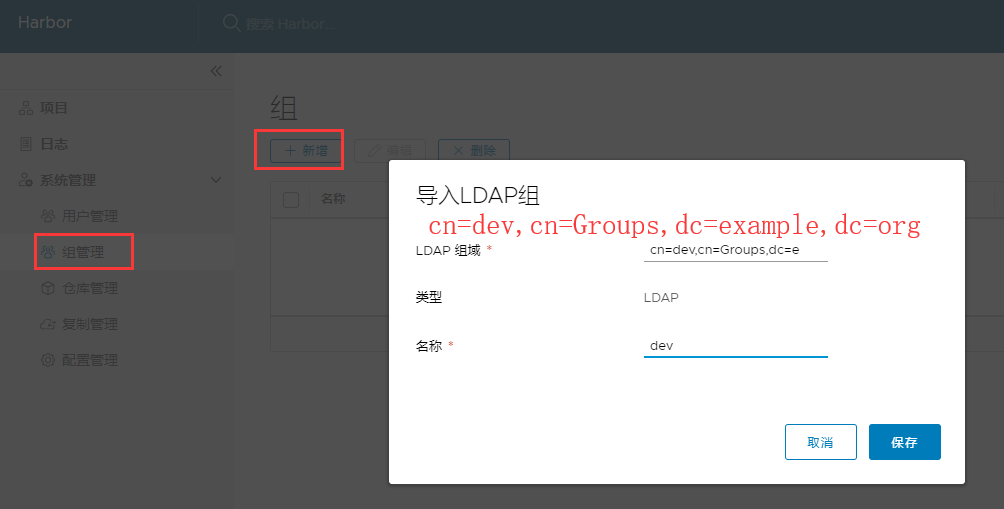
4,创建用户和组
- 用户无需自己创建,可以直接登录,注意使用的是email格式

5,配置证书
5.1 查看harbor自带证书
[root@k8s-master01 harbor-helm-ldap]# kubectl get secrets/hb-ldap-harbor-ingress -n harbor -o jsonpath="{.data.ca.crt}" | base64 --decode
-----BEGIN CERTIFICATE-----
MIIC9TCCAd2gAwIBAgIRAKOxABnkDrCfBg/00owLsbQwDQYJKoZIhvcNAQELBQAw
FDESMBAGA1UEAxMJaGFyYm9yLWNhMB4XDTE4MTIxOTA5MTIwOVoXDTI4MTIxNjA5
MTIwOVowFDESMBAGA1UEAxMJaGFyYm9yLWNhMIIBIjANBgkqhkiG9w0BAQEFAAOC
AQ8AMIIBCgKCAQEAvm2nDWGAHFNDlYaFF1Twfuoc8rxh+yWmzHvxo1nUF5JUUOlA
eSqP9IaN7M8QGLY62QAjHwdBFnczR1073t246JUC4aucKYBLuz/hUnNJESmMaZnr
EMLQyL9Av9RiRAWdbyNufab4RtkcYuUJdbWjqzwLW1/JSC+KJ4yX0dmV2g9sa/66
wow5R79oOYe5ZCb4vJk2o9/Qw0bC5P+tsGAtq3doM7RX9CCCkYWWQUEWSjsnXQDh
9AHJMHChFVLuwLVSXptUQaCswWV8pR+w6gn+UiQdq7Xxv79p/zoy7CaKAqgvBsR9
XxbgE3xNg1RUG9cTn6aNqxCzkCwpJBgZ3V3uWwIDAQABo0IwQDAOBgNVHQ8BAf8E
BAMCAqQwHQYDVR0lBBYwFAYIKwYBBQUHAwEGCCsGAQUFBwMCMA8GA1UdEwEB/wQF
MAMBAf8wDQYJKoZIhvcNAQELBQADggEBAEW1tMByf2gxVZiVIdiRGT5qetGHzHBH
xJsesfqTntO0zEsNCP1ma01Z8P2VuVJ5uRIICSqcUU1ywqzqntIZ6BkXIZV13ttL
MBRuetKdYfl/WI6WnccGlo0sAsqupc+h97MlqLJstnY/bOyT9Dl84DrKnhxt0MRj
gDycf1snXGMICIGp0WX0ImNuDXRyZm+p6mCwXXcnXm2bo+gF3ms/VNULFLZjYWdw
8Zf5M930PlUH+c76kNsQ762IqspKwic5pwu5cmxZDcMDpQRPmJz0g7o+k5jUB+FX
KA6w/+IGR8Wj5M/wpwSnECHhP3LsjZRcUCia1hVbbZHH4FQQ+AxDHBI=
-----END CERTIFICATE-----
5.2 创建证书 并push 镜像
[root@k8s-master01 harbor-helm-ldap]# mkdir -p /etc/docker/certs.d/harbor.k8s.net/
[root@k8s-master01 harbor-helm-ldap]# cat <<EOF > /etc/docker/certs.d/harbor.k8s.net/ca.crt
-----BEGIN CERTIFICATE-----
MIIC9TCCAd2gAwIBAgIRAKOxABnkDrCfBg/00owLsbQwDQYJKoZIhvcNAQELBQAw
FDESMBAGA1UEAxMJaGFyYm9yLWNhMB4XDTE4MTIxOTA5MTIwOVoXDTI4MTIxNjA5
MTIwOVowFDESMBAGA1UEAxMJaGFyYm9yLWNhMIIBIjANBgkqhkiG9w0BAQEFAAOC
AQ8AMIIBCgKCAQEAvm2nDWGAHFNDlYaFF1Twfuoc8rxh+yWmzHvxo1nUF5JUUOlA
eSqP9IaN7M8QGLY62QAjHwdBFnczR1073t246JUC4aucKYBLuz/hUnNJESmMaZnr
EMLQyL9Av9RiRAWdbyNufab4RtkcYuUJdbWjqzwLW1/JSC+KJ4yX0dmV2g9sa/66
wow5R79oOYe5ZCb4vJk2o9/Qw0bC5P+tsGAtq3doM7RX9CCCkYWWQUEWSjsnXQDh
9AHJMHChFVLuwLVSXptUQaCswWV8pR+w6gn+UiQdq7Xxv79p/zoy7CaKAqgvBsR9
XxbgE3xNg1RUG9cTn6aNqxCzkCwpJBgZ3V3uWwIDAQABo0IwQDAOBgNVHQ8BAf8E
BAMCAqQwHQYDVR0lBBYwFAYIKwYBBQUHAwEGCCsGAQUFBwMCMA8GA1UdEwEB/wQF
MAMBAf8wDQYJKoZIhvcNAQELBQADggEBAEW1tMByf2gxVZiVIdiRGT5qetGHzHBH
xJsesfqTntO0zEsNCP1ma01Z8P2VuVJ5uRIICSqcUU1ywqzqntIZ6BkXIZV13ttL
MBRuetKdYfl/WI6WnccGlo0sAsqupc+h97MlqLJstnY/bOyT9Dl84DrKnhxt0MRj
gDycf1snXGMICIGp0WX0ImNuDXRyZm+p6mCwXXcnXm2bo+gF3ms/VNULFLZjYWdw
8Zf5M930PlUH+c76kNsQ762IqspKwic5pwu5cmxZDcMDpQRPmJz0g7o+k5jUB+FX
KA6w/+IGR8Wj5M/wpwSnECHhP3LsjZRcUCia1hVbbZHH4FQQ+AxDHBI=
-----END CERTIFICATE-----
EOF
5.3 登录 harbor
[root@k8s-master01 harbor-helm-ldap]# systemctl restart docker
- 账号和密码:luobing@mail.com/luobing
[root@k8s-master01 harbor-helm-ldap]# docker login harbor.k8s.net
Username: luobing@mail.com
Password:
Login Succeeded
5.3.1 报错证书不信任错误x509: certificate signed by unknown authority
chmod 644 /etc/pki/ca-trust/extracted/pem/tls-ca-bundle.pem
- 将上述ca.crt添加到/etc/pki/tls/certs/ca-bundle.crt即可
cp /etc/docker/certs.d/harbor.k8s.net/ca.crt /etc/pki/tls/certs/ca-bundle.crt
chmod 444 /etc/pki/ca-trust/extracted/pem/tls-ca-bundle.pem
5.4 上传镜像
[root@k8s-master01 harbor-helm-ldap]# docker images | grep busybox
busybox 1.27 6ad733544a63 13 months ago 1.13 MB
core.harbor.domain/develop/busybox 1.27 6ad733544a63 13 months ago 1.13 MB
busybox
[root@k8s-master01 harbor-helm-ldap]# docker tag busybox:1.27 harbor.k8s.net/develop/busybox:1.27
[root@k8s-master01 harbor-helm-ldap]# docker push harbor.k8s.net/develop/busybox:1.27
The push refers to a repository [harbor.k8s.net/develop/busybox]
0271b8eebde3: Pushed
1.27: digest: sha256:179cf024c8a22f1621ea012bfc84b0df7e393cb80bf3638ac80e30d23e69147f size: 527






